The Unacceptable Flaw with : Use of Game Explorer/DB in
Por um escritor misterioso
Last updated 21 fevereiro 2025
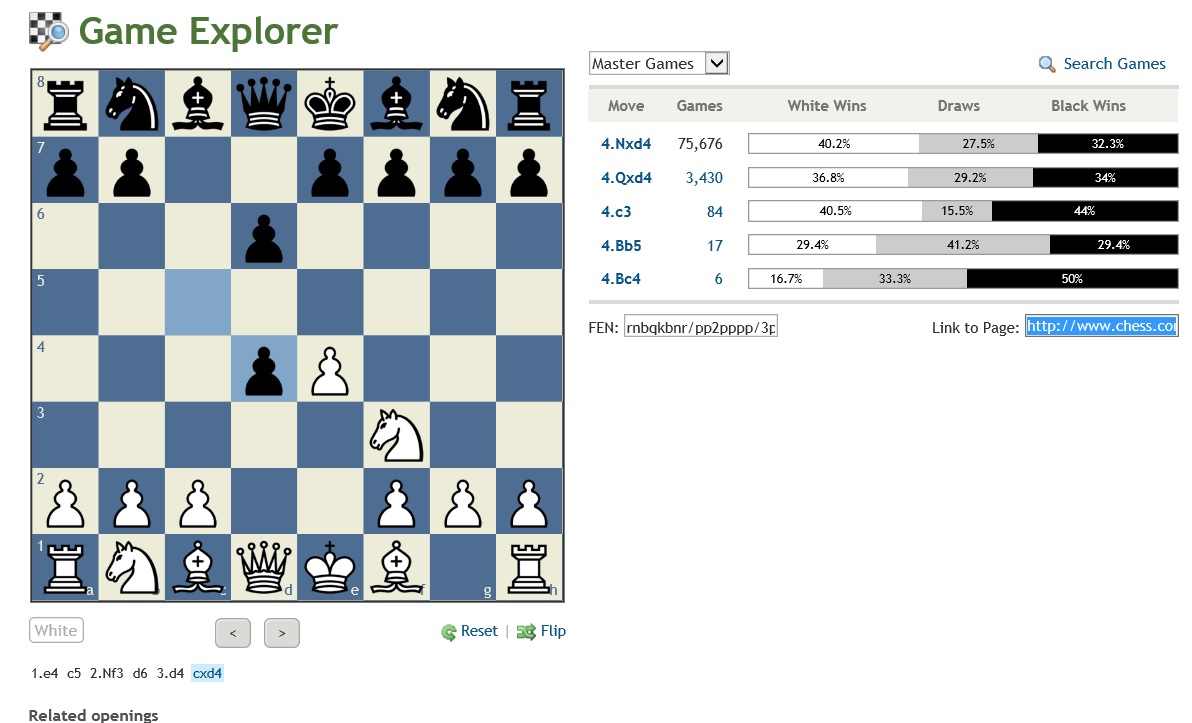
DO YOU REALIZE THAT YOUR TURN BASED OPPONENT CAN LEGALLY PLAY THE WORLD'S BEST CHESS MOVE AGAINST YOU FOR THE ENTIRE OPENING? That as long as you stay in book (which means making a good move), they can choose the most preferred move from the collection of Masters and Grandmasters since the 1800s against

Writing Exploits for Win32 Systems from Scratch

Paste Error Persists When Trying to Do Special-Pas - Esri Community
Highlight, take notes, and search in the book

Art of Software Security Testing, The: Identifying Software Security Flaws: Identifying Software Security Flaws

Q&A: Zero-days attacks – the holy grail of computer hacking

The Web3 Movement's Quest to Build a 'Can't Be Evil' Internet

Dell XPS 27 review: A high-end PC with 4K display and awesome
80% Objects in Space on

