GootBot - Gootloader's new approach to post-exploitation
Por um escritor misterioso
Last updated 18 janeiro 2025
IBM X-Force discovered a new variant of Gootloader — the "GootBot" implant. Learn more about this and how to combat it.
The Rise of Post-Exploitation Attack Frameworks

CyberWire Daily – Podcast – Podtail

Mitigating CVE-2023-3595 and CVE-2023-3596 Impacting Rockwell Automation ControlLogix Firmware : r/worldTechnology

cisa podcasts
Gootloader” expands its payload delivery options – Sophos News
Stopping Gootloader with Sophos Intercept X – Sophos News

Trusteer Rapport Effectively Resists Carberp Bypass Attempts
GootBot: A Stealthy Game Changer in Malware - PureVPN Blog
38 Million Reasons to use Cryptography for Business - Security Intelligence

Gootloader” expands its payload delivery options – Sophos News

How human behavior research informs security strategies: Kai Roer explains., CyberCureME - Cyber Security Marketplace posted on the topic
Pratik Raval (PratikR38076335@) / X
GootBot: A Stealthy Game Changer in Malware - PureVPN Blog

Deleting Your Way Into SYSTEM: Why Arbitrary File Deletion Vulnerabilities Matter : r/worldTechnology

CyberCureME - Cyber Security Marketplace on LinkedIn: F5 BIG-IP vulnerabilities leveraged by attackers: What to do? - Help Net…
