Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Por um escritor misterioso
Last updated 21 fevereiro 2025

A full reverse engineering analysis of the emotet trojan : r/netsec

Emotet trojan is back with a vengeance
Emotet vs Trump – Deep Dive Analysis of a Killer Info-Stealer - Cynet
Emotet vs Trump – Deep Dive Analysis of a Killer Info-Stealer - Cynet

What is Emotet Malware and How Do You Defend Against it?

The Reemergence of the Emotet Trojan
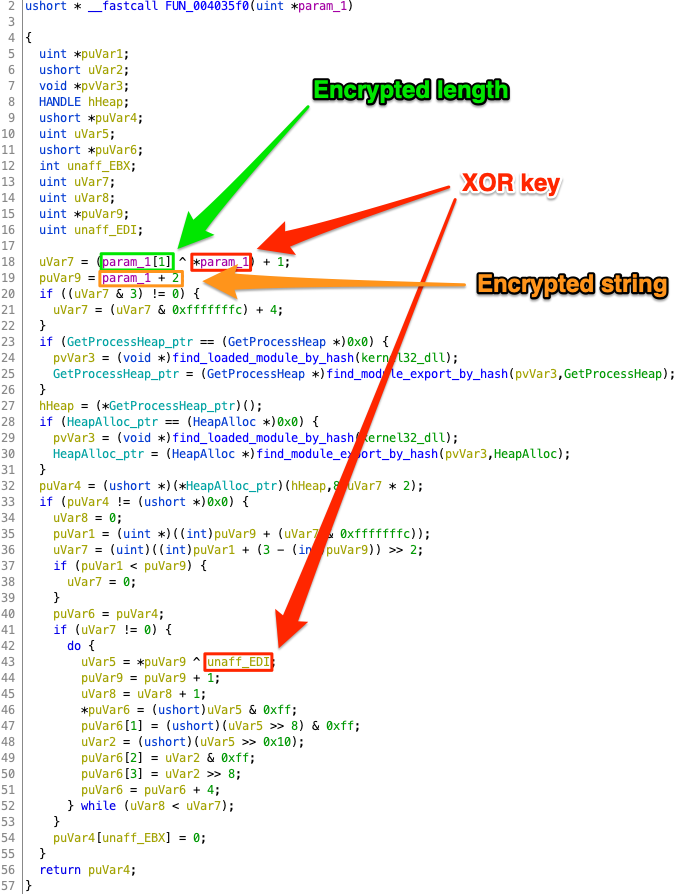
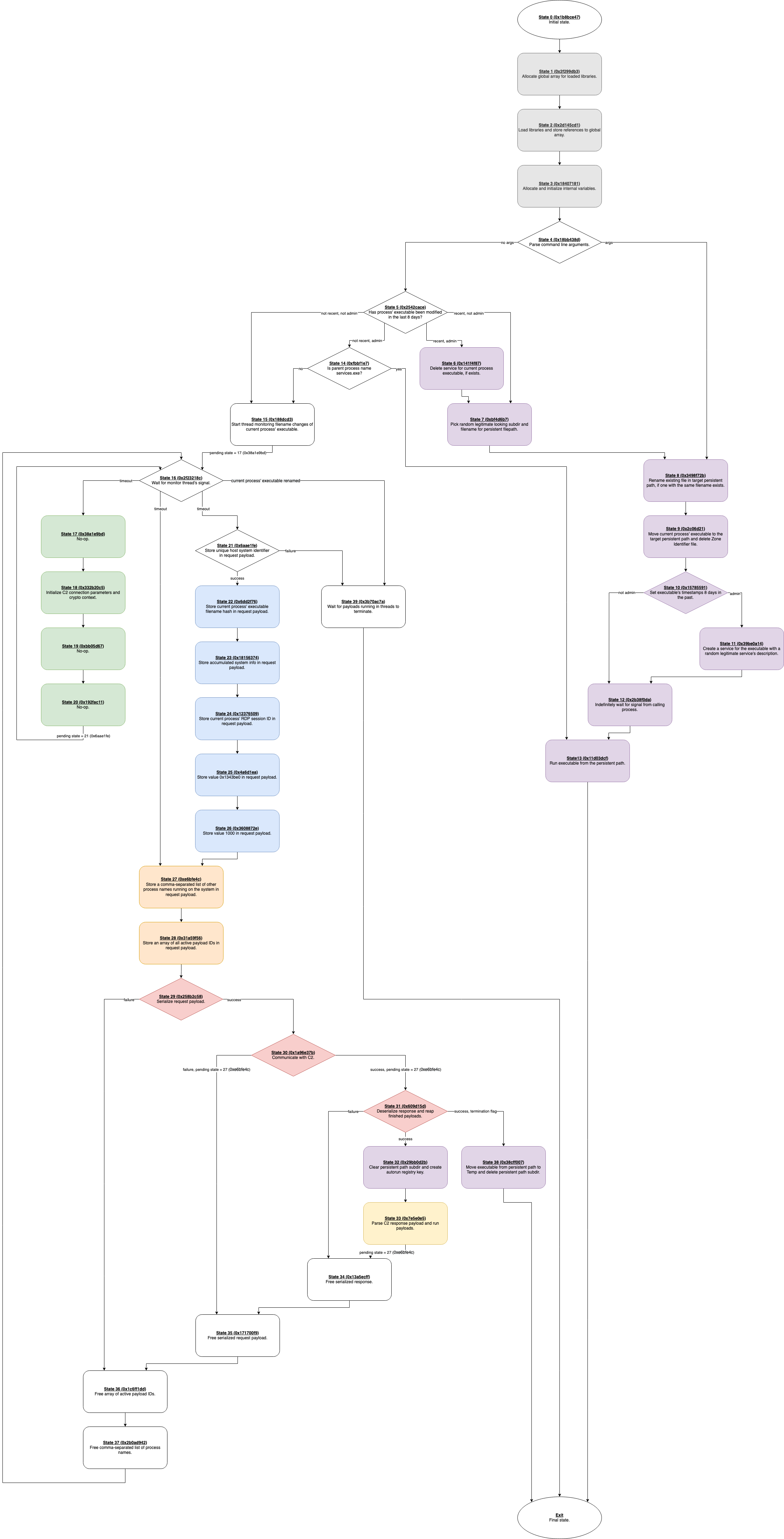
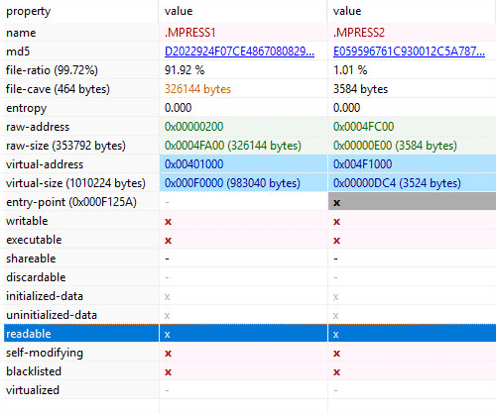
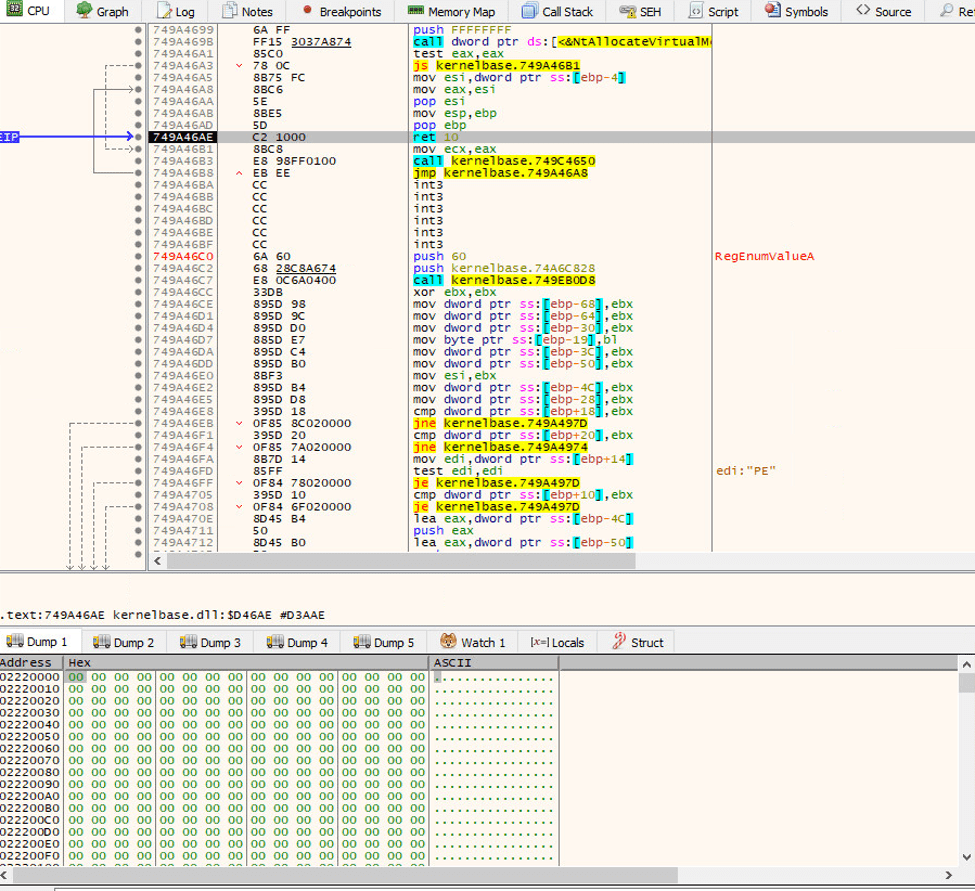
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

Reverse Engineering Emotet. (Behavior and Static Analysis), by Bruno Costa

The current Emotet malware threat: How can you protect your fleet?

GIAC Reverse Engineering Malware (GREM) - Credly
