Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Por um escritor misterioso
Last updated 18 janeiro 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
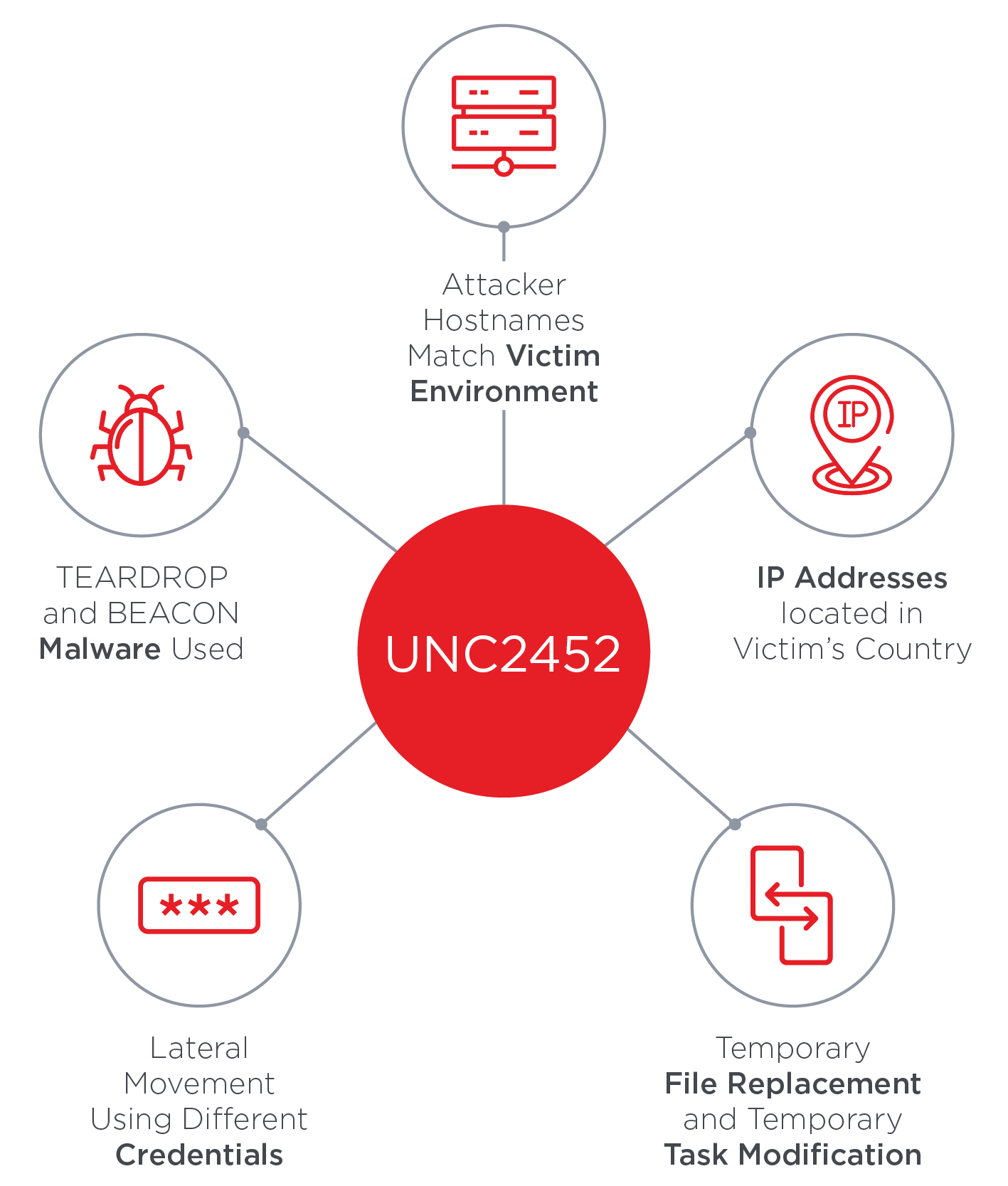
SolarWinds Supply Chain Attack Uses SUNBURST Backdoor

BOLO - Be On The Lookout: FireEye Red Team Tools Stolen in Nation
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

FireEye veterans launch threat intelligence firm Silent Push with
Tactics, Techniques and Procedures of FireEye Red Team Tools

FireEye Threat Intelligence

TTPs Within Cyber Threat Intelligence

FireEye offers proactive OT environment protection with latest
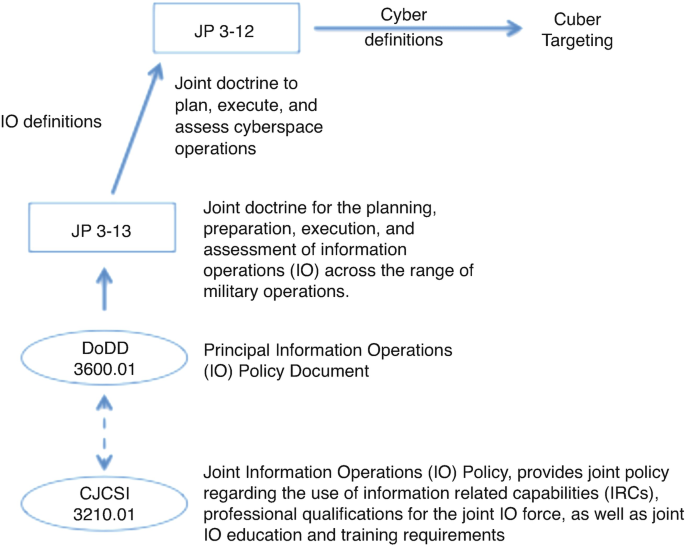
Cyber Policy, Doctrine, and Tactics, Techniques, and Procedures
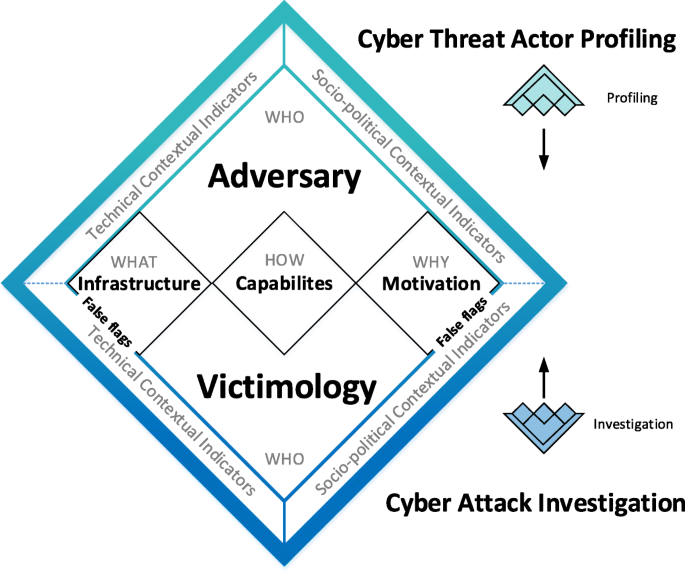
Under false flag: using technical artifacts for cyber attack

TagTeam :: Investigating with Indicators of Compromise (IOCs
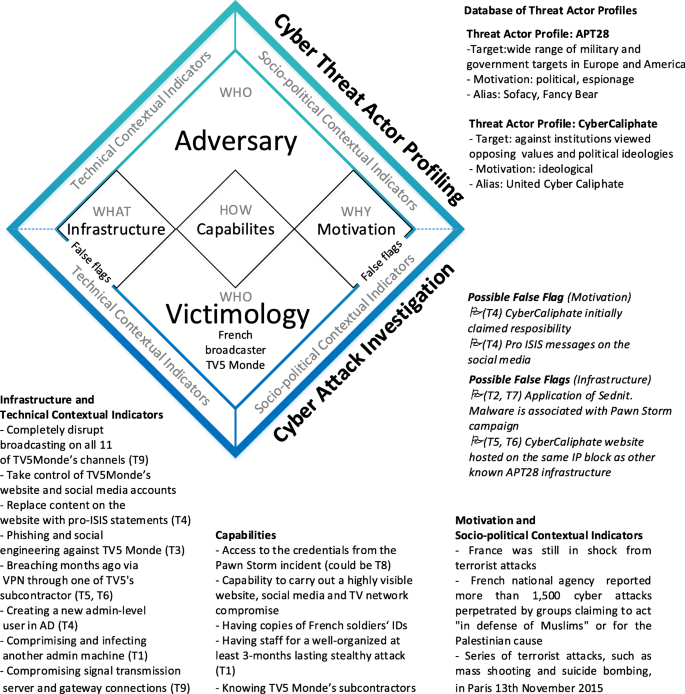
Under false flag: using technical artifacts for cyber attack
