Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Last updated 07 março 2025

In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

Project Zero: Remote iPhone Exploitation Part 2: Bringing Light

Code of Ethics for Government Services Poster

Exploiting OGNL Injection in Apache Struts

FastJSON deserialization bug can trigger RCE in popular Java

Some States Are Ready To Punish Abortion in a Post-Roe World

What are the Cures Act Information Blocking Exceptions?

Code of Ethics for Government Services Poster
Log4Shell Zero-Day Vulnerability - CVE-2021-44228

Trusted Platform Module - Wikipedia
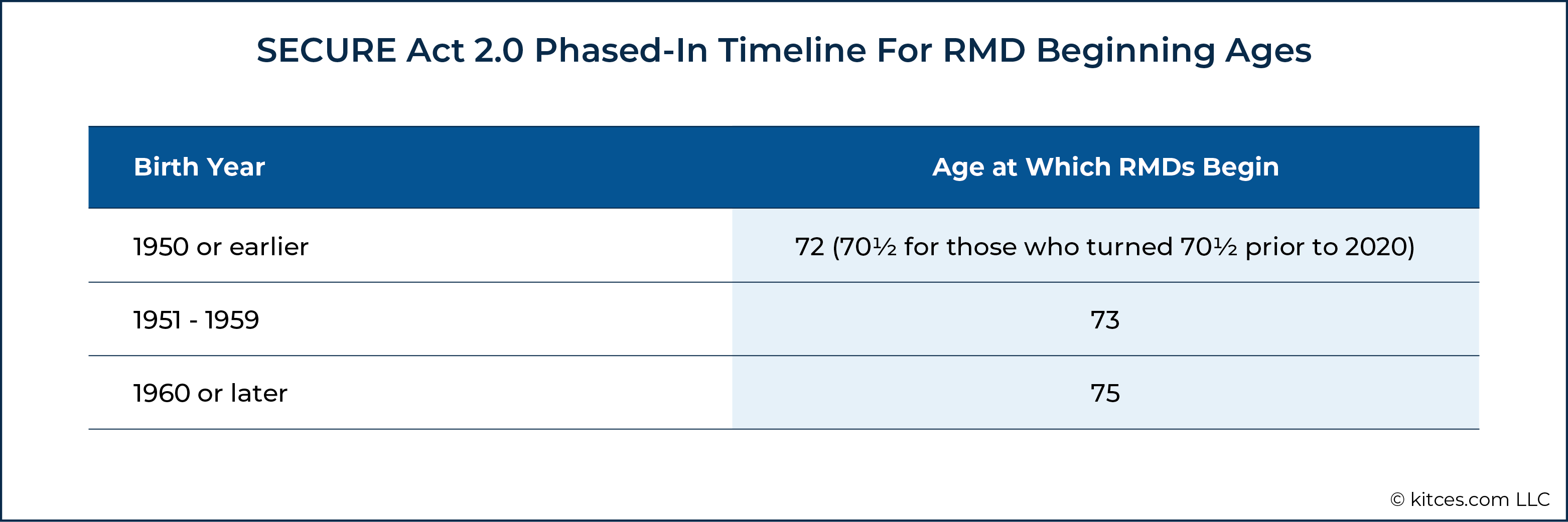
Secure Act 2.0: Detailed Breakdown Of Key Tax Opportunities

