HTB: Investigation
Por um escritor misterioso
Last updated 16 novembro 2024

Investigation starts with a website that accepts user uploaded images and runs Exiftool on them. This version has a command injection. I’ll dig into that vulnerability, and then exploit it to get a foothold. Then I find a set of Windows event logs, and analyze them to extract a password. Finally, I find a piece of malware that runs as root and understand it to get execution.
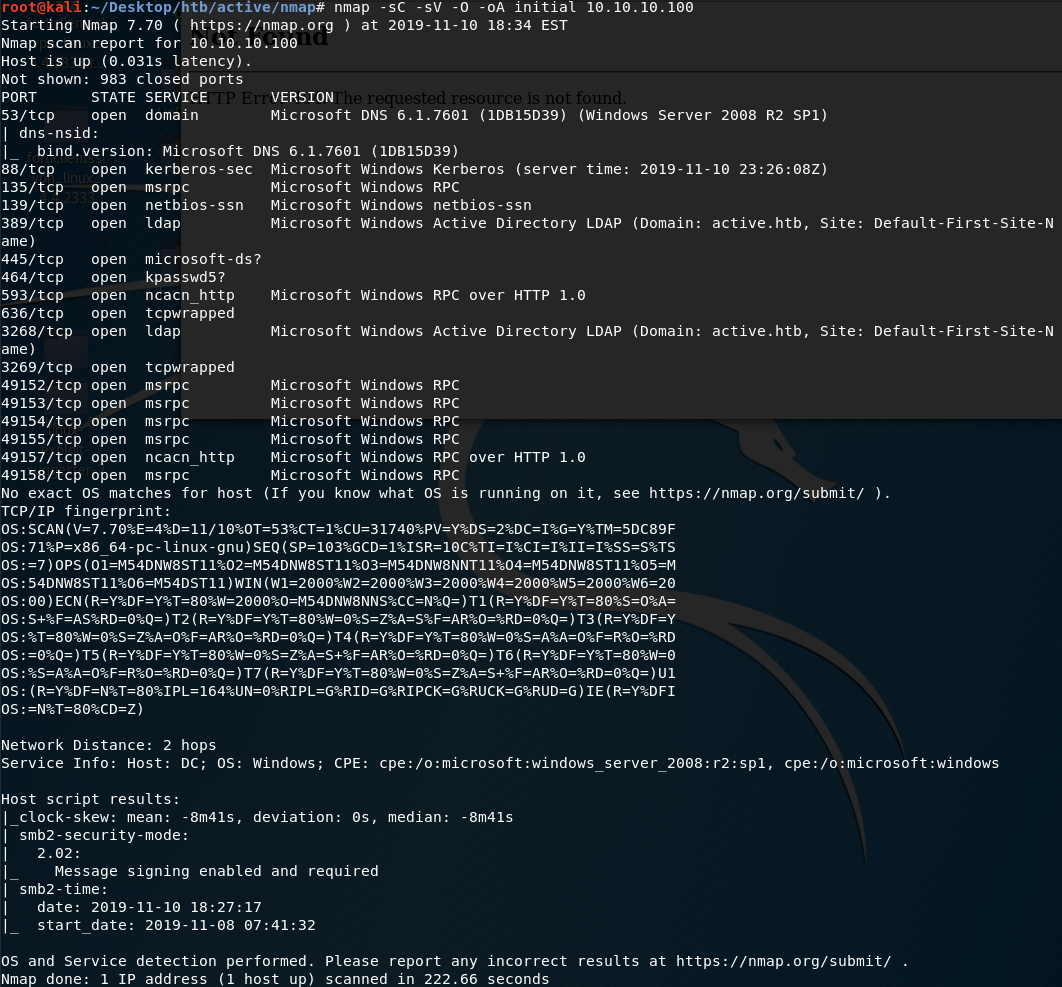
Active Writeup w/o Metasploit - Hack The Box OSCP Preparation

HTB: Investigation
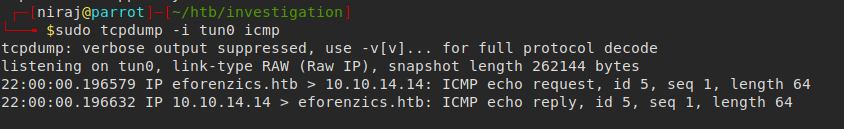
HTB — Investigation. A detailed walkthrough for solving…, by Niraj Kharel