Recomendado para você
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG18 janeiro 2025
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG18 janeiro 2025 -
 meu cachorro morreu e agora não tenho dinheiro para spoofer no18 janeiro 2025
meu cachorro morreu e agora não tenho dinheiro para spoofer no18 janeiro 2025 -
 YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub18 janeiro 2025
YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub18 janeiro 2025 -
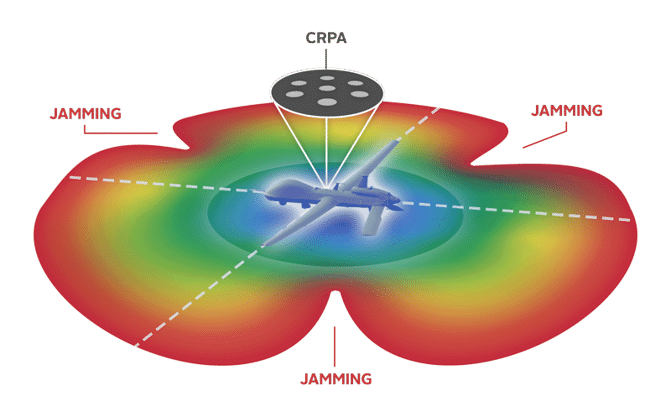 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing18 janeiro 2025
