Hacking, Cybersecurity
Por um escritor misterioso
Last updated 22 fevereiro 2025


Introduction to Defensive Hacking

In)Famous Hacking Groups - United States Cybersecurity Magazine

Importance of Ethical Hacking in Today's Cybersecurity Landscape

Navigating the Moral Ambiguity in the Ethics of Hacking

Cybersecurity Solutions Offensive Security Ethical Hacking - Cybersecurity Solutions
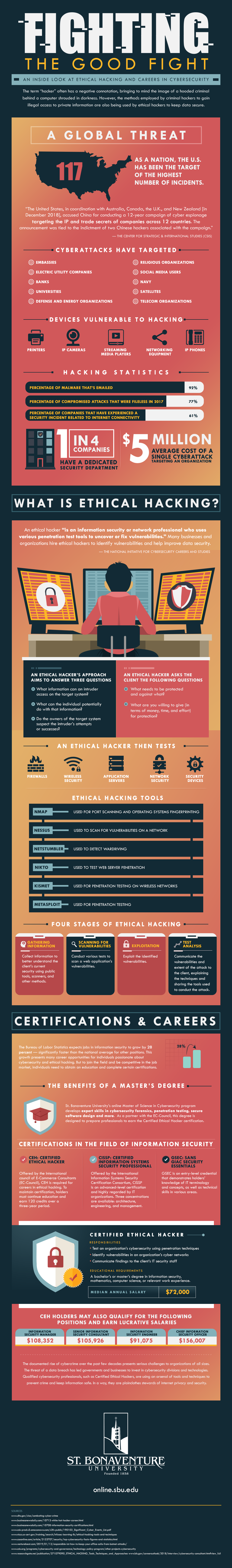
Cybersecurity: Fighting the Good Fight Infographic

Cyber security researchers become target of criminal hackers
Difference Between Cybersecurity and Ethical Hacking on 10 Crucial Metrics

The Role of Ethical Hacking in Strengthening Cybersecurity

Hacking healthcare: With 385M patient records exposed, cybersecurity experts sound alarm on breach surge

As Hackers Get Smarter, Cyber Security Experts Turn to New Ideas - IEEE Innovation at Work

