Malware analysis Malicious activity
Por um escritor misterioso
Last updated 19 dezembro 2024

Endpoint Detection and Response, Free - What is EDR Security?
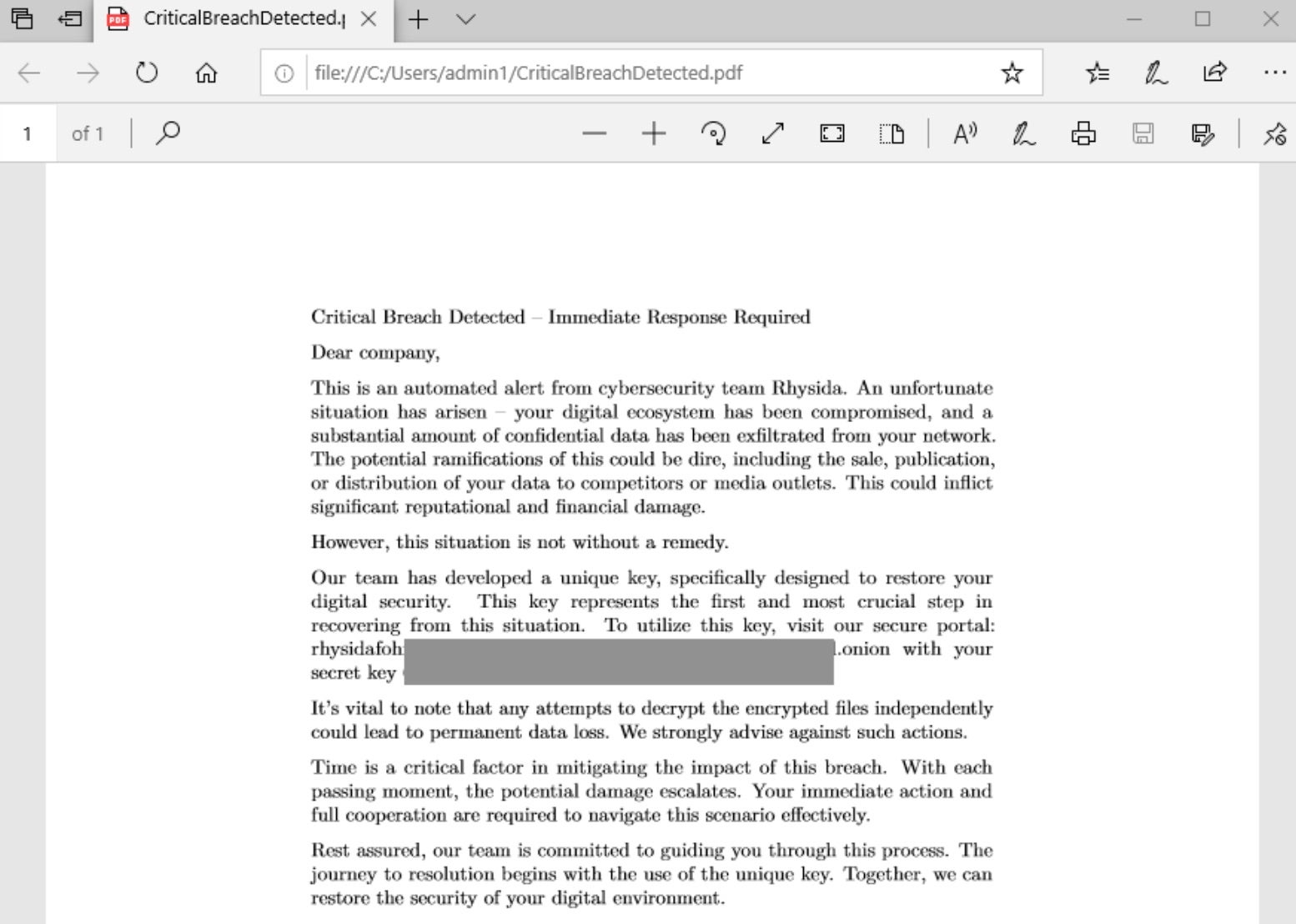
Rhysida - SentinelOne

Security Orchestration Use Case: Automating Malware Analysis

What to Include in a Malware Analysis Report

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug
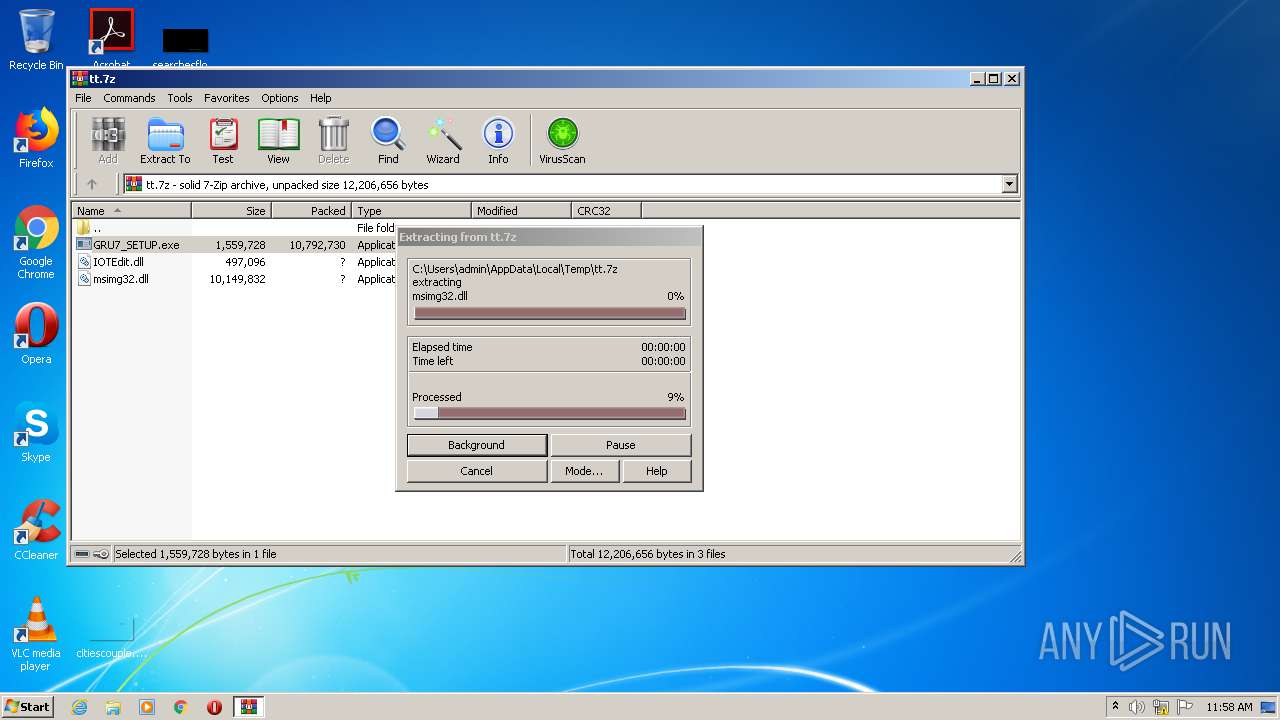
Malware analysis tt.7z Malicious activity
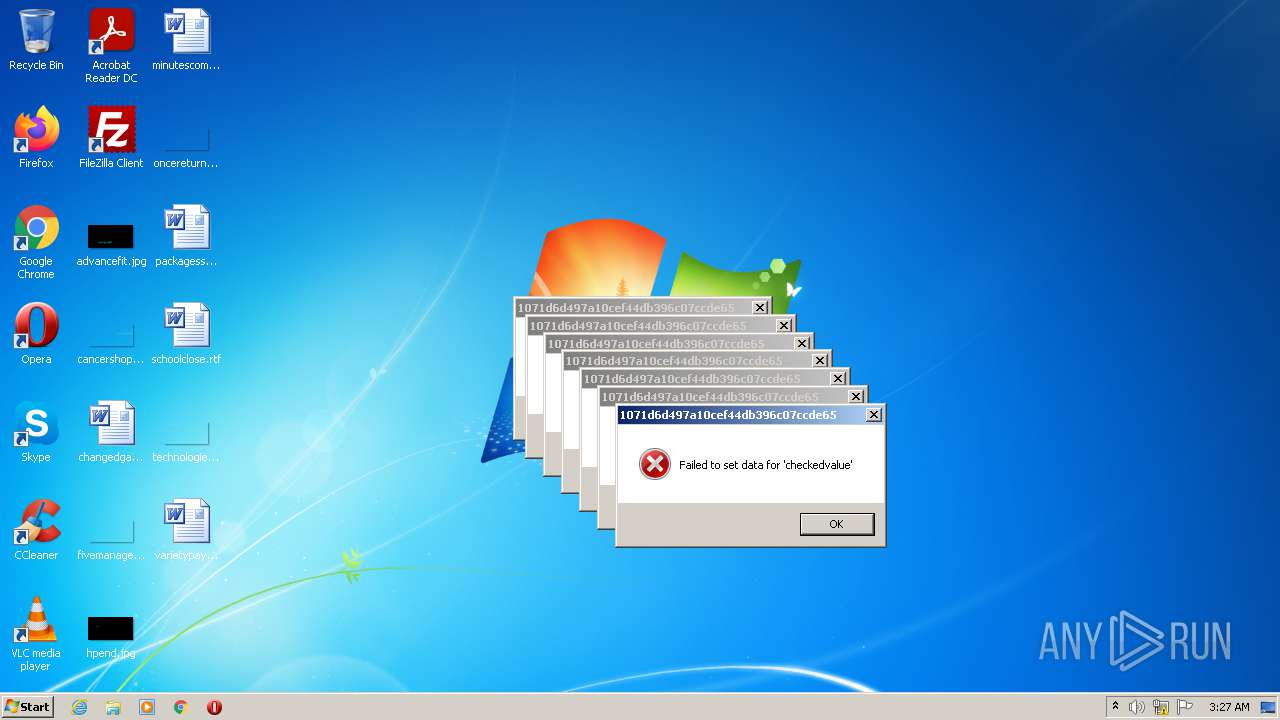
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious

