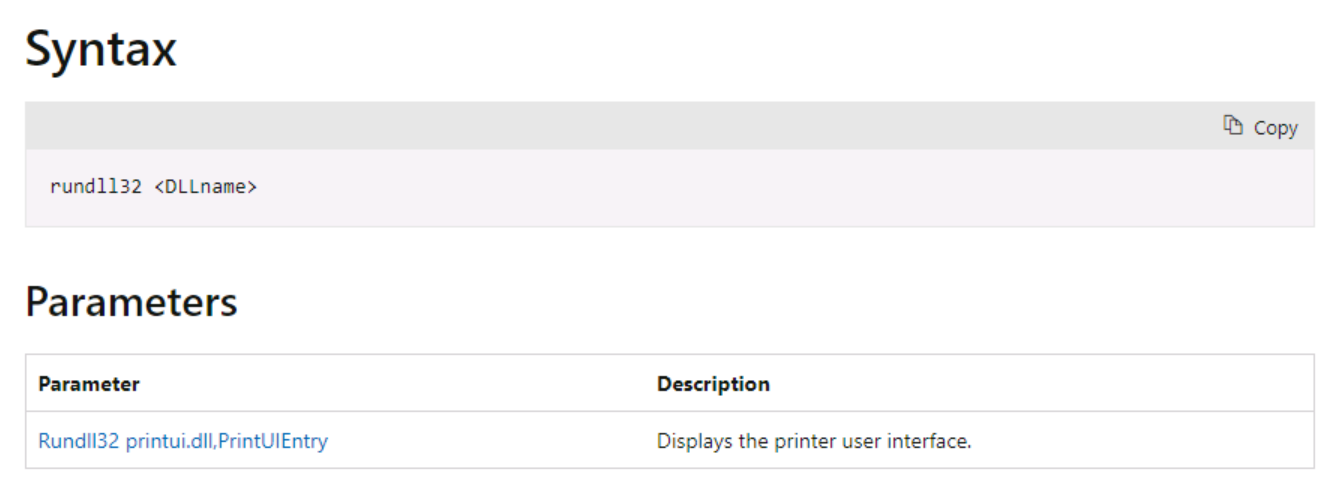
Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Last updated 17 janeiro 2025
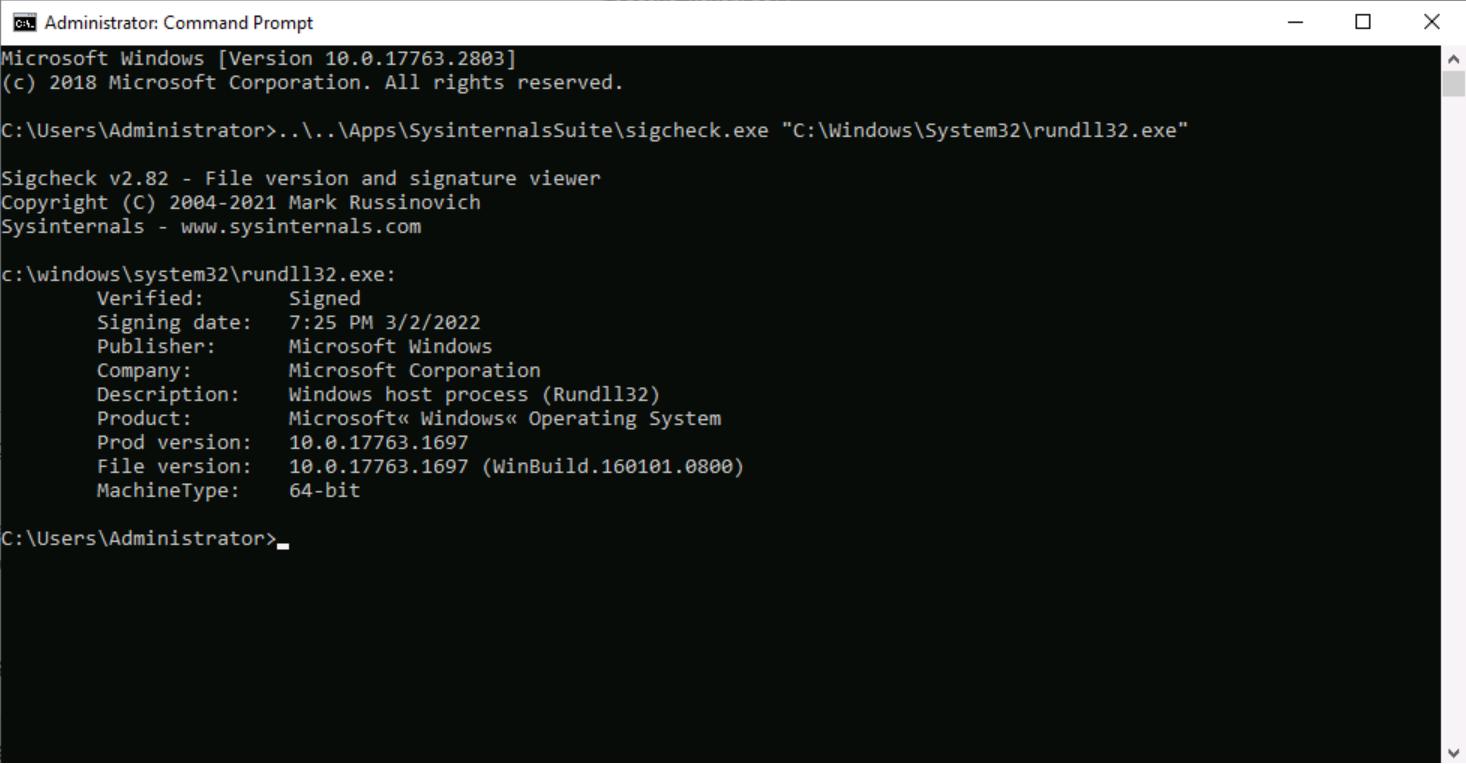
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

themed campaigns of Lazarus in the Netherlands and Belgium
Shelob Moonlight – Spinning a Larger Web From IcedID to CONTI, a Trojan and Ransomware collaboration - Cynet

Silvio R. (@Pinas_) / X
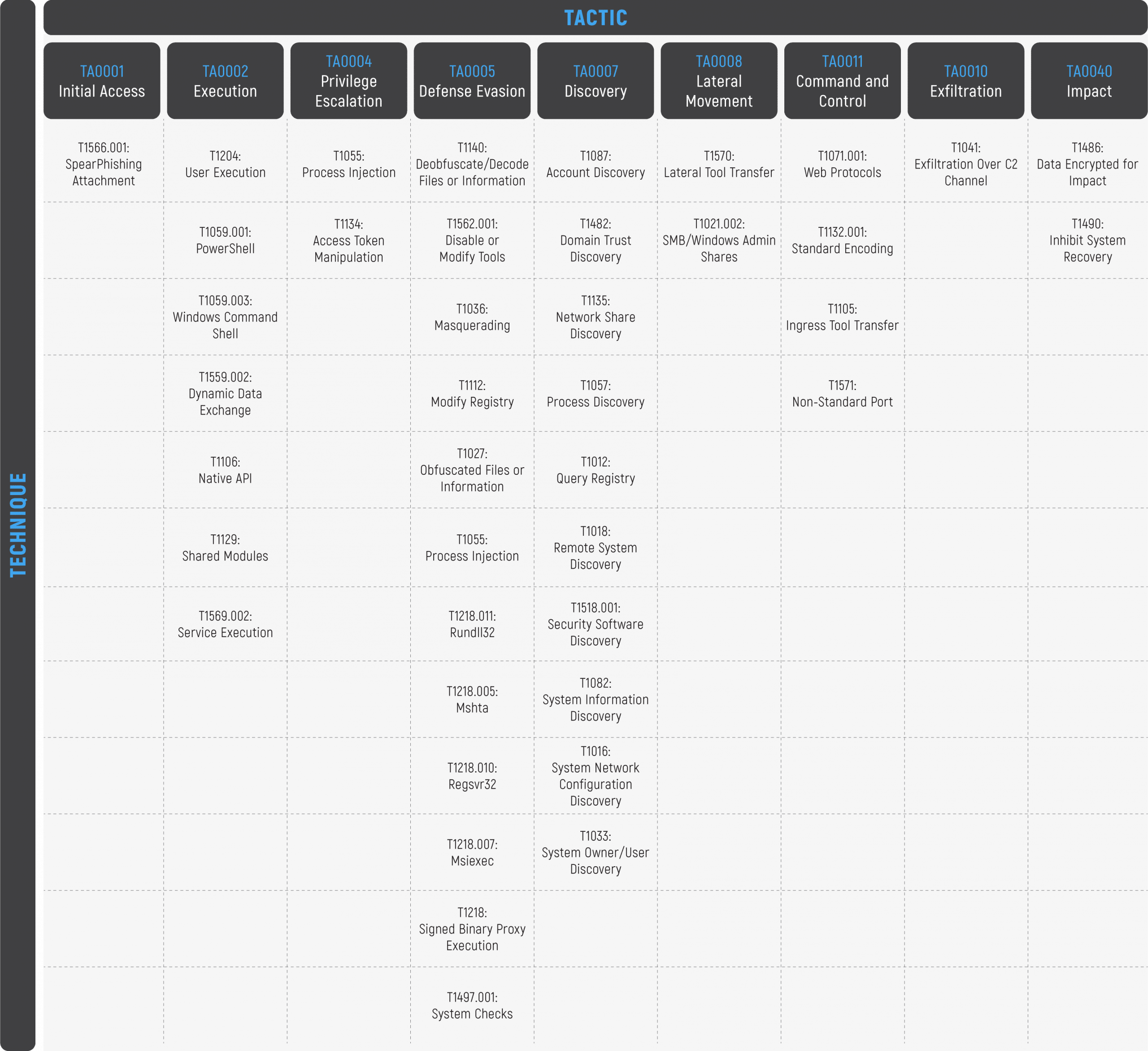
System Binary Proxy Execution Rundll32, Nordic Defender