What is Cybersecurity and Ethical Hacking? - Scaler Topics
Recomendado para você
-
 Appdome Agile Mobile Cheat Prevention in Android and iOS Apps22 fevereiro 2025
Appdome Agile Mobile Cheat Prevention in Android and iOS Apps22 fevereiro 2025 -
 The secret world of malware-like cheats in video games22 fevereiro 2025
The secret world of malware-like cheats in video games22 fevereiro 2025 -
How to hack a mobile game - Quora22 fevereiro 2025
-
 FAQ - Painter22 fevereiro 2025
FAQ - Painter22 fevereiro 2025 -
 Hacking Android Games using GameGuardian for Beginners22 fevereiro 2025
Hacking Android Games using GameGuardian for Beginners22 fevereiro 2025 -
 How to Hack any Android Emulator Game using Cheat Engine on PC22 fevereiro 2025
How to Hack any Android Emulator Game using Cheat Engine on PC22 fevereiro 2025 -
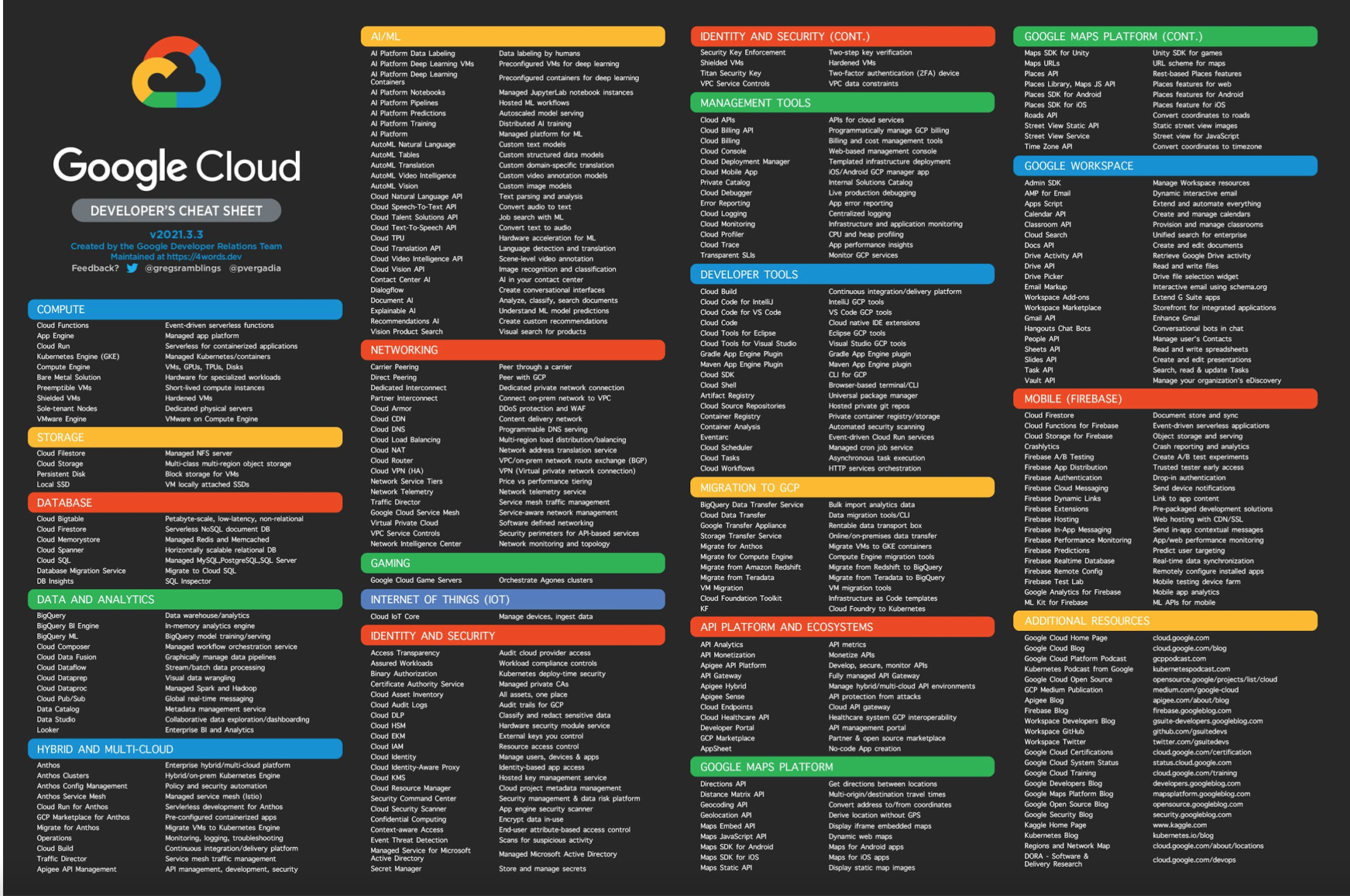 5 cheat sheets to help you get started with Google Cloud - Cloudfresh22 fevereiro 2025
5 cheat sheets to help you get started with Google Cloud - Cloudfresh22 fevereiro 2025 -
Latest technologies in world - Microsoft Apps22 fevereiro 2025
-
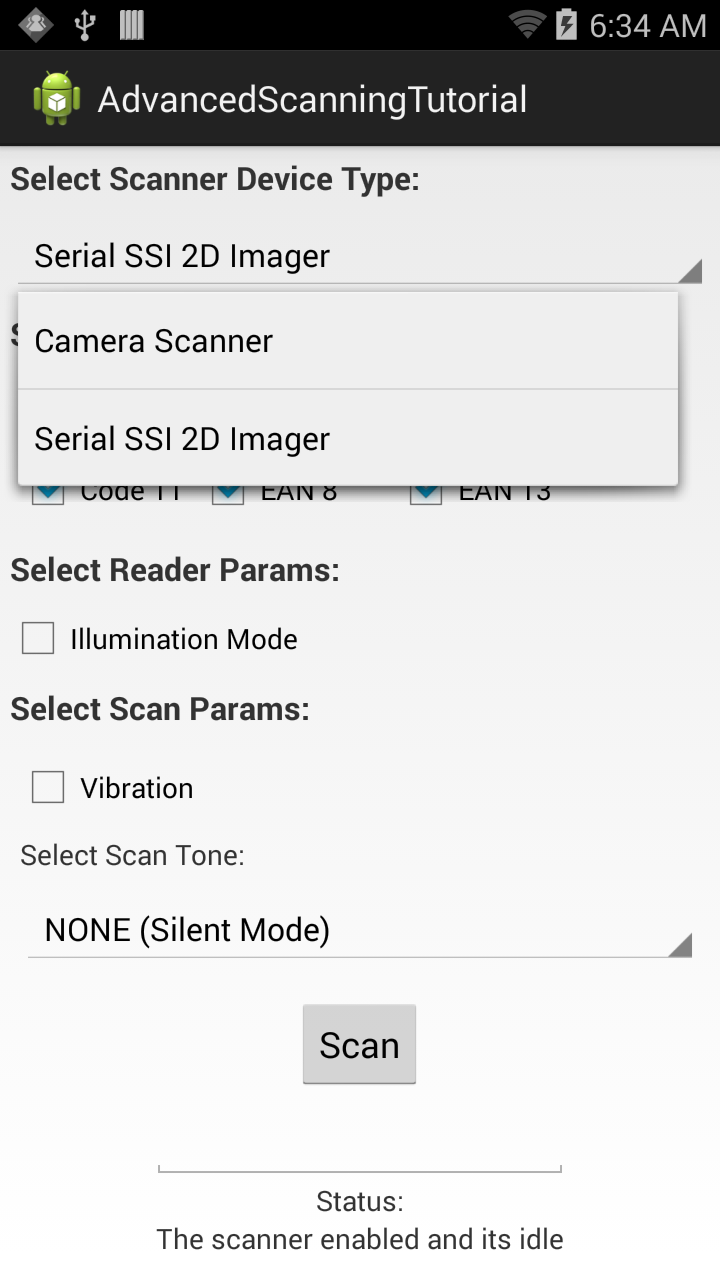 Advanced Scanning Tutorial using Barcode API - Zebra Technologies22 fevereiro 2025
Advanced Scanning Tutorial using Barcode API - Zebra Technologies22 fevereiro 2025 -
About: Cheat Engine for Android Tips (Google Play version22 fevereiro 2025
você pode gostar
-
 Fiat uno Mille : r/carros22 fevereiro 2025
Fiat uno Mille : r/carros22 fevereiro 2025 -
