Delay-CJ: A novel cryptojacking covert attack method based on
Por um escritor misterioso
Last updated 07 março 2025

Cryptojacking is a type of resource embezzlement attack, wherein an attacker secretly executes the cryptocurrency mining program in the target host to…

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library

PDF) A deep learning approach for host-based cryptojacking malware detection
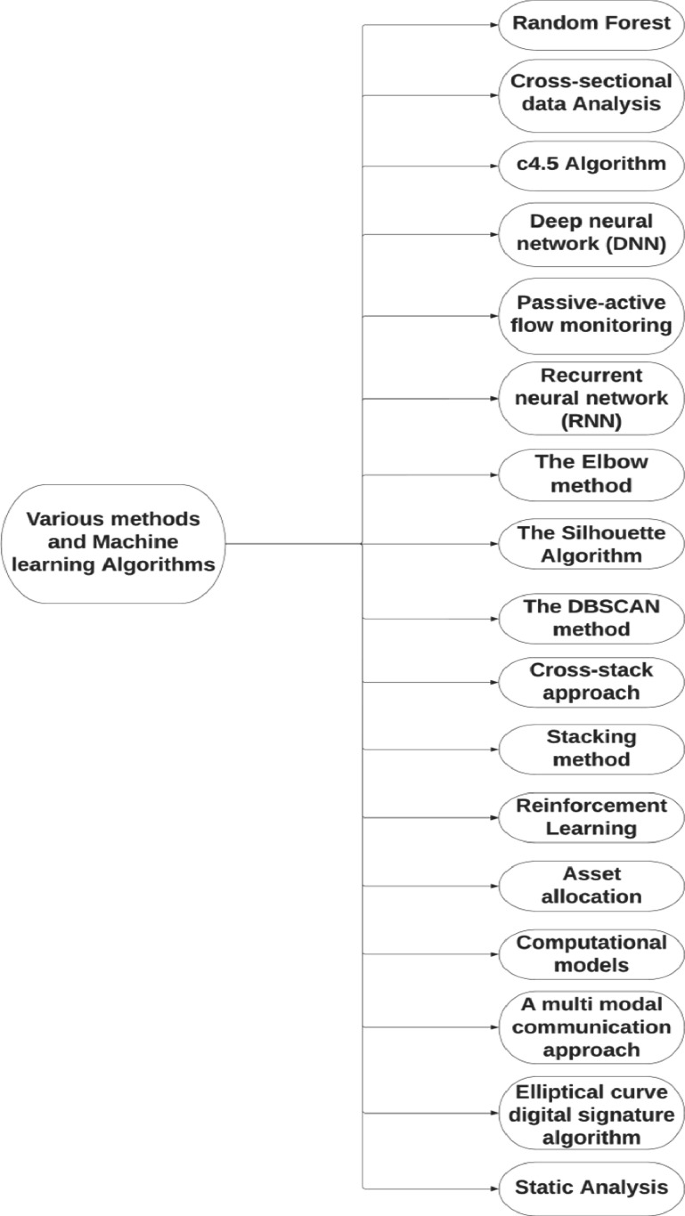
Variants of Crypto-Jacking Attacks and Their Detection Techniques

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect

What is cryptojacking? A beginner's guide to crypto mining malware
WR.1943-5452.0001265/asset/cb7a57af-5a2c-4ed9-8f84-a45c7a67946c/assets/images/large/figure4.jpg)
Review of Modeling Methodologies for Managing Water Distribution Security, Journal of Water Resources Planning and Management

