Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 19 dezembro 2024

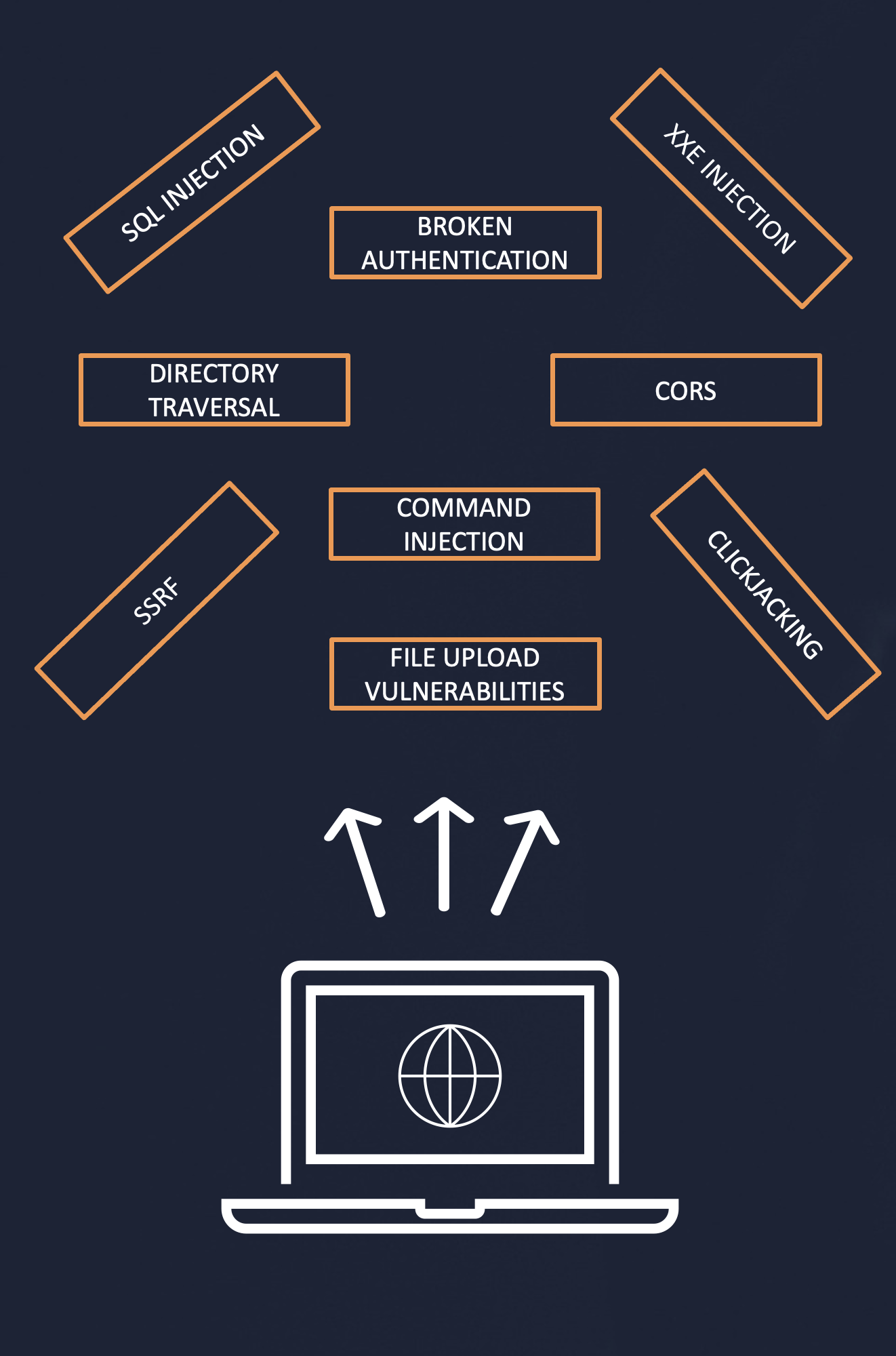
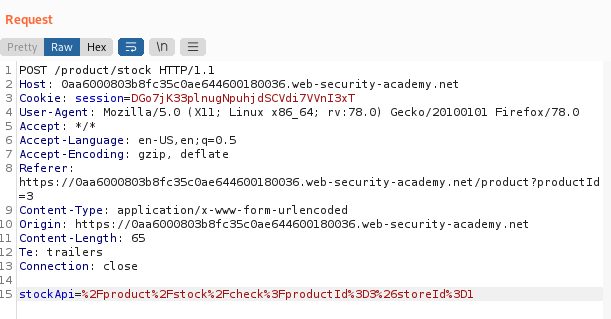
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

