Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Last updated 22 fevereiro 2025


Threat Insight Information & Resources

Blog, News & Press Releases - Field Effect
Raccoon Stealer Announce Return After Hiatus
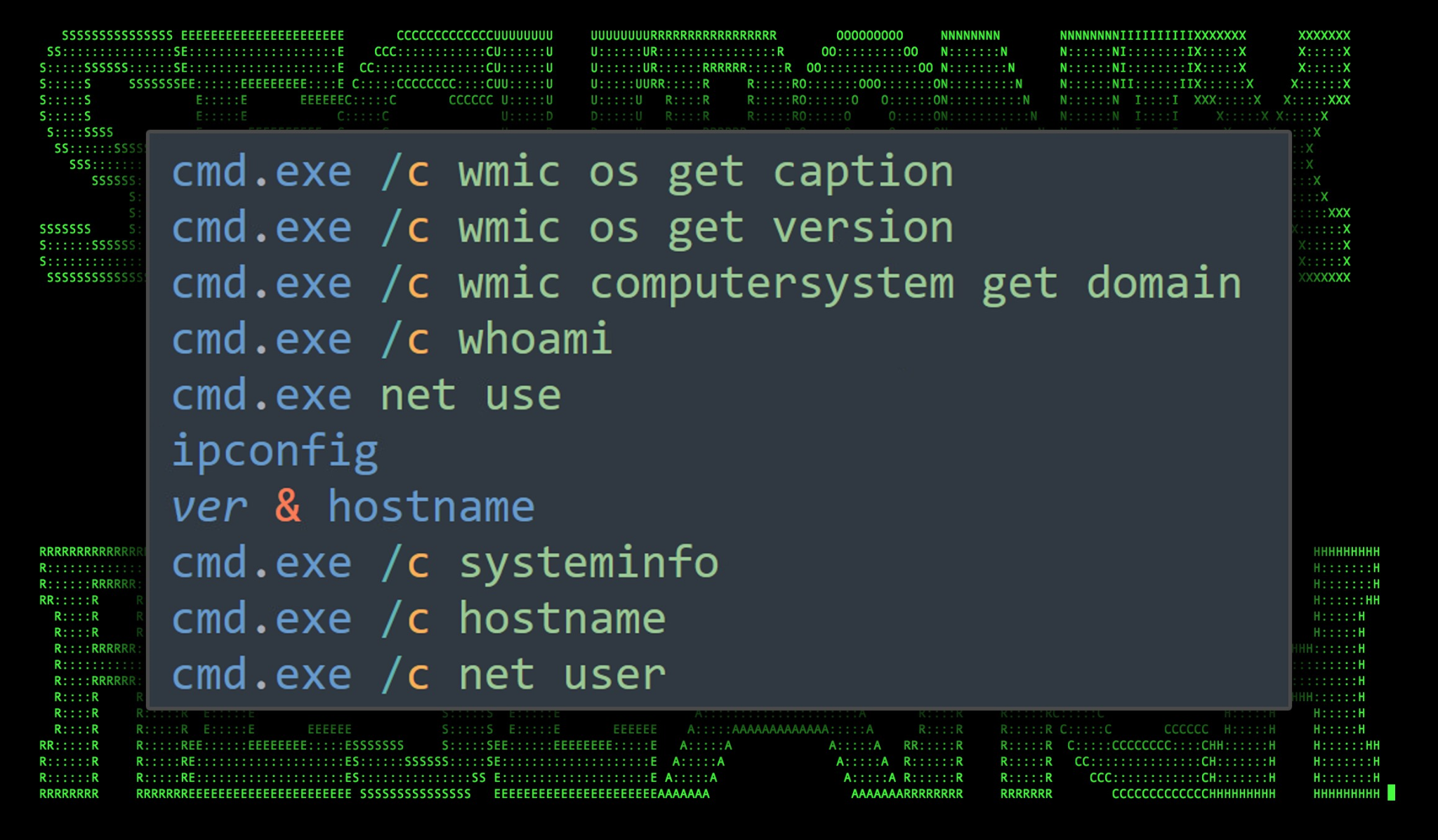
Securonix Threat Labs Security Advisory: Threat Actors Target
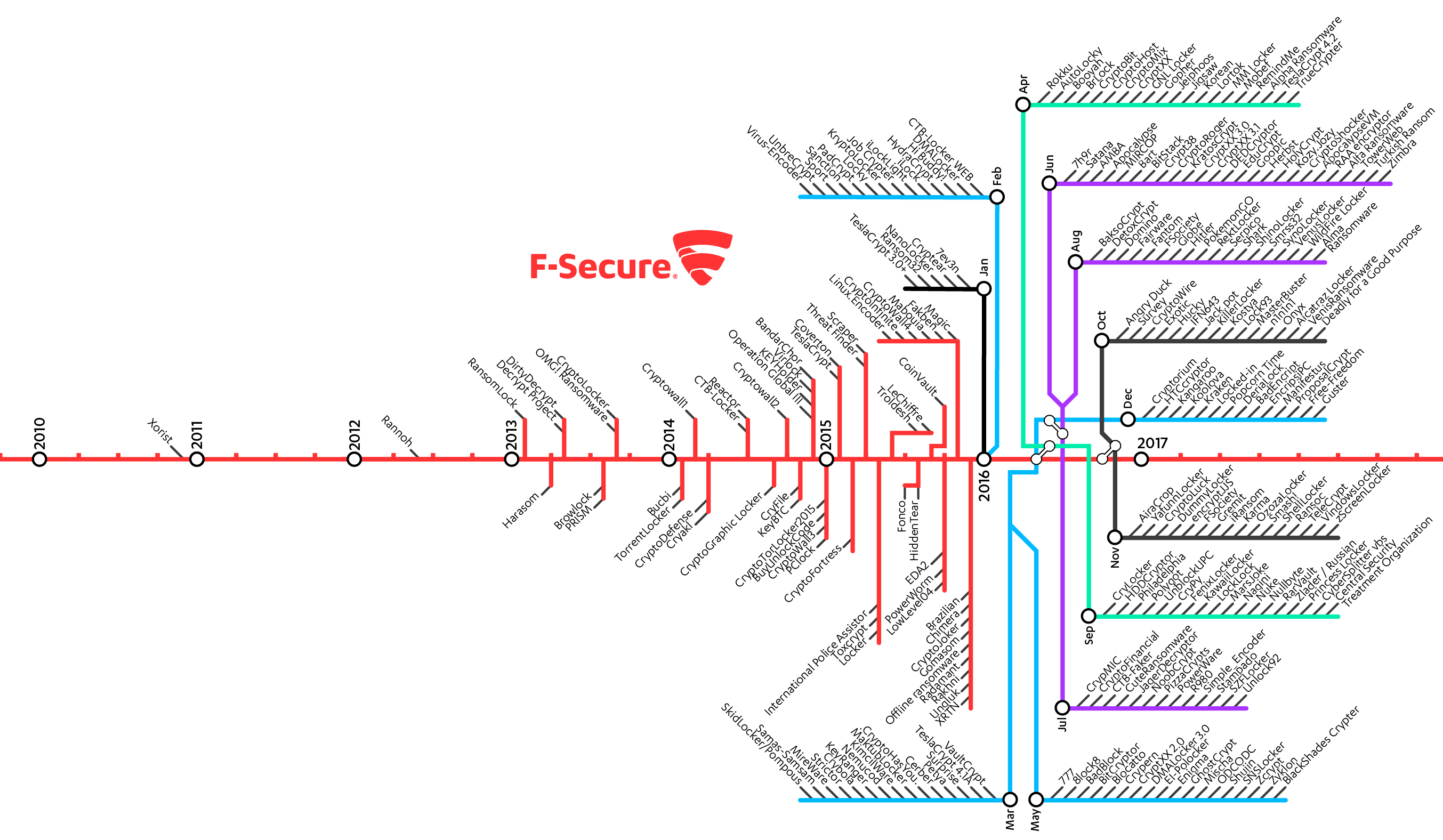
Ransomware Timeline: 2010 – 2017 - F-Secure Blog
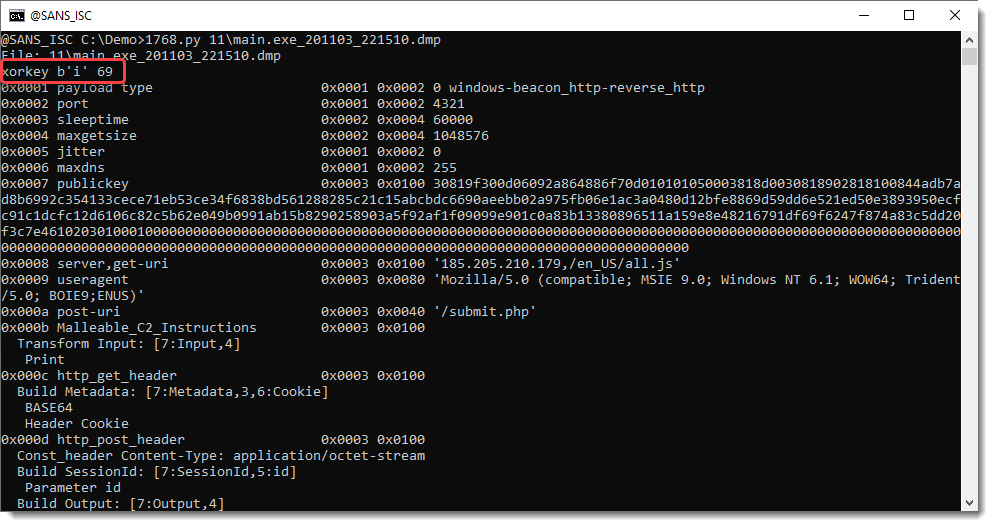
InfoSec Diary Blog Archive - SANS Internet Storm Center
The Top 50 InfoSec Blogs You Should Be Reading in 2019

ZINC weaponizing open-source software
The Unintentional Leak: A glimpse into the attack vectors of APT37
Recomendado para você
-
WiFi Password Hacker Prank - Apps on Google Play22 fevereiro 2025
-
Wifi Password Hacker - Microsoft Apps22 fevereiro 2025
-
Hacker App: Wifi Password Hack – Apps on Google Play22 fevereiro 2025
-
 Hasil gambar untuk hacker Hacker aesthetic, Hacker, Hacker programs22 fevereiro 2025
Hasil gambar untuk hacker Hacker aesthetic, Hacker, Hacker programs22 fevereiro 2025 -
 Look Like A Movie Hacker22 fevereiro 2025
Look Like A Movie Hacker22 fevereiro 2025 -
