Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 15 janeiro 2025
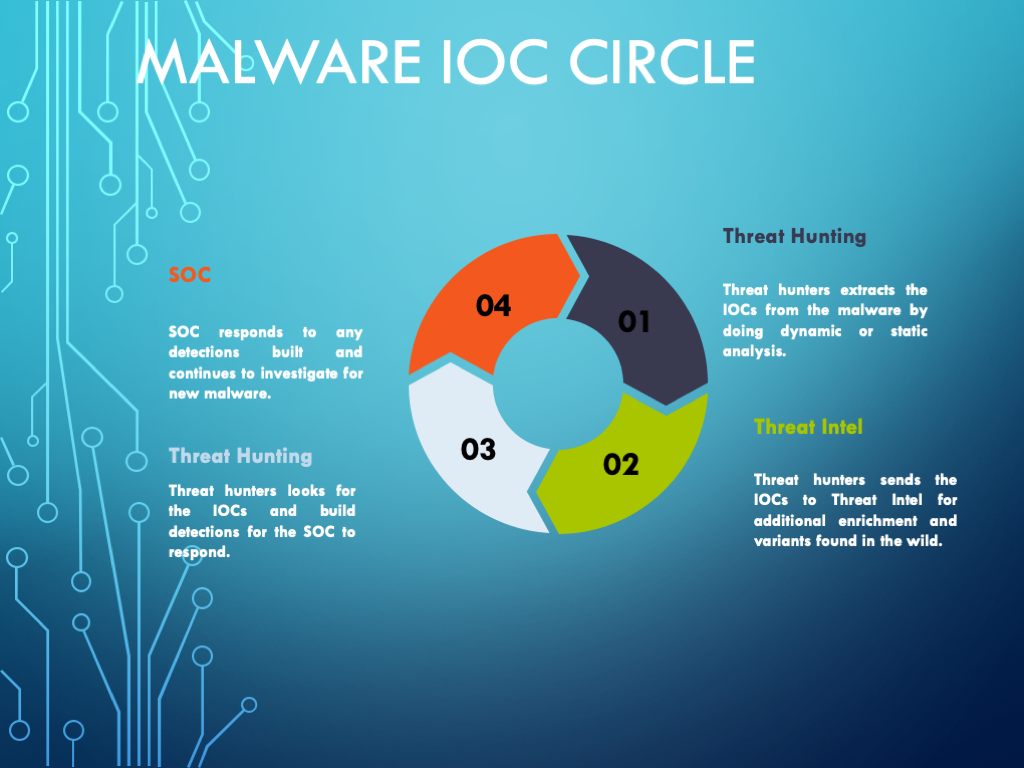
Malware Analysis Framework v1.0
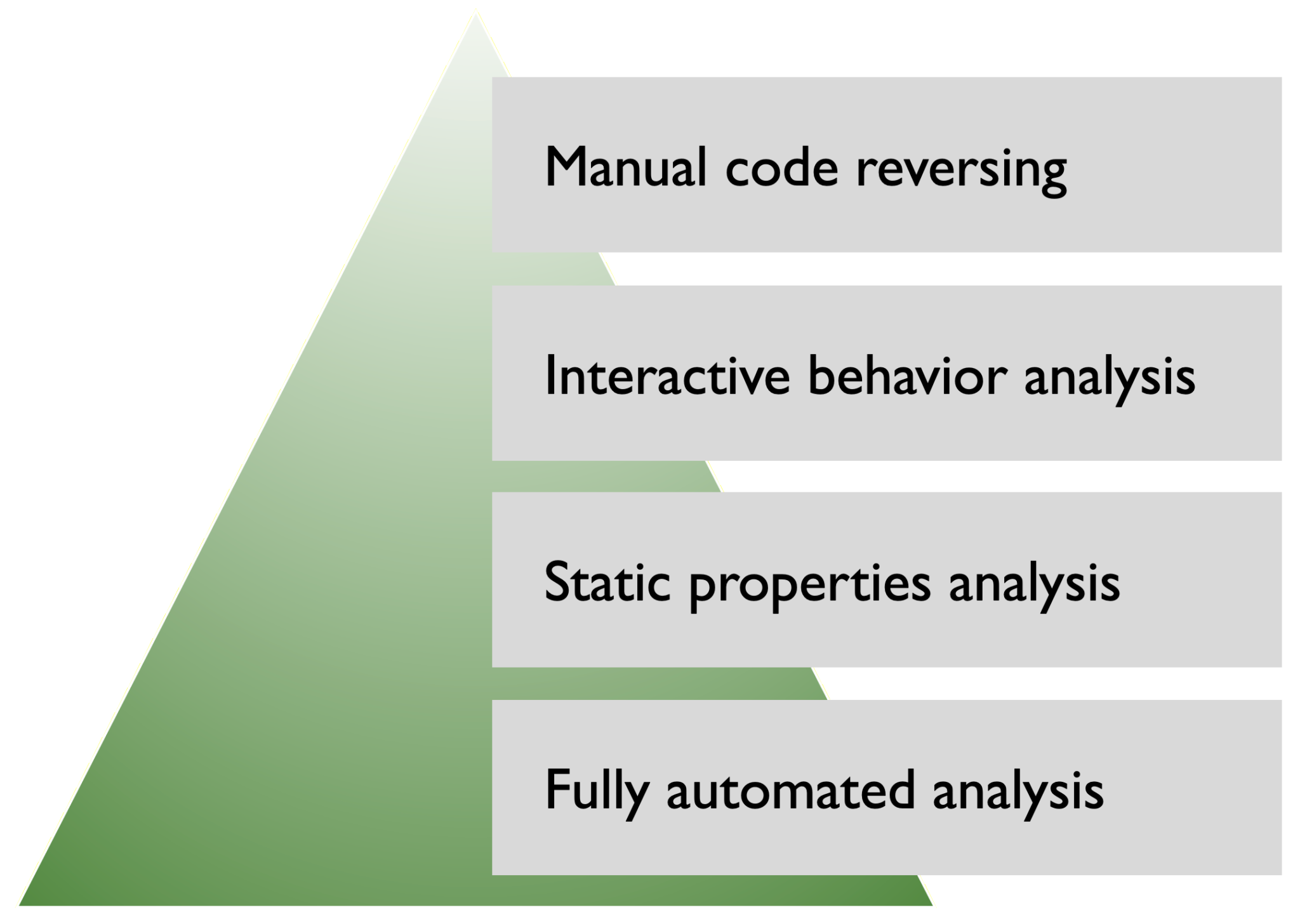
How You Can Start Learning Malware Analysis