Brute Force Attacks: Password Protection

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Mastering Malware Analysis
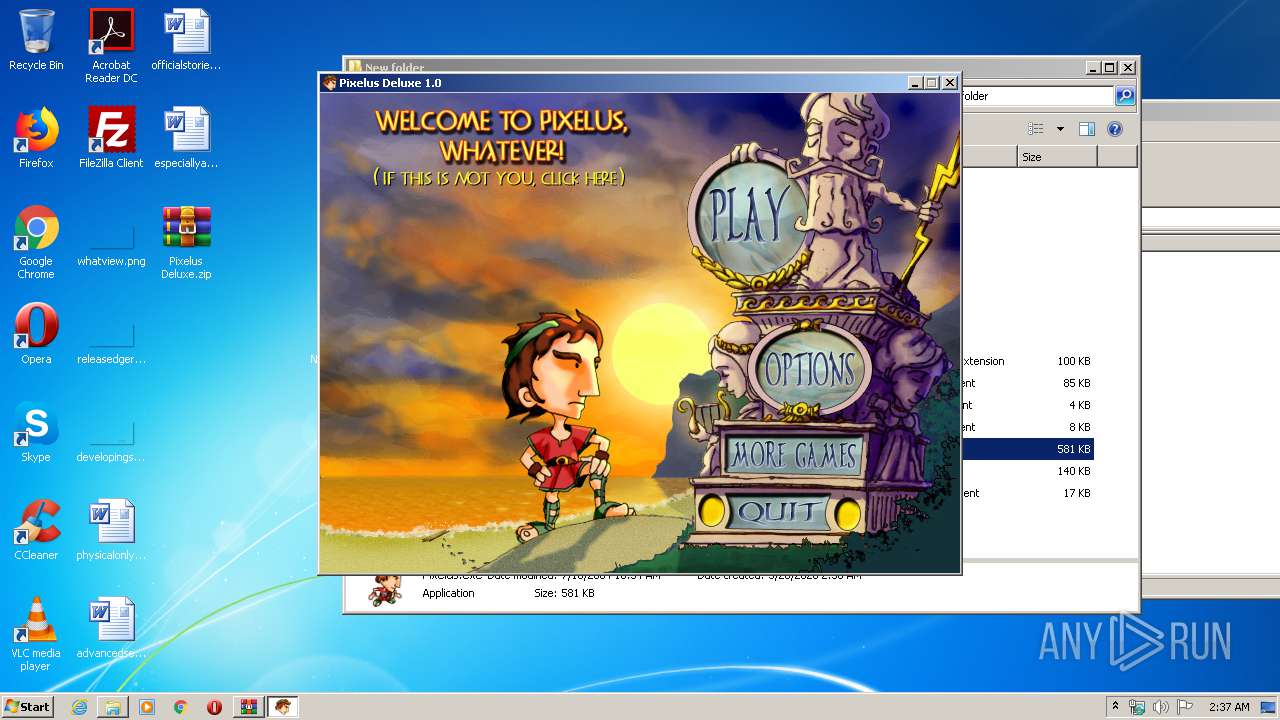
Malware analysis Pixelus Deluxe.zip Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
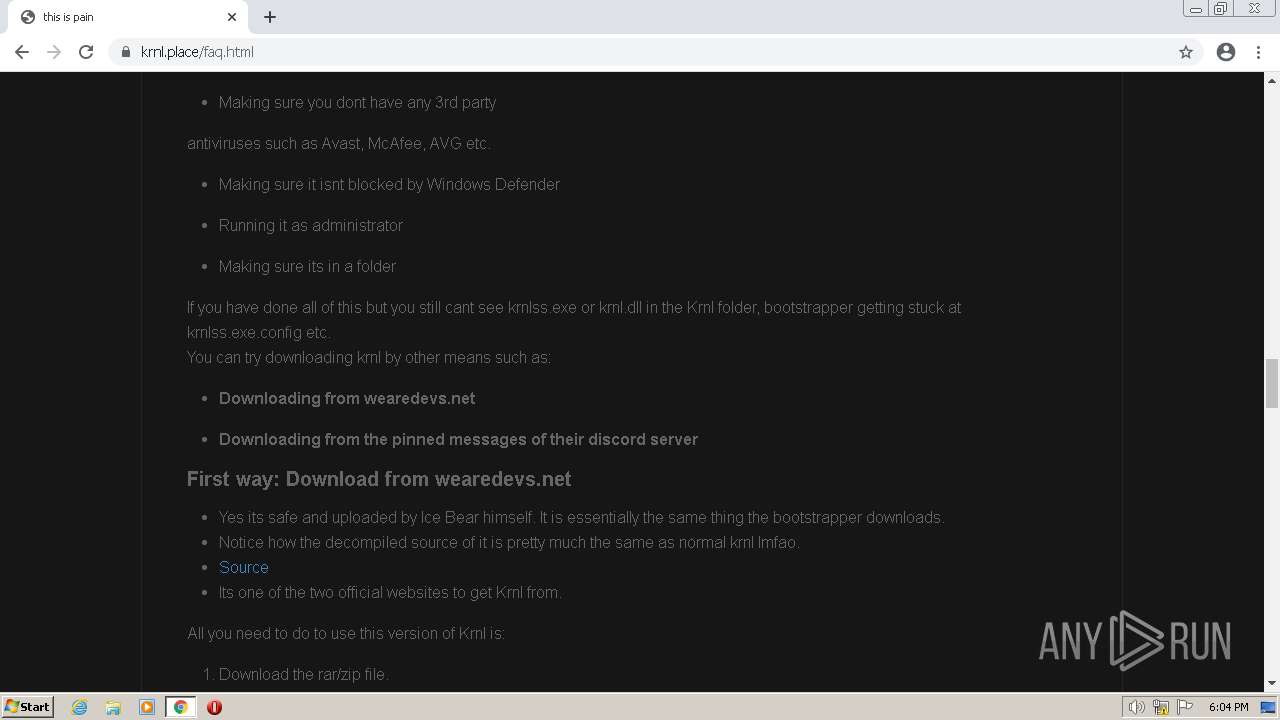
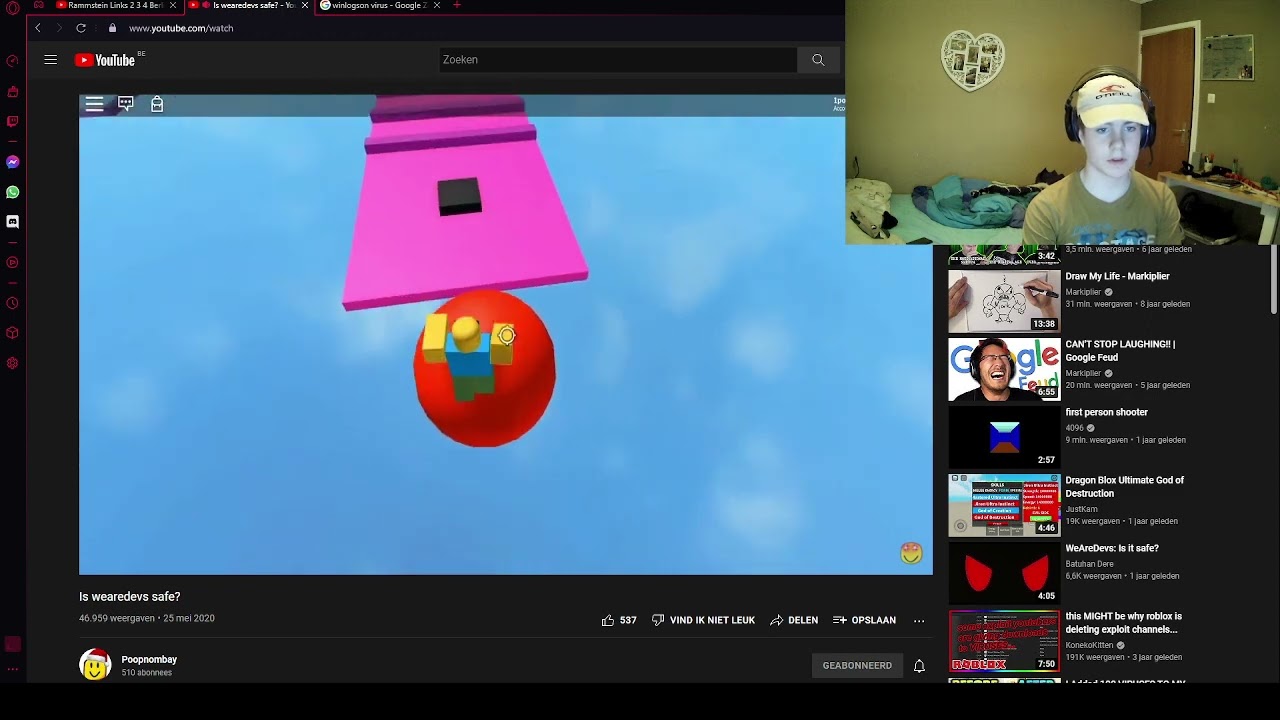 wearedevs is not safe19 dezembro 2024
wearedevs is not safe19 dezembro 2024 -
Racmdx Da Hood Script Download19 dezembro 2024
-
krnl-executor · GitHub Topics · GitHub19 dezembro 2024
-
