Profiler 2.8 – Windows Memory Forensics – Cerbero Blog
Por um escritor misterioso
Last updated 22 fevereiro 2025

Best of Washington DC volume 1 by Global Village - Issuu
C2 Payload Hiding and Memory Forensics - 4xpl0r3r's blog

Twiti: Social Listening for Threat Intelligence

Computer forensics: FTK forensic toolkit overview [updated 2019]

Memory Forensics - an overview

current top 5: may 2020 – Meg McMillin

2020 Cyber Attacks Statistics – HACKMAGEDDON

Core Impact System Requirements

Memory Analysis and Forensics using Volatility - GISPP
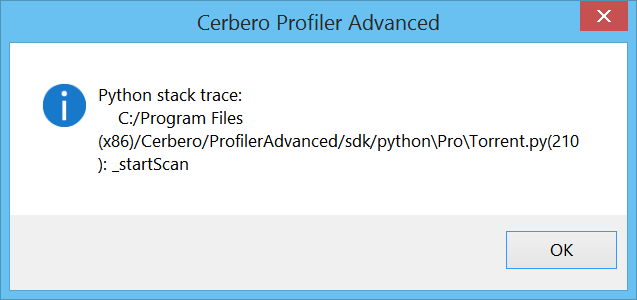
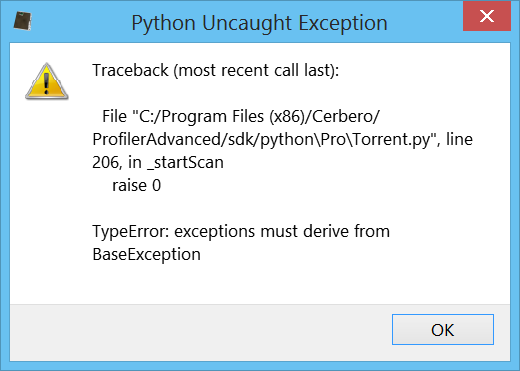
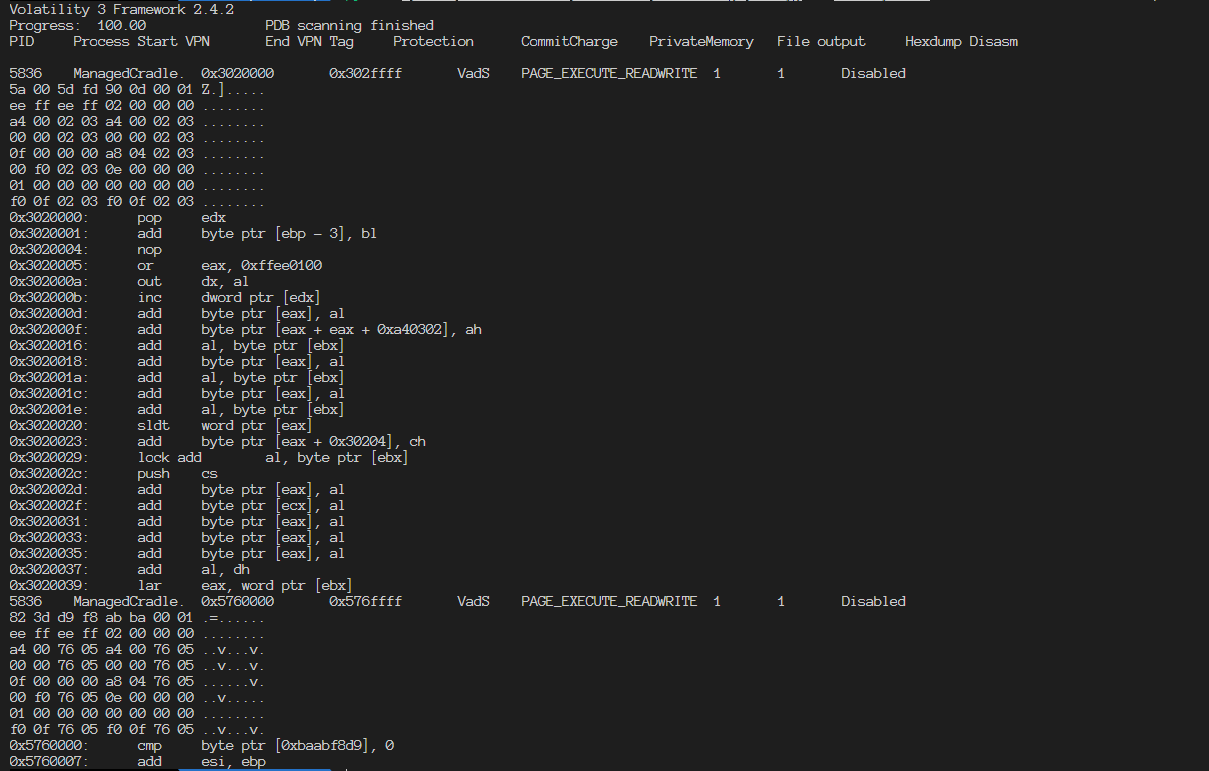
Profiler 2.8 – Windows Memory Forensics – Cerbero Blog
Windows Memory Forensics using Open Source Tools, by Aditya Pratap
Using the Unity Memory Profiler to Troubleshoot Out-of-Memory Issues
PDF) Windows Memory-Injected Malware Detection Freeware Comparison

