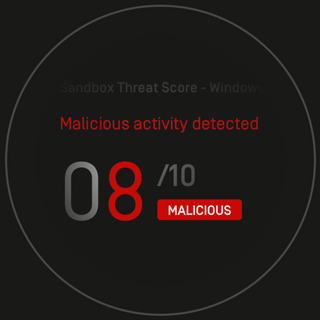
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 fevereiro 2025

Malware Analysis: Steps & Examples - CrowdStrike
MetaDefender Cloud Advanced threat prevention and detection

How to Do Malware Analysis?

Robust Malware Detection Models: Learning From Adversarial Attacks

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging

Malware Analysis Benefits Incident Response
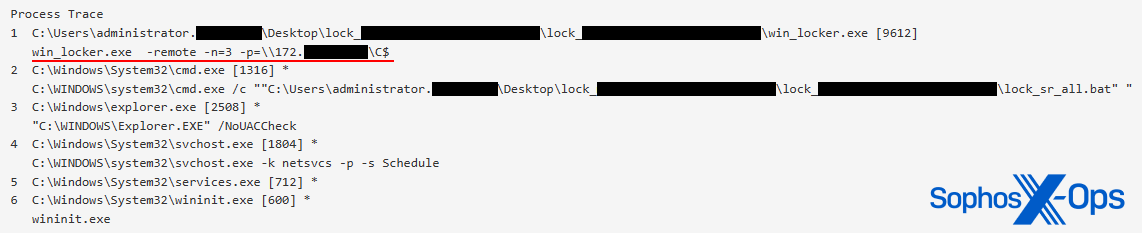
CryptoGuard: An asymmetric approach to the ransomware battle

Cybersecurity Search Engine

Malware analysis Program_Install_and_Uninstall Malicious activity
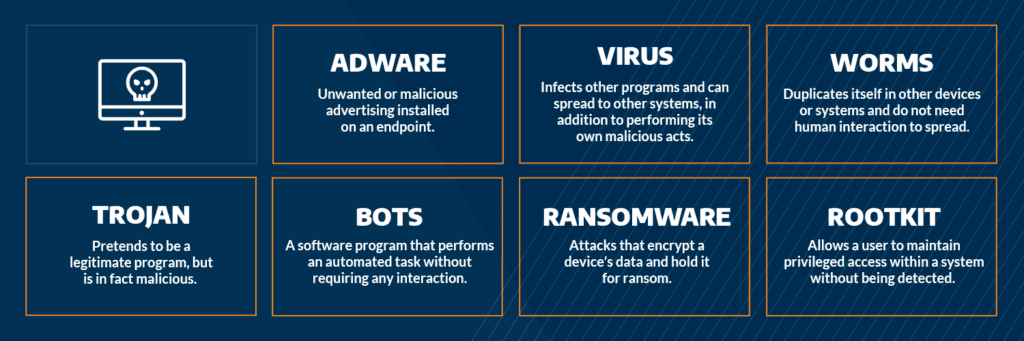
Most Common Malware Attacks

Malware Analysis: Steps & Examples - CrowdStrike
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

A detailed analysis of the Menorah malware used by APT34
Recomendado para você
-
 MSN Games - Jewel Shuffle22 fevereiro 2025
MSN Games - Jewel Shuffle22 fevereiro 2025 -
 MSN Games - Free Online Games22 fevereiro 2025
MSN Games - Free Online Games22 fevereiro 2025 -
 msn-games-640 - SiliconANGLE22 fevereiro 2025
msn-games-640 - SiliconANGLE22 fevereiro 2025 -
 MSN Games - PC Downloads22 fevereiro 2025
MSN Games - PC Downloads22 fevereiro 2025 -
 MSN Games - Mythical Jewels22 fevereiro 2025
MSN Games - Mythical Jewels22 fevereiro 2025 -
 Microsoft Solitaire Collection - MSN Games - Free Online Games22 fevereiro 2025
Microsoft Solitaire Collection - MSN Games - Free Online Games22 fevereiro 2025 -
 MYTHICAL JEWELS online game22 fevereiro 2025
MYTHICAL JEWELS online game22 fevereiro 2025 -
 Microsoft Spades Game Free - Colaboratory22 fevereiro 2025
Microsoft Spades Game Free - Colaboratory22 fevereiro 2025 -
 MSN Games - Free Online Games22 fevereiro 2025
MSN Games - Free Online Games22 fevereiro 2025 -
 Looking Back to 2001 with Bejeweled - In the Middle of a Chain Reaction22 fevereiro 2025
Looking Back to 2001 with Bejeweled - In the Middle of a Chain Reaction22 fevereiro 2025
você pode gostar
-
 ▷ Os 25 melhores jogos de futebol para Android 【Classificação 2023】22 fevereiro 2025
▷ Os 25 melhores jogos de futebol para Android 【Classificação 2023】22 fevereiro 2025 -
 Tejina-senpai – Wikipédia, a enciclopédia livre22 fevereiro 2025
Tejina-senpai – Wikipédia, a enciclopédia livre22 fevereiro 2025 -
 X 上的Power of Anim3:「♡♡#kiss #harutora and #natsume ♡♡ •○○>>Anime:tokyo ravens <<○○• #followme #followback / X22 fevereiro 2025
X 上的Power of Anim3:「♡♡#kiss #harutora and #natsume ♡♡ •○○>>Anime:tokyo ravens <<○○• #followme #followback / X22 fevereiro 2025 -
 Fastupload.io on X: This *FREE* ROBUX Promo Code Gives FREE ROBUX! (Roblox 2019) Link: #2019robloxpromocodes #freerobloxcodes #freerobux #freerobux2019 #freerobuxcodes #freerobuxpromocodes2019 #freerobuxroblox22 fevereiro 2025
Fastupload.io on X: This *FREE* ROBUX Promo Code Gives FREE ROBUX! (Roblox 2019) Link: #2019robloxpromocodes #freerobloxcodes #freerobux #freerobux2019 #freerobuxcodes #freerobuxpromocodes2019 #freerobuxroblox22 fevereiro 2025 -
![HELP] I need some nice fruits🤕 : r/bloxfruits](https://i.redd.it/64chogezmr5b1.gif) HELP] I need some nice fruits🤕 : r/bloxfruits22 fevereiro 2025
HELP] I need some nice fruits🤕 : r/bloxfruits22 fevereiro 2025 -
 Comparação DirectX 11 vs DirectX 12 - Unreal Engine 4 Elemental22 fevereiro 2025
Comparação DirectX 11 vs DirectX 12 - Unreal Engine 4 Elemental22 fevereiro 2025 -
 Triste Emoção Fofa Kawaii Encara ícone Do Vetor Emocional22 fevereiro 2025
Triste Emoção Fofa Kawaii Encara ícone Do Vetor Emocional22 fevereiro 2025 -
Buy Desire Steam Key GLOBAL - Cheap - !22 fevereiro 2025
-
 Download do APK de Colorir e Jogos: Animais para Android22 fevereiro 2025
Download do APK de Colorir e Jogos: Animais para Android22 fevereiro 2025 -
Monem Shariar Chowdhury - General Help - Compass Group Chartwells22 fevereiro 2025