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing18 janeiro 2025 -
Location Guard18 janeiro 2025
-
CHEAPEST RED ENGINE SPOOFER, Video Gaming, Gaming Accessories18 janeiro 2025
-
 Simply Click to Change Your Location in Pokémon GO18 janeiro 2025
Simply Click to Change Your Location in Pokémon GO18 janeiro 2025 -
Cracked Hwid Spoofer18 janeiro 2025
-
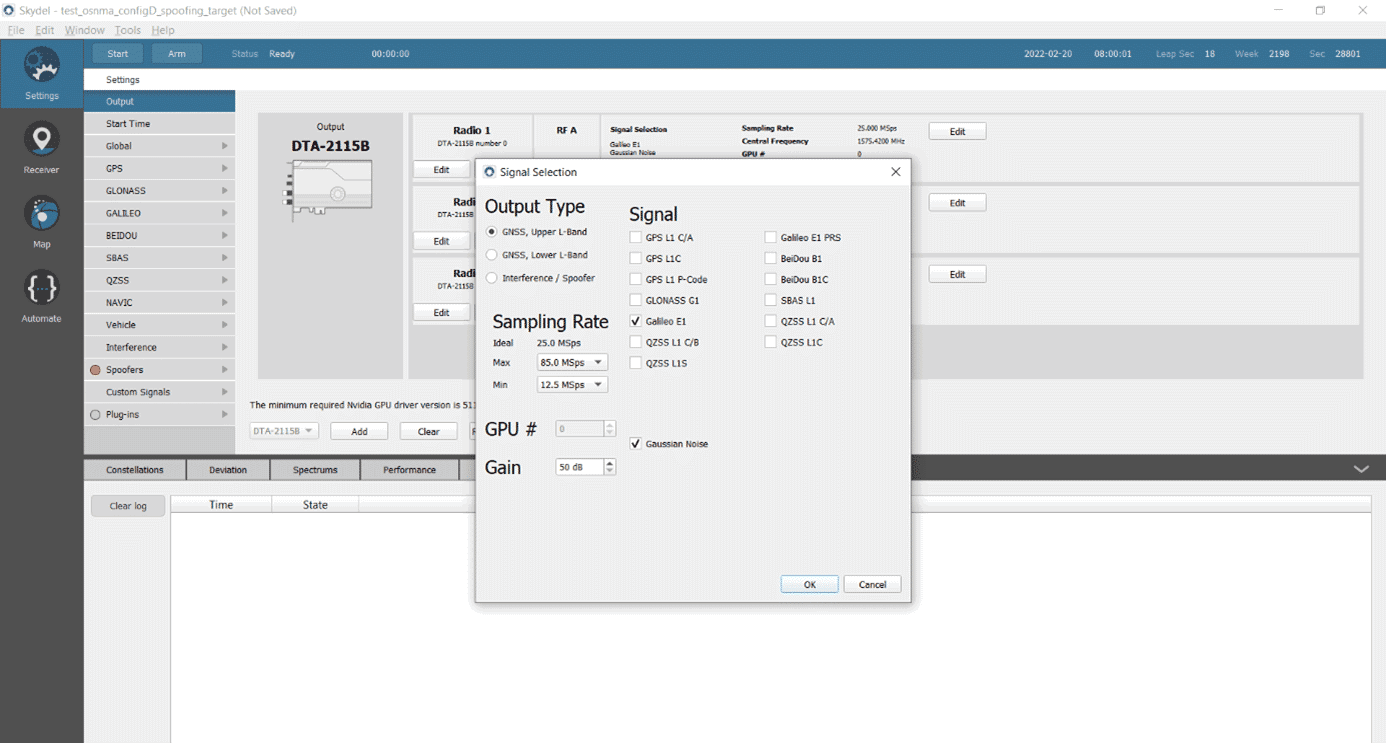 Testing a Receiver's Galileo OS-NMA Capability Using Skydel18 janeiro 2025
Testing a Receiver's Galileo OS-NMA Capability Using Skydel18 janeiro 2025 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's18 janeiro 2025
