Malware analysis Malicious activity
Por um escritor misterioso
Last updated 21 fevereiro 2025
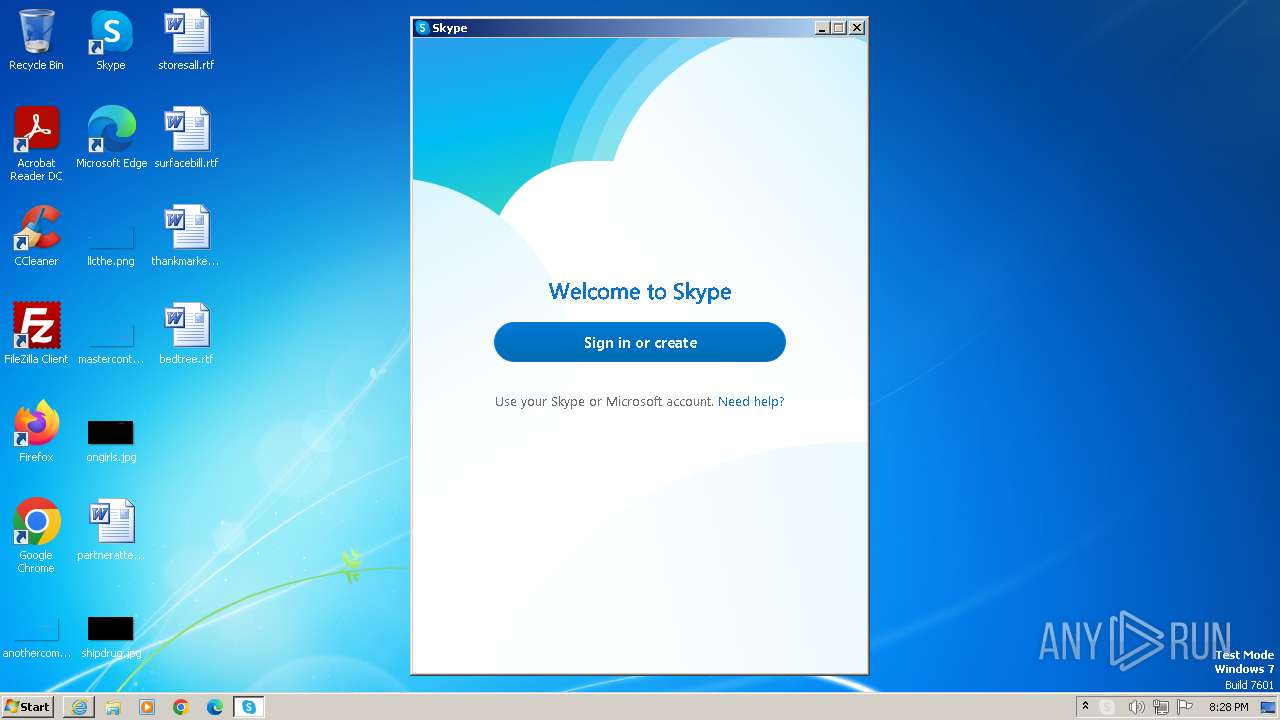

