Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 22 janeiro 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

9 types of computer virus and how they do their dirty work
Abusing Exceptions for Code Execution, Part 1
User Account Control – Overview and Exploitation

Classification of Web Application Vulnerabilities

101 Landing Page Optimization Tips & Ideas

Evading Windows Defender with 1 Byte Change - Red Team Notes
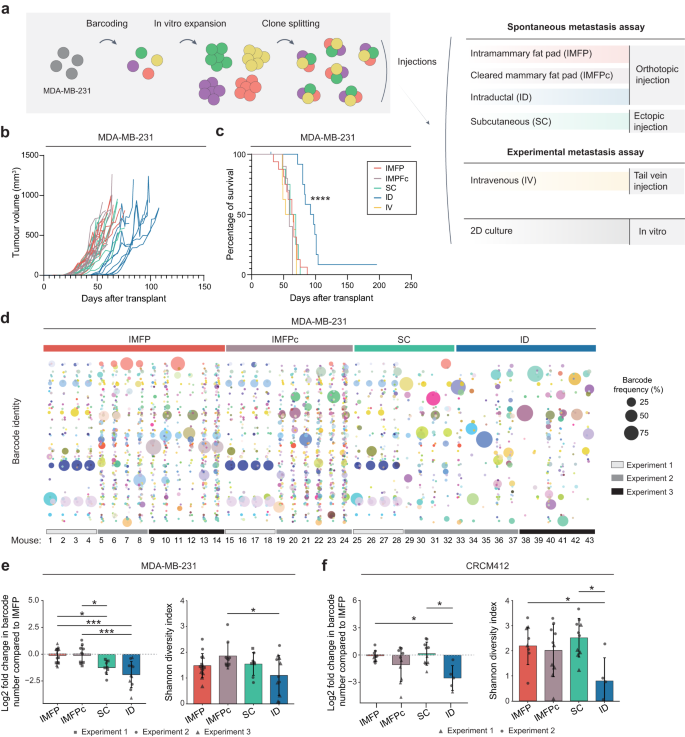
Experimental and spontaneous metastasis assays can result in divergence in clonal architecture
Abusing Jenkins Groovy Script Console to get Shell, by Nishant Sharma