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Malware Analysis: Steps & Examples - CrowdStrike
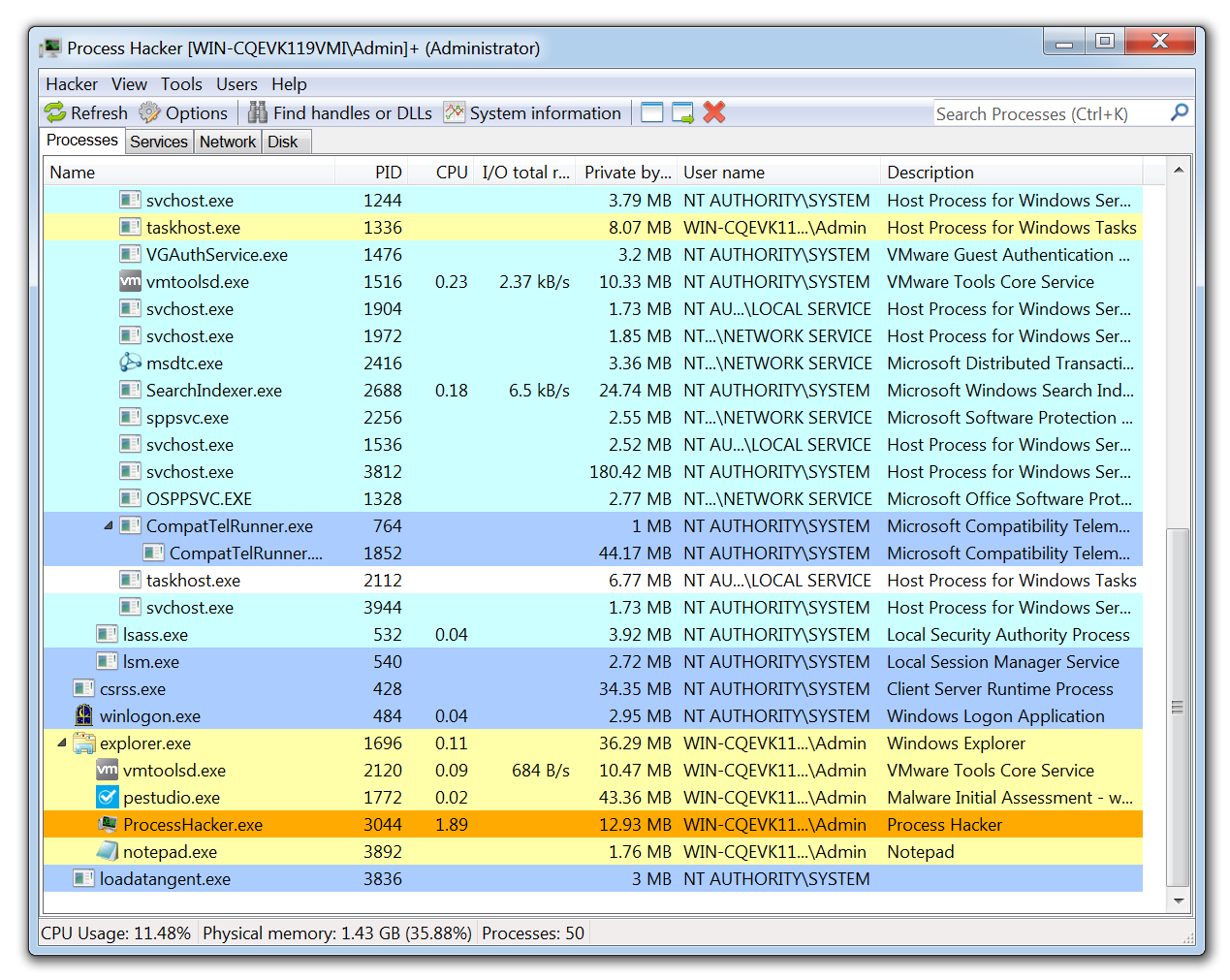
11 Best Malware Analysis Tools and Their Features

What Is Malware Analysis? Definition, Types, Stages, and Best

Tools and Techniques for Collection and Analysis of Internet-of