Expanded Perspectives - Expanded Perspectives
Windows Memory Forensics: Close to Release – Cerbero Blog
Recomendado para você
-
 Python Exceptions and Errors – PYnative22 fevereiro 2025
Python Exceptions and Errors – PYnative22 fevereiro 2025 -
 PYTHON : Error exception must derive from BaseException even when it does (Python 2.7)22 fevereiro 2025
PYTHON : Error exception must derive from BaseException even when it does (Python 2.7)22 fevereiro 2025 -
what does mean exceptions must derive from BaseException? · Issue #16 · rmotr-curriculum/advanced-python-programming-questions · GitHub22 fevereiro 2025
-
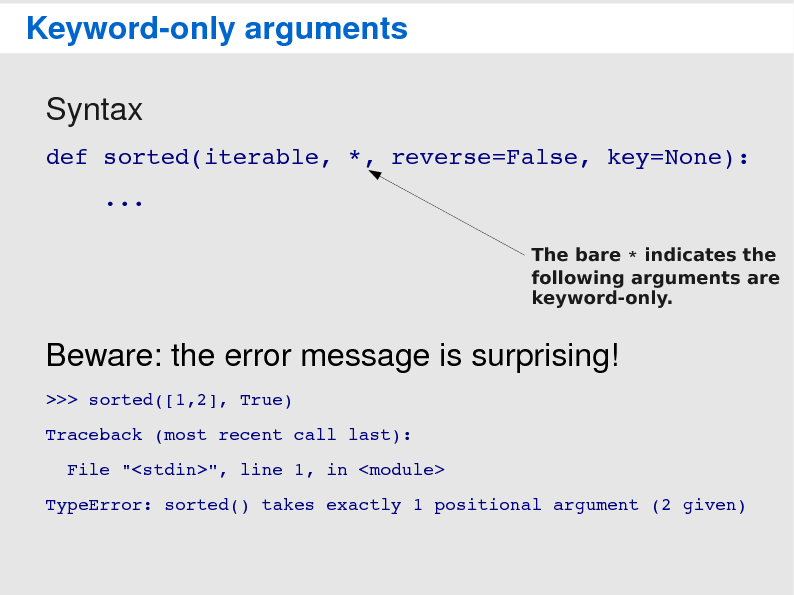 Porting your code to Python 322 fevereiro 2025
Porting your code to Python 322 fevereiro 2025 -
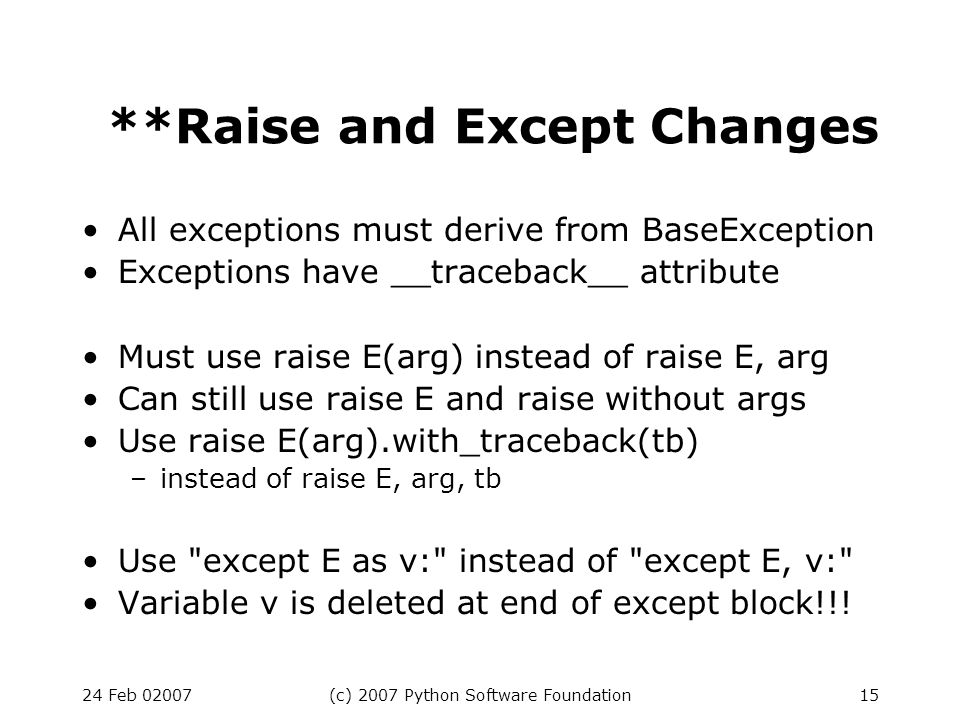 Python 3000 (PyCon, 24-Feb-02007) Guido van Rossum - ppt download22 fevereiro 2025
Python 3000 (PyCon, 24-Feb-02007) Guido van Rossum - ppt download22 fevereiro 2025 -
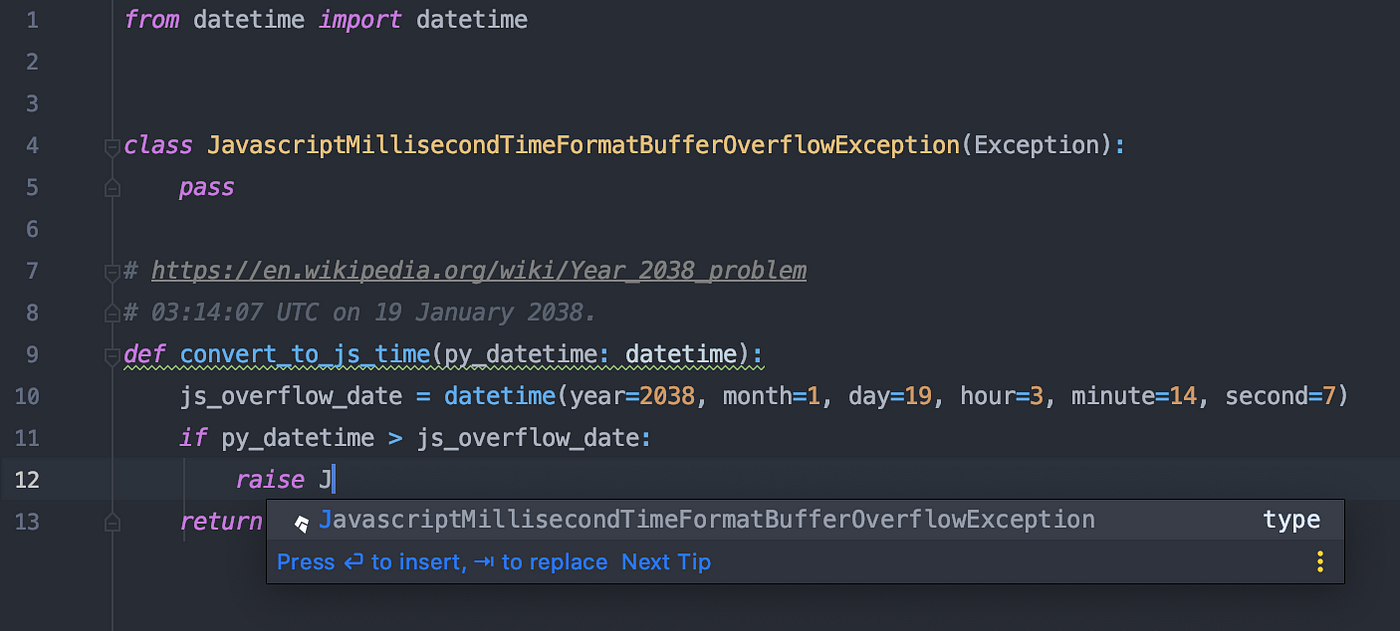 A Comprehensive Guide to Handling Exceptions in Python, by Henry George22 fevereiro 2025