 35 Surprisingly Useful Websites You Never Knew You Needed22 fevereiro 2025
35 Surprisingly Useful Websites You Never Knew You Needed22 fevereiro 2025 -
 This Hacktivist Site Lets You Prank Call Russian Officials22 fevereiro 2025
This Hacktivist Site Lets You Prank Call Russian Officials22 fevereiro 2025 -
 Meet 'swatting,' the dangerous prank that could get someone killed22 fevereiro 2025
Meet 'swatting,' the dangerous prank that could get someone killed22 fevereiro 2025 -
 Hacking is a Mindset, Not a Skillset: Why civic hacking is key for22 fevereiro 2025
Hacking is a Mindset, Not a Skillset: Why civic hacking is key for22 fevereiro 2025 -
 Leave no trace: how a teenage hacker lost himself online22 fevereiro 2025
Leave no trace: how a teenage hacker lost himself online22 fevereiro 2025
você pode gostar
-
 Os esportes em Boston - Turismo em Boston22 fevereiro 2025
Os esportes em Boston - Turismo em Boston22 fevereiro 2025 -
O homem voltou ao fundo, 52 anos depois, Ciências22 fevereiro 2025
-
TOP 10 APELIDOS DO TONINHO TORNADO + Tutorial #CapCut22 fevereiro 2025
-
 Oretacha Youkai Ningen, BEM Wiki22 fevereiro 2025