Full article: Cryptojacking injection: A paradigm shift to cryptocurrency- based web-centric internet attacks

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
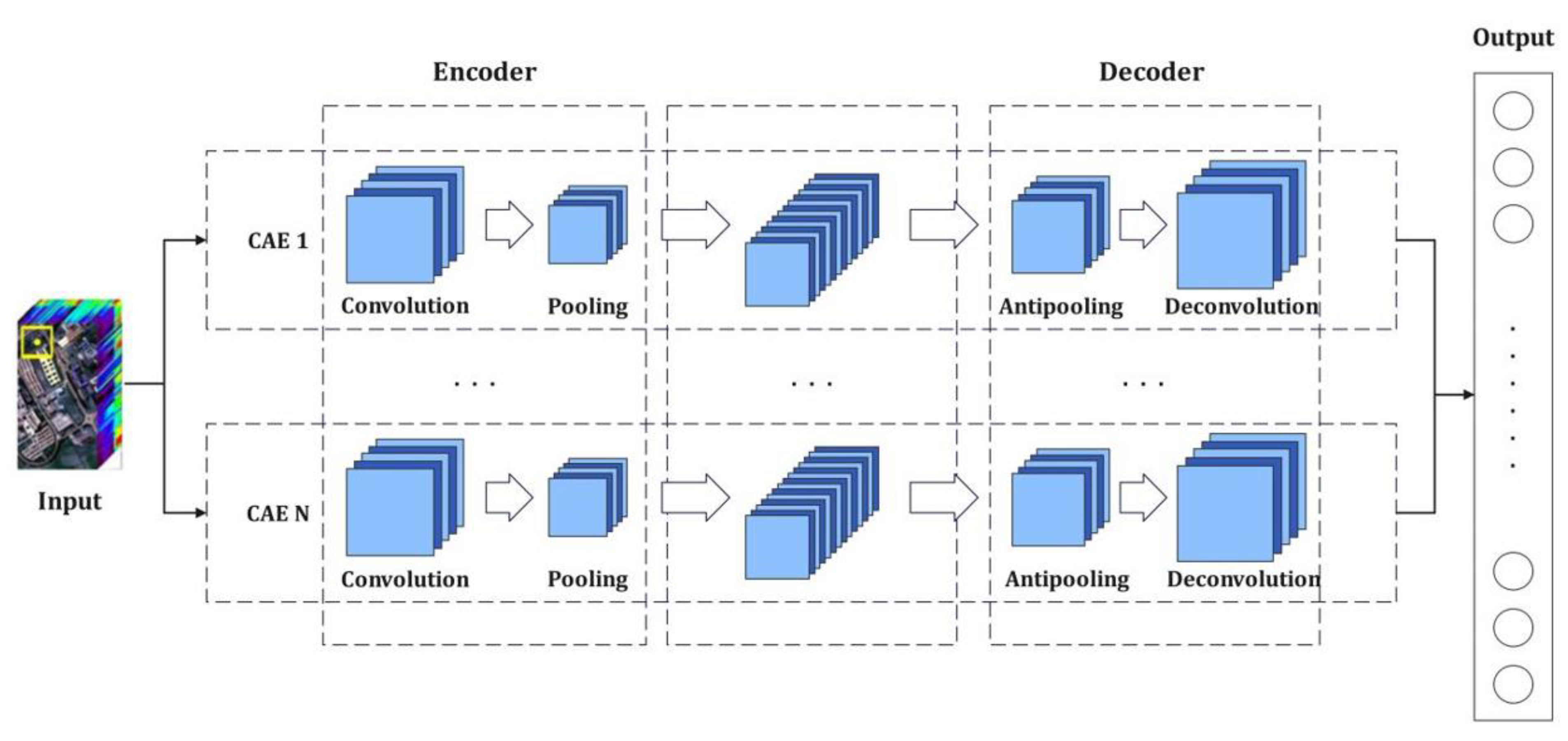
Sensors, Free Full-Text

PSAK: A provably secure authenticated key agreement scheme based on extended Chebyshev chaotic maps for smart grid environments - Wang - 2023 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
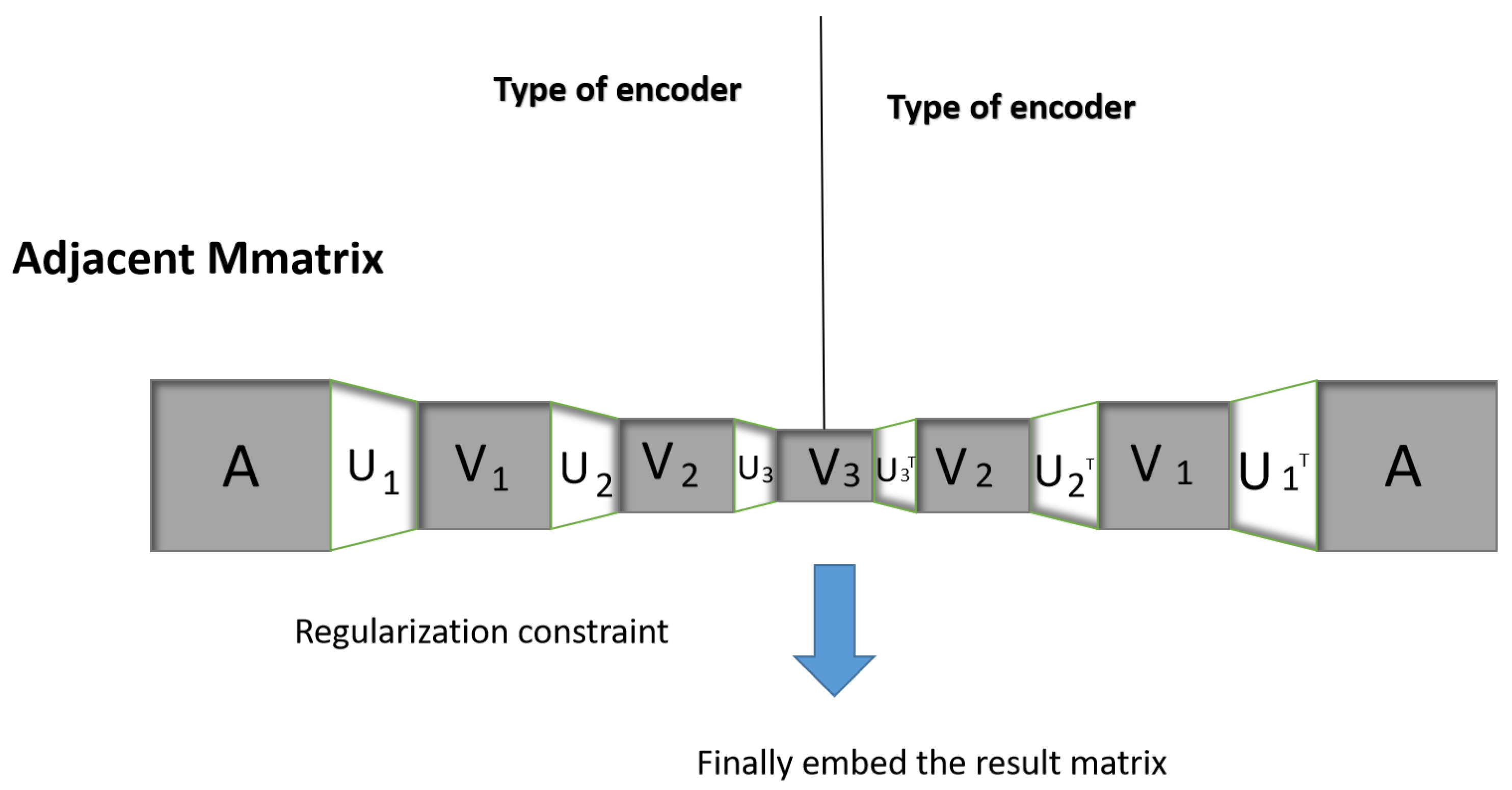
Mathematics, Free Full-Text
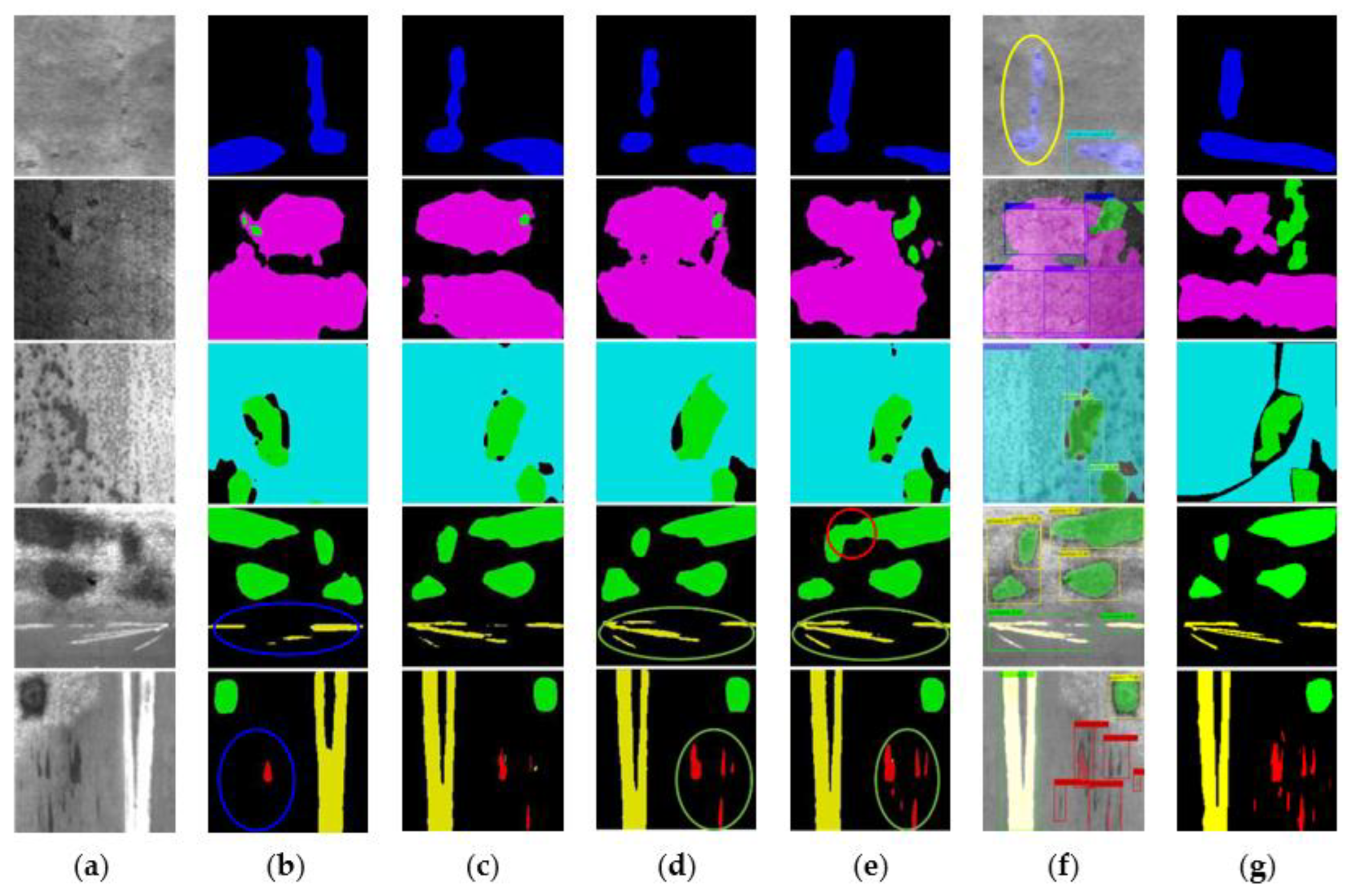
Sensors, Free Full-Text
Recomendado para você
-
 AdBlock and Authedmine.com cryptocurrency miners – AdBlock07 março 2025
AdBlock and Authedmine.com cryptocurrency miners – AdBlock07 março 2025 -
How to stop websites from using your computer to mine Bitcoin - Quora07 março 2025
-
 Line of Duty: Yes eBook : Blocker MD, Virginia Irvine, Wooten Ph.D.., Heather G.: Kindle Store07 março 2025
