11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 22 fevereiro 2025

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.

6 Common Phishing Attacks and How to Protect Against Them

The Comprehensive Guide to 11 Types of Malware in 2023 - TitanFile
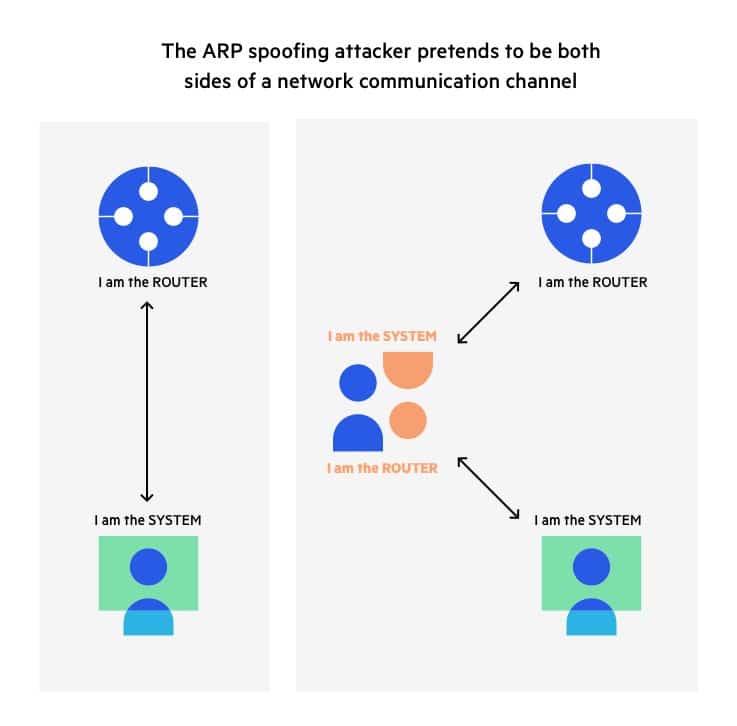
What is ARP Spoofing, ARP Cache Poisoning Attack Explained
Detecting Domain Name Abuse – Security Spotlight

