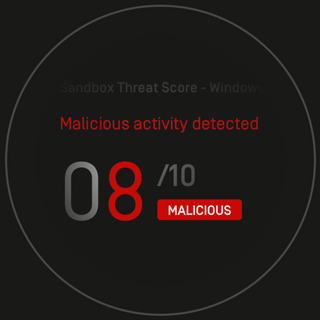
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 fevereiro 2025

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights
Krebs on Security – In-depth security news and investigation

Detail procedure of malware analysis

Malware analysis file Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

GitHub - mesquidar/ForensicsTools: A list of free and open forensics analysis tools and other resources
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

How to build a malware analysis sandbox with Elastic Security

Malware Analysis: Steps & Examples - CrowdStrike

Malware analysis index.html Malicious activity

Malware analysis mykey_.rar Malicious activity
MetaDefender Cloud Advanced threat prevention and detection

Dynamic malware analysis [34]
Recomendado para você
-
 RBLXWild (@rblx_wild) / X22 fevereiro 2025
RBLXWild (@rblx_wild) / X22 fevereiro 2025 -
 HOW I MADE 150K ROBUX ON RBLXWILD!22 fevereiro 2025
HOW I MADE 150K ROBUX ON RBLXWILD!22 fevereiro 2025 -
 Bloxflip · Git Hub Topics · Git Hub - # bloxflip Here are 1922 fevereiro 2025
Bloxflip · Git Hub Topics · Git Hub - # bloxflip Here are 1922 fevereiro 2025 -
 How To Redeem Codes On RBLXWILD For *FREE* Robux!22 fevereiro 2025
How To Redeem Codes On RBLXWILD For *FREE* Robux!22 fevereiro 2025 -
 How To Redeem Codes On RBLXWILD And Get *FREE* Robux!22 fevereiro 2025
How To Redeem Codes On RBLXWILD And Get *FREE* Robux!22 fevereiro 2025 -
Sahlad - Twitch Stats, Analytics and Channel Overview22 fevereiro 2025
-
GitHub - Odsku/betterAutoJoiner: Automatically joins RBLXWILD rains22 fevereiro 2025
-
 rblxwild redeem code ewe to get 100 robux for free22 fevereiro 2025
rblxwild redeem code ewe to get 100 robux for free22 fevereiro 2025 -
 BIG WINS ON RBLXWILD (UNSPONSORED)22 fevereiro 2025
BIG WINS ON RBLXWILD (UNSPONSORED)22 fevereiro 2025 -
joiner · GitHub Topics · GitHub22 fevereiro 2025
você pode gostar
-
SeriesFlix (Original Ver Series) MOD APK for Android22 fevereiro 2025
-
 Color Print Anime Song Lilium Elfen Lied Music Box Wooden Black Hand Movement Girls For Girlfriend Wife Friend Christmas Kid Toy - AliExpress22 fevereiro 2025
Color Print Anime Song Lilium Elfen Lied Music Box Wooden Black Hand Movement Girls For Girlfriend Wife Friend Christmas Kid Toy - AliExpress22 fevereiro 2025 -
![Soft Demon :] Club outfits, Club hairstyles, Club design](https://i.pinimg.com/originals/bd/24/8a/bd248aa7901c7f05f9d664d44bdd5463.jpg) Soft Demon :] Club outfits, Club hairstyles, Club design22 fevereiro 2025
Soft Demon :] Club outfits, Club hairstyles, Club design22 fevereiro 2025 -
 Serving All Deez Customers! Papa's Hot Doggeria22 fevereiro 2025
Serving All Deez Customers! Papa's Hot Doggeria22 fevereiro 2025 -
 Tier list but bad quality Roblox Creatures of Sonaria Amino22 fevereiro 2025
Tier list but bad quality Roblox Creatures of Sonaria Amino22 fevereiro 2025 -
 Andrea Bocelli: Crossover Tenor Sensation Leads Pop-Opera22 fevereiro 2025
Andrea Bocelli: Crossover Tenor Sensation Leads Pop-Opera22 fevereiro 2025 -
 Uncharted Movie Poster Concept by Byzial on DeviantArt22 fevereiro 2025
Uncharted Movie Poster Concept by Byzial on DeviantArt22 fevereiro 2025 -
 Scoob Dog, INHUMAS22 fevereiro 2025
Scoob Dog, INHUMAS22 fevereiro 2025 -
 Red Dead Redemption 2 PC Release Date: Is it Coming to PC22 fevereiro 2025
Red Dead Redemption 2 PC Release Date: Is it Coming to PC22 fevereiro 2025 -
 call drifting game|TikTok Search22 fevereiro 2025
call drifting game|TikTok Search22 fevereiro 2025