Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 18 dezembro 2024

Network Hacker Stickers for Sale
Metasploit Tutorial for Beginners - Basics to Advanced
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview) « Null Byte :: WonderHowTo

The hackers manual 2015 revised edition by Gerson Villa Gonzalez - Issuu
GitHub - Micle5858/PENTESTING-BIBLE
How to Install the Command Line Developer Tools Without Xcode « Mac OS Tips :: Gadget Hacks

D-Link, IoT Devices Under Attack By Tor-Based Gafgyt Variant - vulnerability database
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution

Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X « Mac OS Tips :: Gadget Hacks

ENISA Threat Landscape Report 2016
Shellshock vulnerability for beginners - Hackercool Magazine
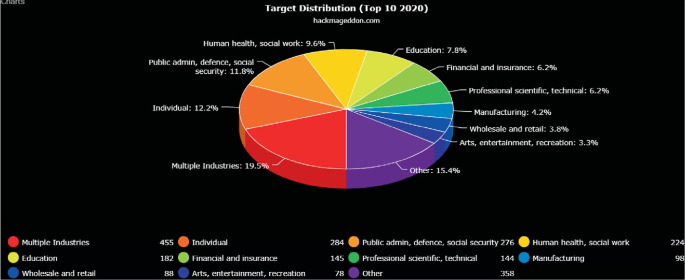
Determining Vulnerabilities of Pervasive IoT Devices and Their Geographic Distribution