7 Types of Spoofing Attacks And How To Detect Them

Types of Cyber Attacks You Should Be Aware of in 2024

13 Common Types of Cyber Attacks and How to Prevent Them

Top Types of Spoofing Attacks – Gridinsoft Blogs

5 Common Types of Phishing Attacks

Must Know Phishing Statistics In 2023 - Attacks And Breaches

What Is Spoofing? Don't Be Caught Out - ClearVPN

What is Spoofing?, Examples & Prevention
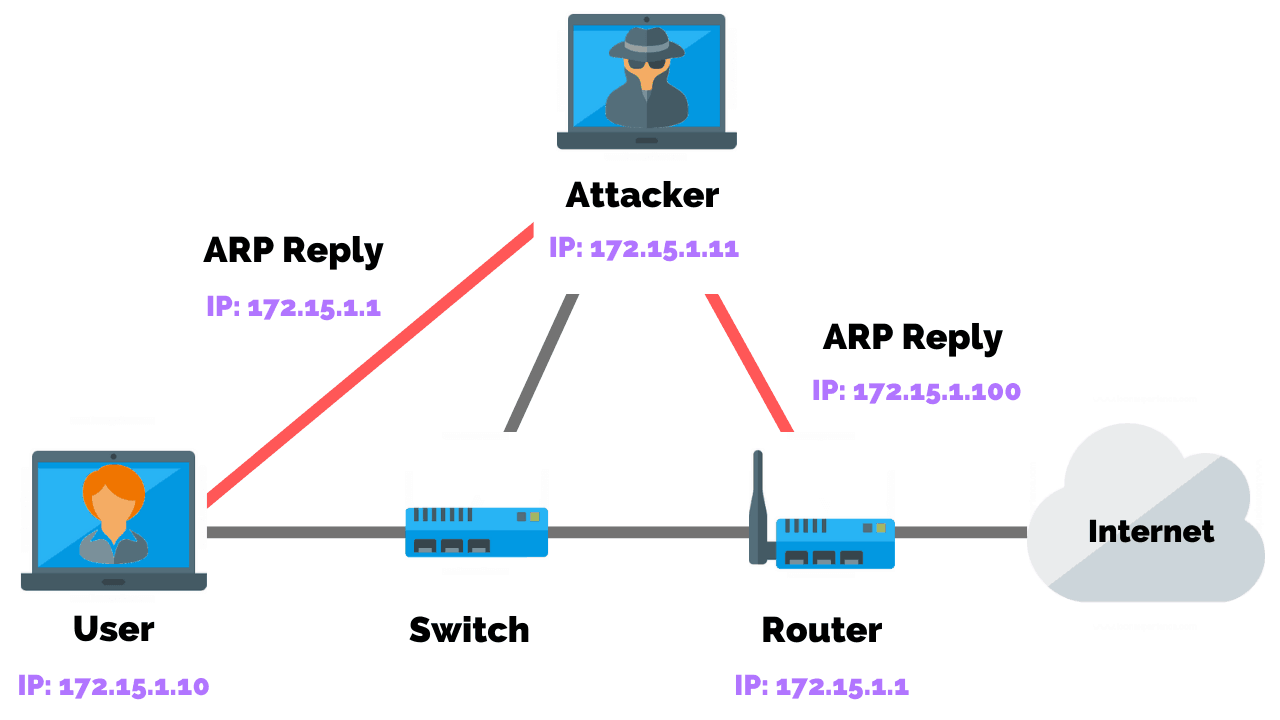
How To Prevent Network Attacks
Recomendado para você
-
 Spoofer Redengine Semanal - Others - DFG22 fevereiro 2025
Spoofer Redengine Semanal - Others - DFG22 fevereiro 2025 -
 Interfacing with CAST Navigation GNSS/INS Simulation Solutions22 fevereiro 2025
Interfacing with CAST Navigation GNSS/INS Simulation Solutions22 fevereiro 2025 -
 James the Red Engine, Movie Spoof Films Wikia22 fevereiro 2025
James the Red Engine, Movie Spoof Films Wikia22 fevereiro 2025 -
best fivem spoofer free|TikTok Search22 fevereiro 2025
-
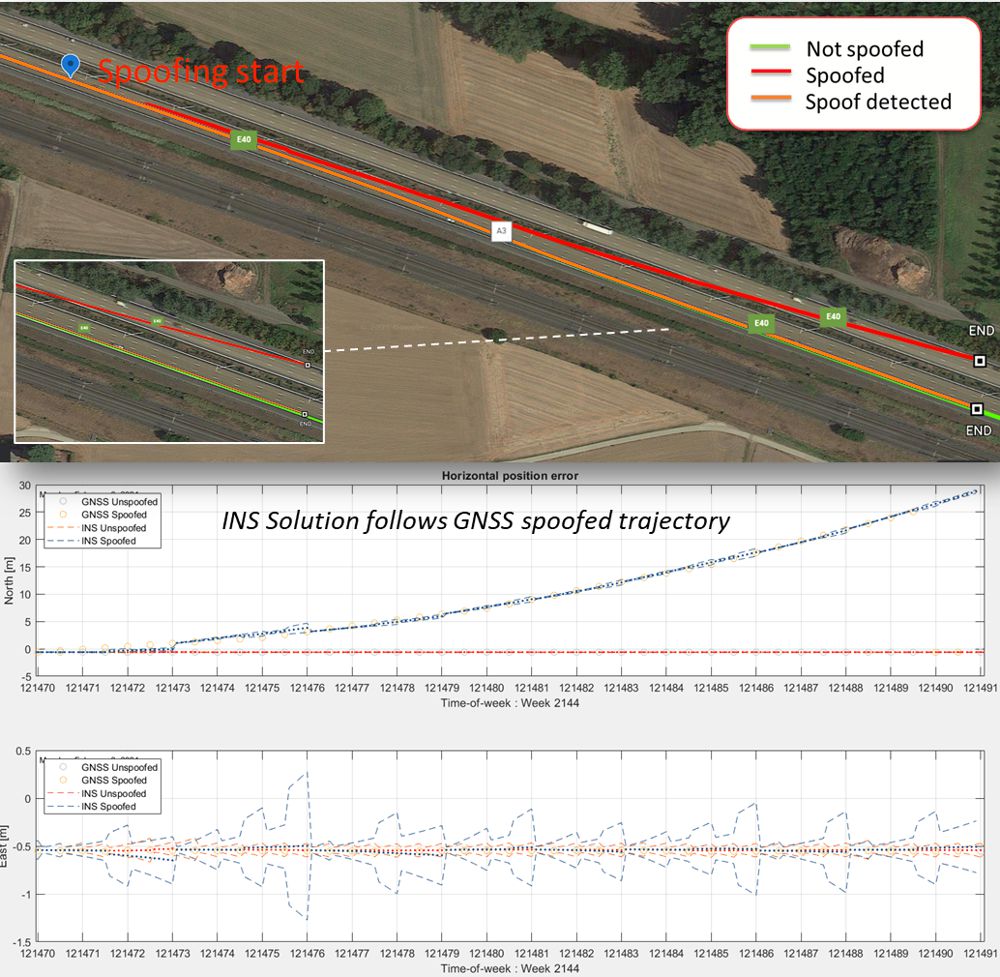 Secure GPS receivers are crucial for GNSS/INS systems - Highways Today22 fevereiro 2025
Secure GPS receivers are crucial for GNSS/INS systems - Highways Today22 fevereiro 2025 -
Eulen or redengine? #cheating #eulen #fivem #jus2rich #gaming22 fevereiro 2025
-
 Protecting GPS From Spoofers Is Critical to the Future of22 fevereiro 2025
Protecting GPS From Spoofers Is Critical to the Future of22 fevereiro 2025 -
 1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for22 fevereiro 2025
1PC RED MAGIC Quasi-Speed Fan Simulator Spoofer Remover for22 fevereiro 2025 -
 Protecting GPS From Spoofers Is Critical to the Future of Navigation22 fevereiro 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation22 fevereiro 2025 -