Abusing Windows Internals - Part Two

An Overview of MS-RPC and Its Security Mechanisms

Coders' Rights Project Reverse Engineering FAQ
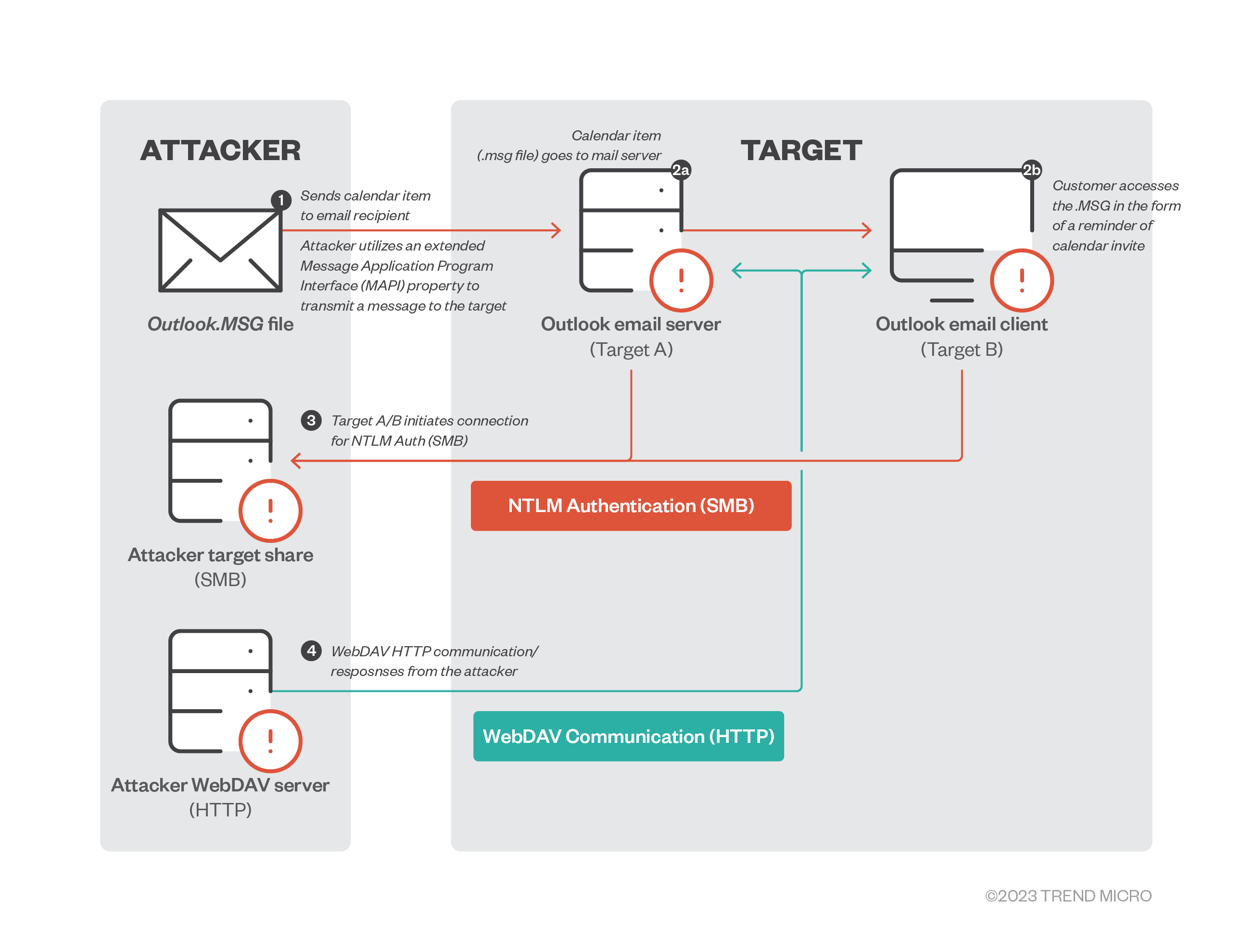
Patch CVE-2023-23397 Immediately: What You Need To Know and Do
Recomendado para você
-
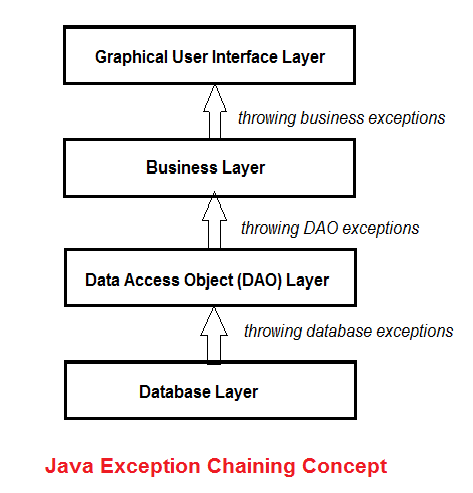 Understanding Java Exception Chaining with Code Examples07 março 2025
Understanding Java Exception Chaining with Code Examples07 março 2025 -
 demonstrate custom exceptions inheritance java - Stack Overflow07 março 2025
demonstrate custom exceptions inheritance java - Stack Overflow07 março 2025 -
 Python's raise: Effectively Raising Exceptions in Your Code – Real Python07 março 2025
Python's raise: Effectively Raising Exceptions in Your Code – Real Python07 março 2025 -
 Dress Expectations / Dress Code Exceptions07 março 2025
Dress Expectations / Dress Code Exceptions07 março 2025 -
 Java - Custom Light Exceptions - Advlatam07 março 2025
Java - Custom Light Exceptions - Advlatam07 março 2025 -
 Java Exception Rule Book – Nico de Wet scalable and robust distributed systems07 março 2025
Java Exception Rule Book – Nico de Wet scalable and robust distributed systems07 março 2025 -
 Implement Custom Exceptions in Java: Why, When and How07 março 2025
Implement Custom Exceptions in Java: Why, When and How07 março 2025 -
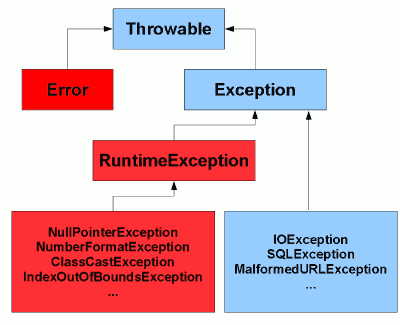 The exception hierarchy in Java07 março 2025
The exception hierarchy in Java07 março 2025 -
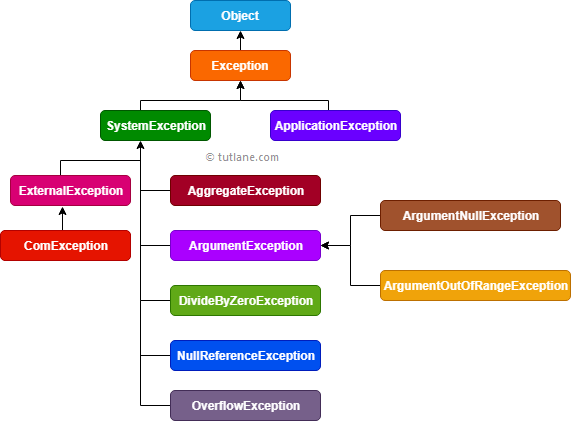 Visual Basic Exception - Tutlane07 março 2025
Visual Basic Exception - Tutlane07 março 2025 -
IT Exception Management07 março 2025
você pode gostar
-
 Anúncio do GTA 6 pode acontecer ainda este ano e lançamento para 202407 março 2025