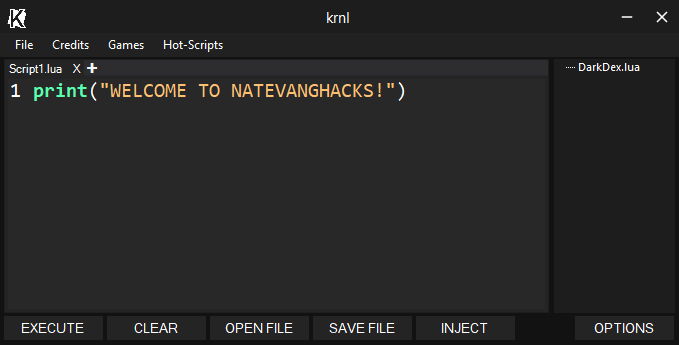 RBXEXploits (@RbxeXploits) / X19 dezembro 2024
RBXEXploits (@RbxeXploits) / X19 dezembro 2024 -
wearedevs19 dezembro 2024
-
 How to download KRNL from WeAreDevs19 dezembro 2024
How to download KRNL from WeAreDevs19 dezembro 2024 -
 Krnl – Download Krnl Free19 dezembro 2024
Krnl – Download Krnl Free19 dezembro 2024 -
krnl.place Reviews Read Customer Service Reviews of krnl.place19 dezembro 2024
-
 Game Jolt - Share your creations19 dezembro 2024
Game Jolt - Share your creations19 dezembro 2024 -
