Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download
Por um escritor misterioso
Last updated 22 fevereiro 2025
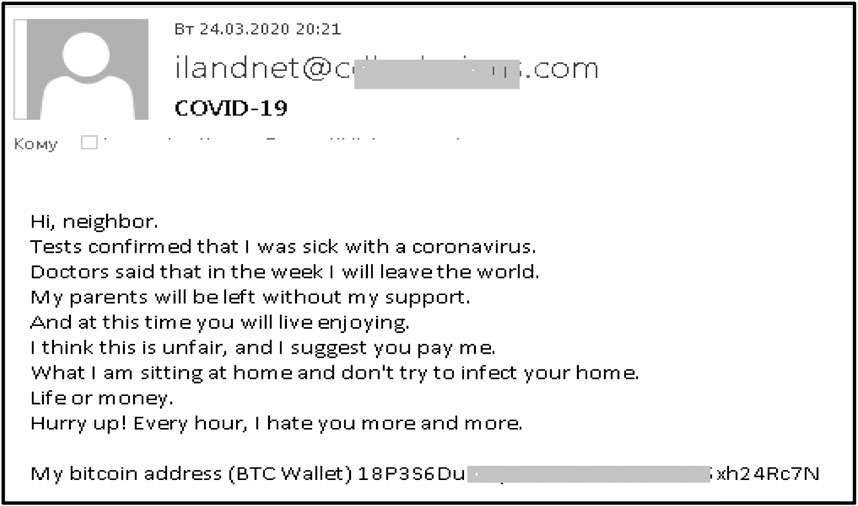
Phishing utilizing social engineering Induces the recipient to reveal desired personal information Bank account SSN Address Etc. Sometimes entices the recipient to go to a malicious web site
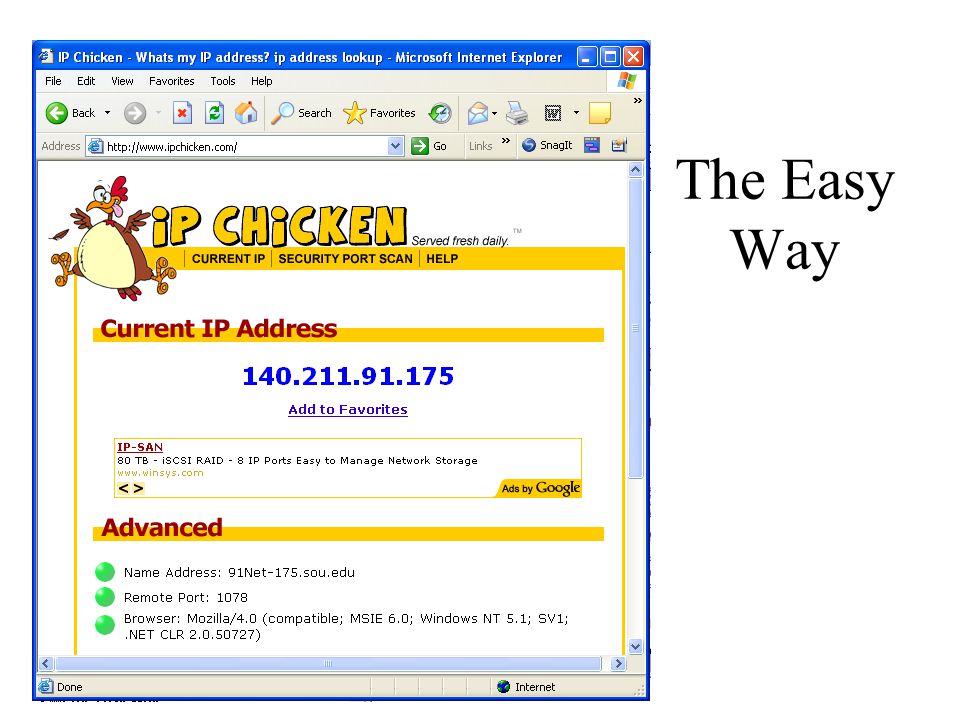
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the

Role of MX Records in Email Forensics Investigation

What Is Domain Name System (DNS)?
