Preventing threat actors from taking advantage of Bloodhound 3.0, by Biju Varghese, AttivoTechBlogs
Por um escritor misterioso
Last updated 17 janeiro 2025

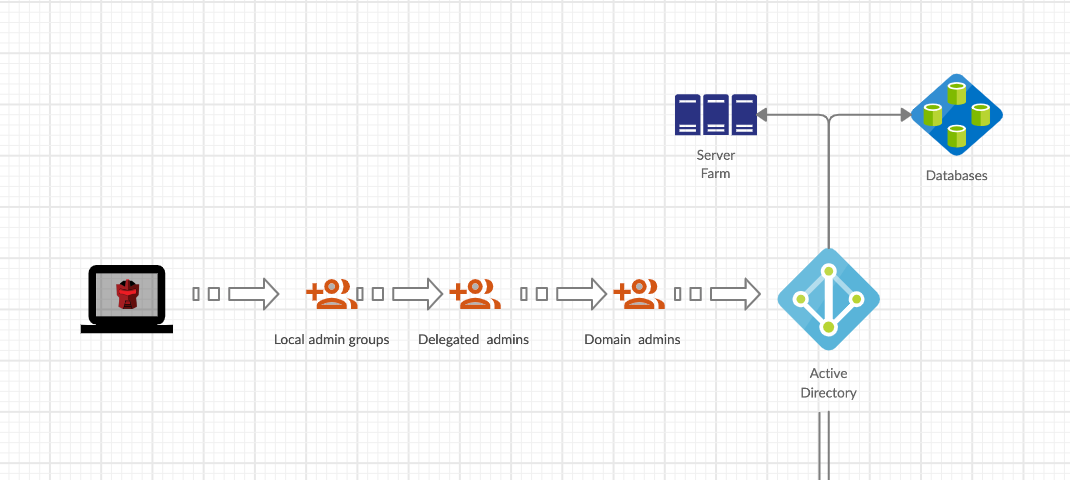
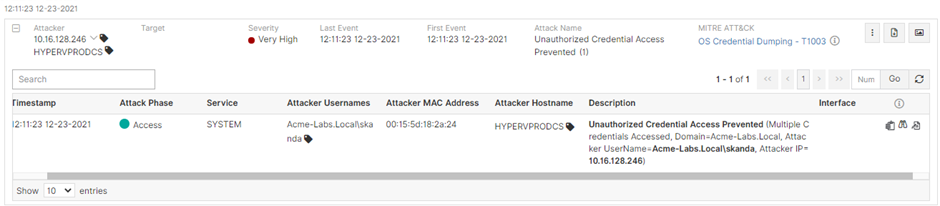
Bloodhound 3.0 with three new attack methods — GMSA Control, OU Control & SID History. This article discusses how one can protect one’s Active Directory

Latest stories published on AttivoTechBlogs – Medium
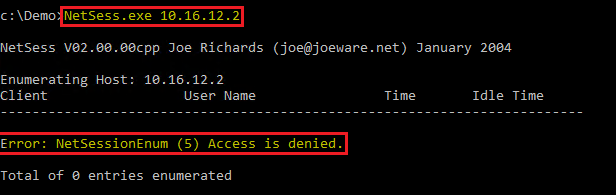
Lateral Movement Using SMB Session Enumeration
Top stories published by AttivoTechBlogs in 2020 – Medium
Preventing samaccountname spoofing and kdc bamboozing

Preventing threat actors from taking advantage of Bloodhound 3.0

Preventing threat actors from taking advantage of Bloodhound 3.0
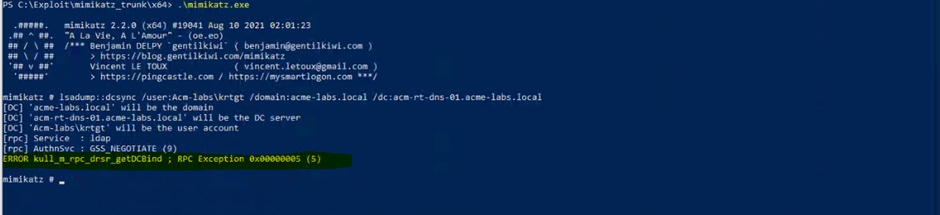
Preventing samaccountname spoofing and kdc bamboozing