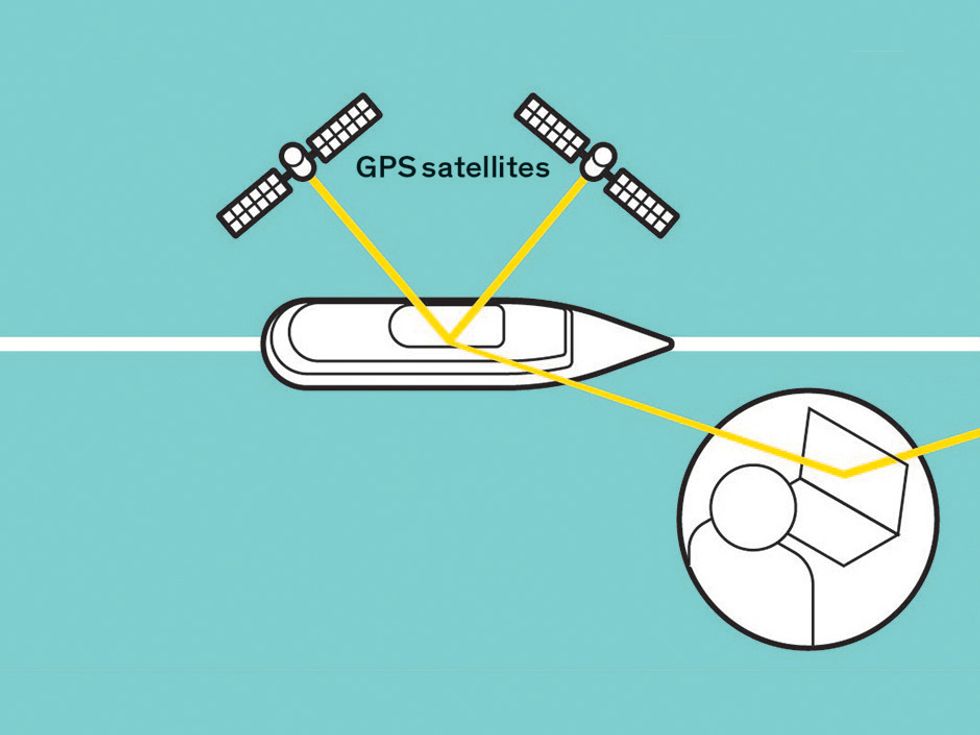 Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum22 fevereiro 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum22 fevereiro 2025
você pode gostar
-
 O Lado Bom da Vida (Livro e Filme)22 fevereiro 2025
O Lado Bom da Vida (Livro e Filme)22 fevereiro 2025 -
 D&D Adventure: Curse of Strahd Revamped Box Set22 fevereiro 2025
D&D Adventure: Curse of Strahd Revamped Box Set22 fevereiro 2025 -
 Caderno Pequeno 1/4 Brochura 80 Folhas Free Fire TILIBRA22 fevereiro 2025
Caderno Pequeno 1/4 Brochura 80 Folhas Free Fire TILIBRA22 fevereiro 2025 -
 FINAIS DA COPA DO BRASIL (2000-2022)22 fevereiro 2025
FINAIS DA COPA DO BRASIL (2000-2022)22 fevereiro 2025 -
 The Witcher Season 3, Part 2 Release Date, Story & Everything We Know22 fevereiro 2025
The Witcher Season 3, Part 2 Release Date, Story & Everything We Know22 fevereiro 2025 -
Miranda #041 grau e corte22 fevereiro 2025
-
 Última a Sair de Beach City, Steven Universo Wiki22 fevereiro 2025
Última a Sair de Beach City, Steven Universo Wiki22 fevereiro 2025 -
![TBH White YIPPEE Creature Plush [8 Inch] - DayLikesCookies's Ko-fi Shop](https://storage.ko-fi.com/cdn/useruploads/display/f5fee0d8-7eca-4d6c-af1c-47459c3a8eeb_20220921_003250_by_daylikescookies_dfex1vt.jpg) TBH White YIPPEE Creature Plush [8 Inch] - DayLikesCookies's Ko-fi Shop22 fevereiro 2025
TBH White YIPPEE Creature Plush [8 Inch] - DayLikesCookies's Ko-fi Shop22 fevereiro 2025 -
 Mandalorian Jetpack Beskar / Din Djarin Cosplay / Rising Phoenix Mando Jet22 fevereiro 2025
Mandalorian Jetpack Beskar / Din Djarin Cosplay / Rising Phoenix Mando Jet22 fevereiro 2025 -
 Mine craft: Story mode download distribution starts - GIGAZINE22 fevereiro 2025
Mine craft: Story mode download distribution starts - GIGAZINE22 fevereiro 2025


