Malware analysis Malicious activity
Por um escritor misterioso
Last updated 21 fevereiro 2025

Dynamic malware analysis [34]
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Malware analysis file Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Mastering Malware Analysis

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug
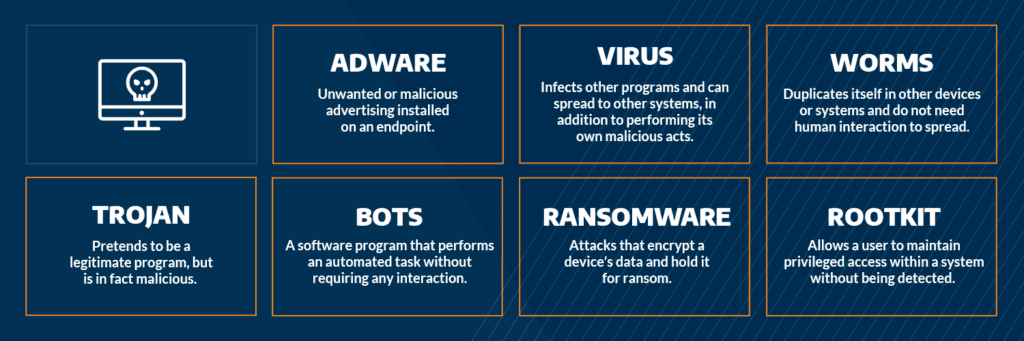
Most Common Malware Attacks

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Malware Analysis: Steps & Examples - CrowdStrike

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
Recomendado para você
-
 File:Google Translate logo.svg - Wikimedia Commons21 fevereiro 2025
File:Google Translate logo.svg - Wikimedia Commons21 fevereiro 2025 -
 Google Tradutor : r/ontheledgeandshit21 fevereiro 2025
Google Tradutor : r/ontheledgeandshit21 fevereiro 2025 -
Reverso Translate and Learn - Apps on Google Play21 fevereiro 2025
-
 tcho, Autor em Lá no Frai é assim!21 fevereiro 2025
tcho, Autor em Lá no Frai é assim!21 fevereiro 2025 -
 Google drive21 fevereiro 2025
Google drive21 fevereiro 2025 -
Sneaky fake Google Translate app installs crypto miner on 112,000 PCs21 fevereiro 2025
-
Discuss Everything About Ultra Custom Night Wiki21 fevereiro 2025
-
![Remove FAKE Google Translate Extension [Virus Removal]](https://malwaretips.com/blogs/wp-content/uploads/2022/08/Fake-Google-Translate-extension.jpg) Remove FAKE Google Translate Extension [Virus Removal]21 fevereiro 2025
Remove FAKE Google Translate Extension [Virus Removal]21 fevereiro 2025 -
 Google Demo Slam: Translate Beat Box21 fevereiro 2025
Google Demo Slam: Translate Beat Box21 fevereiro 2025 -
Você já conhece a ferramenta de inspeção de anúncios gratuita do PubGuru? Esse é um trechinho do nosso último webinar onde falamos mais sobre o PubGuru, By PubGuru Br21 fevereiro 2025
você pode gostar
-
 Baobá - Fundo para Equidade Racial, Autor em Baobá - Página 4 de 2321 fevereiro 2025
Baobá - Fundo para Equidade Racial, Autor em Baobá - Página 4 de 2321 fevereiro 2025 -
 Banana Prata Org Solo Vivo 800g - Supermercado Savegnago21 fevereiro 2025
Banana Prata Org Solo Vivo 800g - Supermercado Savegnago21 fevereiro 2025 -
 Demon Slayer: Swordsmith Village: How Many Episodes & When Does It End?21 fevereiro 2025
Demon Slayer: Swordsmith Village: How Many Episodes & When Does It End?21 fevereiro 2025 -
 Description Meet our new Modern MiniBox! Check out our New Lily White Table Top! Ships between 2-10 busin…21 fevereiro 2025
Description Meet our new Modern MiniBox! Check out our New Lily White Table Top! Ships between 2-10 busin…21 fevereiro 2025 -
 Para Julia Minegirl - Desenho de sofia2021 - Gartic21 fevereiro 2025
Para Julia Minegirl - Desenho de sofia2021 - Gartic21 fevereiro 2025 -
![Zelda no Densetsu: Toki no Ocarina 3D [Decrypted] 3DS (JPN) ROM](https://www.ziperto.com/wp-content/uploads/2020/01/Zelda-no-Densetsu-TNO-shot1.jpg) Zelda no Densetsu: Toki no Ocarina 3D [Decrypted] 3DS (JPN) ROM21 fevereiro 2025
Zelda no Densetsu: Toki no Ocarina 3D [Decrypted] 3DS (JPN) ROM21 fevereiro 2025 -
 Toca Discos Portátil com Alto Falantes Estéreo, AUX e 3 Velocidades, HelloGoody, Verde - Dular21 fevereiro 2025
Toca Discos Portátil com Alto Falantes Estéreo, AUX e 3 Velocidades, HelloGoody, Verde - Dular21 fevereiro 2025 -
 Quiz Ace of Diamond - Characters - Cine and TV Shows21 fevereiro 2025
Quiz Ace of Diamond - Characters - Cine and TV Shows21 fevereiro 2025 -
 🔴 Pegando KYOGRE SHINY LENDARIO Pokemon Go! Passe GRATIS AGORA21 fevereiro 2025
🔴 Pegando KYOGRE SHINY LENDARIO Pokemon Go! Passe GRATIS AGORA21 fevereiro 2025 -
 Shogi Japanese Chess Game Set with Wooden Board and Koma Pieces21 fevereiro 2025
Shogi Japanese Chess Game Set with Wooden Board and Koma Pieces21 fevereiro 2025