Exit Interview: I'm A Crypto-Specialist Working To Secure the Internet

Open Source Insight: GitHub Finds 4M Flaws, IAST Magic Quadrant
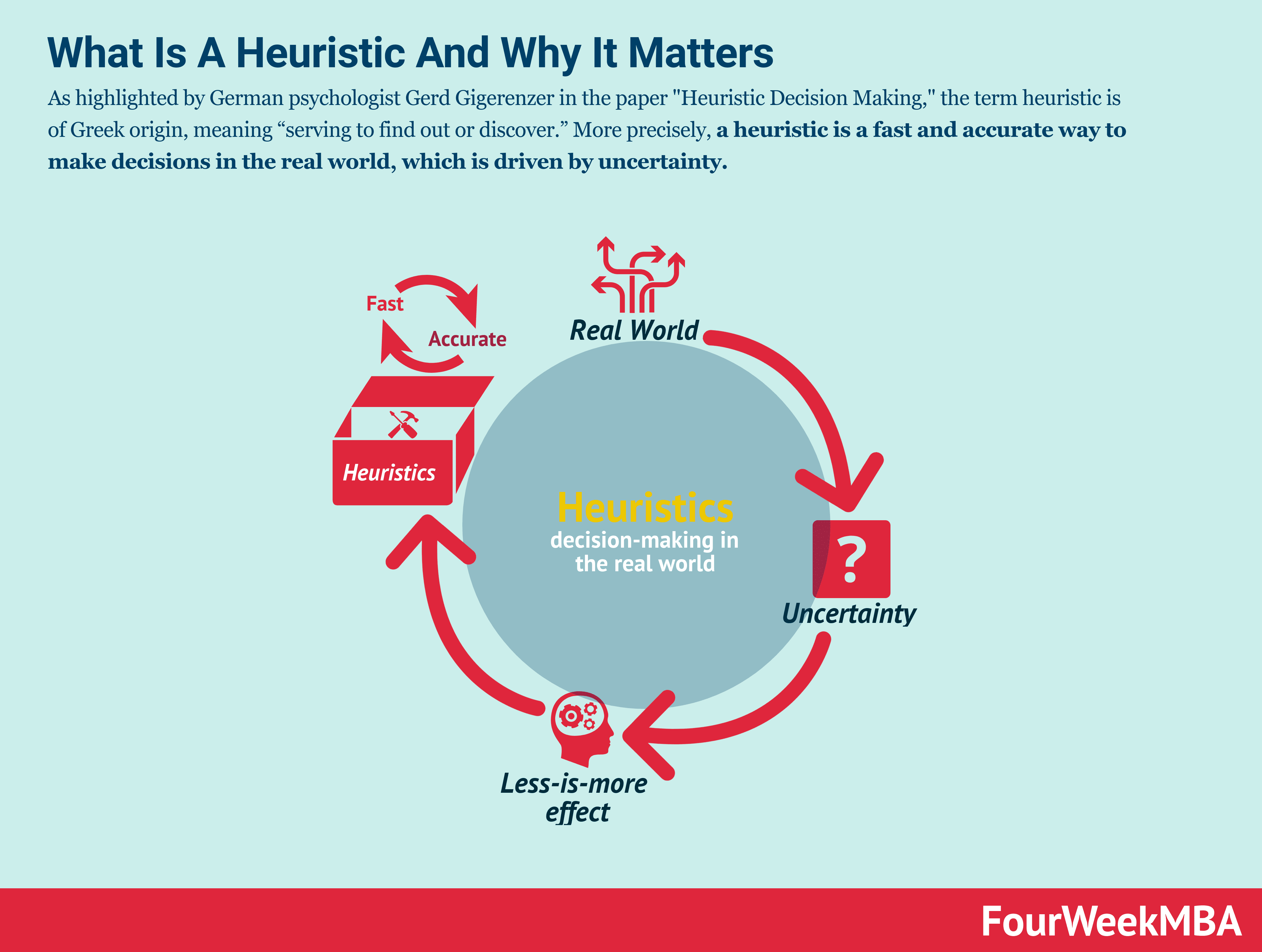
What Is A Heuristic And Why Heuristics Matter In Business
I developed an algorithm capable of finding all the areas that a
The critical flaw of asset browsers, by Robin-Yann Storm