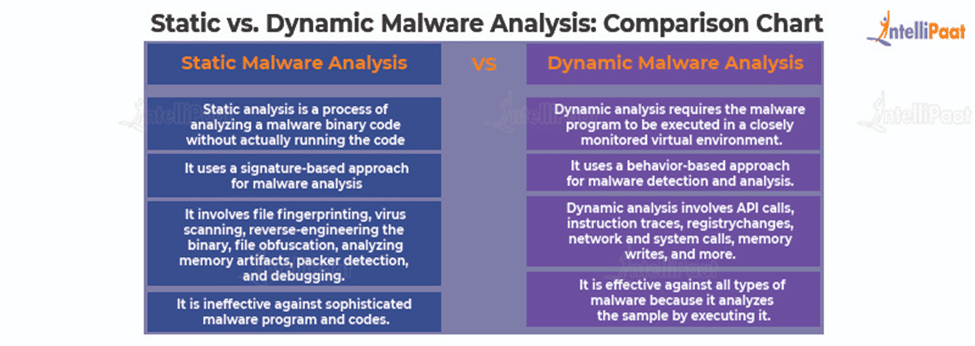
Malware Analysis - What is, Benefits & Types (Easily Explained)
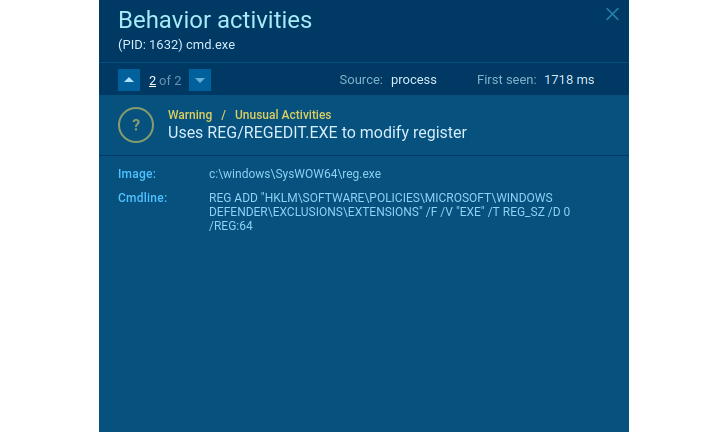
How to Detect New Threats via Suspicious Activities

How to Analyze Malware Infections?
