Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 18 janeiro 2025

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called
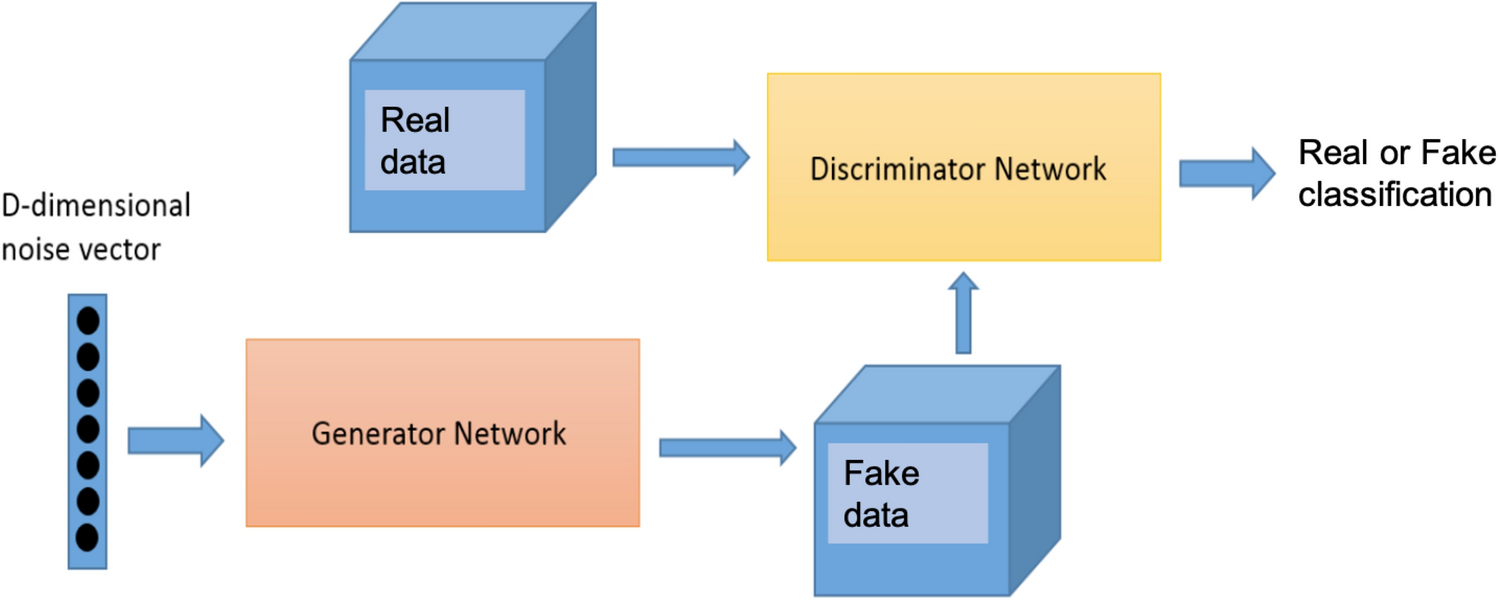
Synthetic flow-based cryptomining attack generation through

Other 3,700 MikroTik Routers compromised in cryptoJacking campaigns

The Anomali Blog
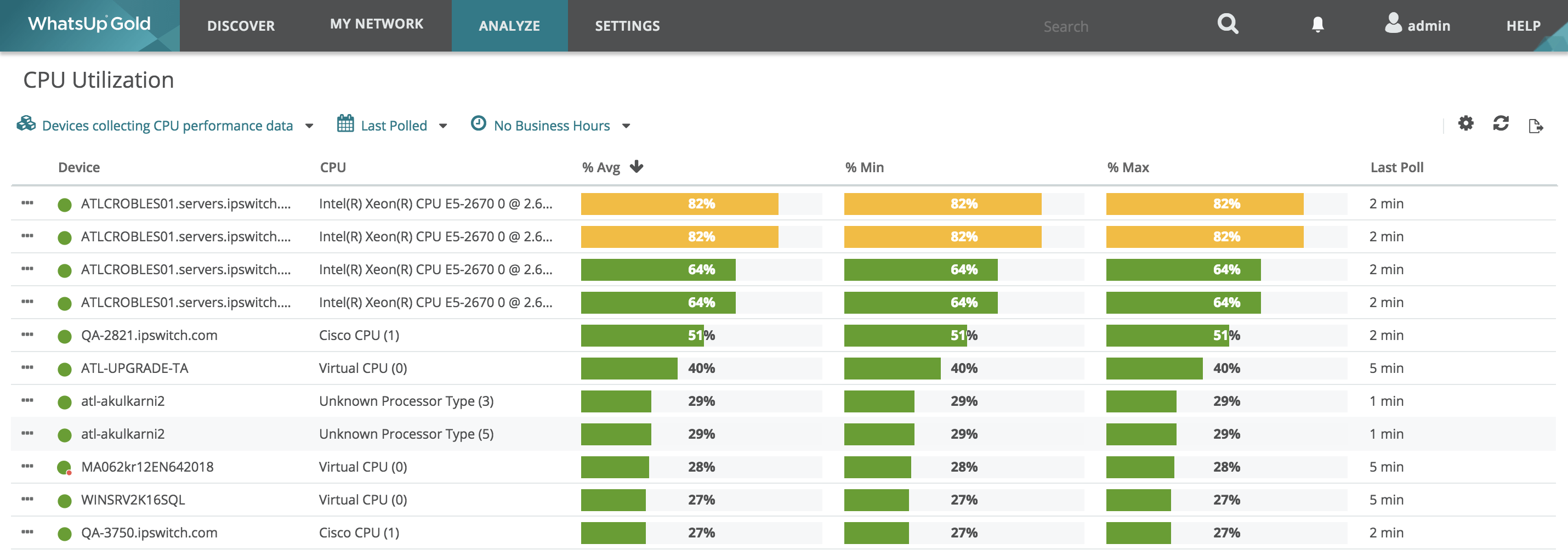
How to Detect and Stop Cryptomining on Your Network

The concept of cryptojacking and how it works?

