Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 22 fevereiro 2025

Describing activities of a crime group attacking Ukraine.

A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak
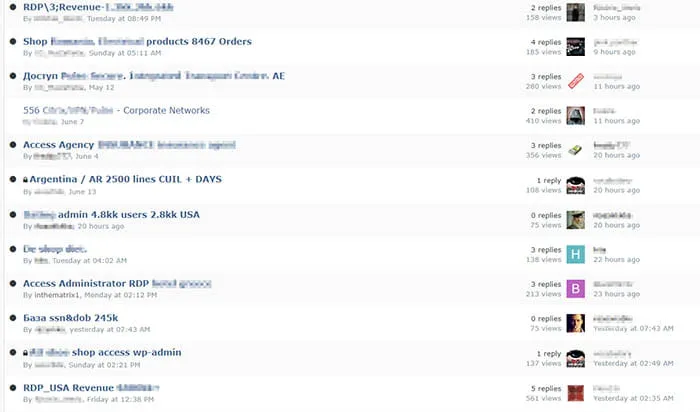
Initial Access Brokers Fueling Ransomware
A Guide to Demystifying Cloud Security SLAs

Google: Former Conti ransomware members attacking Ukraine

US6968571B2 - Secure customer interface for web based data management - Google Patents

FBI, CISA and HHS warns of Royal ransomware gang attacks
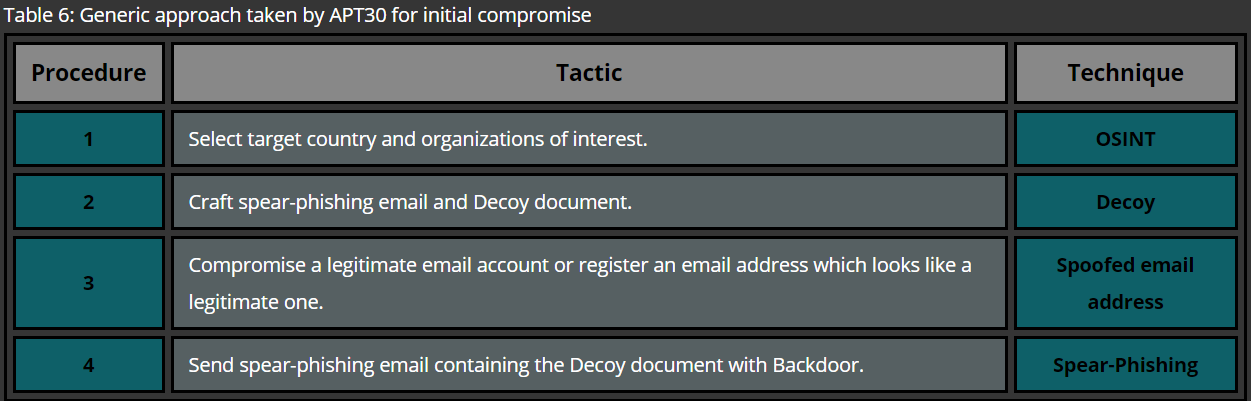
Initial Compromise
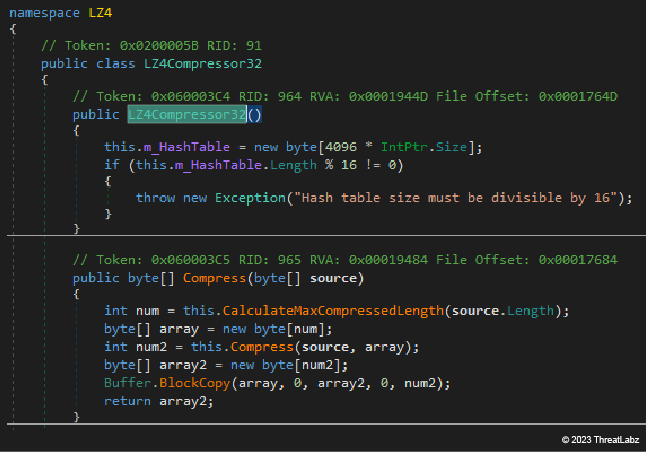
JanelaRAT ThreatLabz Zscaler Blog
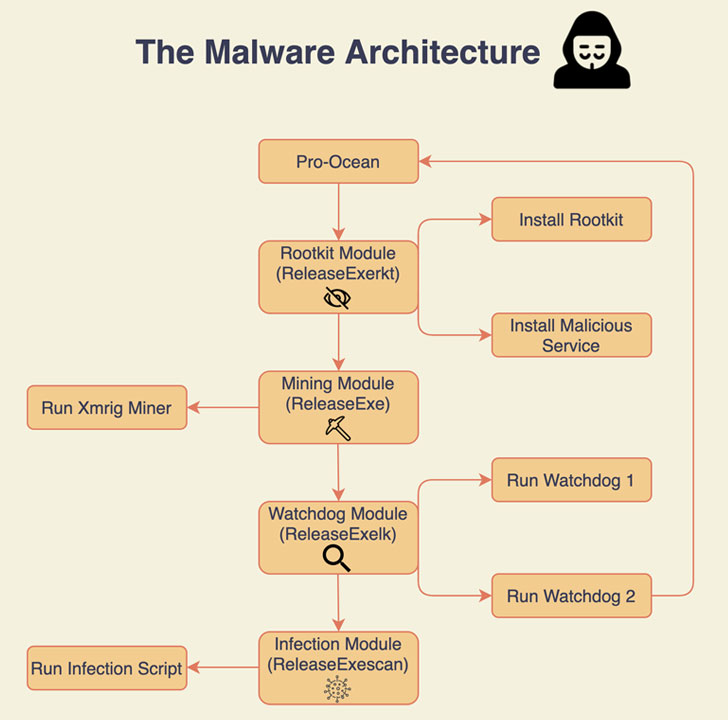
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database