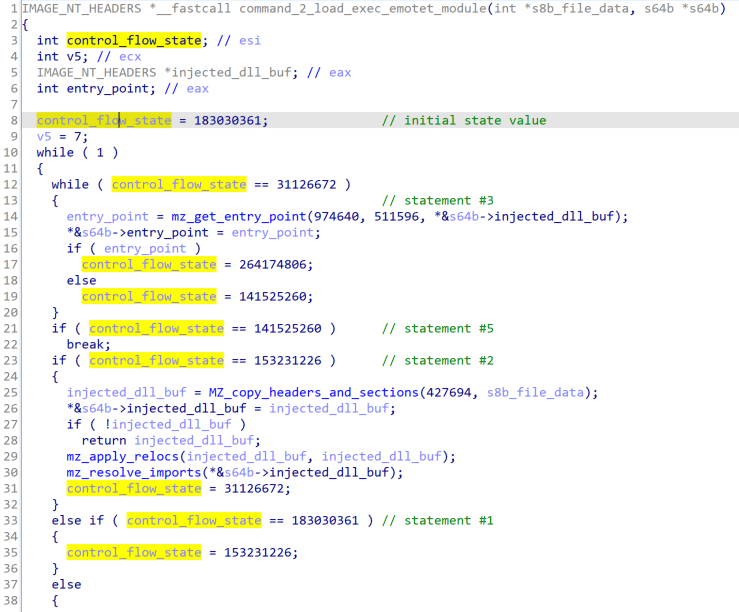
Return of Emotet: Malware Analysis
Recomendado para você
-
 Terraria bosses: how to summon and defeat them21 fevereiro 2025
Terraria bosses: how to summon and defeat them21 fevereiro 2025 -
 Moon Lord - Terraria Wiki21 fevereiro 2025
Moon Lord - Terraria Wiki21 fevereiro 2025 -
Steam Community :: Guide :: [2022] Terraria Ranger Guide (1.4.3)21 fevereiro 2025
-
 Brain of Cthulhu in Terraria21 fevereiro 2025
Brain of Cthulhu in Terraria21 fevereiro 2025 -
Progression Guide Terraria21 fevereiro 2025
-
 Terraria 1.4 Master Mode Boss Progression Guide - SteamAH21 fevereiro 2025
Terraria 1.4 Master Mode Boss Progression Guide - SteamAH21 fevereiro 2025 -
 Bosses (Homeward Journey) - Official Terraria Mods Wiki21 fevereiro 2025
Bosses (Homeward Journey) - Official Terraria Mods Wiki21 fevereiro 2025 -