 PASSO A PASSO COMO INSTALAR JOGOS NO NINTENDO SWITCH DESBLOQUEADO ATMOSPHERE VIA TINFOIL - AE Games22 fevereiro 2025
PASSO A PASSO COMO INSTALAR JOGOS NO NINTENDO SWITCH DESBLOQUEADO ATMOSPHERE VIA TINFOIL - AE Games22 fevereiro 2025 -
/cdn.vox-cdn.com/uploads/chorus_asset/file/23177603/1563424.jpg) Microsoft's Activision acquisition: What franchises does it own now? - Polygon22 fevereiro 2025
Microsoft's Activision acquisition: What franchises does it own now? - Polygon22 fevereiro 2025 -
 Spy, Town of Salem Wiki22 fevereiro 2025
Spy, Town of Salem Wiki22 fevereiro 2025 -
 Jogo Forza Horizon - Xbox 360 Seminovo - SL Shop - A melhor loja22 fevereiro 2025
Jogo Forza Horizon - Xbox 360 Seminovo - SL Shop - A melhor loja22 fevereiro 2025 -
 World of Warcraft Alliance & Horde Cotton Lycra – Purpleseamstress Fabric22 fevereiro 2025
World of Warcraft Alliance & Horde Cotton Lycra – Purpleseamstress Fabric22 fevereiro 2025 -
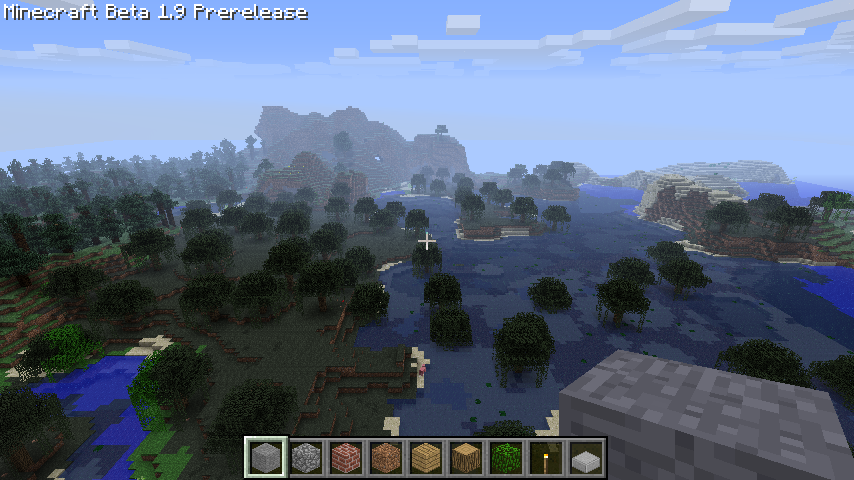 Java Edition Beta 1.9 Prerelease – Minecraft Wiki22 fevereiro 2025
Java Edition Beta 1.9 Prerelease – Minecraft Wiki22 fevereiro 2025 -
 MOD-MASTER for Roblox - APK Download for Android22 fevereiro 2025
MOD-MASTER for Roblox - APK Download for Android22 fevereiro 2025 -
 Watch Si Ge Yongzhe English Subbed in HD on 9anime22 fevereiro 2025
Watch Si Ge Yongzhe English Subbed in HD on 9anime22 fevereiro 2025 -
 Ada Wong (Resident Evil 4)22 fevereiro 2025
Ada Wong (Resident Evil 4)22 fevereiro 2025