Virus Bulletin on X: The Cybereason Blue Team describe how Microsoft's rundll32.exe tool, which allows code to be loaded and executed, is often used by adversaries during their offensive operations. /
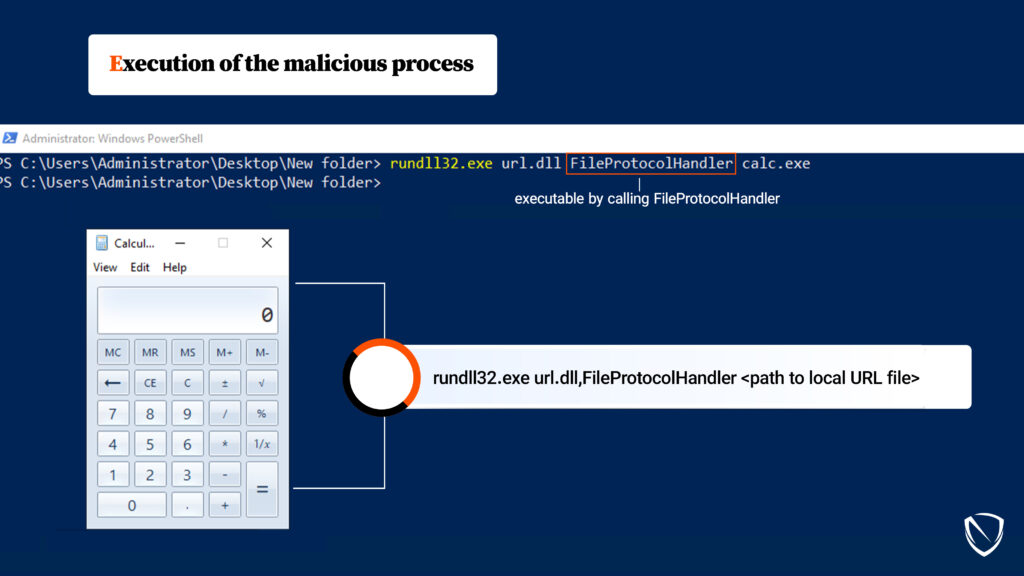
Threat Intelligence Report
Rundll32: The Infamous Proxy for Executing Malicious Code

Swedish Windows Security User Group » NOBELIUM
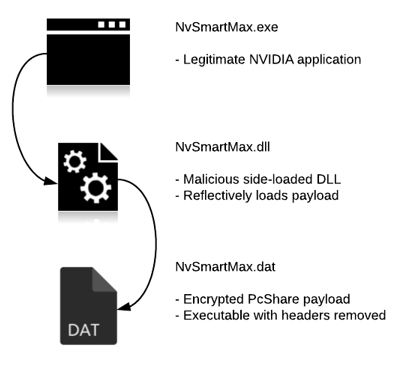
PcShare Backdoor Attacks Targeting Windows Users with FakeNarrator Malware
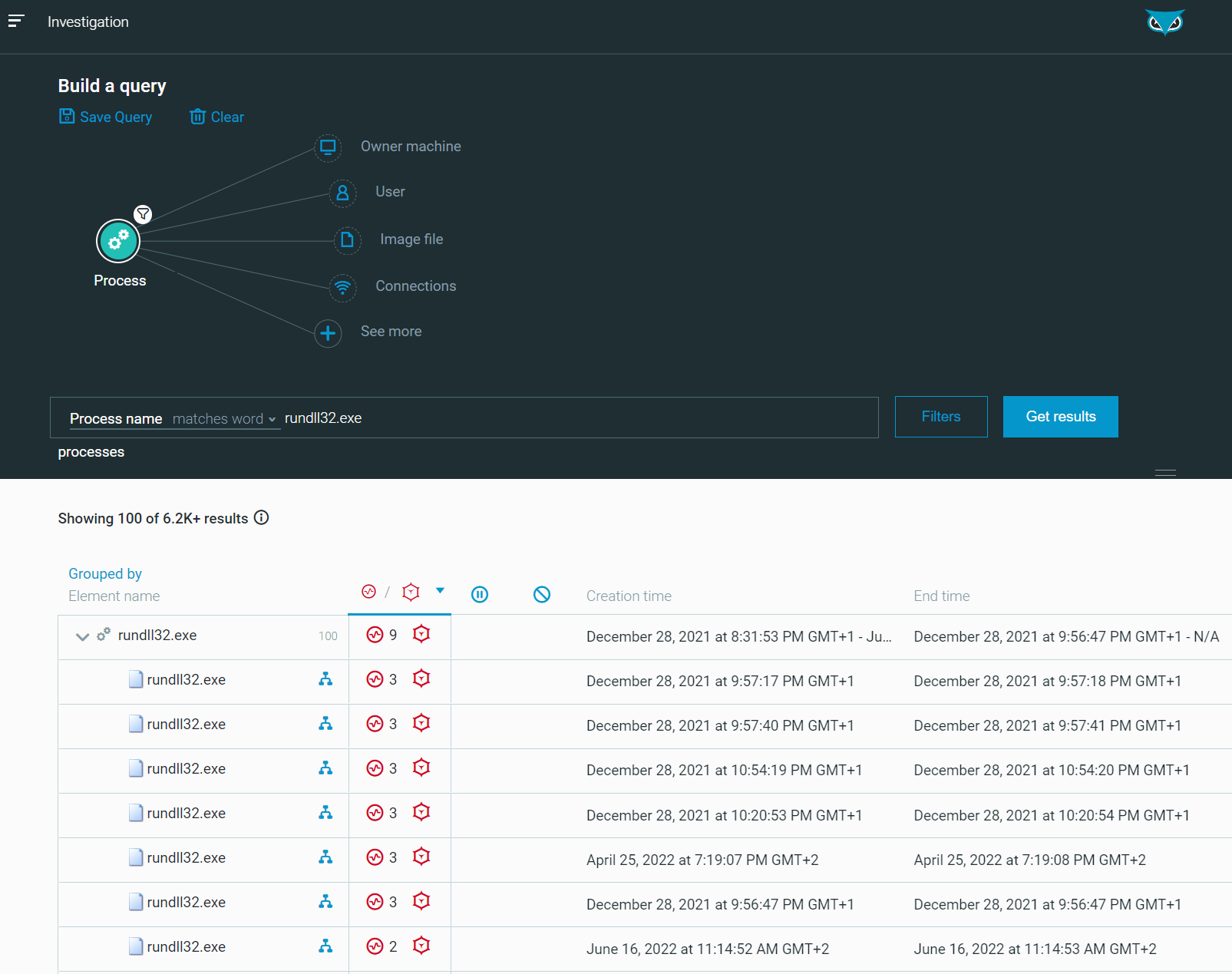
Rundll32: The Infamous Proxy for Executing Malicious Code