 Bosses - Spirit Mod Wiki21 fevereiro 2025
Bosses - Spirit Mod Wiki21 fevereiro 2025 -
 Terraria - All Progression Pre-Boss - Steam Lists21 fevereiro 2025
Terraria - All Progression Pre-Boss - Steam Lists21 fevereiro 2025 -
 Pre Bosses Summoner Progression Guide // Terraria 1.4.4.721 fevereiro 2025
Pre Bosses Summoner Progression Guide // Terraria 1.4.4.721 fevereiro 2025
você pode gostar
-
 Livro - Vida Após Suicídio - Livros de Autoajuda - Magazine Luiza21 fevereiro 2025
Livro - Vida Após Suicídio - Livros de Autoajuda - Magazine Luiza21 fevereiro 2025 -
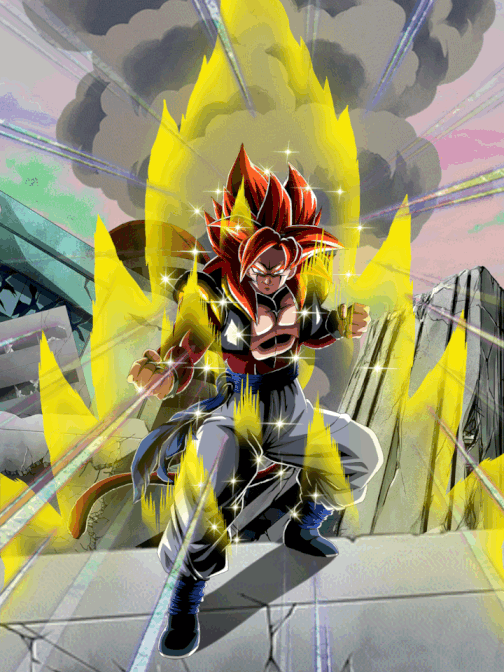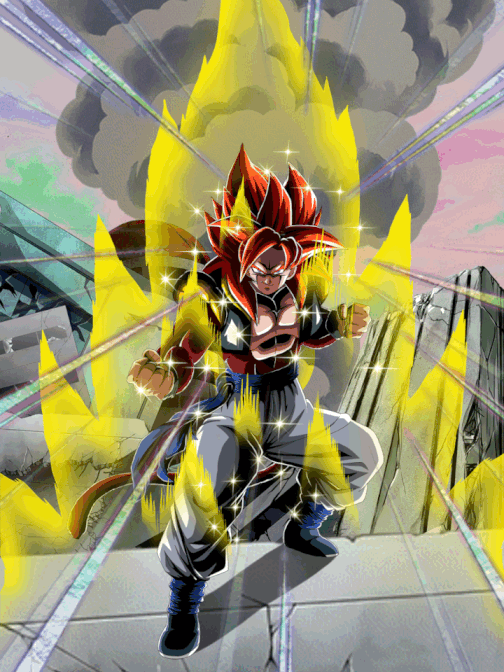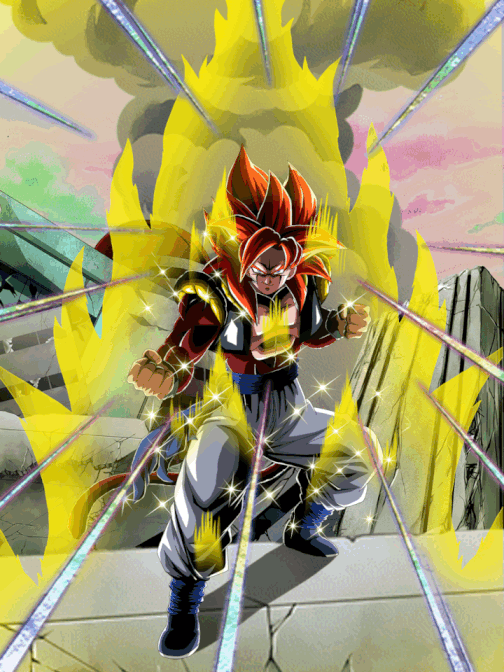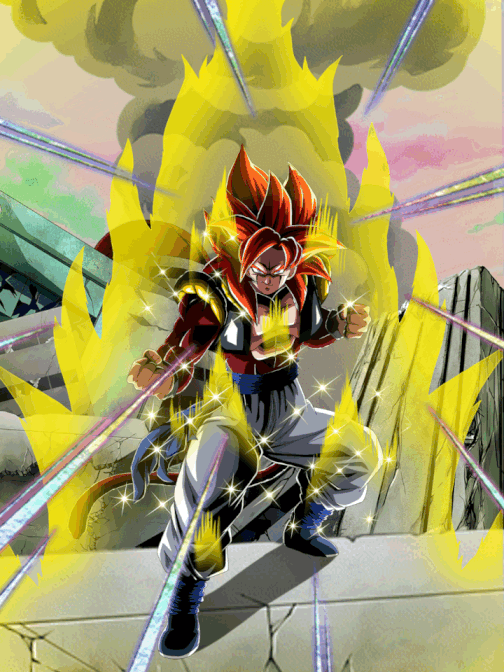 Pinnacle of Saiyan Might Super Saiyan 4 Gogeta, Dokfan Battle Wiki21 fevereiro 2025
