TeamTNT Script Employed to Grab AWS Credentials - Cado Security
Por um escritor misterioso
Last updated 22 fevereiro 2025
TeamTNT script has been employed to target a Confluence vulnerability that grabs AWS credentials including those from ECS.
Malware using new Ezuri memory loader

Team TNT – The First Crypto-Mining Worm to Steal AWS Credentials - Cado Security
Agile Approach to mass cloud credential harvesting and crypto mining sprints ahead

SCARLETEEL Cryptojacking Campaign Exploiting AWS Fargate in Ongoing Campaign

AWS Archives - Security Affairs

Learning from AWS Customer Security Incidents [2022] - Speaker Deck

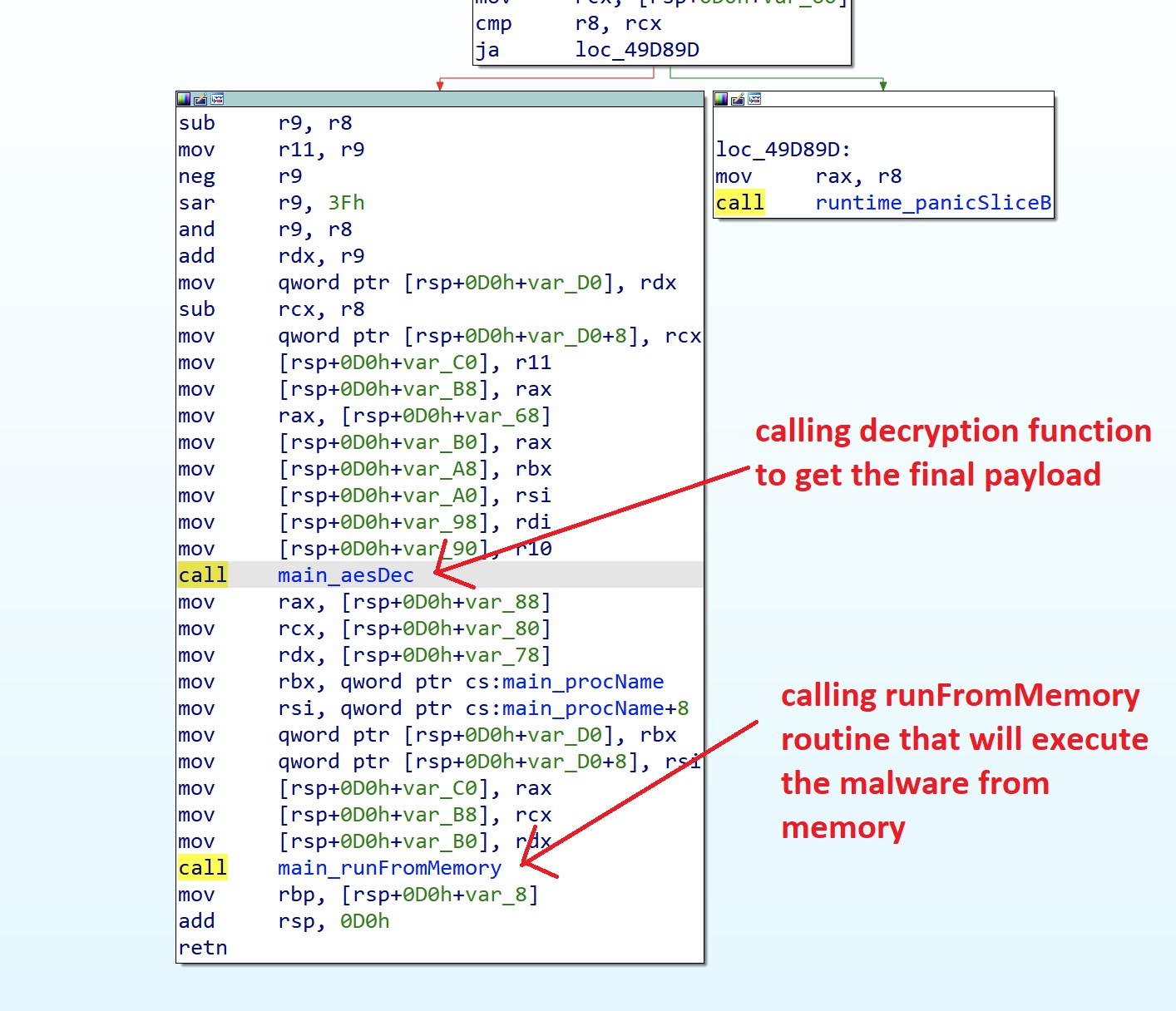
