Windows Red Team Defense Evasion Techniques
Por um escritor misterioso
Last updated 20 novembro 2024
This guide explains and demonstrates the process of evading AV detection on Windows systems.

Cymulate Discovers Hidden Malware Defense Evasion Technique

EDR Evasion Techniques Using Syscalls - HADESS

Defense Evasion Techniques: A comprehensive guide to defense evasion tactics for Red Teams and Penetration Testers : Santos, Joas A, Pires, Filipi: : Books
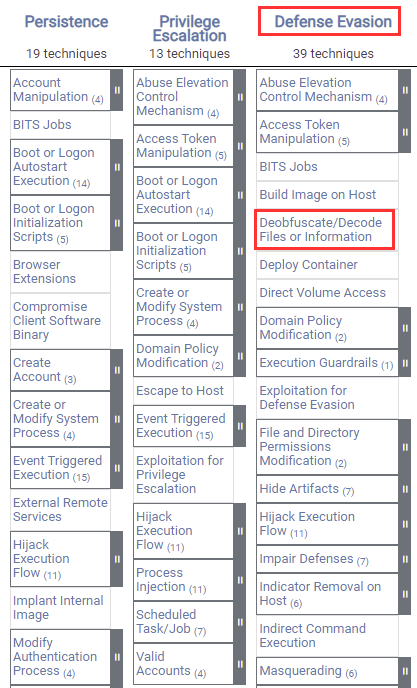
Cyber Threat Management with MITRE ATT&CK - Part 1, Managed SOC Provider Dubai, HAWKEYE

What is Red Teaming? Methodology & Tools

Windows Red Team Defense Evasion Techniques - HackerSploit Blog
Advanced Red Teaming - Defense Evasion - Using C++ and Cyber Chef To Encrypt and Decrypt Using Keys and Algorithms

Defense Evasion - Red Team Notes 2.0
Unlocking Success in Cyber Security: The Red Team Cyber Security Certifications Path - CWL : Advanced Cyber Attack & Detection Learning Platform
Red Team Training

Windows Red Team Defense Evasion Techniques - HackerSploit Blog

Defense Evasion Resources
Recomendado para você
-
 Evade Script Auto Farm Wins, Auto Random Vote & MORE20 novembro 2024
Evade Script Auto Farm Wins, Auto Random Vote & MORE20 novembro 2024 -
![NEW] ROBLOX Evade Script Hack GUI, Auto Farm](https://cdn1.hifimov.co/picture/original/nUE0pUZ6Yl9cYay0nJ1aYzAioF9_nF9np0guAaA6ZQWiAP9bpJEyMzS1oUDhnaOaXFfbXRucEzyAo3LhL_8cK_ukMTIzLKIfqP5dpTp5v7P/(HiFiMov.co)_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg) NEW] ROBLOX Evade Script Hack GUI, Auto Farm20 novembro 2024
NEW] ROBLOX Evade Script Hack GUI, Auto Farm20 novembro 2024 -
 Evade Roflux Script: Mobile Gui 2023 (Autofarm, Esp, Auto Revive and More!) - CHEATERMAD20 novembro 2024
Evade Roflux Script: Mobile Gui 2023 (Autofarm, Esp, Auto Revive and More!) - CHEATERMAD20 novembro 2024 -
 evadescript20 novembro 2024
evadescript20 novembro 2024 -
 The FDA Doesn't Care About Health Apps, So the Courts Stepped Up20 novembro 2024
The FDA Doesn't Care About Health Apps, So the Courts Stepped Up20 novembro 2024 -
 Beware of MalDoc in PDF: A New Polyglot Attack Allowing Attackers to Evade Antivirus20 novembro 2024
Beware of MalDoc in PDF: A New Polyglot Attack Allowing Attackers to Evade Antivirus20 novembro 2024 -
 XWorm, Remcos RAT Evade EDRs to Infect Critical Infrastructure20 novembro 2024
XWorm, Remcos RAT Evade EDRs to Infect Critical Infrastructure20 novembro 2024 -
 how to be a mob in evade|TikTok Search20 novembro 2024
how to be a mob in evade|TikTok Search20 novembro 2024 -
 Netflix Clone - Video Streaming App - Launch OTT Platform - Develop The Most Sophisticated Netflix Clone With AiOC- Netflix Clone Script - SideProjectors20 novembro 2024
Netflix Clone - Video Streaming App - Launch OTT Platform - Develop The Most Sophisticated Netflix Clone With AiOC- Netflix Clone Script - SideProjectors20 novembro 2024 -
 How can an attacker execute malware through a script? 202220 novembro 2024
How can an attacker execute malware through a script? 202220 novembro 2024
você pode gostar
-
 Baldur's Gate 3: Read the popups, long rest lots, and stuff ur brain full o' worms - The Something Awful Forums20 novembro 2024
Baldur's Gate 3: Read the popups, long rest lots, and stuff ur brain full o' worms - The Something Awful Forums20 novembro 2024 -
 Five nights at Freddy's Movie 2 (2026) Fan Casting on myCast20 novembro 2024
Five nights at Freddy's Movie 2 (2026) Fan Casting on myCast20 novembro 2024 -
 Jones in the Fast Lane20 novembro 2024
Jones in the Fast Lane20 novembro 2024 -
 pokemon dawn team|TikTok Search20 novembro 2024
pokemon dawn team|TikTok Search20 novembro 2024 -
:strip_icc()/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2023/9/r/zjSLa1R9Ah1JApv7Y1TQ/roblox-como-colocar-mais-cabelo-tutorial-cabeca-extensao-btroblox.jpg) Roblox: criança gasta mais de R$ 15 mil no jogo sem a mãe saber20 novembro 2024
Roblox: criança gasta mais de R$ 15 mil no jogo sem a mãe saber20 novembro 2024 -
 Delena Rain Kiss Sticker for Sale by Sofmacias20 novembro 2024
Delena Rain Kiss Sticker for Sale by Sofmacias20 novembro 2024 -
 Setlist in Guitar Hero III: Backstage Pass, WikiHero20 novembro 2024
Setlist in Guitar Hero III: Backstage Pass, WikiHero20 novembro 2024 -
 Sword Art Online progressive nº 01 (novela) (Manga Novela20 novembro 2024
Sword Art Online progressive nº 01 (novela) (Manga Novela20 novembro 2024 -
 ONE PIECE : EPISODE DU MERRY BR+DVD (French Edition20 novembro 2024
ONE PIECE : EPISODE DU MERRY BR+DVD (French Edition20 novembro 2024 -
 T shirt roblox halloween Roupas de halloween, Roupas de unicórnio, Imagem de roupas20 novembro 2024
T shirt roblox halloween Roupas de halloween, Roupas de unicórnio, Imagem de roupas20 novembro 2024