Line of Duty: Yes eBook : Blocker MD, Virginia Irvine, Wooten Ph.D.., Heather G.: Kindle Store07 março 2025 -
Yes! Hackers are using your computer to make money (Crypto Currency).07 março 2025
-
 12 Air Date 01/16/1960 Stock Photos, High-Res Pictures, and Images - Getty Images07 março 2025
12 Air Date 01/16/1960 Stock Photos, High-Res Pictures, and Images - Getty Images07 março 2025 -
 Stablecoin Issuer Tether (USDT/BTC) Wants to Become a Major Bitcoin Miner - Bloomberg07 março 2025
Stablecoin Issuer Tether (USDT/BTC) Wants to Become a Major Bitcoin Miner - Bloomberg07 março 2025 -
![App Fridays] Kiwi Browser comes with a crypto-mining blocker, allows background play for videos](https://images.yourstory.com/cs/wordpress/2018/08/Kiwi-Feature.png?w=1152&fm=auto&ar=2:1&mode=crop&crop=faces) App Fridays] Kiwi Browser comes with a crypto-mining blocker, allows background play for videos07 março 2025
App Fridays] Kiwi Browser comes with a crypto-mining blocker, allows background play for videos07 março 2025 -
 Miners Volleyball Defeats Reno in a Thrilling Match, “High Hopes07 março 2025
Miners Volleyball Defeats Reno in a Thrilling Match, “High Hopes07 março 2025 -
 STL file Fantasy Football - Dwarf Blocker 02・Template to download07 março 2025
STL file Fantasy Football - Dwarf Blocker 02・Template to download07 março 2025 -
 The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost07 março 2025
The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost07 março 2025
você pode gostar
-
 China, Wiki07 março 2025
China, Wiki07 março 2025 -
 MLP - A Miraculous Play by Kawaii-tron on DeviantArt07 março 2025
MLP - A Miraculous Play by Kawaii-tron on DeviantArt07 março 2025 -
 Watch Dogs Legion - Steam Vertical Grid by BrokenNoah on DeviantArt07 março 2025
Watch Dogs Legion - Steam Vertical Grid by BrokenNoah on DeviantArt07 março 2025 -
 Carvalho Enxovais - Jogo de Tapete Cozinha - Café Preto07 março 2025
Carvalho Enxovais - Jogo de Tapete Cozinha - Café Preto07 março 2025 -
 How to Convert a GIF to JPG in a Few Simple Steps07 março 2025
How to Convert a GIF to JPG in a Few Simple Steps07 março 2025 -
 TechScape: suspicious of TikTok? You're not alone, TikTok07 março 2025
TechScape: suspicious of TikTok? You're not alone, TikTok07 março 2025 -
 CoComelon Song CoComelon Nursery Rhymes & Kids Songs07 março 2025
CoComelon Song CoComelon Nursery Rhymes & Kids Songs07 março 2025 -
 Outfits (Roupas, Olhos, Cabelo) de Gacha Life07 março 2025
Outfits (Roupas, Olhos, Cabelo) de Gacha Life07 março 2025 -
 Schnapsen- An Excellent Card Game for 2 People07 março 2025
Schnapsen- An Excellent Card Game for 2 People07 março 2025 -
 Noragami Aragoto - 04 - Lost in Anime07 março 2025
Noragami Aragoto - 04 - Lost in Anime07 março 2025