Previously Undiscovered TeamTNT Payload Recently Surfaced - Cado Security
Forensicating Threats in the Cloud - eForensics

Team TNT – The First Crypto-Mining Worm to Steal AWS Credentials - Cado Security
Recomendado para você
-
IP Grabber - Microsoft Apps22 fevereiro 2025
-
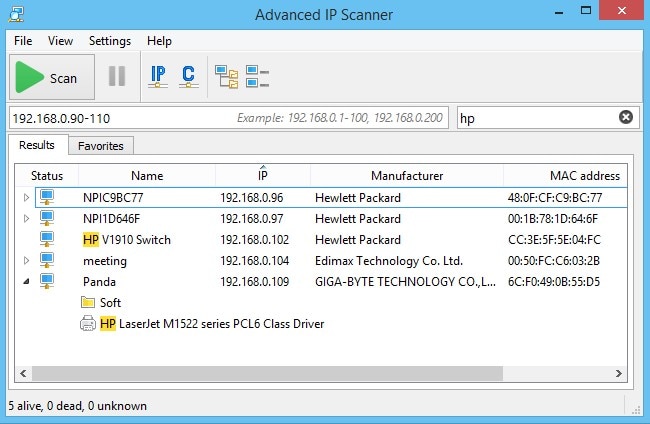 The 7 Best IP Address Trackers - DNSstuff22 fevereiro 2025
The 7 Best IP Address Trackers - DNSstuff22 fevereiro 2025 -
 Roblox Script Showcase IP Logger22 fevereiro 2025
Roblox Script Showcase IP Logger22 fevereiro 2025 -
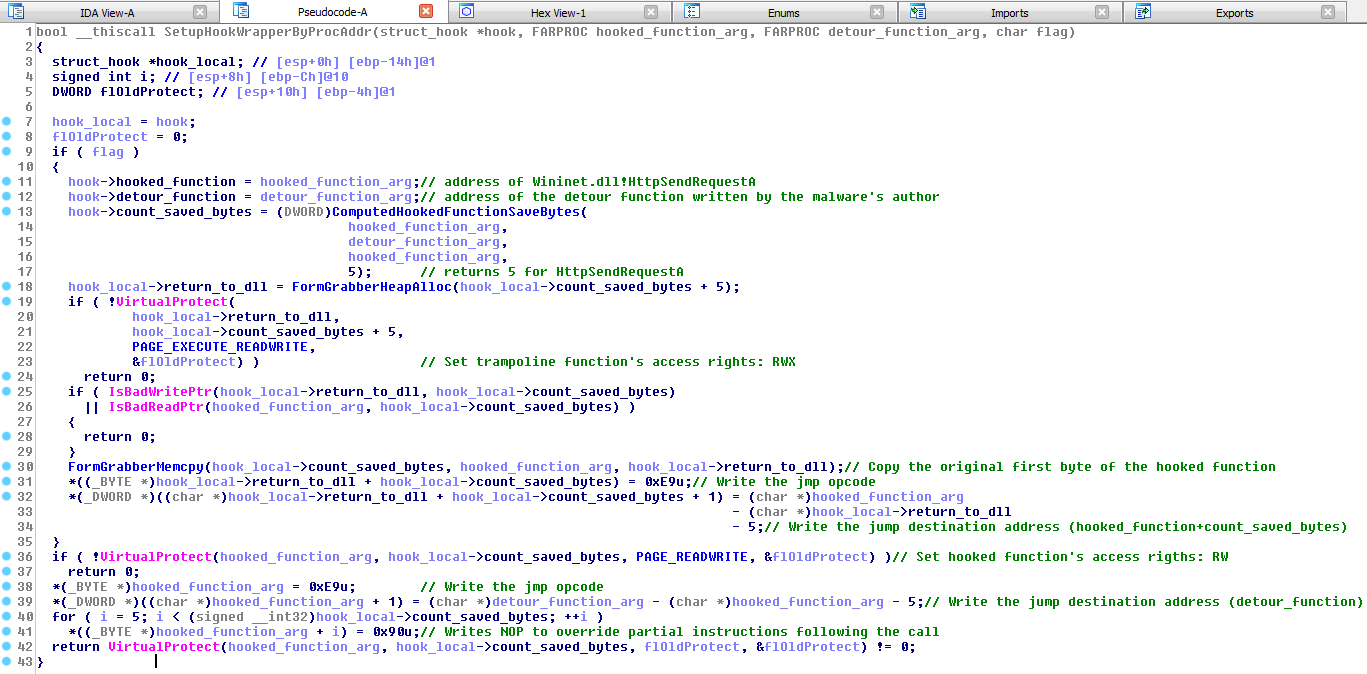 Analyzing a form-grabber malware - Stormshield22 fevereiro 2025
Analyzing a form-grabber malware - Stormshield22 fevereiro 2025 -