Info stealers and how to protect against them
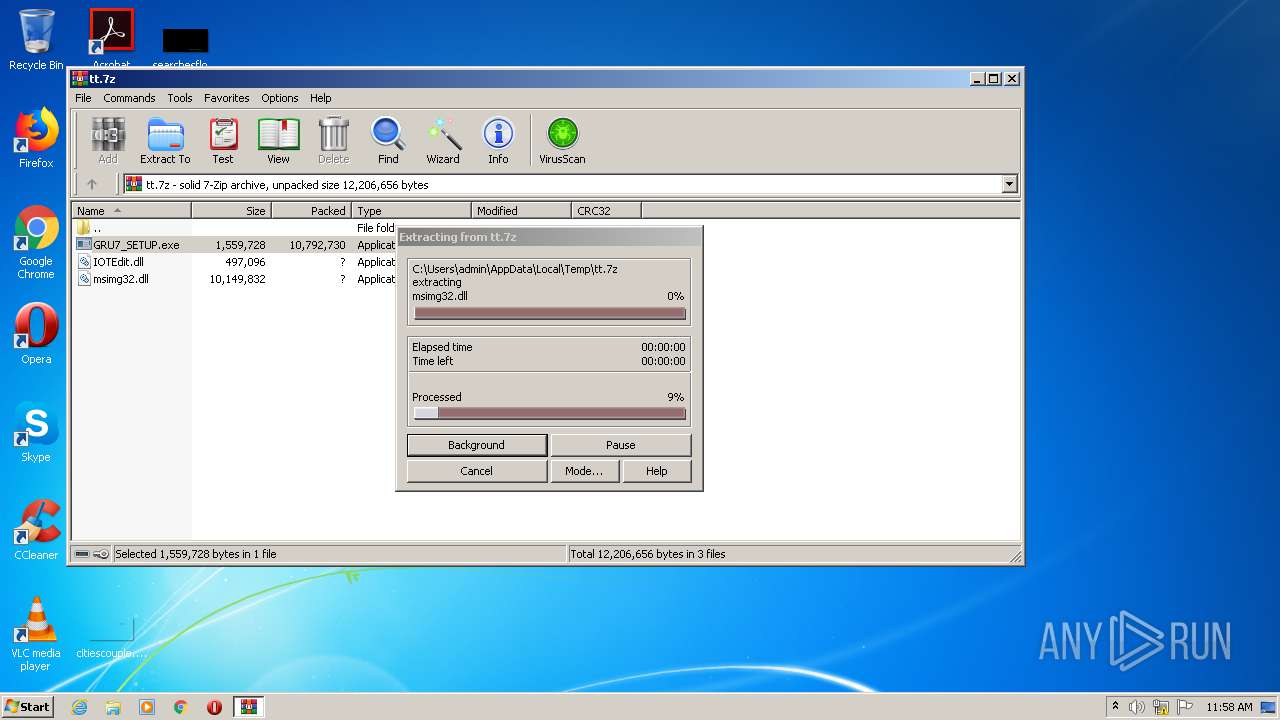
Malware analysis tt.7z Malicious activity
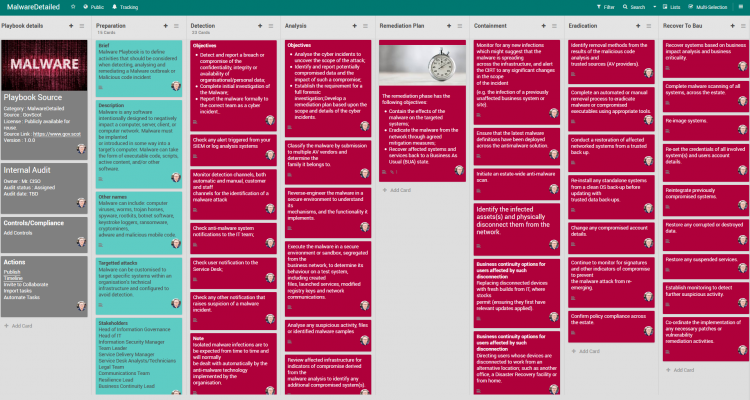
Playbook for Malware outbreak

What is Malware? Definition, Types, Prevention - TechTarget

Malware Analysis: Steps & Examples - CrowdStrike

How to Do Malware Analysis?