A Comprehensive Guide to Handling Exceptions in Python, by Henry George22 fevereiro 2025 -
 Exception Handling in Python - Coding Ninjas22 fevereiro 2025
Exception Handling in Python - Coding Ninjas22 fevereiro 2025 -
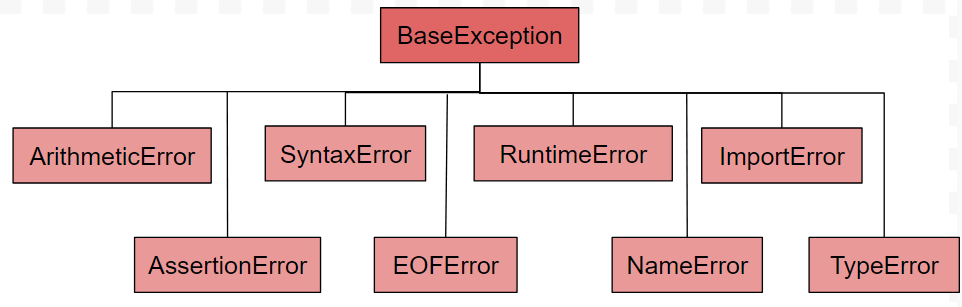
 Built-in Exceptions — Python 3.12.1 documentation22 fevereiro 2025
Built-in Exceptions — Python 3.12.1 documentation22 fevereiro 2025 -
 9 Handling exceptions - Programmer's Guide to Apache Thrift22 fevereiro 2025
9 Handling exceptions - Programmer's Guide to Apache Thrift22 fevereiro 2025 -
 Python basics of exception handling in Hindi22 fevereiro 2025
Python basics of exception handling in Hindi22 fevereiro 2025
você pode gostar
-
 Pulseira Relogio Borracha Masculino Magnum22 fevereiro 2025
Pulseira Relogio Borracha Masculino Magnum22 fevereiro 2025 -
 The Rock Reacts To My Videos22 fevereiro 2025
The Rock Reacts To My Videos22 fevereiro 2025 -
Meme Brown22 fevereiro 2025
-
 How To Create A Responsive Anime Website22 fevereiro 2025
How To Create A Responsive Anime Website22 fevereiro 2025 -