4 malicious campaigns, 13 confirmed victims, and a new wave of APT41 attacks

The second program that was found is rundll32exe which is a Microsoft signed

The Windows Process Journey: by Dr. Shlomi Boutnaru, PDF, Windows Registry
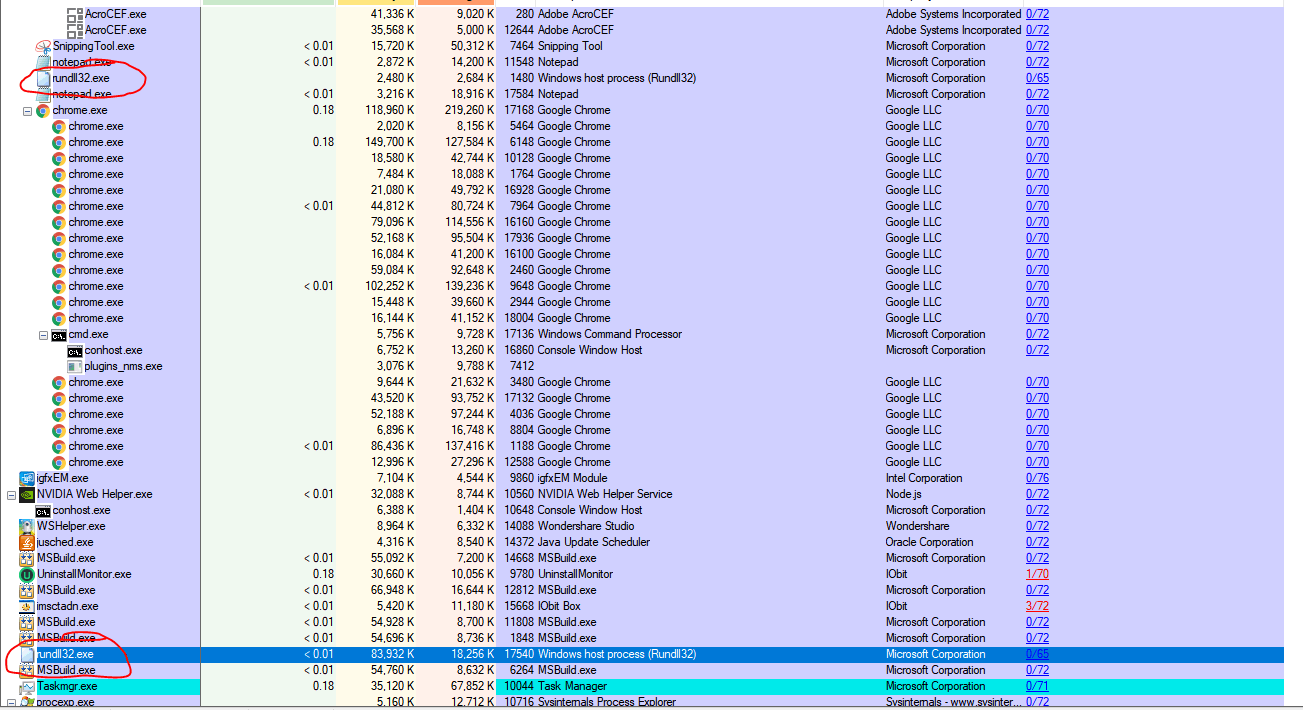
Rundll32 Injected with mining malware - Microsoft Community

Detect PlugX Trojan Masquerading as a Legitimate Windows Debugger Tool to Fly Under the Radar - SOC Prime
Recomendado para você
-
 Help for PDQ Deploy17 janeiro 2025
Help for PDQ Deploy17 janeiro 2025 -
 Unattended Installation - How to Silently Install your EXE using PowerShell & CMD?17 janeiro 2025