Latest stories published on AttivoTechBlogs – Medium

AttivoTechBlogs – Medium
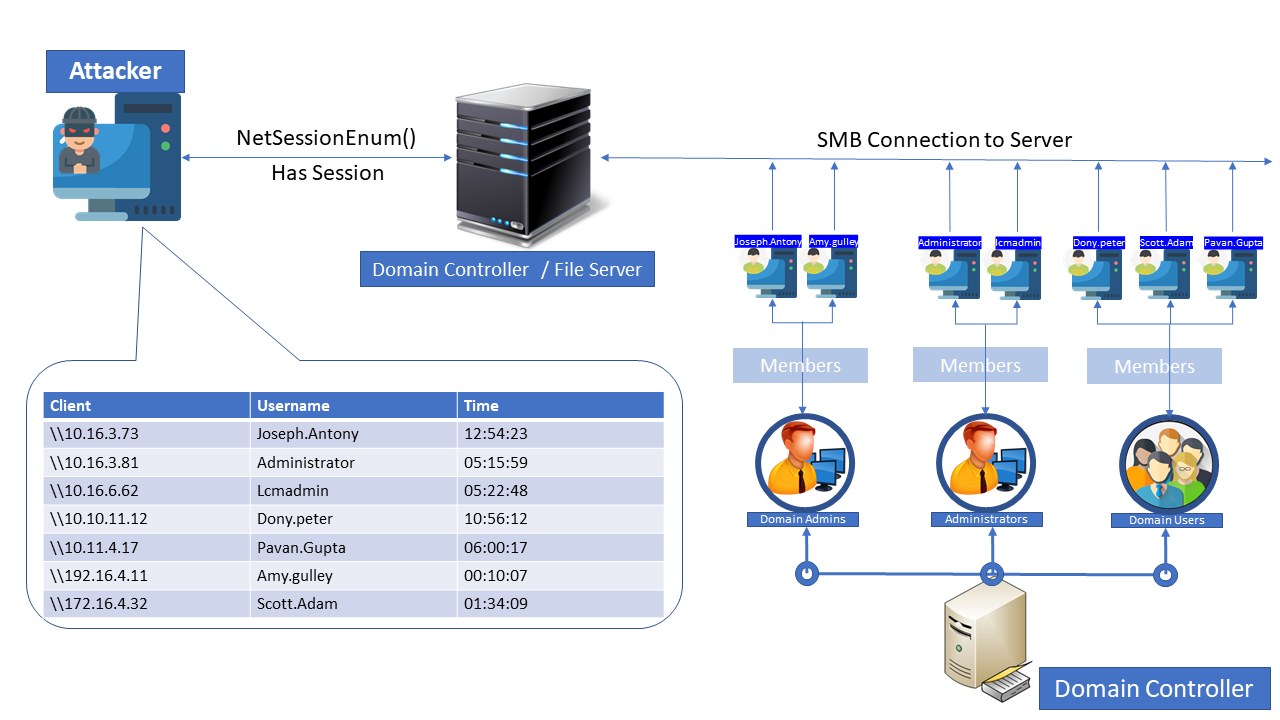
Lateral Movement Using SMB Session Enumeration
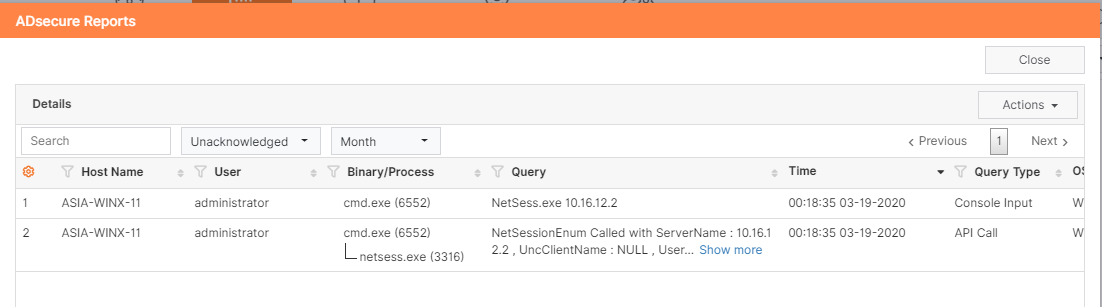
Lateral Movement Using SMB Session Enumeration