CVE-2018-8611 Exploiting Windows KTM Part 5/5 – Vulnerability detection and a better read/write primitive, NCC Group Research Blog
Recomendado para você
-
 Java Fundamentals Tutorial: Exceptions22 janeiro 2025
Java Fundamentals Tutorial: Exceptions22 janeiro 2025 -
 Types of exceptions in Java: checked, unchecked, and custom22 janeiro 2025
Types of exceptions in Java: checked, unchecked, and custom22 janeiro 2025 -
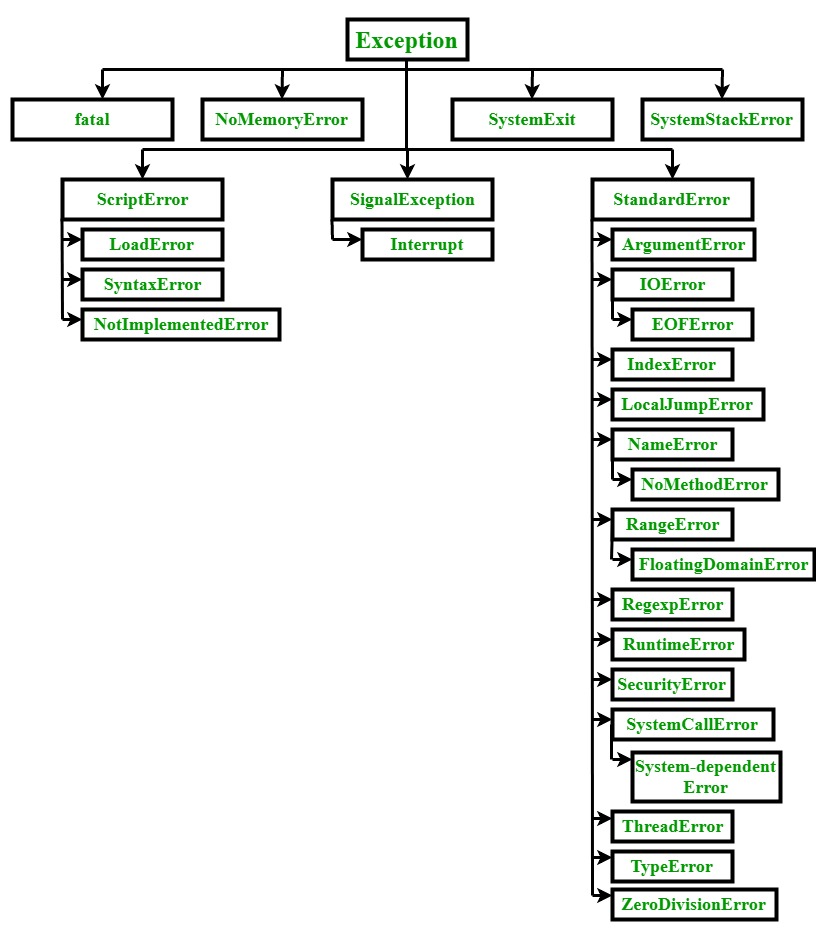 Ruby Exceptions - GeeksforGeeks22 janeiro 2025
Ruby Exceptions - GeeksforGeeks22 janeiro 2025 -
 10 Commonplace Exceptions in Selenium WebDriver22 janeiro 2025
10 Commonplace Exceptions in Selenium WebDriver22 janeiro 2025 -
 Java - Custom Light Exceptions - Advlatam22 janeiro 2025
Java - Custom Light Exceptions - Advlatam22 janeiro 2025 -
🚀Mastering Error and Exception Handling: A Deep Dive into Reliable Code Execution 💻✨22 janeiro 2025
-
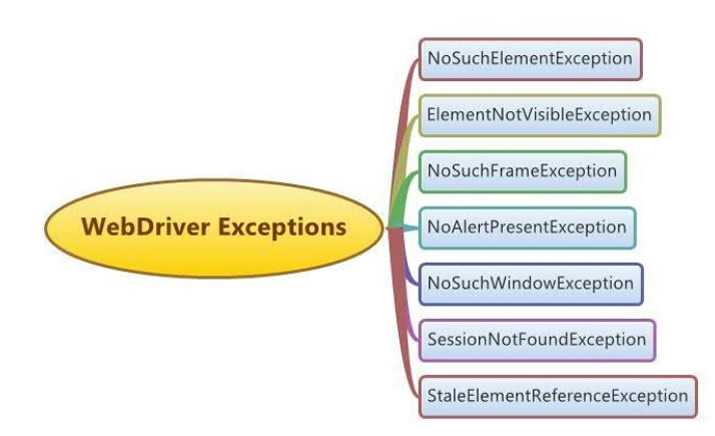 Different types of Selenium WebDriver Common Exceptions22 janeiro 2025
Different types of Selenium WebDriver Common Exceptions22 janeiro 2025 -
![Exceptions API, Elastic Security Solution [8.11]](https://www.elastic.co/guide/en/security/current/images/exceptions-logic.png) Exceptions API, Elastic Security Solution [8.11]22 janeiro 2025
Exceptions API, Elastic Security Solution [8.11]22 janeiro 2025 -
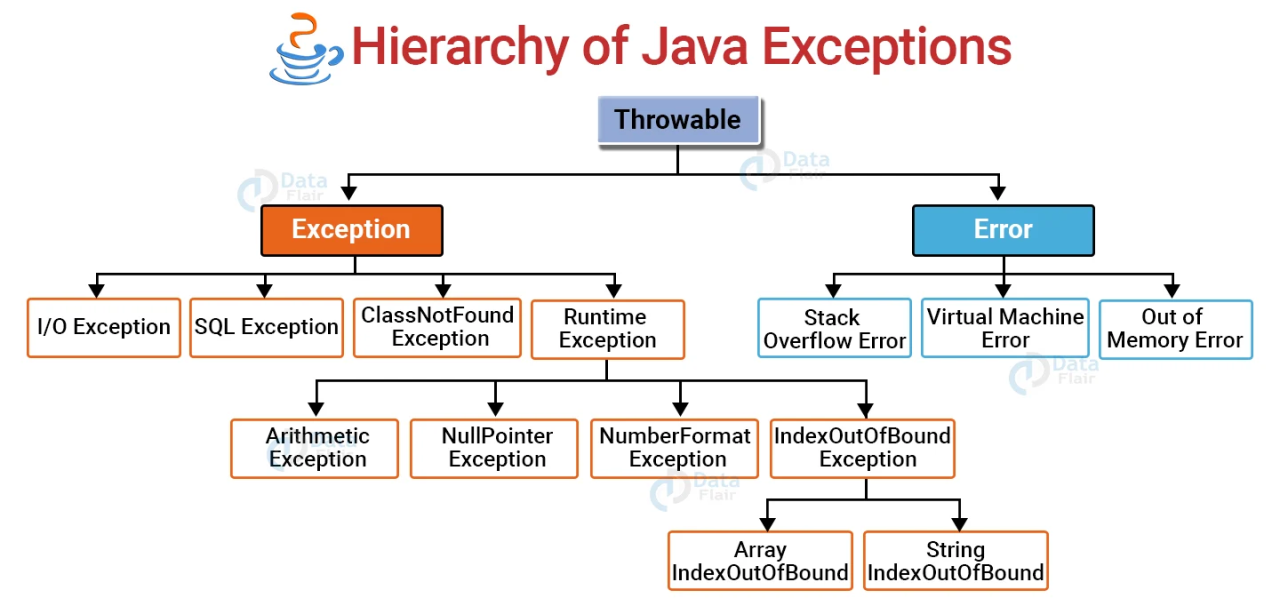
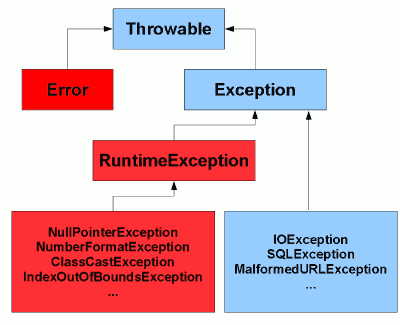 The exception hierarchy in Java22 janeiro 2025
The exception hierarchy in Java22 janeiro 2025 -
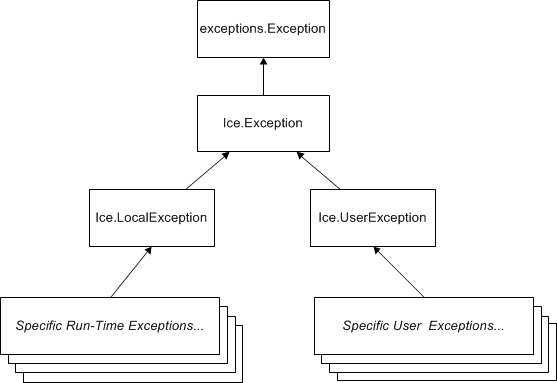 Python Mapping for Exceptions - Ice22 janeiro 2025
Python Mapping for Exceptions - Ice22 janeiro 2025
você pode gostar
-
 Cuando Se Estrenará La Temporada 2 De Blood Lad?22 janeiro 2025
Cuando Se Estrenará La Temporada 2 De Blood Lad?22 janeiro 2025 -
 Dexibell VIVO S10 88-key Digital Stage Piano22 janeiro 2025