 What is Ur clock is prolly bad : r/PhantomForces22 fevereiro 2025
What is Ur clock is prolly bad : r/PhantomForces22 fevereiro 2025 -
 Final Bicicleta Truques Façanha 3D - jogo de moto - Download do APK para Android22 fevereiro 2025
Final Bicicleta Truques Façanha 3D - jogo de moto - Download do APK para Android22 fevereiro 2025 -
 FROZEN 3 (2025) : Trailer, Release Date & Everything You Need To22 fevereiro 2025
FROZEN 3 (2025) : Trailer, Release Date & Everything You Need To22 fevereiro 2025 -
 File:Milan Baranyk (MMKS Podhale Nowy Targ 2011)b.jpg - Wikimedia Commons22 fevereiro 2025
File:Milan Baranyk (MMKS Podhale Nowy Targ 2011)b.jpg - Wikimedia Commons22 fevereiro 2025 -
 ROMWE Kawaii Shorts com cordão Carta Gráfico de morango babado, SHEIN Brasil em 202322 fevereiro 2025
ROMWE Kawaii Shorts com cordão Carta Gráfico de morango babado, SHEIN Brasil em 202322 fevereiro 2025 -
 Behind the Design: Resident Evil Village - Discover - Apple Developer22 fevereiro 2025
Behind the Design: Resident Evil Village - Discover - Apple Developer22 fevereiro 2025