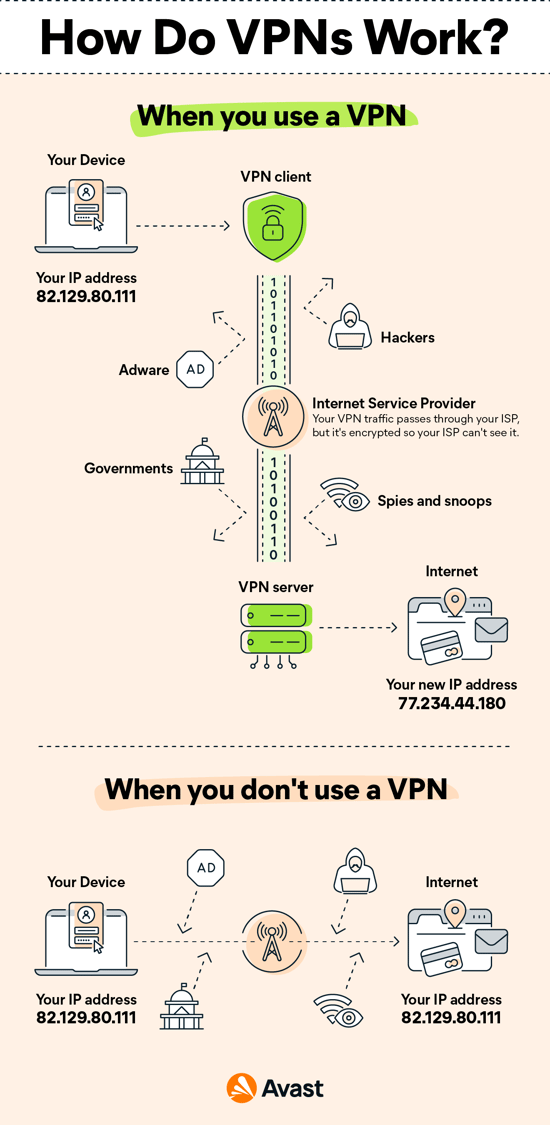
VPN Meaning: What Is a VPN & What Does It Do?

How to Detect Data Exfiltration (Before It's Too Late)

Computer Forensics 252 Tracing Thomas Schwarz, S.J ppt download
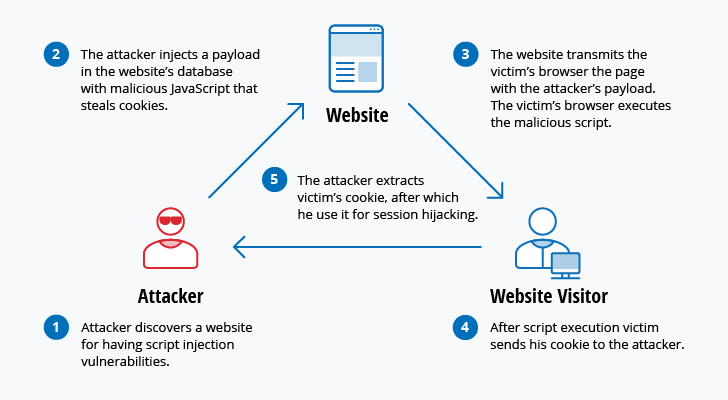
The 12 Most Common Types of Cybersecurity Attacks Today

Behavior‐based botnet detection in parallel - Wang - 2014

6 Common Phishing Attacks and How to Protect Against Them
Frontiers Phishing Attacks: A Recent Comprehensive Study and a

URL Definition, Parts & Examples - Video & Lesson Transcript

PPT - Spam, Phishing & Trojans PowerPoint Presentation, free
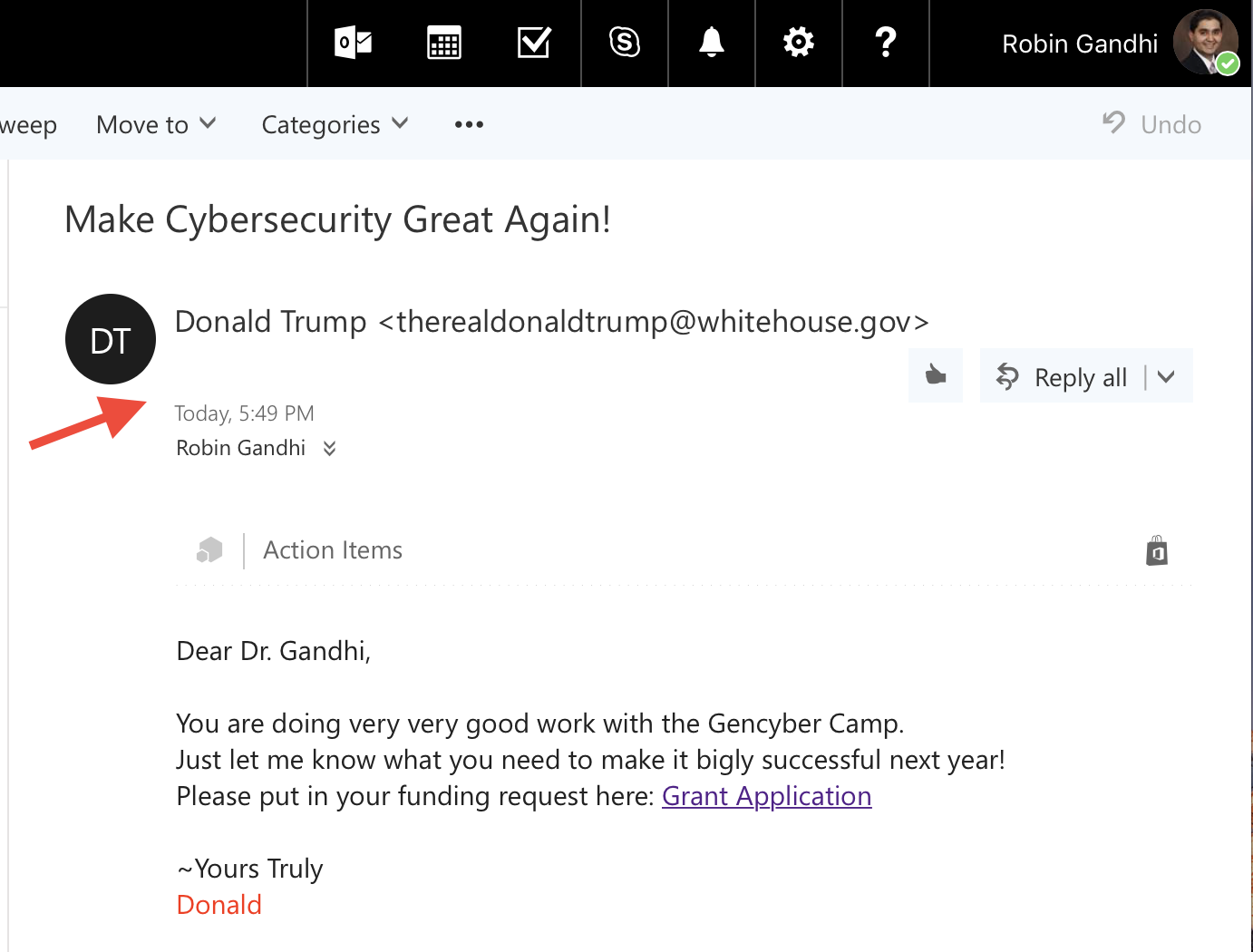
Phishing - Email Header Analysis · nebraska-gencyber-modules