Latest stories published on AttivoTechBlogs – Medium
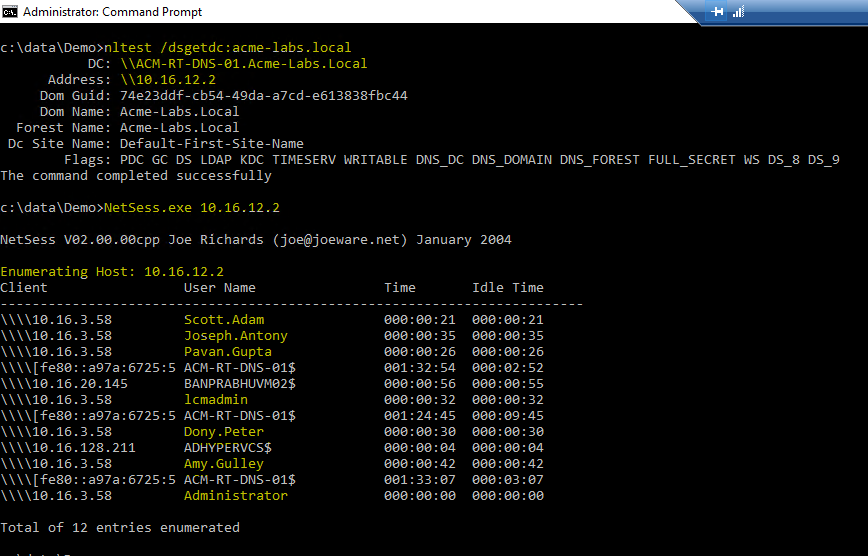
Lateral Movement Using SMB Session Enumeration
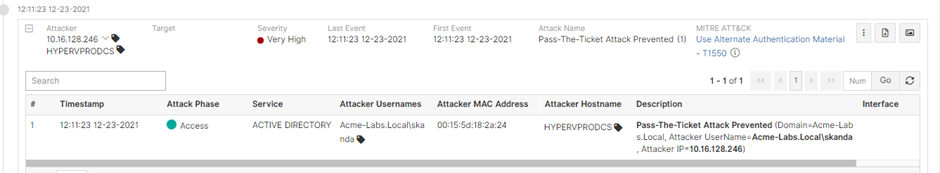
Preventing samaccountname spoofing and kdc bamboozing
Recomendado para você
-
 Grand Theft Auto IV – Wikipédia, a enciclopédia livre17 janeiro 2025
Grand Theft Auto IV – Wikipédia, a enciclopédia livre17 janeiro 2025 -
 Códigos e cheats de GTA 5 para Xbox, PlayStation e PC - Olhar Digital17 janeiro 2025
Códigos e cheats de GTA 5 para Xbox, PlayStation e PC - Olhar Digital17 janeiro 2025 -
 GTA Online: San Andreas Mercenaries já disponível - Rockstar Games17 janeiro 2025
GTA Online: San Andreas Mercenaries já disponível - Rockstar Games17 janeiro 2025 -
 GTA 5: veja os melhores locais para encontrar helicópteros e aviões17 janeiro 2025
GTA 5: veja os melhores locais para encontrar helicópteros e aviões17 janeiro 2025 -
 Informação sobre beneficiário no pagamento de boletos - Conta do Nubank - NuCommunity17 janeiro 2025
Informação sobre beneficiário no pagamento de boletos - Conta do Nubank - NuCommunity17 janeiro 2025 -
Cartão SD Sat Nav para Renault Carminat, R-Link 11.05 Europa Cacém E São Marcos • OLX Portugal17 janeiro 2025
-
 Annihilator, Grand Theft Auto Wiki17 janeiro 2025
Annihilator, Grand Theft Auto Wiki17 janeiro 2025 -
 News Chopper, Grand Theft Auto Wiki17 janeiro 2025
News Chopper, Grand Theft Auto Wiki17 janeiro 2025 -
 Passagens de Nível Infraestruturas de Portugal17 janeiro 2025
Passagens de Nível Infraestruturas de Portugal17 janeiro 2025 -
 Códigos de GTA 5 Cheats e macetes para PS4, PS5, Xbox e PC – Tecnoblog17 janeiro 2025
Códigos de GTA 5 Cheats e macetes para PS4, PS5, Xbox e PC – Tecnoblog17 janeiro 2025
você pode gostar
-
 Desenhos de Son Goku e Vegeta para Colorir e Imprimir17 janeiro 2025
Desenhos de Son Goku e Vegeta para Colorir e Imprimir17 janeiro 2025 -
 Phil's Infinity Gauntlet and our Dream Xbox Crossovers - Git Gud17 janeiro 2025
Phil's Infinity Gauntlet and our Dream Xbox Crossovers - Git Gud17 janeiro 2025 -
 Cut the Rope 3 All Levels Three Star Walkthrough Gameplay : r/AppleArcade17 janeiro 2025
Cut the Rope 3 All Levels Three Star Walkthrough Gameplay : r/AppleArcade17 janeiro 2025 -
Meninas desenho tumblr - e tipo bff17 janeiro 2025
-
 The Man from the window call 1 APKs - com.HorrorMan17 janeiro 2025
The Man from the window call 1 APKs - com.HorrorMan17 janeiro 2025 -
 Gacha Life 2 APK MOD 0.93 Download free for Android 202317 janeiro 2025
Gacha Life 2 APK MOD 0.93 Download free for Android 202317 janeiro 2025 -
 Dre_Drews_ on X: Finalizado Ellie The Last of us II Realismo - - - - - - - #art #arts #draw #drawing #drawings #arte #artes #desenho #desenhos #games # jogos #jogo #jogoamericano #gamer #17 janeiro 2025
Dre_Drews_ on X: Finalizado Ellie The Last of us II Realismo - - - - - - - #art #arts #draw #drawing #drawings #arte #artes #desenho #desenhos #games # jogos #jogo #jogoamericano #gamer #17 janeiro 2025 -
 Baraka (MKA), Mortal Kombat17 janeiro 2025
Baraka (MKA), Mortal Kombat17 janeiro 2025 -
 Shine On! Bakumatsu Bad Boys! - Série TV 2022 - Manga news17 janeiro 2025
Shine On! Bakumatsu Bad Boys! - Série TV 2022 - Manga news17 janeiro 2025 -
 Pokémon Go shiny Mewtwo ~PSY STRIKE~ WEATHER BOOSTED~ reliable17 janeiro 2025
Pokémon Go shiny Mewtwo ~PSY STRIKE~ WEATHER BOOSTED~ reliable17 janeiro 2025