Hack Like a Pro « Null Byte :: WonderHowTo
Recomendado para você
-
Buy ShellShock Live - Microsoft Store en-IL18 dezembro 2024
-
 The Internet Braces for the Crazy Shellshock Worm18 dezembro 2024
The Internet Braces for the Crazy Shellshock Worm18 dezembro 2024 -
 Shellshock: 'Deadly serious' new vulnerability found - BBC News18 dezembro 2024
Shellshock: 'Deadly serious' new vulnerability found - BBC News18 dezembro 2024 -
 Yahoo hack wasn't Shellshock, company claims, The Independent18 dezembro 2024
Yahoo hack wasn't Shellshock, company claims, The Independent18 dezembro 2024 -
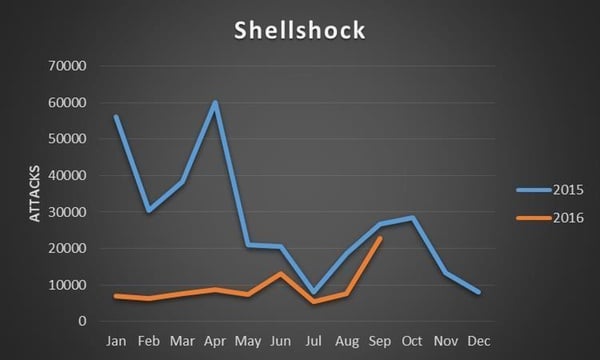 Shellshock two years on – has your company forgotten about it?18 dezembro 2024
Shellshock two years on – has your company forgotten about it?18 dezembro 2024 -
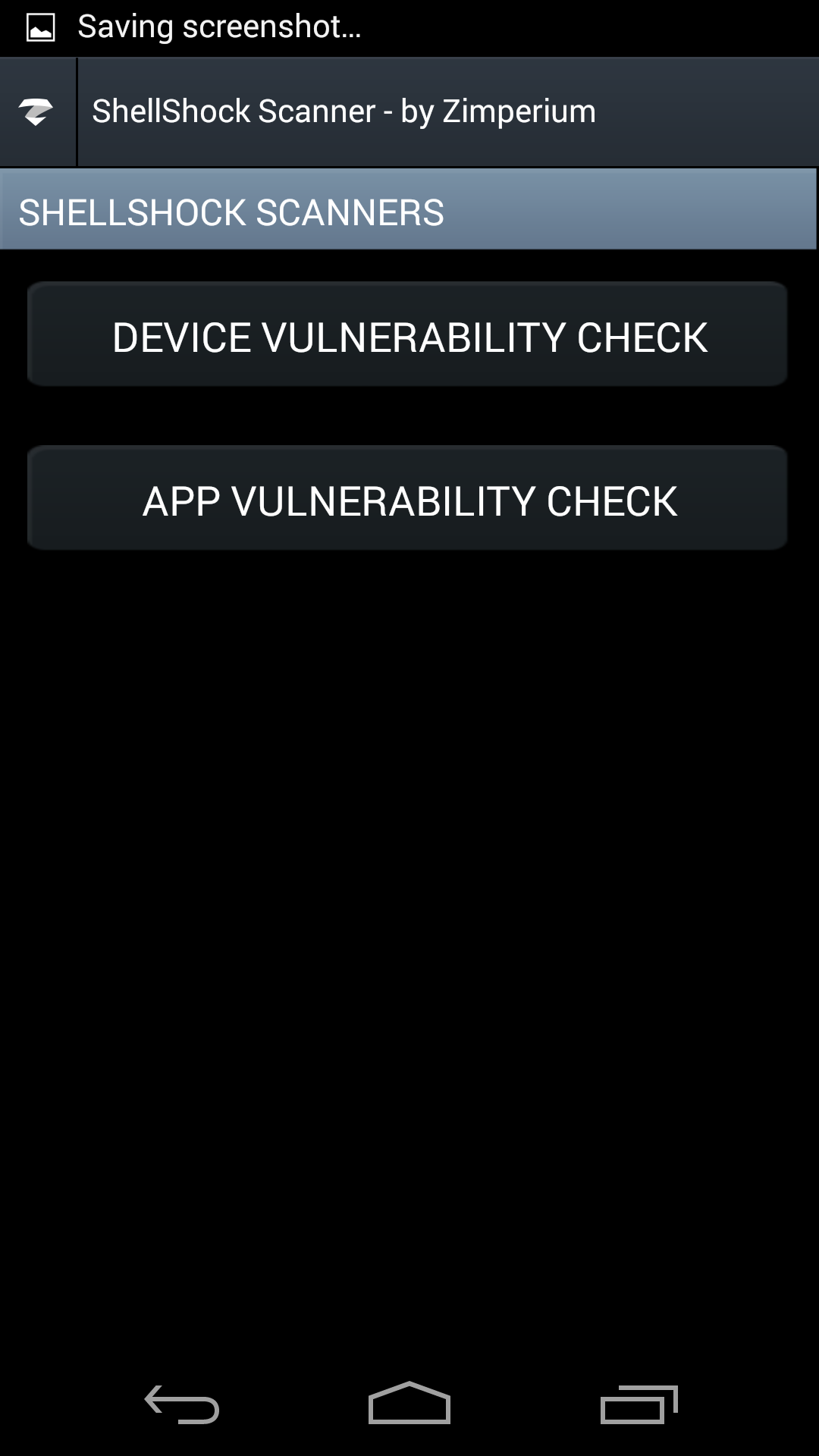 Shellshock – Find out if your mobile device is vulnerable - Zimperium18 dezembro 2024
Shellshock – Find out if your mobile device is vulnerable - Zimperium18 dezembro 2024 -
 Successfully Tackling Shellshock Vulnerability18 dezembro 2024
Successfully Tackling Shellshock Vulnerability18 dezembro 2024 -
 Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent18 dezembro 2024
Shellshock: Romanian hackers are accessing Yahoo servers, claims security expert, The Independent18 dezembro 2024 -
.jpg&h=420&w=748&c=0&s=0) Privacy Commissioner warns business to fix Shellshock - Security - iTnews18 dezembro 2024
Privacy Commissioner warns business to fix Shellshock - Security - iTnews18 dezembro 2024 -
 Kali Linux Web Penetration Testing Cookbook18 dezembro 2024
Kali Linux Web Penetration Testing Cookbook18 dezembro 2024
você pode gostar
-
 Pokemon XYZ: The Greatest Pokemon anime18 dezembro 2024
Pokemon XYZ: The Greatest Pokemon anime18 dezembro 2024 -
Spicy Roblox Memes18 dezembro 2024
-
 O Xbox está trabalhando com fabricantes de TV para trazer jogos em18 dezembro 2024
O Xbox está trabalhando com fabricantes de TV para trazer jogos em18 dezembro 2024 -
 AnimeLab Announces More Titles for Fall Simulcast Lineup - News - Anime News Network18 dezembro 2024
AnimeLab Announces More Titles for Fall Simulcast Lineup - News - Anime News Network18 dezembro 2024 -
 Na vida, no trabalho e no amor. Não Gilles Bruno Benicio - Pensador18 dezembro 2024
Na vida, no trabalho e no amor. Não Gilles Bruno Benicio - Pensador18 dezembro 2024 -
 Neelam Giri, M.D., M.B.B.S., biographical sketch and research interests - NCI18 dezembro 2024
Neelam Giri, M.D., M.B.B.S., biographical sketch and research interests - NCI18 dezembro 2024 -
 NCAA volleyball semifinals: Texas rolls past Wisconsin 3-1, returns to finals to face Nebraska Cornhuskers18 dezembro 2024
NCAA volleyball semifinals: Texas rolls past Wisconsin 3-1, returns to finals to face Nebraska Cornhuskers18 dezembro 2024 -
 Tensei Shitara Slime Datta Ken Chapter 111: Tournament - Finals Part 618 dezembro 2024
Tensei Shitara Slime Datta Ken Chapter 111: Tournament - Finals Part 618 dezembro 2024 -
 Scarlet Nexus Mods Pack for RE4 200718 dezembro 2024
Scarlet Nexus Mods Pack for RE4 200718 dezembro 2024 -
 Mão De Desenho Animado Desenhado Equitação Motocicleta Menino18 dezembro 2024
Mão De Desenho Animado Desenhado Equitação Motocicleta Menino18 dezembro 2024