window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Last updated 19 dezembro 2024
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
Security: window.open(url, name) is vulnerable to XSS with name collision · Issue #1509 · whatwg/html · GitHub
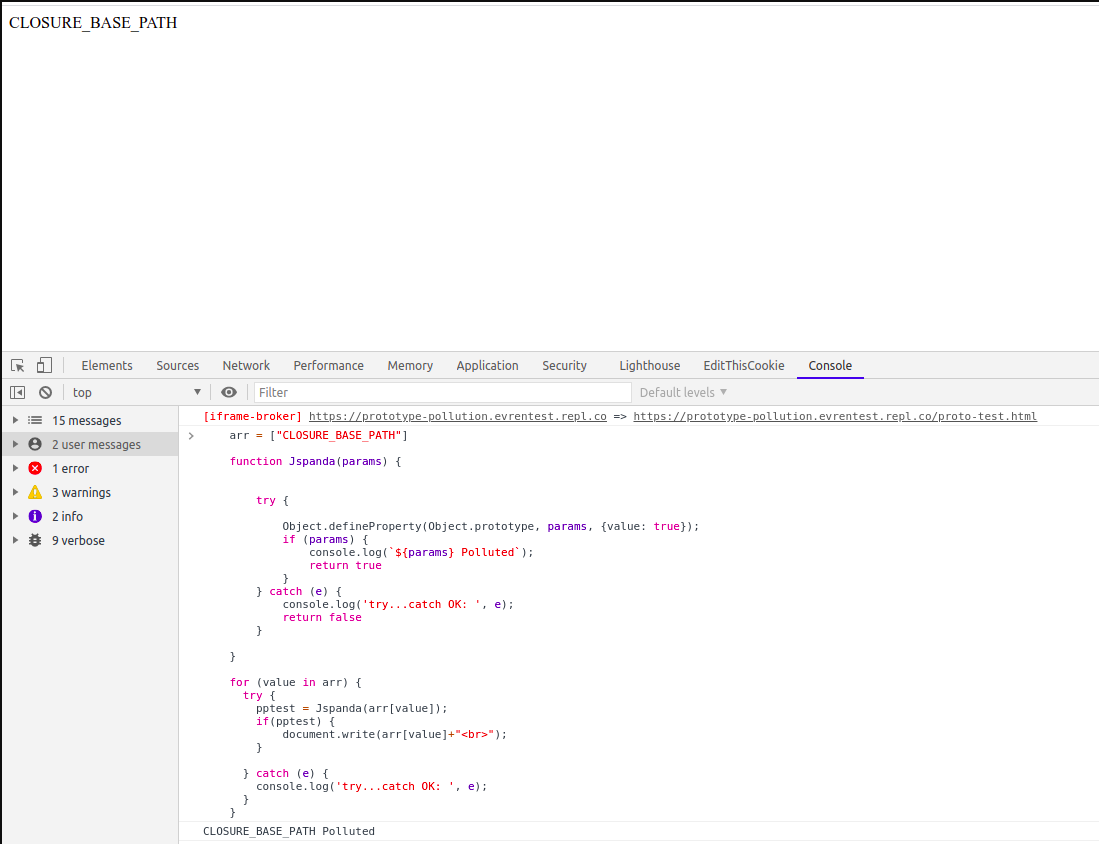
JSPanda - Client-Side Prototype Pullution Vulnerability Scanner

Persistent XSS (unvalidated Open Graph embed) at LinkedIn.com, by Jonathan Bouman
GitHub - cak/XSS-Challenge: A simple Cross-Site Scripting (XSS) challenge with multiple contexts and filters.

Wacky XSS challenge write-up. On November 4th BugPoc published a new…, by Daniel Santos
open-redirect-detection · GitHub Topics · GitHub

How We Found Another XSS in Google with Acunetix

Security Weekly Podcast Network (Video)

FIX: WebClient Service Missing in Server 2016/2012 (Fix Error 0x80070043: Windows cannot access the SharePoint site).
Offensive-Payloads/Cross-Site-Scripting-XSS-Payloads.txt at main · InfoSecWarrior/Offensive-Payloads · GitHub

Wacky XSS challenge write-up. On November 4th BugPoc published a new…, by Daniel Santos

Wacky XSS challenge write-up. On November 4th BugPoc published a new…, by Daniel Santos
GitHub - inforkgodara/xss-vulnerability: Explanation of Cross-site Scripting (XSS) with PHP mini project.