Dexibell VIVO S10 88-key Digital Stage Piano22 janeiro 2025 -
![RELEASE] (1.26.5.0) World Update X: United States and US Territories Now Available! - News & Announcements - Microsoft Flight Simulator Forums](https://img.youtube.com/vi/NBwP4NlG61c/maxresdefault.jpg) RELEASE] (1.26.5.0) World Update X: United States and US Territories Now Available! - News & Announcements - Microsoft Flight Simulator Forums22 janeiro 2025
RELEASE] (1.26.5.0) World Update X: United States and US Territories Now Available! - News & Announcements - Microsoft Flight Simulator Forums22 janeiro 2025 -
 Google Doodle temático das Olimpíadas traz minijogos retrô com várias modalidades - Correio de Minas22 janeiro 2025
Google Doodle temático das Olimpíadas traz minijogos retrô com várias modalidades - Correio de Minas22 janeiro 2025 -
 Portal Cast 81 - Nova PS Plus x Gamepass22 janeiro 2025
Portal Cast 81 - Nova PS Plus x Gamepass22 janeiro 2025 -
You are an Idiot Popups's Code & Price - RblxTrade22 janeiro 2025
-
 Why Chainsaw Man Fans Don't Want MAPPA to Take Over Season 222 janeiro 2025
Why Chainsaw Man Fans Don't Want MAPPA to Take Over Season 222 janeiro 2025 -
 Jogo Perguntados De Tabuleiro Com Cartas 360 Perguntas Menino Menina Brinquedo Infantil 8 Anos22 janeiro 2025
Jogo Perguntados De Tabuleiro Com Cartas 360 Perguntas Menino Menina Brinquedo Infantil 8 Anos22 janeiro 2025 -
 Rock 'em Sock 'em Robots Game for sale online22 janeiro 2025
Rock 'em Sock 'em Robots Game for sale online22 janeiro 2025 -
![An American Werewolf in London [4K Ultra HD Blu-ray/Blu-ray] [1981] - Best Buy](https://pisces.bbystatic.com/image2/BestBuy_US/images/products/afc7f3ee-639a-4627-a314-6c423b6ff6af.jpg) An American Werewolf in London [4K Ultra HD Blu-ray/Blu-ray] [1981] - Best Buy22 janeiro 2025
An American Werewolf in London [4K Ultra HD Blu-ray/Blu-ray] [1981] - Best Buy22 janeiro 2025