 How to know IP of UrlFetchApp in Google Apps Script? - Stack Overflow22 fevereiro 2025
How to know IP of UrlFetchApp in Google Apps Script? - Stack Overflow22 fevereiro 2025 -
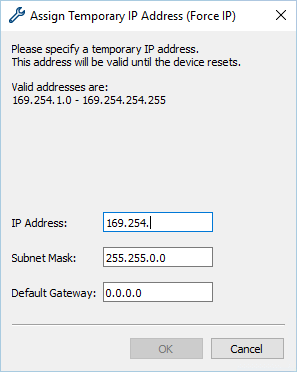 Assigning a Temporary IP Address to a Camera22 fevereiro 2025
Assigning a Temporary IP Address to a Camera22 fevereiro 2025 -
Discord Ip Address Grabber22 fevereiro 2025
-
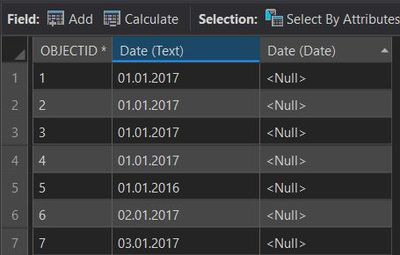
Solved: Convert text format to date format - Esri Community22 fevereiro 2025
-
 Public IP Grabber - Hak522 fevereiro 2025
Public IP Grabber - Hak522 fevereiro 2025 -
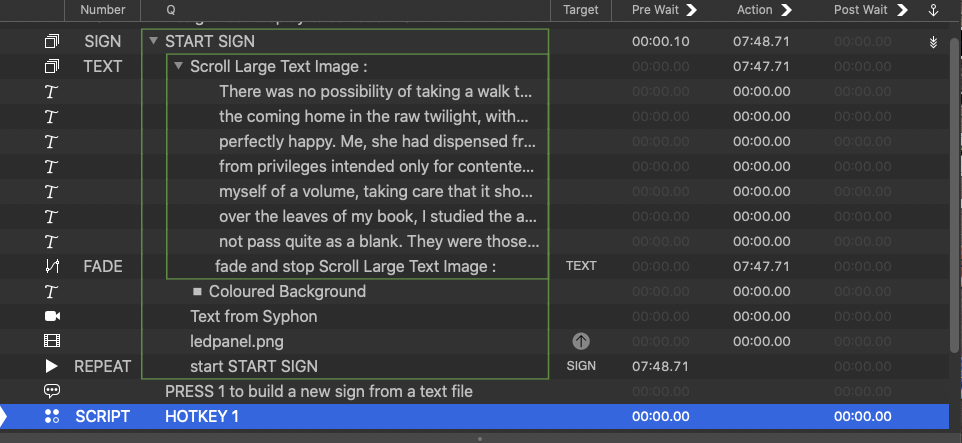 Text scroll for Credits shows solid white22 fevereiro 2025