Oretacha Youkai Ningen, BEM Wiki22 fevereiro 2025 -
 Country steep, Meaning not too long but you are in the wron…22 fevereiro 2025
Country steep, Meaning not too long but you are in the wron…22 fevereiro 2025 -
 PS Stars rewards : r/playstation22 fevereiro 2025
PS Stars rewards : r/playstation22 fevereiro 2025 -
 Watch I've Been Killing Slimes for 300 Years and Maxed Out My Level Episode 3 Online - Along Came an Elf22 fevereiro 2025
Watch I've Been Killing Slimes for 300 Years and Maxed Out My Level Episode 3 Online - Along Came an Elf22 fevereiro 2025 -
 Who Said 'Game of Thrones' Wasn't for Kids? - The New York Times22 fevereiro 2025
Who Said 'Game of Thrones' Wasn't for Kids? - The New York Times22 fevereiro 2025 -
 ALLES FREE IN TOCA BOCA?! #HappyMod, BESTIE GAMING Alina & Anika22 fevereiro 2025
ALLES FREE IN TOCA BOCA?! #HappyMod, BESTIE GAMING Alina & Anika22 fevereiro 2025 -
 Rekrutmen dan Pembinaan Calon Guru Sekolah Minggu & Asisten Guru - Gereja Presbyterian Orchard22 fevereiro 2025
Rekrutmen dan Pembinaan Calon Guru Sekolah Minggu & Asisten Guru - Gereja Presbyterian Orchard22 fevereiro 2025