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Recomendado para você
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG18 janeiro 2025
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG18 janeiro 2025 -
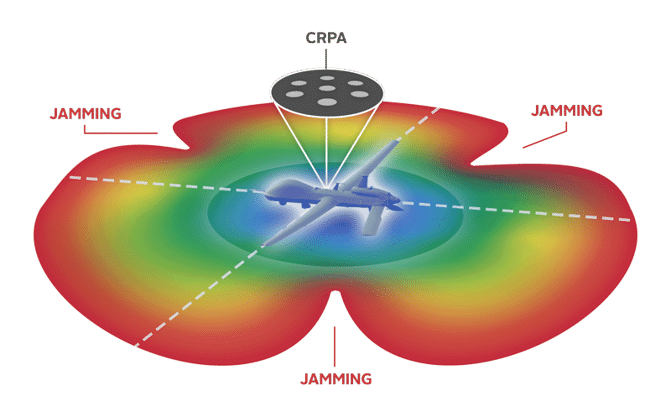 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing18 janeiro 2025
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing18 janeiro 2025 -
 CAIDA Catalog Search - A Collection of Scientific Research on the18 janeiro 2025
CAIDA Catalog Search - A Collection of Scientific Research on the18 janeiro 2025 -
Hack The Seas Village - AIS Spoofing Attacks and Some Tools - TIB18 janeiro 2025
-
RoDAR the Equaliser18 janeiro 2025
-
Red Engine Un Ban18 janeiro 2025
-
 Pokemod Devs released info on what they believe is behind the most18 janeiro 2025
Pokemod Devs released info on what they believe is behind the most18 janeiro 2025 -
 Precision Digital Webinars18 janeiro 2025
Precision Digital Webinars18 janeiro 2025 -
 How Do MAC Spoofing Attacks Work?18 janeiro 2025