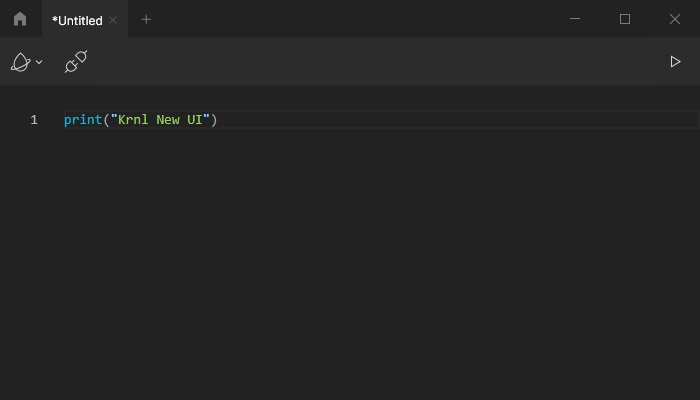 Krnl Free Download For Windows PC - Softlay19 dezembro 2024
Krnl Free Download For Windows PC - Softlay19 dezembro 2024
você pode gostar
-
 85% OFF → Eloboost24.Eu Promo Code, Coupon Code19 dezembro 2024
85% OFF → Eloboost24.Eu Promo Code, Coupon Code19 dezembro 2024 -
 Liberação dos jogos da PS Plus Extra e Deluxe de Fevereiro 2023!!! É hoje! Horizon Forbidden West!19 dezembro 2024
Liberação dos jogos da PS Plus Extra e Deluxe de Fevereiro 2023!!! É hoje! Horizon Forbidden West!19 dezembro 2024 -
 Aldnoah.Zero - Anime Spoilers & Speculation - Page 138 - AnimeSuki19 dezembro 2024