PacNOG 23: Introduction to Crypto Jacking

Defeat Cryptojacking with Decryption and Inspection

Cryptojacking
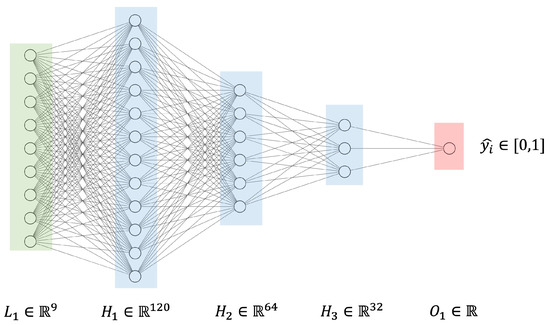
Applied Sciences, Free Full-Text

cisco Archives - STL Partners

Austreme Discovers Crypto-jacking Software in Merchant Sites
Recomendado para você
-
 Anti-Coinminer Mining Campaign18 janeiro 2025
Anti-Coinminer Mining Campaign18 janeiro 2025 -
 Ad blocker with miner included18 janeiro 2025
Ad blocker with miner included18 janeiro 2025 -
 Is your web browser secretly mining cryptocurrency?18 janeiro 2025
Is your web browser secretly mining cryptocurrency?18 janeiro 2025 -
 Virus Bulletin on X: 'Coin miner blocker' offered on dodgy website contains a coin miner / X18 janeiro 2025
Virus Bulletin on X: 'Coin miner blocker' offered on dodgy website contains a coin miner / X18 janeiro 2025 -
 Line of Duty: Yes eBook : Blocker MD, Virginia Irvine, Wooten Ph.D.., Heather G.: Kindle Store18 janeiro 2025
Line of Duty: Yes eBook : Blocker MD, Virginia Irvine, Wooten Ph.D.., Heather G.: Kindle Store18 janeiro 2025 -
 Miner blockers excited about potential record18 janeiro 2025
Miner blockers excited about potential record18 janeiro 2025 -
 Block Rewards vs. Transaction Fees - Why We Need Both18 janeiro 2025
Block Rewards vs. Transaction Fees - Why We Need Both18 janeiro 2025 -
 AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock18 janeiro 2025
AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock18 janeiro 2025 -
 The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost18 janeiro 2025
The Pirate Bay miner: Here's how to keep cryptocurrency miners away from using your CPU processing power-Tech News , Firstpost18 janeiro 2025 -
 Unknown, Accents, Door Window Draft Stopper Blocker 35 Inches Plush Old Codger Miner Cowboy18 janeiro 2025
Unknown, Accents, Door Window Draft Stopper Blocker 35 Inches Plush Old Codger Miner Cowboy18 janeiro 2025
você pode gostar
-
 Motors - How to Sell a Vehicle - Describe the Vehicle18 janeiro 2025
Motors - How to Sell a Vehicle - Describe the Vehicle18 janeiro 2025 -
 Como ter a Pokédex completa em Pokémon Let's Go – Tecnoblog18 janeiro 2025
Como ter a Pokédex completa em Pokémon Let's Go – Tecnoblog18 janeiro 2025 -
 Improved Chess Rating Comparisons Using Nonparametric Statistics18 janeiro 2025
Improved Chess Rating Comparisons Using Nonparametric Statistics18 janeiro 2025 -
 Cara Fêmea Edições Que Afetam Meninas Princesa E Reflexão Da Menina No Espelho Coroa Da Joia Do Desgaste De Mulher No Espelho Bel Foto de Stock - Imagem de princesa, coroa: 11741502018 janeiro 2025
Cara Fêmea Edições Que Afetam Meninas Princesa E Reflexão Da Menina No Espelho Coroa Da Joia Do Desgaste De Mulher No Espelho Bel Foto de Stock - Imagem de princesa, coroa: 11741502018 janeiro 2025 -
 No Game No Life (No Game, No Life)18 janeiro 2025
No Game No Life (No Game, No Life)18 janeiro 2025 -
 The Proceedings of the Grand Lodge of North Carolina18 janeiro 2025
The Proceedings of the Grand Lodge of North Carolina18 janeiro 2025 -
 Samsung Phone18 janeiro 2025
Samsung Phone18 janeiro 2025 -
 Toxicity T-Shirt – System of a Down18 janeiro 2025
Toxicity T-Shirt – System of a Down18 janeiro 2025 -
 HD wallpaper: code geass cc anime 1920x1080 Anime Code Geass HD Art, C.C.18 janeiro 2025
HD wallpaper: code geass cc anime 1920x1080 Anime Code Geass HD Art, C.C.18 janeiro 2025 -
 🔴 VISH VAI DAR RUIM! KAWAKI COMEÇOU A BAGUNCINHA! - BORUTO 289: O QUE ESPERAR DO EPISÓDIO?18 janeiro 2025
🔴 VISH VAI DAR RUIM! KAWAKI COMEÇOU A BAGUNCINHA! - BORUTO 289: O QUE ESPERAR DO EPISÓDIO?18 janeiro 2025