Anúncio do GTA 6 pode acontecer ainda este ano e lançamento para 202407 março 2025 -
 5 Doa Memohon Ampunan Atas Dosa-Dosa yang Dilakukan07 março 2025
5 Doa Memohon Ampunan Atas Dosa-Dosa yang Dilakukan07 março 2025 -
 Dash! Eevee Eeveelutions ver.2 Pokemon Card Sleeve Deck Shield Single07 março 2025
Dash! Eevee Eeveelutions ver.2 Pokemon Card Sleeve Deck Shield Single07 março 2025 -
 GTA 5 Online YimMenu Cheat + Scripts07 março 2025
GTA 5 Online YimMenu Cheat + Scripts07 março 2025 -
 Anamnese Psicológica - Ep 02 Conceitos Fundamentais da Psicologia07 março 2025
Anamnese Psicológica - Ep 02 Conceitos Fundamentais da Psicologia07 março 2025 -
 Fortnite SHHHH Nerf Gun. Yellow. WORKS!! With detachable silencer Tested07 março 2025
Fortnite SHHHH Nerf Gun. Yellow. WORKS!! With detachable silencer Tested07 março 2025 -
Yu Yu Hakusho - Série completa + Filmes e Ovas em DVD07 março 2025
-
 PAPA JOHNS PIZZA - 17 Photos & 27 Reviews - 2390 4th St N, St. Petersburg, Florida - Pizza - Restaurant Reviews - Phone Number - Yelp07 março 2025
PAPA JOHNS PIZZA - 17 Photos & 27 Reviews - 2390 4th St N, St. Petersburg, Florida - Pizza - Restaurant Reviews - Phone Number - Yelp07 março 2025 -
 Play 3 Game Pack! – The Game of Life Payday Yahtzee Online - Play All Game Boy Advance Games Online07 março 2025
Play 3 Game Pack! – The Game of Life Payday Yahtzee Online - Play All Game Boy Advance Games Online07 março 2025 -
 9/11 Memorial: Survivor Tree. Countless memorials throughout New York…, by Frederick Hissenkaemper, Dust Settled07 março 2025
9/11 Memorial: Survivor Tree. Countless memorials throughout New York…, by Frederick Hissenkaemper, Dust Settled07 março 2025