Pinnacle of Saiyan Might Super Saiyan 4 Gogeta, Dokfan Battle Wiki21 fevereiro 2025 -
 FÍGADO DE FRANGO NA CEBOLA DOURADA21 fevereiro 2025
FÍGADO DE FRANGO NA CEBOLA DOURADA21 fevereiro 2025 -
format(webp)) Oshi no Ko : L'opening atteint (déjà) 100 millions de vues et écoutes en streaming dans le monde - Crunchyroll News21 fevereiro 2025
Oshi no Ko : L'opening atteint (déjà) 100 millions de vues et écoutes en streaming dans le monde - Crunchyroll News21 fevereiro 2025 -
 Nexxus Shampoo & Conditioner Combo Pack, Therappe Humectress, Caviar Complex, 13.5 Oz Each21 fevereiro 2025
Nexxus Shampoo & Conditioner Combo Pack, Therappe Humectress, Caviar Complex, 13.5 Oz Each21 fevereiro 2025 -
 Conta de Roblox Anime Adventures com - Roblox - Outros jogos Roblox - GGMAX21 fevereiro 2025
Conta de Roblox Anime Adventures com - Roblox - Outros jogos Roblox - GGMAX21 fevereiro 2025 -
 Which Roblox N looks better? : r/MurderDrones21 fevereiro 2025
Which Roblox N looks better? : r/MurderDrones21 fevereiro 2025 -
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/15494143/pc-red-alert.0.0.1441610107.gif) The PC industry is betting big on gamers - The Verge21 fevereiro 2025
The PC industry is betting big on gamers - The Verge21 fevereiro 2025 -
 The Legend of Zelda: The Wind Waker HD - Nintendo Wii U (European21 fevereiro 2025
The Legend of Zelda: The Wind Waker HD - Nintendo Wii U (European21 fevereiro 2025 -
 Buy Xbox Game Cards Online Safe. Secure. Pay with PayPal21 fevereiro 2025
Buy Xbox Game Cards Online Safe. Secure. Pay with PayPal21 fevereiro 2025
![Steam Community :: Guide :: [2022] Terraria Ranger Guide (1.4.3)](https://steamuserimages-a.akamaihd.net/ugc/1039715372122182453/AD57BB55E26954F0A41AB36DFFE4D4DDA6291273/)