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware analysis Program_Install_and_Uninstall Malicious activity

Remediation and Malware Detection Overview

What is Malware? Definition, Types, Prevention - TechTarget
Recomendado para você
-
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack21 fevereiro 2025
-
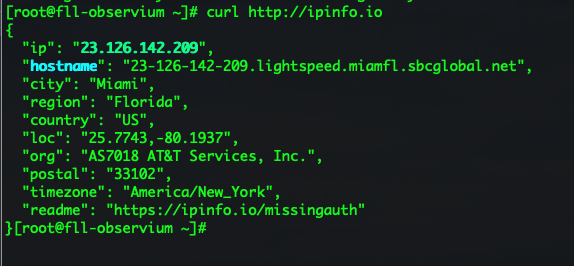 Doing “IP Chicken” from the CLI – InfoSec Monkey21 fevereiro 2025
Doing “IP Chicken” from the CLI – InfoSec Monkey21 fevereiro 2025 -
 IP Chicken - Wat is mijn IP adres? ip adres opzoeken21 fevereiro 2025
IP Chicken - Wat is mijn IP adres? ip adres opzoeken21 fevereiro 2025 -
ipchicken.com Competitors - Top Sites Like ipchicken.com21 fevereiro 2025
-
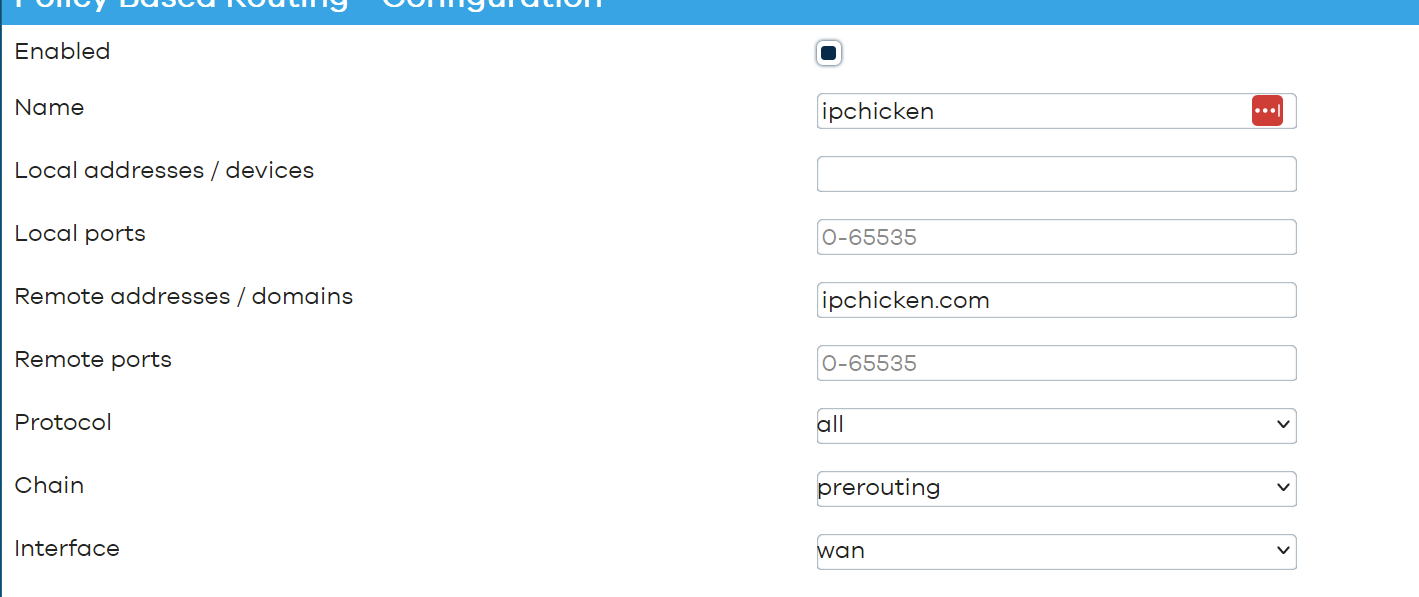 PBR with MulladVPN - Network and Wireless Configuration - OpenWrt Forum21 fevereiro 2025
PBR with MulladVPN - Network and Wireless Configuration - OpenWrt Forum21 fevereiro 2025 -
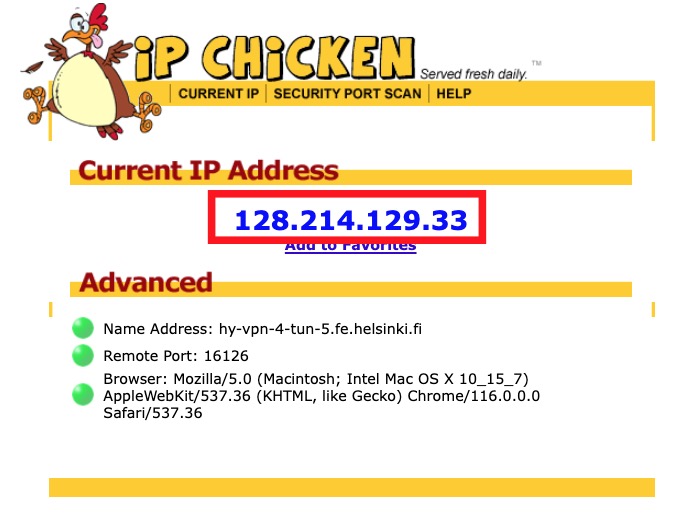 HY-VPN – Checking functionality and errors (Linux)21 fevereiro 2025
HY-VPN – Checking functionality and errors (Linux)21 fevereiro 2025 -
 ipchickenhawk.com - What is my IP Address - whatsm - IP Chickenhawk21 fevereiro 2025
ipchickenhawk.com - What is my IP Address - whatsm - IP Chickenhawk21 fevereiro 2025 -
 Delicious Chicken Stock in your Instant Pot - JennCaffeinated21 fevereiro 2025
Delicious Chicken Stock in your Instant Pot - JennCaffeinated21 fevereiro 2025 -
 Instant Pot Whole Chicken: Whole30, Paleo, Keto, Easy! - Whole Kitchen Sink21 fevereiro 2025