How Do MAC Spoofing Attacks Work?18 janeiro 2025 -
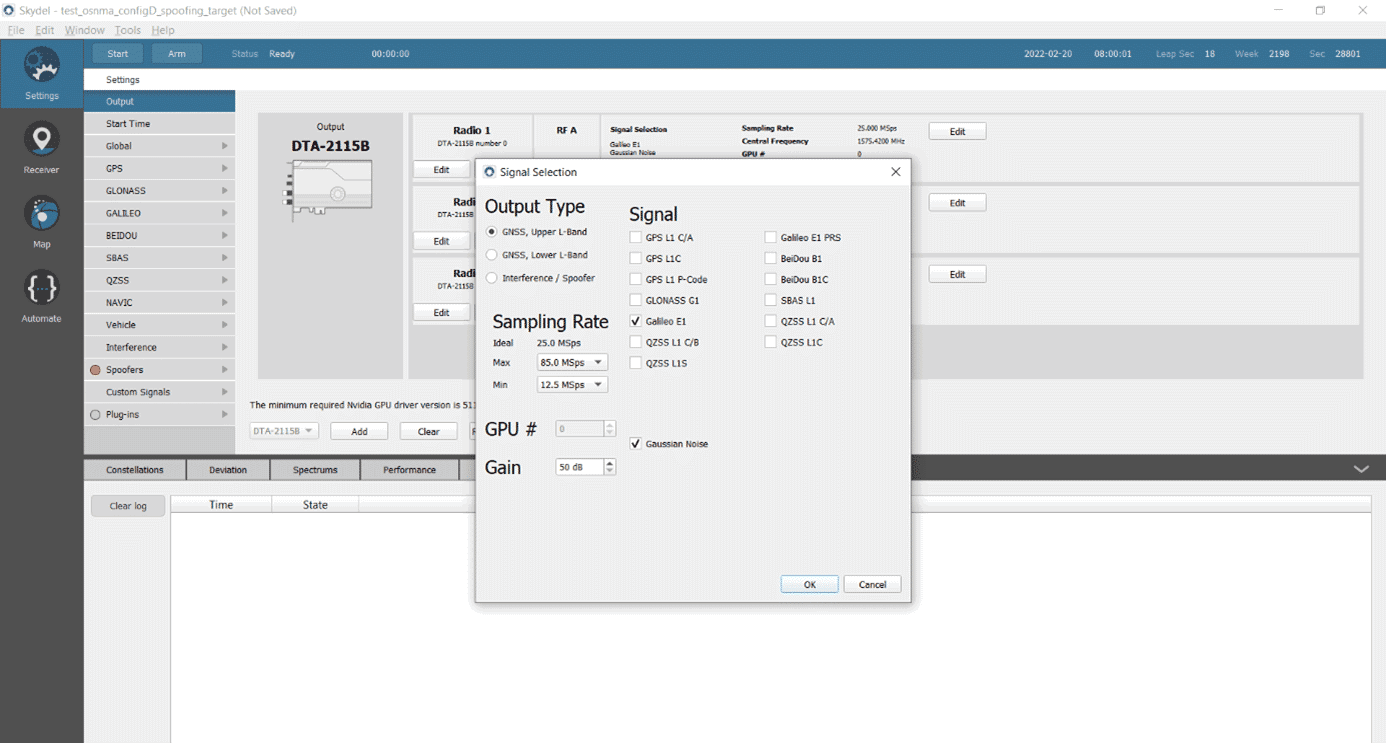 Testing a Receiver's Galileo OS-NMA Capability Using Skydel18 janeiro 2025
Testing a Receiver's Galileo OS-NMA Capability Using Skydel18 janeiro 2025
você pode gostar
-
 toy chica jumpscare - ibisPaint18 janeiro 2025
toy chica jumpscare - ibisPaint18 janeiro 2025 -
 Titanfall 2: Estos son los requisitos mínimos y recomendados - PC18 janeiro 2025
Titanfall 2: Estos son los requisitos mínimos y recomendados - PC18 janeiro 2025 -
 Bragg Gaming on X: Bragg's ORYX Gaming has won the Casino Product18 janeiro 2025
Bragg Gaming on X: Bragg's ORYX Gaming has won the Casino Product18 janeiro 2025 -
 Various types and shapes pasta, noodles and macaroni with cereal ear realistic vector illustration set isolated on white. Italian national cuisine traditional ingredient. Natural healthy eating food Stock Vector18 janeiro 2025
Various types and shapes pasta, noodles and macaroni with cereal ear realistic vector illustration set isolated on white. Italian national cuisine traditional ingredient. Natural healthy eating food Stock Vector18 janeiro 2025 -
 Marvel Universe Avengers Assemble Season Two (2014) #118 janeiro 2025
Marvel Universe Avengers Assemble Season Two (2014) #118 janeiro 2025 -
 PDF) Traduções do fantástico de Roald Dahl: um estudo baseado no corpus da obra Charlie and the Chocolate Factory18 janeiro 2025
PDF) Traduções do fantástico de Roald Dahl: um estudo baseado no corpus da obra Charlie and the Chocolate Factory18 janeiro 2025 -
 Attack on Titan – The Final Season (Episodes 76 – 87) Review18 janeiro 2025
Attack on Titan – The Final Season (Episodes 76 – 87) Review18 janeiro 2025 -
 Fairy Tail RPG?! Fairy Tail Amino18 janeiro 2025
Fairy Tail RPG?! Fairy Tail Amino18 janeiro 2025 -
Builderman Shoulder Buddy Minion's Code & Price - RblxTrade18 janeiro 2025
-
 Pin by My Info on ok Roblox shirt, Create shirts, T shirt design template18 janeiro 2025
Pin by My Info on ok Roblox shirt, Create shirts, T shirt design template18 janeiro 2025