Text scroll for Credits shows solid white22 fevereiro 2025
você pode gostar
-
![AmiAmi [Character & Hobby Shop] Pokemon Ultra Sun Ultra Moon Official Guidebook Official Pokemon Nationwide Pokedex 2018 (BOOK)(Released)](https://img.amiami.com/images/product/main/174/MED-BOOK-010632.jpg) AmiAmi [Character & Hobby Shop] Pokemon Ultra Sun Ultra Moon Official Guidebook Official Pokemon Nationwide Pokedex 2018 (BOOK)(Released)22 fevereiro 2025
AmiAmi [Character & Hobby Shop] Pokemon Ultra Sun Ultra Moon Official Guidebook Official Pokemon Nationwide Pokedex 2018 (BOOK)(Released)22 fevereiro 2025 -
 T-Shirt Classic Camiseta 7 Pecados Capitais Meliodas R$69,90 em Vestindo Nerds22 fevereiro 2025
T-Shirt Classic Camiseta 7 Pecados Capitais Meliodas R$69,90 em Vestindo Nerds22 fevereiro 2025 -
![The Great Ace Attorney Chronicles [Online Game Code]](https://c1.neweggimages.com/productimage/nb640/32-233-191-01.jpg) The Great Ace Attorney Chronicles [Online Game Code]22 fevereiro 2025
The Great Ace Attorney Chronicles [Online Game Code]22 fevereiro 2025 -
 Pra quem quiser a foto do meu perfil completa, tá aí.22 fevereiro 2025
Pra quem quiser a foto do meu perfil completa, tá aí.22 fevereiro 2025 -
 Mr beast do be big brain : r/memes22 fevereiro 2025
Mr beast do be big brain : r/memes22 fevereiro 2025 -
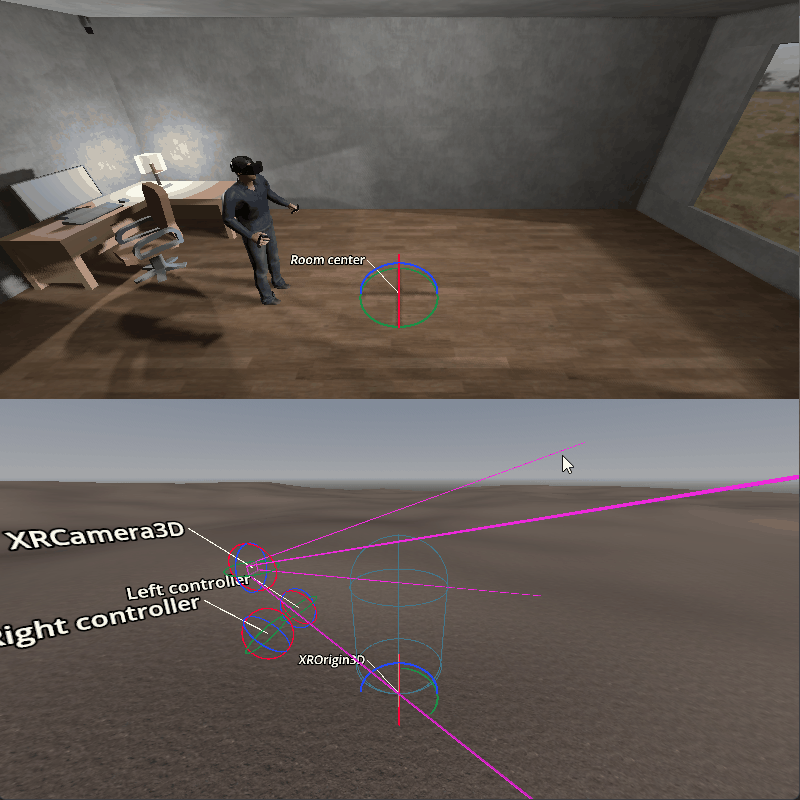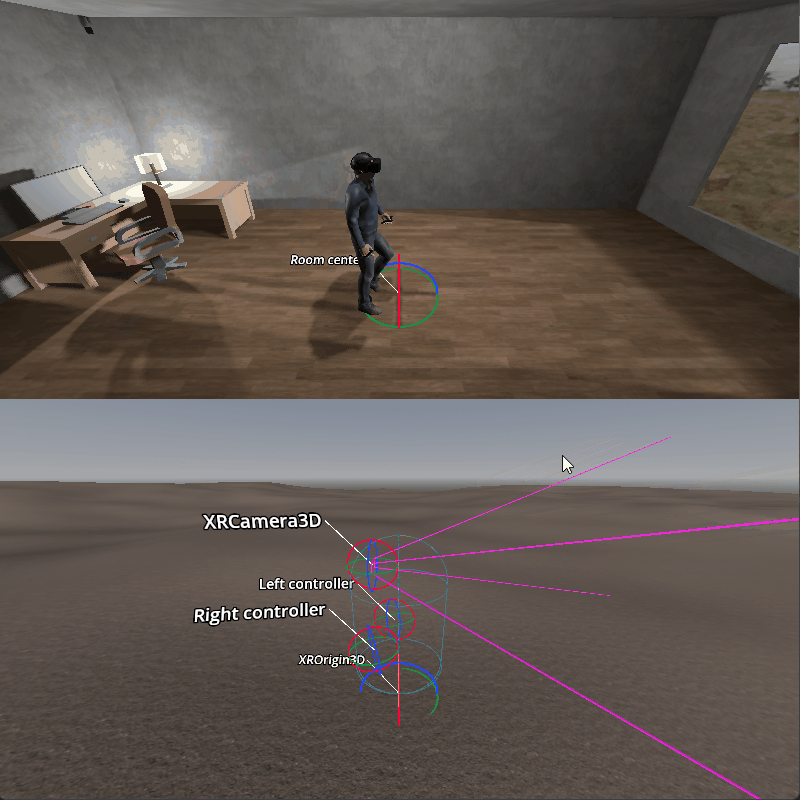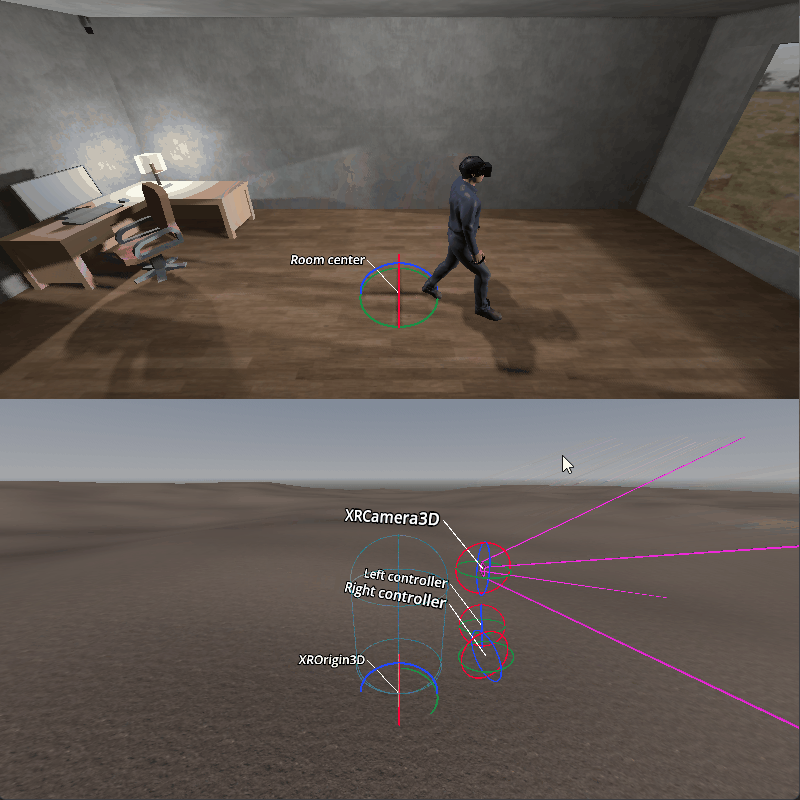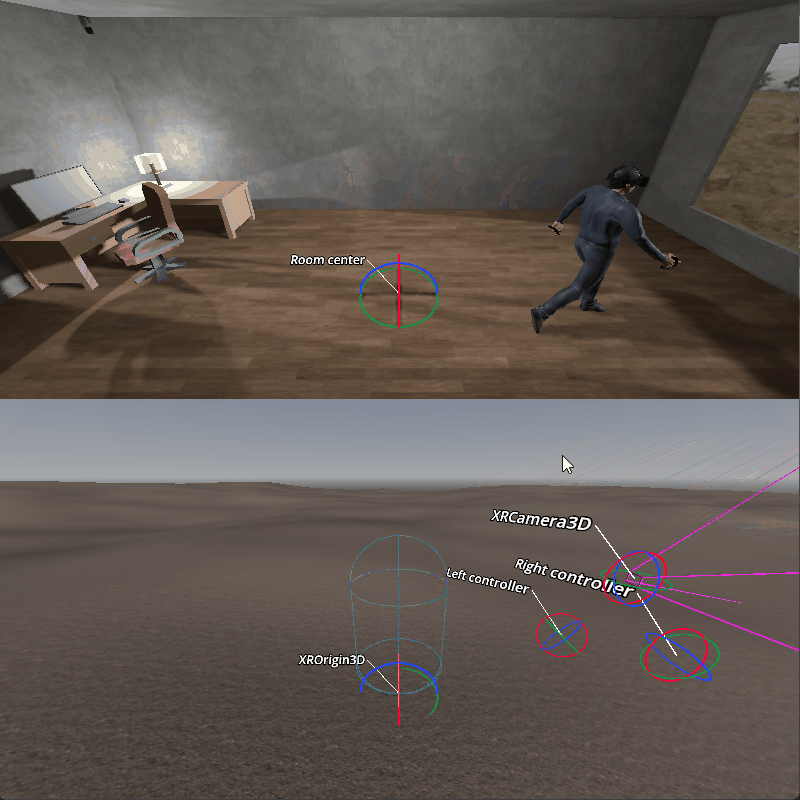 Room scale in XR — Documentación de Godot Engine (4.x) en español22 fevereiro 2025
Room scale in XR — Documentación de Godot Engine (4.x) en español22 fevereiro 2025 -
 Prime Video: Dragons: Nine Realms - Season 122 fevereiro 2025
Prime Video: Dragons: Nine Realms - Season 122 fevereiro 2025 -
Escape From The Garten Of BanBan Chapter 4 OBBY! - Roblox22 fevereiro 2025
-
 Carro controle remoto Super Car Corrida Divertida – DM Toys22 fevereiro 2025
Carro controle remoto Super Car Corrida Divertida – DM Toys22 fevereiro 2025 -
 Significado do nome Eloá: História e origem!22 fevereiro 2025
Significado do nome Eloá: História e origem!22 fevereiro 2025