HackTheBox Bolt walkthrough

How to buy police evidence management products (eBook)

Hack the Box (HTB) – Soccer – Lisandre

Walk-through of Union from HackTheBox

HTB Cyber Apocalypse 2023: Forensics - forensicskween

Approach for investigating the photobinding of HTB to HSA.
Recomendado para você
-
-min.png?locale=en) DigDig.IO Gold Bot16 novembro 2024
DigDig.IO Gold Bot16 novembro 2024 -
 Digdig.io Tips and Tricks16 novembro 2024
Digdig.io Tips and Tricks16 novembro 2024 -
 Hacks - Dig Dug Arcade Edition16 novembro 2024
Hacks - Dig Dug Arcade Edition16 novembro 2024 -
 DIG Hackathon — Disrupting The Industry From the Inside16 novembro 2024
DIG Hackathon — Disrupting The Industry From the Inside16 novembro 2024 -
 Playable 2600 Dig Dug-arcade gfx hack! - Atari 2600 Hacks16 novembro 2024
Playable 2600 Dig Dug-arcade gfx hack! - Atari 2600 Hacks16 novembro 2024 -
 Anthony J. D'Angelo Quote: “When solving problems, dig at the16 novembro 2024
Anthony J. D'Angelo Quote: “When solving problems, dig at the16 novembro 2024 -
 Try These 10 Financial Life Hacks16 novembro 2024
Try These 10 Financial Life Hacks16 novembro 2024 -
 Dig Dug Arcade Game Scoring Hack!16 novembro 2024
Dig Dug Arcade Game Scoring Hack!16 novembro 2024 -
 Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte :: WonderHowTo16 novembro 2024
Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte :: WonderHowTo16 novembro 2024 -
 Dig Muck: Craft Adventure Game for Android - Download16 novembro 2024
Dig Muck: Craft Adventure Game for Android - Download16 novembro 2024
você pode gostar
-
 Piercing Fake Argola Tubo Banhado Em Ouro 18k16 novembro 2024
Piercing Fake Argola Tubo Banhado Em Ouro 18k16 novembro 2024 -
 Bayonetta 3 Box Shot for Nintendo Switch - GameFAQs16 novembro 2024
Bayonetta 3 Box Shot for Nintendo Switch - GameFAQs16 novembro 2024 -
 Hades 2: From Ancient Titans to Forgotten Gods, Supergiant Games' Upcoming Sequel Is More Than Godly!16 novembro 2024
Hades 2: From Ancient Titans to Forgotten Gods, Supergiant Games' Upcoming Sequel Is More Than Godly!16 novembro 2024 -
 WTA China Open (Pequim): Resultados - Ténis - Jornal Record16 novembro 2024
WTA China Open (Pequim): Resultados - Ténis - Jornal Record16 novembro 2024 -
/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2022/3/c/BtdHYsRCAIBxaJV3XoCw/67ba6e6c-fccd-4c93-b439-c8655f34374d.jpg) Clube terá comissão técnica de fora do Acre, segundo presidente; peneira para base neste sábado, independência16 novembro 2024
Clube terá comissão técnica de fora do Acre, segundo presidente; peneira para base neste sábado, independência16 novembro 2024 -
![How to Play FreeCell Solitaire: Rules & Set-Up [8 Steps + Video]](https://online-solitaire.com/images/freecell_rules_0@2x.jpg) How to Play FreeCell Solitaire: Rules & Set-Up [8 Steps + Video]16 novembro 2024
How to Play FreeCell Solitaire: Rules & Set-Up [8 Steps + Video]16 novembro 2024 -
 Create meme the get red skin Nike, t shirt get the Nike, roblox16 novembro 2024
Create meme the get red skin Nike, t shirt get the Nike, roblox16 novembro 2024 -
 The Weeknd Shares New Video for 'Sacrifice' From Dawn FM - SPIN16 novembro 2024
The Weeknd Shares New Video for 'Sacrifice' From Dawn FM - SPIN16 novembro 2024 -
 Is Street Fighter 6 coming to Nintendo Switch? - Charlie INTEL16 novembro 2024
Is Street Fighter 6 coming to Nintendo Switch? - Charlie INTEL16 novembro 2024 -
id shirt code roblox brookhaven club soccer|TikTok Search16 novembro 2024