Recomendado para você
-
 Away Viewing Fix - Dynamic URL Change, WiFi Baby, Compare Baby Monitors 201922 fevereiro 2025
Away Viewing Fix - Dynamic URL Change, WiFi Baby, Compare Baby Monitors 201922 fevereiro 2025 -
 Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community22 fevereiro 2025
Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community22 fevereiro 2025 -
 Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey22 fevereiro 2025
Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey22 fevereiro 2025 -
 VyprVPN Review - Secure Personal VPN Service Review22 fevereiro 2025
VyprVPN Review - Secure Personal VPN Service Review22 fevereiro 2025 -
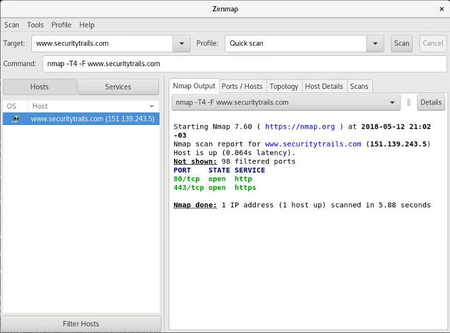 Top 5 Most Popular Port Scanners in CyberSecurity22 fevereiro 2025
Top 5 Most Popular Port Scanners in CyberSecurity22 fevereiro 2025 -
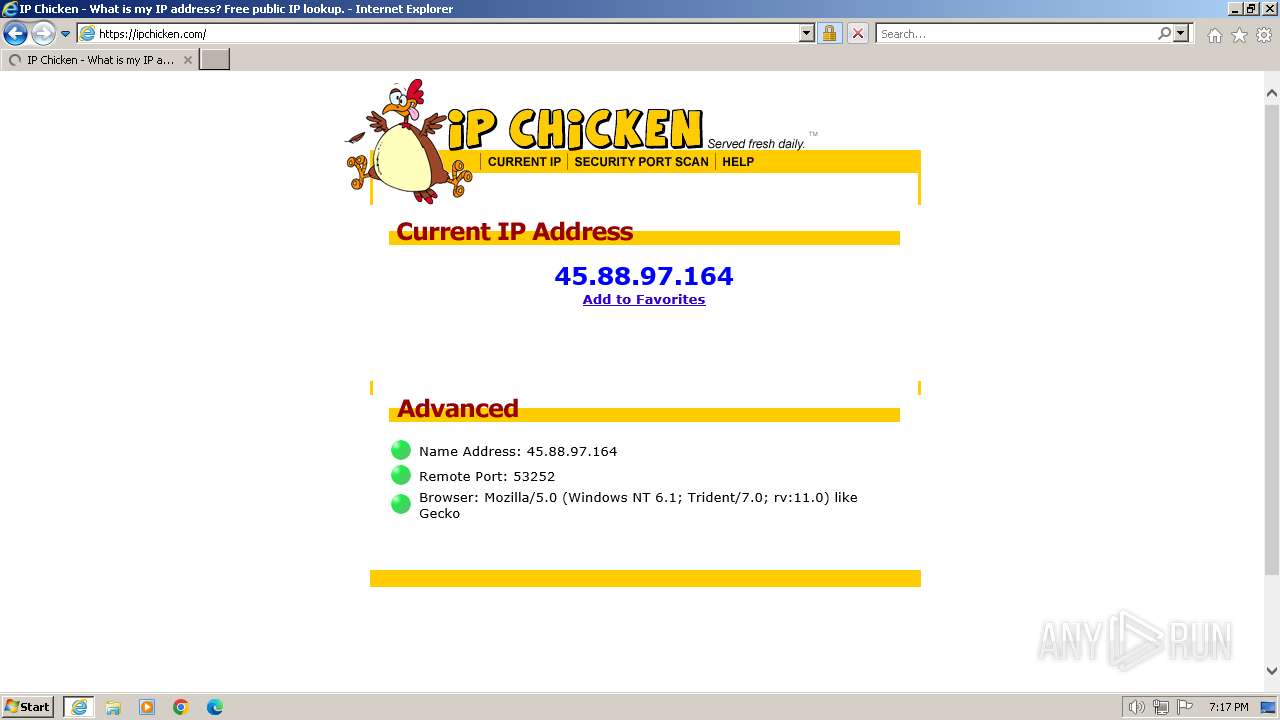 Malware analysis Malicious activity22 fevereiro 2025
Malware analysis Malicious activity22 fevereiro 2025 -
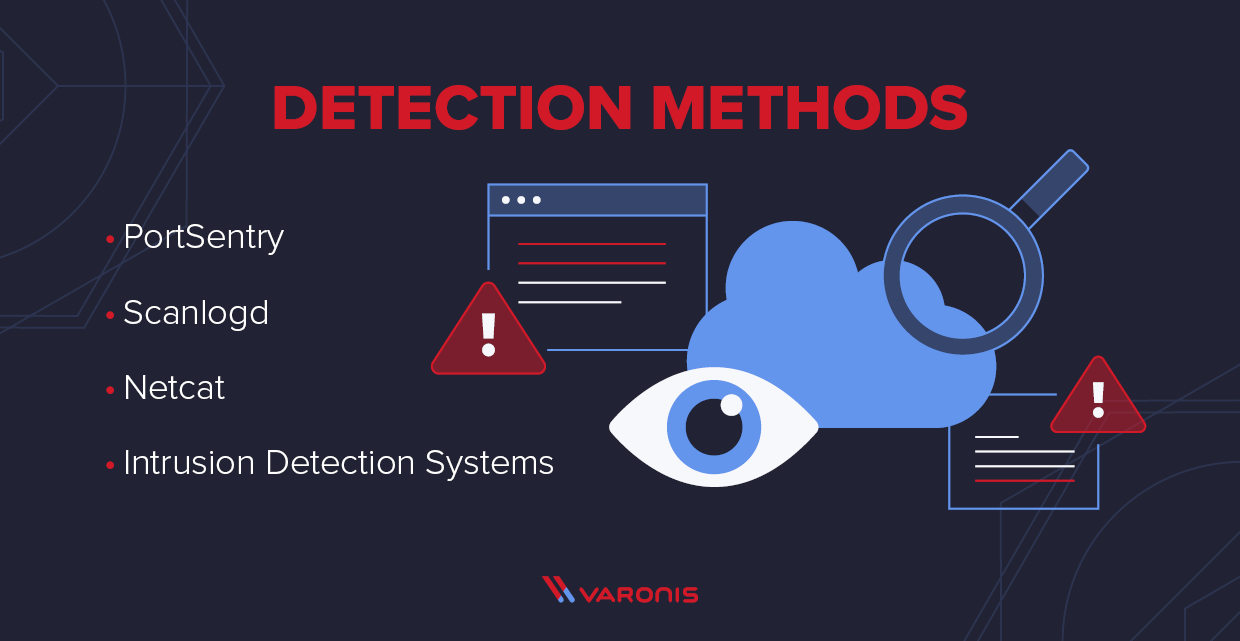 What is a Port Scanner and How Does it Work?22 fevereiro 2025
What is a Port Scanner and How Does it Work?22 fevereiro 2025 -
Help Center22 fevereiro 2025
-
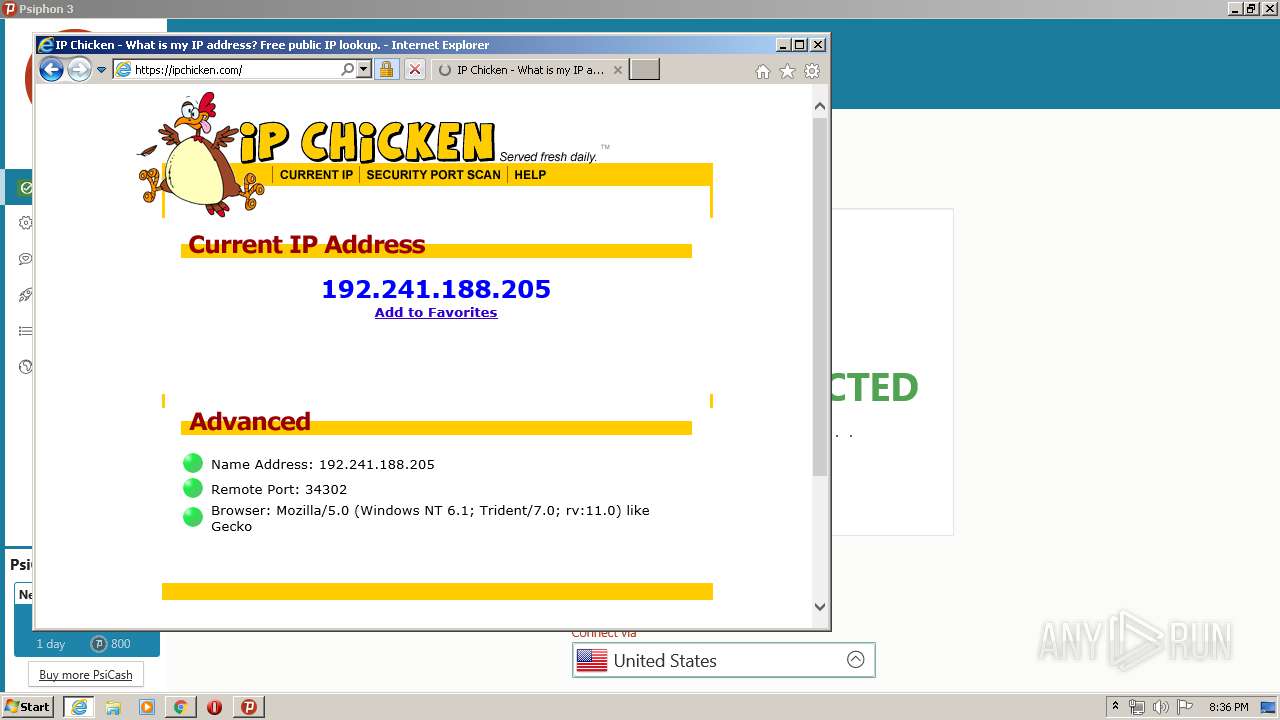 Malware analysis Malicious activity22 fevereiro 2025
Malware analysis Malicious activity22 fevereiro 2025 -
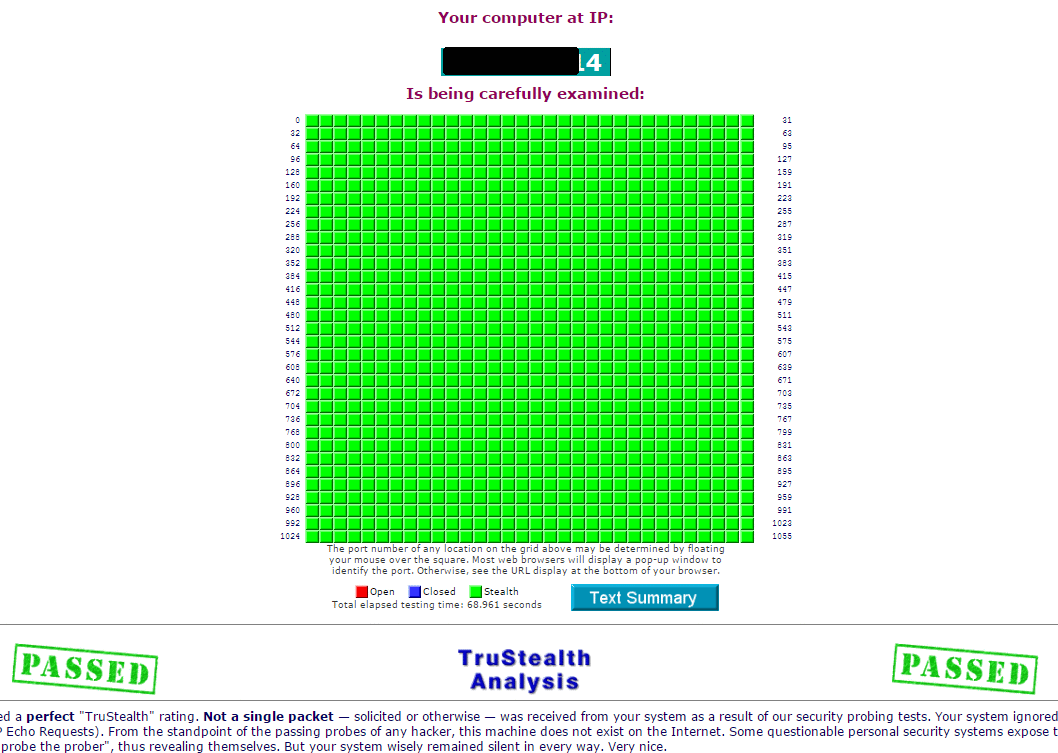 Test Your Router22 fevereiro 2025