Unattended Installation - How to Silently Install your EXE using PowerShell & CMD?17 janeiro 2025 -
 AdvancedRun - Run a Windows program with different settings17 janeiro 2025
AdvancedRun - Run a Windows program with different settings17 janeiro 2025 -
 How to execute an SSIS package from the command line or a batch file – SQLServerCentral17 janeiro 2025
How to execute an SSIS package from the command line or a batch file – SQLServerCentral17 janeiro 2025 -
 How to Schedule a PowerShell Script17 janeiro 2025
How to Schedule a PowerShell Script17 janeiro 2025 -
 cmd - How do i run a program with arguments and as administrator17 janeiro 2025
cmd - How do i run a program with arguments and as administrator17 janeiro 2025 -
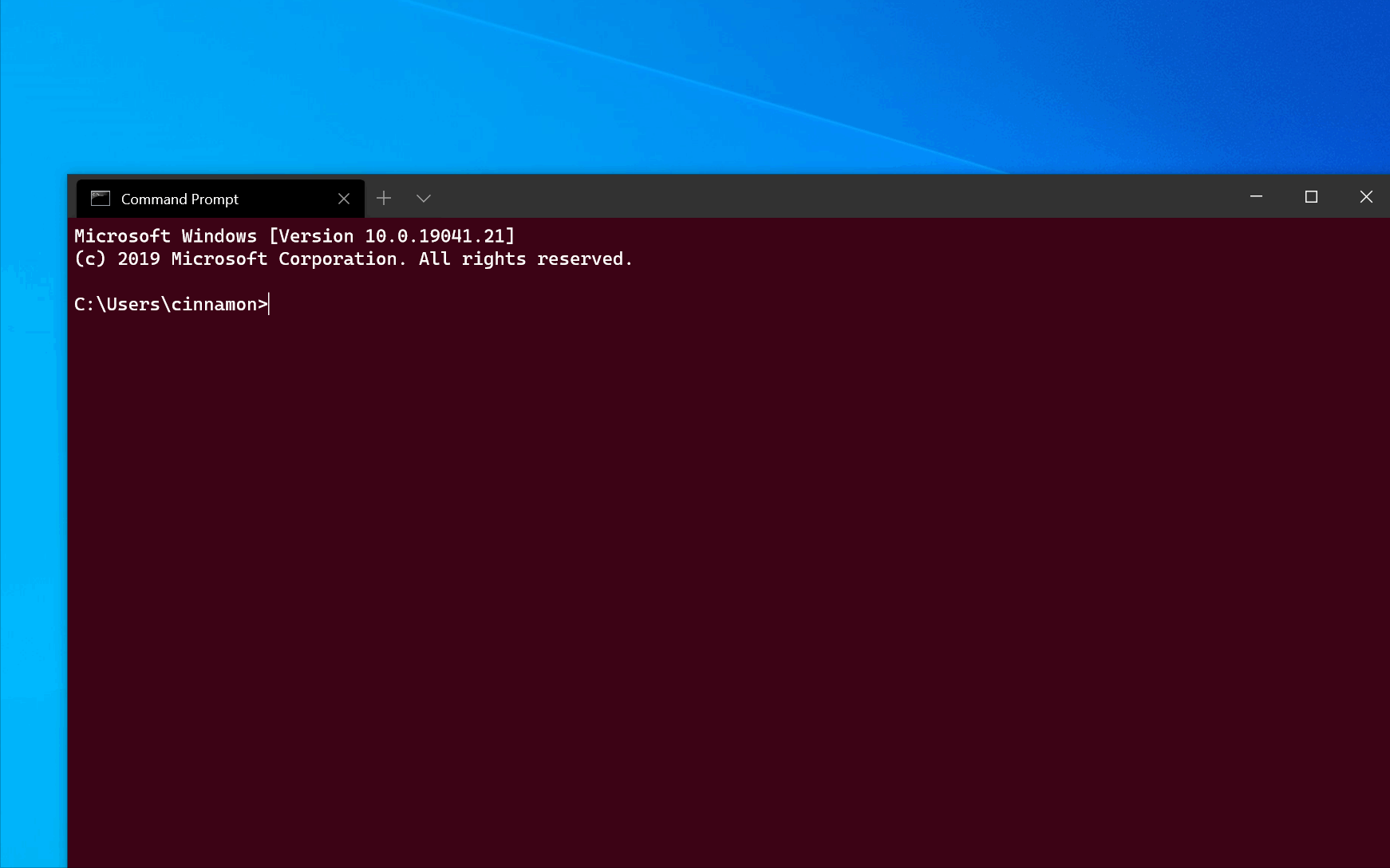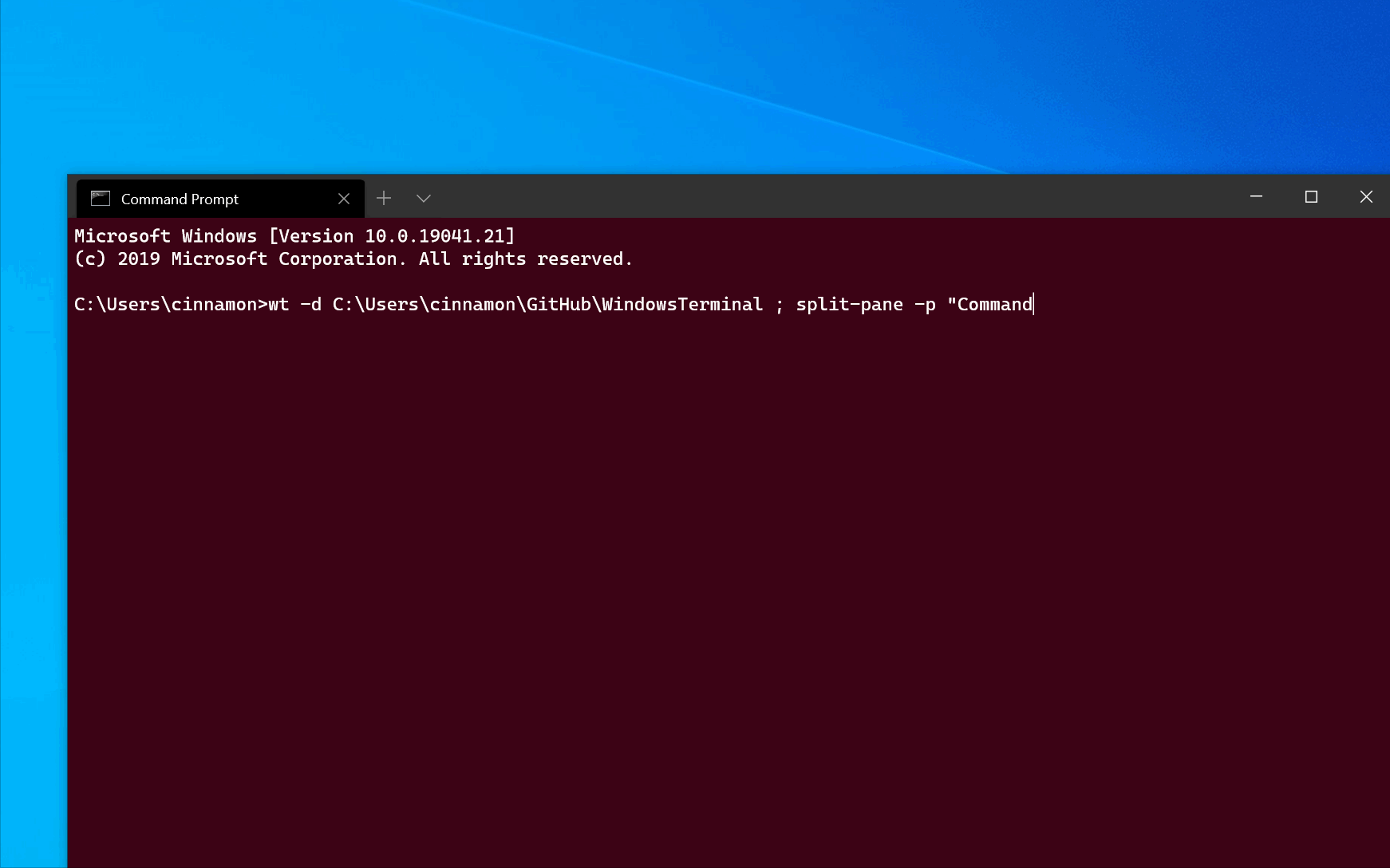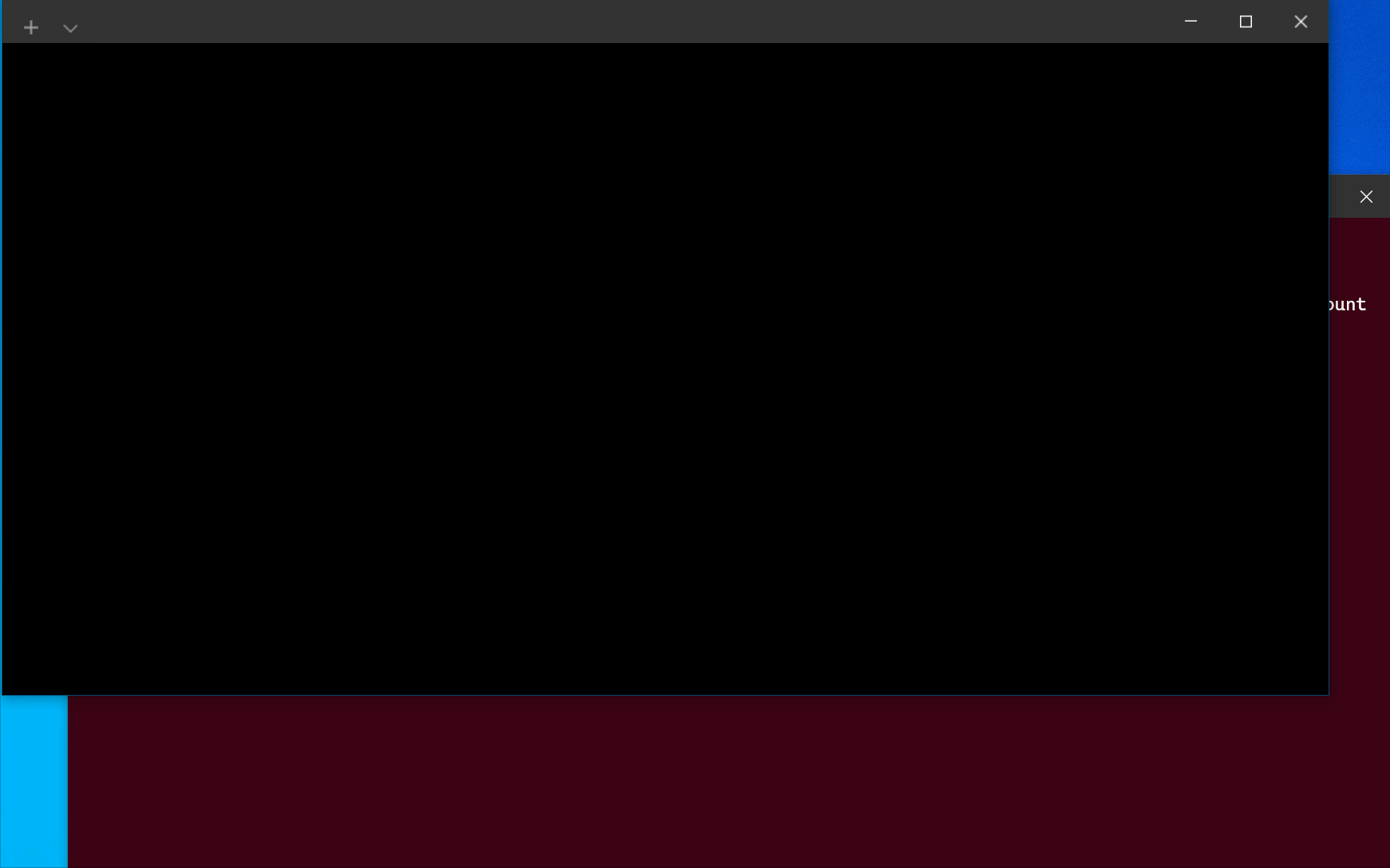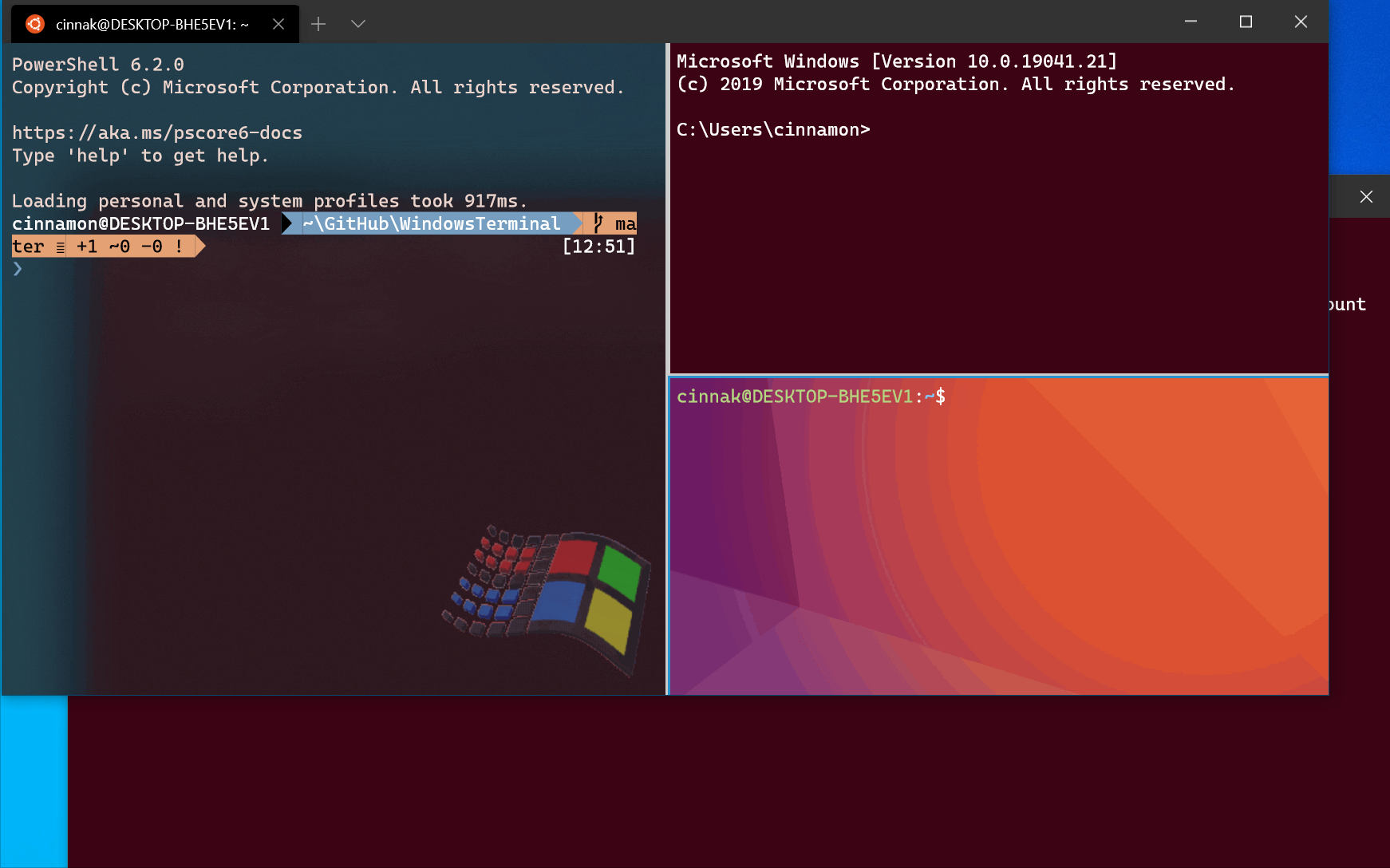 Windows Terminal command line arguments17 janeiro 2025
Windows Terminal command line arguments17 janeiro 2025 -
 Getting command line arguments in a Unity executable17 janeiro 2025