Free Cybersecurity & Hacking Training

Attacking Common Applications Course
Web Security Academy Series Course

HackMD - Collaborative Markdown Knowledge Base

Gaining Access through Server-side Request Forgery

Web application security in Java > Cydrill Software Security

Blind SSRF with Shellshock exploitation (Video Solution)
Solving PortSwigger SSRF Labs - Final Part - ::: re:search + re

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai

Linux Exploitation – Shellshock exploit and privilege escalation
A Glossary of Blind SSRF Chains – Assetnote
Server Side Request Forgery (SSRF) Zafiyeti Nedir? - BGA Cyber
Server Side Request Forgery (SSRF) Zafiyeti Nedir? - BGA Cyber

PortSwigger SSRF Labs. Hey all! This write-up is about my…
Recomendado para você
-
 Shellshock (software bug) - Wikipedia19 dezembro 2024
Shellshock (software bug) - Wikipedia19 dezembro 2024 -
 Shellshock: 'Deadly serious' new vulnerability found - BBC News19 dezembro 2024
Shellshock: 'Deadly serious' new vulnerability found - BBC News19 dezembro 2024 -
 About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Wiadomości bezpieczeństwa19 dezembro 2024
About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Wiadomości bezpieczeństwa19 dezembro 2024 -
 Watch How Hackers Are Exploiting the Shellshock Flaw - Bloomberg19 dezembro 2024
Watch How Hackers Are Exploiting the Shellshock Flaw - Bloomberg19 dezembro 2024 -
 Shellshock In-Depth: Why This Old Vulnerability Won't Go Away19 dezembro 2024
Shellshock In-Depth: Why This Old Vulnerability Won't Go Away19 dezembro 2024 -
 BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek19 dezembro 2024
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek19 dezembro 2024 -
 Hackers seize Apple computers as Shellshock cyber bug strikes19 dezembro 2024
Hackers seize Apple computers as Shellshock cyber bug strikes19 dezembro 2024 -
Stephane Chazelas: the man who found the web's 'most dangerous' internet security bug19 dezembro 2024
-
 Shellshock Vulnerability Exploitation and Mitigation: A Demonstration19 dezembro 2024
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration19 dezembro 2024 -
 Are you suffering from ShellShock? - Infosec Partners19 dezembro 2024
Are you suffering from ShellShock? - Infosec Partners19 dezembro 2024
você pode gostar
-
 Divine-pride.net Monster - Rigid Lava Golem 0D1 in 202319 dezembro 2024
Divine-pride.net Monster - Rigid Lava Golem 0D1 in 202319 dezembro 2024 -
 Toxic Waste Slime Licker Blue Razz Soda19 dezembro 2024
Toxic Waste Slime Licker Blue Razz Soda19 dezembro 2024 -
 Black Adam to Remains in Top Spot at Box Office for Third Straight Weekend19 dezembro 2024
Black Adam to Remains in Top Spot at Box Office for Third Straight Weekend19 dezembro 2024 -
 DancePlug on X: Audition for Tournament of Kings: Seeking dancers for close interaction with audience members & dancing upon a sand-covered surface, for the Tournament of Kings, a medieval-themed jousting show currently19 dezembro 2024
DancePlug on X: Audition for Tournament of Kings: Seeking dancers for close interaction with audience members & dancing upon a sand-covered surface, for the Tournament of Kings, a medieval-themed jousting show currently19 dezembro 2024 -
 Qual fruta divina do One Piece você teria?19 dezembro 2024
Qual fruta divina do One Piece você teria?19 dezembro 2024 -
 Download do APK de Legendary Hero Slots - Casino para Android19 dezembro 2024
Download do APK de Legendary Hero Slots - Casino para Android19 dezembro 2024 -
Jogada Excelente on X: Pokémon GO: Giratina Forma Alterada será o próximo Chefe de Reides 5 Estrelas. Confira quais são os counters recomendados e se prepare! ⠀ Data: 12/10 às 10h a19 dezembro 2024
-
 Nintendo Direct: Nintendo Direct 2023: Time, games, where to watch19 dezembro 2024
Nintendo Direct: Nintendo Direct 2023: Time, games, where to watch19 dezembro 2024 -
Inhibition of the Decomposition Pathways of Ruthenium Olefin Metathesis Catalysts: Development of Highly Efficient Catalysts for Ethenolysis19 dezembro 2024
-
 Alphabet Lore Humans In Gacha Club Part 1 by UnicornButterfly90019 dezembro 2024
Alphabet Lore Humans In Gacha Club Part 1 by UnicornButterfly90019 dezembro 2024