Test Your Router22 fevereiro 2025
você pode gostar
-
 I'm only a fool fy🫵 - video template by CapCut22 fevereiro 2025
I'm only a fool fy🫵 - video template by CapCut22 fevereiro 2025 -
Solitaire-online: Klondike Community22 fevereiro 2025
-
 Download do APK de Crazy Scary Teacher 2020 : Scary Ghost Games22 fevereiro 2025
Download do APK de Crazy Scary Teacher 2020 : Scary Ghost Games22 fevereiro 2025 -
Creed - My Sacrifice on Vimeo22 fevereiro 2025
-
 Arquivos Boku No Hero - Otageek22 fevereiro 2025
Arquivos Boku No Hero - Otageek22 fevereiro 2025 -
 Episode 23 - Beyblade Metal Fusion, FULL EPISODE22 fevereiro 2025
Episode 23 - Beyblade Metal Fusion, FULL EPISODE22 fevereiro 2025 -
 ArtStation - Cyberpunk City Landscape22 fevereiro 2025
ArtStation - Cyberpunk City Landscape22 fevereiro 2025 -
 O quão fã você é de Minecraft?22 fevereiro 2025
O quão fã você é de Minecraft?22 fevereiro 2025 -
/i.s3.glbimg.com/v1/AUTH_51f0194726ca4cae994c33379977582d/internal_photos/bs/2023/8/8/LXEdZLQCGnAvFCZCp9Mg/virginia-2.webp) Virgínia Fonseca é criticada por ostentar carro de luxo enquanto faz parcerias com jogos de azar22 fevereiro 2025
Virgínia Fonseca é criticada por ostentar carro de luxo enquanto faz parcerias com jogos de azar22 fevereiro 2025 -
 Yofukashi no Uta Anime Poster for Sale by roxannewhith22 fevereiro 2025
Yofukashi no Uta Anime Poster for Sale by roxannewhith22 fevereiro 2025