Aldnoah.Zero - Anime Spoilers & Speculation - Page 138 - AnimeSuki19 dezembro 2024 -
 Placa decorativa infantil desenho cacto verde - Wallkids - Placa19 dezembro 2024
Placa decorativa infantil desenho cacto verde - Wallkids - Placa19 dezembro 2024 -
 Calaméo - Y8 Games19 dezembro 2024
Calaméo - Y8 Games19 dezembro 2024 -
Happy Blue Eyes Girl Face 3D (Default Head) - Roblox19 dezembro 2024
-
 Roblox Adds Ambitious Voice Chat System That Aims To Replicate Real Life And Go Beyond It - GameSpot19 dezembro 2024
Roblox Adds Ambitious Voice Chat System That Aims To Replicate Real Life And Go Beyond It - GameSpot19 dezembro 2024 -
 Gamepasses, Anime Fighters Wiki19 dezembro 2024
Gamepasses, Anime Fighters Wiki19 dezembro 2024 -
 Slime Rancher (Multi) será adaptado para um filme pelo estúdio do criador de John Wick - GameBlast19 dezembro 2024
Slime Rancher (Multi) será adaptado para um filme pelo estúdio do criador de John Wick - GameBlast19 dezembro 2024 -
 Gatos pretos: rejeitados e perseguidos19 dezembro 2024
Gatos pretos: rejeitados e perseguidos19 dezembro 2024

