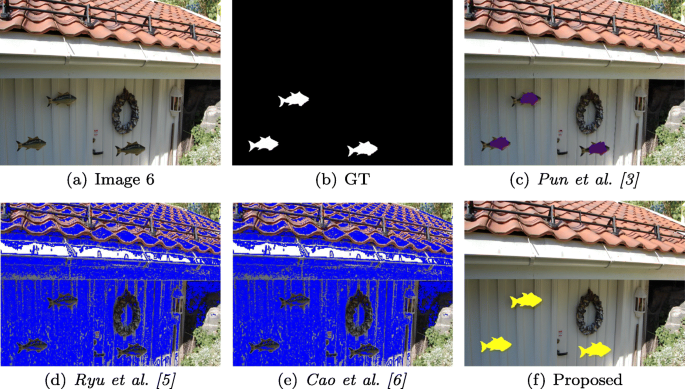
a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Last updated 07 março 2025


Copy-move forgery detection using binary discriminant features - ScienceDirect
GitHub - niyishakapatrick/Copy-move-forgery-detection-using-image-blobs-BRISK-features.: One of the most frequently used types of digital image forgery is copying one area in the image and pasting it into another area of the same image. This

Example for copy-move forgery from [MS07] (original image left

Robust dense‐field based copy‐move forgery localization using generic radial harmonic Fourier moment invariants - Atallah - Journal of Forensic Sciences - Wiley Online Library

Copy-move image forgery detection based on evolving circular domains coverage

Copy Move Image Forgery, PDF, Accuracy And Precision
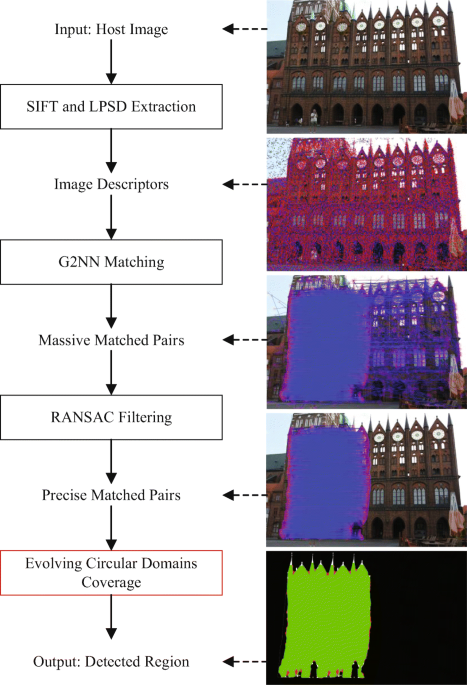
Copy-move image forgery detection based on evolving circular domains coverage
FAST, BRIEF and SIFT based image copy-move forgery detection technique
PDF) Fast and Effective Image Copy-Move Forgery Detection via Hierarchical Feature Point Matching

Utilization of edge operators for localization of copy-move image forgery using WLD-HOG features with connected component labeling

Solved Exercise 3. Let b1 = (1,1,0,1), b2 = (-1,3,1, -2), b3
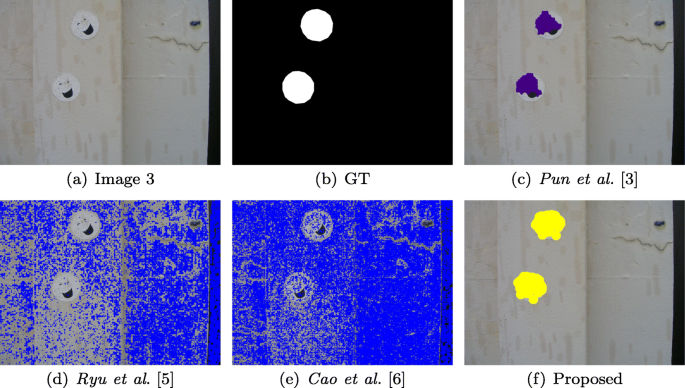
FAST, BRIEF and SIFT based image copy-move forgery detection technique