Microsoft: Attackers Exploiting Windows Zero-Day Flaw

Hackers Using Microsoft MSHTML Flaw to Spy on Targeted PCs w
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/22957871/VRG_ILLO_4824_AR_Parallax_3.png)
AR could be a privacy nightmare — or a chance to rethink computing
Recomendado para você
-
 The chess games of Fabiano Caruana21 fevereiro 2025
The chess games of Fabiano Caruana21 fevereiro 2025 -
 Guide to the chess24 Database, Analysis & Coaching21 fevereiro 2025
Guide to the chess24 Database, Analysis & Coaching21 fevereiro 2025 -
 Chess Games Database Online21 fevereiro 2025
Chess Games Database Online21 fevereiro 2025 -
 All 1d6 Opening Repertoire Collection (6 Digital DVDs)21 fevereiro 2025
All 1d6 Opening Repertoire Collection (6 Digital DVDs)21 fevereiro 2025 -
 Corr. (Correspondence ) Database 2024 Chess Database Software Program21 fevereiro 2025
Corr. (Correspondence ) Database 2024 Chess Database Software Program21 fevereiro 2025 -
 Download Chess Database21 fevereiro 2025
Download Chess Database21 fevereiro 2025 -
 How do I look at chess games played by the masters? - Chess.com Member Support and FAQs21 fevereiro 2025
How do I look at chess games played by the masters? - Chess.com Member Support and FAQs21 fevereiro 2025 -
 u/chessvision-ai-bot NEW FEATURE: Games Database Links, white to play : r/ chess21 fevereiro 2025
u/chessvision-ai-bot NEW FEATURE: Games Database Links, white to play : r/ chess21 fevereiro 2025 -
Improve at Chess by Analyzing Your Openings, by Daniel Etzold21 fevereiro 2025
-
 The Rochester Chess Club Game Database21 fevereiro 2025
The Rochester Chess Club Game Database21 fevereiro 2025
você pode gostar
-
/i.s3.glbimg.com/v1/AUTH_59edd422c0c84a879bd37670ae4f538a/internal_photos/bs/2022/H/h/ov4YDwRAi6uCEyQrZb8w/livro-edificia-casa-ditalia.jpg) Livro sobre Edifício Casa D'Italia, no Centro, resgata mais de 90 anos da presença italiana no Rio, Rio de Janeiro21 fevereiro 2025
Livro sobre Edifício Casa D'Italia, no Centro, resgata mais de 90 anos da presença italiana no Rio, Rio de Janeiro21 fevereiro 2025 -
 Jogo Futebol De Mesa Porttil Brinquedo Infantil Adulto - toys21 fevereiro 2025
Jogo Futebol De Mesa Porttil Brinquedo Infantil Adulto - toys21 fevereiro 2025 -
 Carmen Kass Net Worth 2023: Modeling Career Income Age Cars21 fevereiro 2025
Carmen Kass Net Worth 2023: Modeling Career Income Age Cars21 fevereiro 2025 -
 c0nn0r on X: Here's a lot of dark boy anime icons I use, more at the bottom <3 / X21 fevereiro 2025
c0nn0r on X: Here's a lot of dark boy anime icons I use, more at the bottom <3 / X21 fevereiro 2025 -
![[ NEW UPDATE ] EXECUTOR ANDROID DELTA & SCRIPT BLOX](https://i.ytimg.com/vi/PafG_WfideE/maxresdefault.jpg) [ NEW UPDATE ] EXECUTOR ANDROID DELTA & SCRIPT BLOX21 fevereiro 2025
[ NEW UPDATE ] EXECUTOR ANDROID DELTA & SCRIPT BLOX21 fevereiro 2025 -
 Home - Certabo Chess21 fevereiro 2025
Home - Certabo Chess21 fevereiro 2025 -
/cdn.vox-cdn.com/uploads/chorus_asset/file/23963879/FazBkAQXEAUm7ay.jpeg) Sony's PlayStation VR2 headset is coming in early 2023 - The Verge21 fevereiro 2025
Sony's PlayStation VR2 headset is coming in early 2023 - The Verge21 fevereiro 2025 -
![EU VIM VER O MAMACO - BANANA KONG [ANDROID/IOS]](https://i.ytimg.com/vi/YbJZOstDb2E/maxresdefault.jpg) EU VIM VER O MAMACO - BANANA KONG [ANDROID/IOS]21 fevereiro 2025
EU VIM VER O MAMACO - BANANA KONG [ANDROID/IOS]21 fevereiro 2025 -
 GIF files: How to create, edit and open them21 fevereiro 2025
GIF files: How to create, edit and open them21 fevereiro 2025 -
 Zugzwang: A Pivotal Concept in Chess Strategy - PPQTY21 fevereiro 2025
Zugzwang: A Pivotal Concept in Chess Strategy - PPQTY21 fevereiro 2025