Instant Pot Whole Chicken: Whole30, Paleo, Keto, Easy! - Whole Kitchen Sink21 fevereiro 2025 -
 Automated IPv4 SOCKS5 Proxy Generator and Management Script21 fevereiro 2025
Automated IPv4 SOCKS5 Proxy Generator and Management Script21 fevereiro 2025
você pode gostar
-
 Acromiumeral - Dicio, Dicionário Online de Português21 fevereiro 2025
Acromiumeral - Dicio, Dicionário Online de Português21 fevereiro 2025 -
 Discover - INPRNT21 fevereiro 2025
Discover - INPRNT21 fevereiro 2025 -
 Blox Fruits Script Mobile Script - Blox Fruit Script21 fevereiro 2025
Blox Fruits Script Mobile Script - Blox Fruit Script21 fevereiro 2025 -
 MORTAL KOMBAT X 1.1.0 Apk Mod - Apk Data Mod21 fevereiro 2025
MORTAL KOMBAT X 1.1.0 Apk Mod - Apk Data Mod21 fevereiro 2025 -
 Phoenix Wright: Ace Attorney - Um jogo LEGAL21 fevereiro 2025
Phoenix Wright: Ace Attorney - Um jogo LEGAL21 fevereiro 2025 -
 Top Skyrim Player Home Mods: Mansion Edition - KeenGamer21 fevereiro 2025
Top Skyrim Player Home Mods: Mansion Edition - KeenGamer21 fevereiro 2025 -
 World of Nintendo 91424 2.5 Cat Mario Action Figure : Toys & Games21 fevereiro 2025
World of Nintendo 91424 2.5 Cat Mario Action Figure : Toys & Games21 fevereiro 2025 -
 Mega Database 2023: el juego moderno magistral21 fevereiro 2025
Mega Database 2023: el juego moderno magistral21 fevereiro 2025 -
 Fall Guys - Official Arcade Classics Pack Trailer - IGN21 fevereiro 2025
Fall Guys - Official Arcade Classics Pack Trailer - IGN21 fevereiro 2025 -
POU BOMBADO #f #fypシ #fyp #fy #you #for #status #foryoupage #foryou #f21 fevereiro 2025