A new Copy-Move forgery detection method using LIOP - ScienceDirect

Copy-move forgery detection using binary discriminant features - ScienceDirect
Recomendado para você
-
 20mm F1/2 G1/2 Thread 2M Long Stainless Steel Handheld Shower Hose Pipe - Silver Tone - On Sale - Bed Bath & Beyond - 3580865607 março 2025
20mm F1/2 G1/2 Thread 2M Long Stainless Steel Handheld Shower Hose Pipe - Silver Tone - On Sale - Bed Bath & Beyond - 3580865607 março 2025 -
 Genera G1 and F1 3D printing system - UK supplier Laser Lines07 março 2025
Genera G1 and F1 3D printing system - UK supplier Laser Lines07 março 2025 -
 Slapdash Powermaster 1988 Vintage G1 Transformers Formula-1 Action Figure - Wheeljack's Lab07 março 2025
Slapdash Powermaster 1988 Vintage G1 Transformers Formula-1 Action Figure - Wheeljack's Lab07 março 2025 -
 G1 - 'F1 2015' é estreia da Fórmula 1 no PlayStation 4 e Xbox One - notícias em Games07 março 2025
G1 - 'F1 2015' é estreia da Fórmula 1 no PlayStation 4 e Xbox One - notícias em Games07 março 2025 -
 XRT136 Replace Remote Control fit for VIZIO Smart TV D50x-G9 D65x-G4 D55x-G1 D40f-G9 D43f-F1 D70-F3 V505-G9 D32h-F1 D24h-G9 E70-F3 D43-F1 V705-G307 março 2025
XRT136 Replace Remote Control fit for VIZIO Smart TV D50x-G9 D65x-G4 D55x-G1 D40f-G9 D43f-F1 D70-F3 V505-G9 D32h-F1 D24h-G9 E70-F3 D43-F1 V705-G307 março 2025 -
 NIU F1 Electric Vehicle Battery F2 GOVA G1 G2 Refitted Straight-on Large-capacity 48V Lithium Battery - AliExpress07 março 2025
NIU F1 Electric Vehicle Battery F2 GOVA G1 G2 Refitted Straight-on Large-capacity 48V Lithium Battery - AliExpress07 março 2025 -
 Transformation G1 Element TE03 TE-03 Version 2.0 MP F1 Mirage Action Figure In Stock With Box Sticker IN STOCK07 março 2025
Transformation G1 Element TE03 TE-03 Version 2.0 MP F1 Mirage Action Figure In Stock With Box Sticker IN STOCK07 março 2025 -
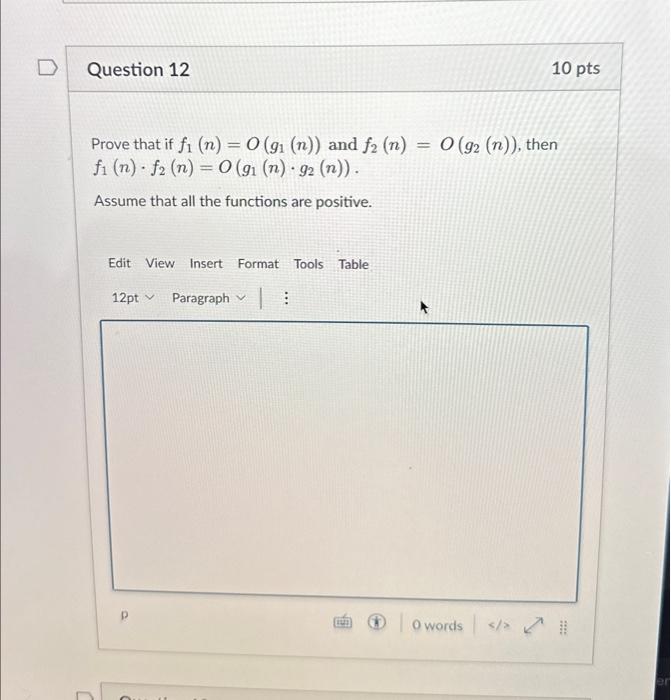
Solved Prove that if f1(n)=O(g1(n)) and f2(n)=O(g2(n)), then07 março 2025
-
G1 (@G1Official) / X07 março 2025
-
 F1 Miami Parking Guide: Official Pass & Unofficial Parking Lots07 março 2025
F1 Miami Parking Guide: Official Pass & Unofficial Parking Lots07 março 2025
você pode gostar
-
 Assistir Kanojo, Okarishimasu 2° Temporada - Episódio 10 Online - Download & Assistir Online! - AnimesTC07 março 2025
Assistir Kanojo, Okarishimasu 2° Temporada - Episódio 10 Online - Download & Assistir Online! - AnimesTC07 março 2025 -
 PAPAS DA LINGUA - EU SEI (INSTRUMENTAL PIANO) by anirak07 março 2025
PAPAS DA LINGUA - EU SEI (INSTRUMENTAL PIANO) by anirak07 março 2025 -
 Haze Piece Trello Link & Wiki (December 2023) - Try Hard Guides07 março 2025
Haze Piece Trello Link & Wiki (December 2023) - Try Hard Guides07 março 2025 -
 Ver Peter Grill and the Philosopher's Time - Super Extra - Super Extra (Season 2)07 março 2025
Ver Peter Grill and the Philosopher's Time - Super Extra - Super Extra (Season 2)07 março 2025 -
 Educação escolar em casa, desenvolvimento infantil na era digital07 março 2025
Educação escolar em casa, desenvolvimento infantil na era digital07 março 2025 -
 Gear icon symbol sign Symbols, Vector art, Gears07 março 2025
Gear icon symbol sign Symbols, Vector art, Gears07 março 2025 -
 id de skins emo07 março 2025
id de skins emo07 março 2025 -
Freckles Studios Schwäbisch Hall07 março 2025
-
Project Car Brazil07 março 2025
-
 Dragon Inferno 2 Player Puzzle Game - SmartGames - Steam Rocket07 março 2025
Dragon Inferno 2 Player Puzzle Game - SmartGames - Steam Rocket07 março 2025