OWASP Top 10 : Cross-Site Scripting #3 Bad JavaScript Imports
Recomendado para você
-
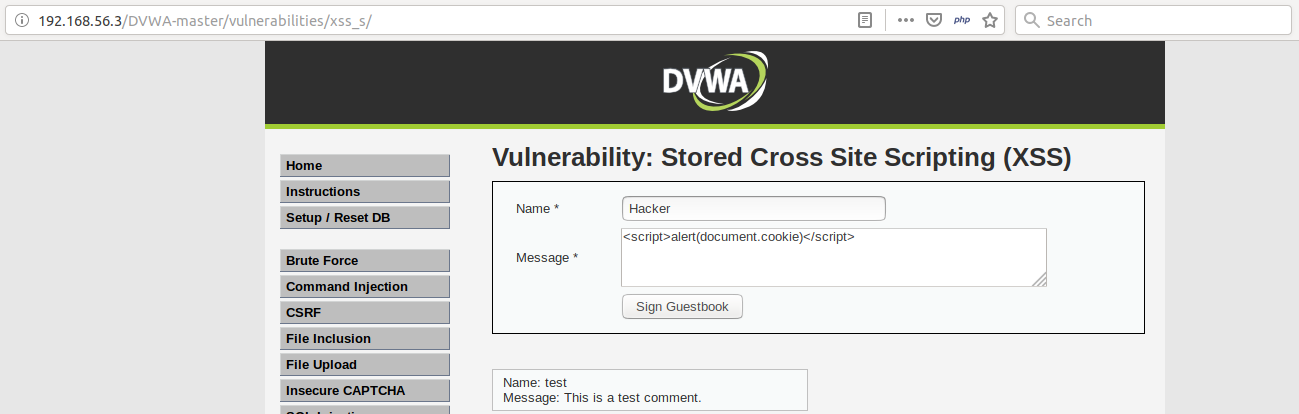 Vulnérabilité XSS, ou injection de code indirecte à distance19 dezembro 2024
Vulnérabilité XSS, ou injection de code indirecte à distance19 dezembro 2024 -
 XSSS-ZC Transparent Bookshelf, Shelf, Transparent Folding Ladder, Multifunctional Bookshelf Ladder, Indoor Bookshelf Ladder, Household Three Step19 dezembro 2024
XSSS-ZC Transparent Bookshelf, Shelf, Transparent Folding Ladder, Multifunctional Bookshelf Ladder, Indoor Bookshelf Ladder, Household Three Step19 dezembro 2024 -
Getting started with XSS: Cross-Site Scripting Attacks19 dezembro 2024
-
 XSS: Cross Site Scripting Web Application Pentesting19 dezembro 2024
XSS: Cross Site Scripting Web Application Pentesting19 dezembro 2024 -
 Single Shaft Shredder XSSS-85019 dezembro 2024
Single Shaft Shredder XSSS-85019 dezembro 2024 -
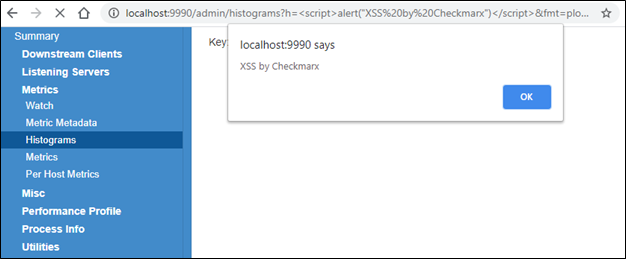 CVE-2020-35774: twitter-server XSS Vulnerability Discovered19 dezembro 2024
CVE-2020-35774: twitter-server XSS Vulnerability Discovered19 dezembro 2024 -
Xsss store - Xsss store added a new photo.19 dezembro 2024
-
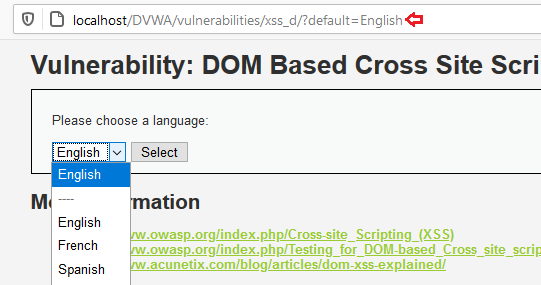 Comprehensive Guide on Cross-Site Scripting (XSS) - Hacking Articles19 dezembro 2024
Comprehensive Guide on Cross-Site Scripting (XSS) - Hacking Articles19 dezembro 2024 -
 XSS exploitation without using the
XSS exploitation without using the