Getting command line arguments in a Unity executable17 janeiro 2025 -
 windows - Applying a command line argument to the binary exe when17 janeiro 2025
windows - Applying a command line argument to the binary exe when17 janeiro 2025 -
 Installing SQL Server from Command line(CMD) – MSSQLTREK17 janeiro 2025
Installing SQL Server from Command line(CMD) – MSSQLTREK17 janeiro 2025
você pode gostar
-
![Cars: Race-O-Rama [Disney Pixar] - Walmart.com](https://i.pinimg.com/474x/28/5a/e0/285ae0c6305055fc261473146d1946df.jpg) Cars: Race-O-Rama [Disney Pixar] - Walmart.com17 janeiro 2025
Cars: Race-O-Rama [Disney Pixar] - Walmart.com17 janeiro 2025 -
 13 pçs glitter borboleta feliz aniversário bolo toppers 3d rosa17 janeiro 2025
13 pçs glitter borboleta feliz aniversário bolo toppers 3d rosa17 janeiro 2025 -
 You actually can't convince me that Lego Dimensions didn't have17 janeiro 2025
You actually can't convince me that Lego Dimensions didn't have17 janeiro 2025 -
 Análise, Sabikui Bisco17 janeiro 2025
Análise, Sabikui Bisco17 janeiro 2025 -
Diogo Rodrigues - Peças e acessórios agrícolas17 janeiro 2025
-
 São Paulo-SP (Vila Maria) - Casa do Construtor17 janeiro 2025
São Paulo-SP (Vila Maria) - Casa do Construtor17 janeiro 2025 -
 CapCut_dih a amar ai video e dek17 janeiro 2025
CapCut_dih a amar ai video e dek17 janeiro 2025 -
 The Risks of Fentanyl Poisoning To Teens - Natural High17 janeiro 2025
The Risks of Fentanyl Poisoning To Teens - Natural High17 janeiro 2025 -
 Cesare Borgia (Assassin's Creed), Pure Evil Wiki17 janeiro 2025
Cesare Borgia (Assassin's Creed), Pure Evil Wiki17 janeiro 2025 -
 Fantasma Games - Slots Beyond Gambling17 janeiro 2025
Fantasma Games - Slots Beyond Gambling17 janeiro 2025