Recomendado para você
-
 Roblox::Appstore for Android15 janeiro 2025
Roblox::Appstore for Android15 janeiro 2025 -
XMAS☃️] Hack Simulator - Roblox15 janeiro 2025
-
 Technical Gamer's Stats and Insights - vidIQ Stats15 janeiro 2025
Technical Gamer's Stats and Insights - vidIQ Stats15 janeiro 2025 -
 Randomizer Roblox Hack – Esp, Aimbot, WalkSPeed – Financial Derivatives Company, Limited15 janeiro 2025
Randomizer Roblox Hack – Esp, Aimbot, WalkSPeed – Financial Derivatives Company, Limited15 janeiro 2025 -
 Anyone remember this page : r/roblox15 janeiro 2025
Anyone remember this page : r/roblox15 janeiro 2025 -
 how to download hacks roblox black fruit|TikTok Search15 janeiro 2025
how to download hacks roblox black fruit|TikTok Search15 janeiro 2025 -
 robux: Roblox 2023 guide: How to get free Robux? Here's what you15 janeiro 2025
robux: Roblox 2023 guide: How to get free Robux? Here's what you15 janeiro 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/6/M/OEKlWPR02pC0tXSsi7Rg/personagem.jpg) Roblox permite hacks? Veja práticas proibidas na plataformas de games15 janeiro 2025
Roblox permite hacks? Veja práticas proibidas na plataformas de games15 janeiro 2025 -
 Electron x FREE Executor 2023, Roblox x Electron Script Menu15 janeiro 2025
Electron x FREE Executor 2023, Roblox x Electron Script Menu15 janeiro 2025 -
 Roblox: The Movie (2014) - IMDb15 janeiro 2025
Roblox: The Movie (2014) - IMDb15 janeiro 2025
você pode gostar
-
Academia de Ajedrez Check - Clases de Ajedrez Online dirigido a niños y adolescentes. Requisitos? Simplemente hambre de gloria y ganas de aprender. Te invitamos a ser parte de nuestro equipo! . . . . . . . . . #15 janeiro 2025
-
Camila Roldon (@caaax3) / X15 janeiro 2025
-
 peão - Wikcionário15 janeiro 2025
peão - Wikcionário15 janeiro 2025 -
 Grounds Crew T Pose GIF by Kane County Cougars - Find & Share on GIPHY15 janeiro 2025
Grounds Crew T Pose GIF by Kane County Cougars - Find & Share on GIPHY15 janeiro 2025 -
 id de perna no berry avenue15 janeiro 2025
id de perna no berry avenue15 janeiro 2025 -
 Tensai Ouji no Akaji Kokka Saisei Jutsu: Short Drama Specials - MyAnimeList .net15 janeiro 2025
Tensai Ouji no Akaji Kokka Saisei Jutsu: Short Drama Specials - MyAnimeList .net15 janeiro 2025 -
Shinsuke Nakamura - Wikipedia15 janeiro 2025
-
 Quando os trabalhadores realizaram suas próprias Olimpíadas15 janeiro 2025
Quando os trabalhadores realizaram suas próprias Olimpíadas15 janeiro 2025 -
 Arquivos resolve fácil - Agência Itapevi de Notícias15 janeiro 2025
Arquivos resolve fácil - Agência Itapevi de Notícias15 janeiro 2025 -
 Rio 2016, Olympics (Portuguese: Jogos Olímpicos de Verão de…15 janeiro 2025
Rio 2016, Olympics (Portuguese: Jogos Olímpicos de Verão de…15 janeiro 2025
![XMAS☃️] Hack Simulator - Roblox](https://tr.rbxcdn.com/574c098d195a021a5faf1b1ece1d5b74/150/150/Image/Png)