Typical steps of APT attack Download Scientific Diagram
Recomendado para você
-
 Menlo Park - Analysis Group22 fevereiro 2025
Menlo Park - Analysis Group22 fevereiro 2025 -
 Analysis Group New York22 fevereiro 2025
Analysis Group New York22 fevereiro 2025 -
 Analysis Group Office Renovation and Restack22 fevereiro 2025
Analysis Group Office Renovation and Restack22 fevereiro 2025 -
 Careers - Analysis Group22 fevereiro 2025
Careers - Analysis Group22 fevereiro 2025 -
 Analysis Group22 fevereiro 2025
Analysis Group22 fevereiro 2025 -
 IAG Strategic Imaging for Accelerated Drug Development22 fevereiro 2025
IAG Strategic Imaging for Accelerated Drug Development22 fevereiro 2025 -
 Joint Pharmaceutical Analysis Group (joint with RPS)22 fevereiro 2025
Joint Pharmaceutical Analysis Group (joint with RPS)22 fevereiro 2025 -
 Protein Analysis Group – University of Copenhagen22 fevereiro 2025
Protein Analysis Group – University of Copenhagen22 fevereiro 2025 -
 Home - AMAG Inc.22 fevereiro 2025
Home - AMAG Inc.22 fevereiro 2025 -
 Hydraulic Analysis Limited Surge Analysis & Flow Assurance Experts22 fevereiro 2025
Hydraulic Analysis Limited Surge Analysis & Flow Assurance Experts22 fevereiro 2025
você pode gostar
-
 Universe 6, Dragon Ball Multiverse Wiki22 fevereiro 2025
Universe 6, Dragon Ball Multiverse Wiki22 fevereiro 2025 -
Animes online22 fevereiro 2025
-
 Blox Fruit Account Lv:2450Max Full Gear Awaken Ghoul Race V422 fevereiro 2025
Blox Fruit Account Lv:2450Max Full Gear Awaken Ghoul Race V422 fevereiro 2025 -
 Xadrez eletrônico jogo de xadrez jogo de ensino único jogador xadrez sem bateria transmissão de voz22 fevereiro 2025
Xadrez eletrônico jogo de xadrez jogo de ensino único jogador xadrez sem bateria transmissão de voz22 fevereiro 2025 -
 Project Drift 2.0 Apk Mod Dinheiro Infinito Versão 10122 fevereiro 2025
Project Drift 2.0 Apk Mod Dinheiro Infinito Versão 10122 fevereiro 2025 -
Custom Roblox EmojiFonts [Roblox] [Mods]22 fevereiro 2025
-
 HD wallpaper: anime character illustration, tenjou tenge, natsume maya, girl22 fevereiro 2025
HD wallpaper: anime character illustration, tenjou tenge, natsume maya, girl22 fevereiro 2025 -
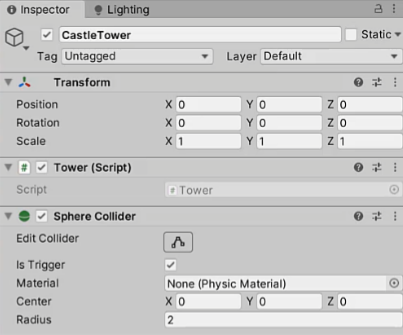 A Guide To Adding Towers For Tower Defense Games In Unity - GameDev Academy22 fevereiro 2025
A Guide To Adding Towers For Tower Defense Games In Unity - GameDev Academy22 fevereiro 2025 -
heion-sedai-no-idaten-tachi-manga, Free Reading22 fevereiro 2025
-
stop posting about baller roblox song id|TikTok Search22 fevereiro 2025