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's18 janeiro 2025
você pode gostar
-
 ESCAPAMOS DE UMA PROFESSORA MUITO ASSUSTADORA (Scary Teacher18 janeiro 2025
ESCAPAMOS DE UMA PROFESSORA MUITO ASSUSTADORA (Scary Teacher18 janeiro 2025 -
 Kimetsu no Yaiba: Yuukaku-hen / Demon Slayer: Entertainment18 janeiro 2025
Kimetsu no Yaiba: Yuukaku-hen / Demon Slayer: Entertainment18 janeiro 2025 -
 Jogo Da Memoria Infantil Desafio Racha Cuca18 janeiro 2025
Jogo Da Memoria Infantil Desafio Racha Cuca18 janeiro 2025 -
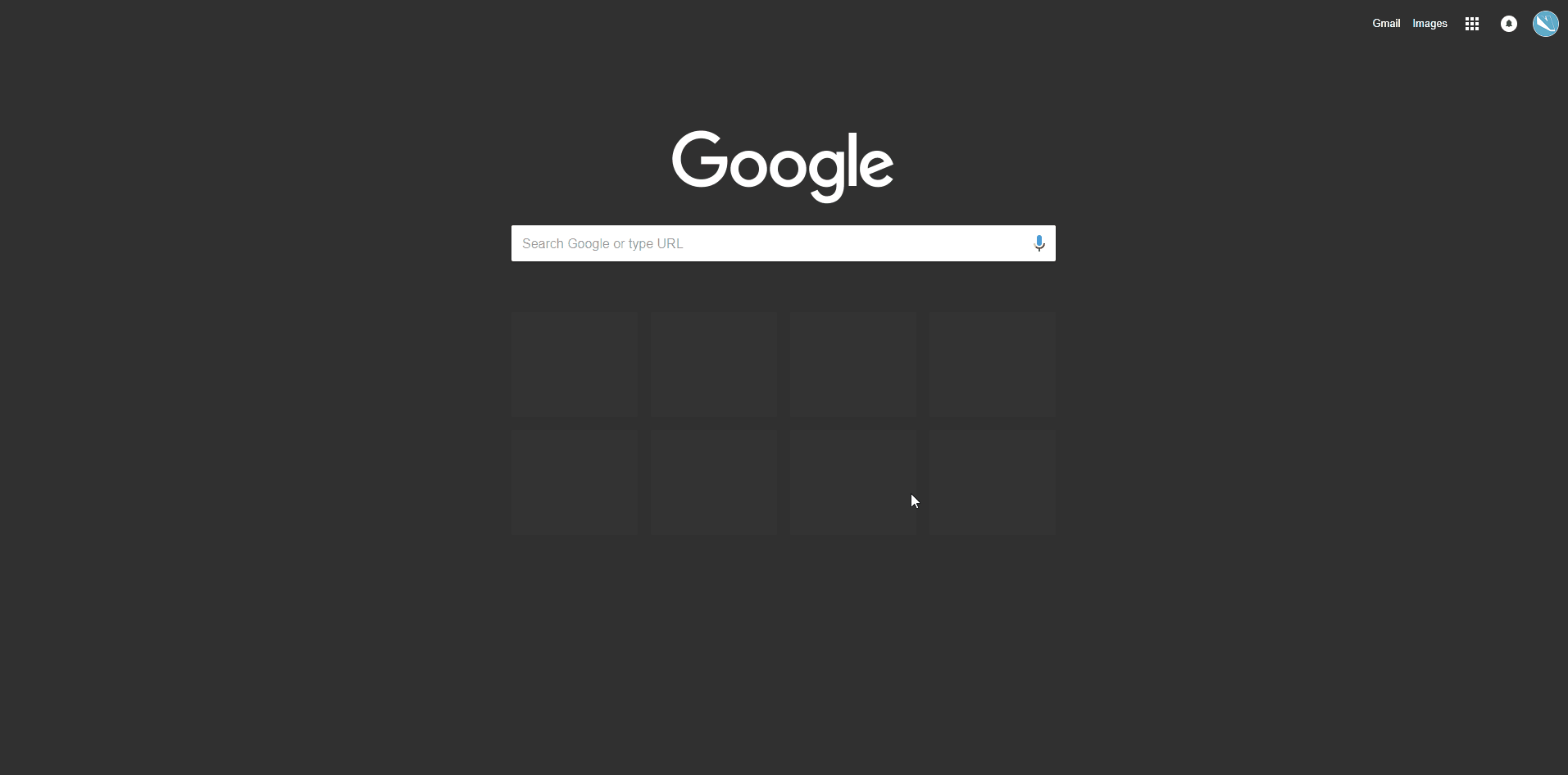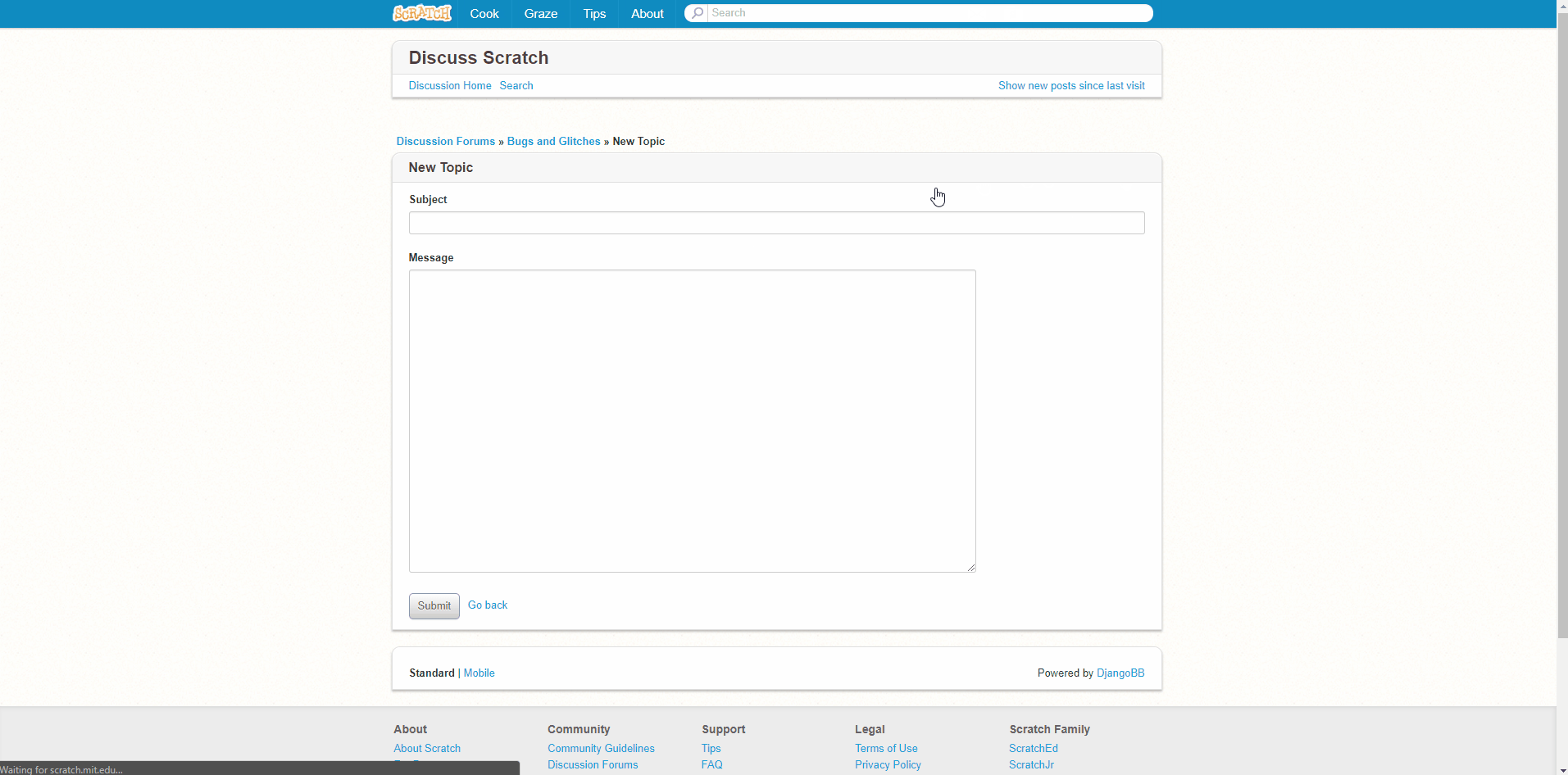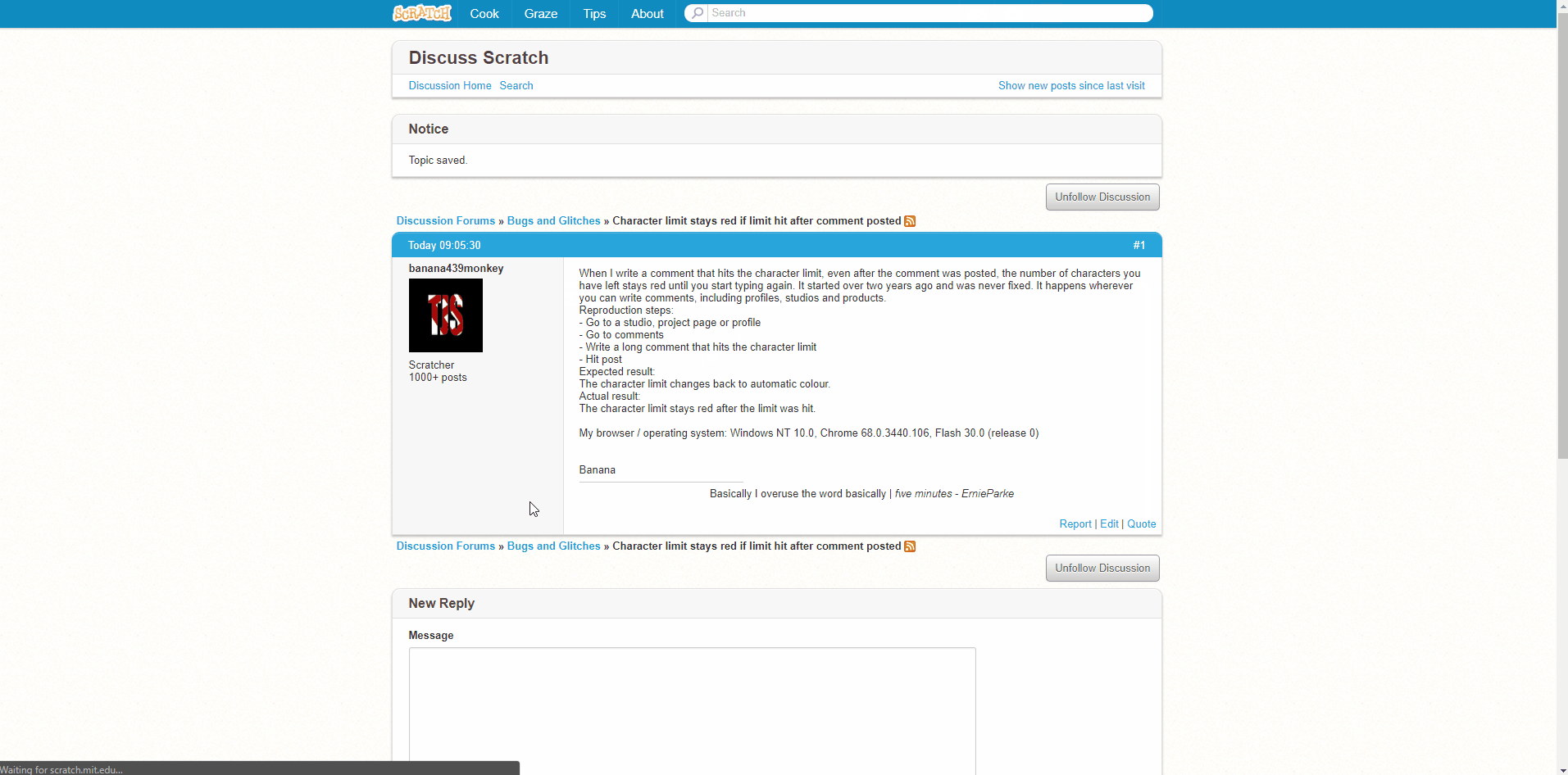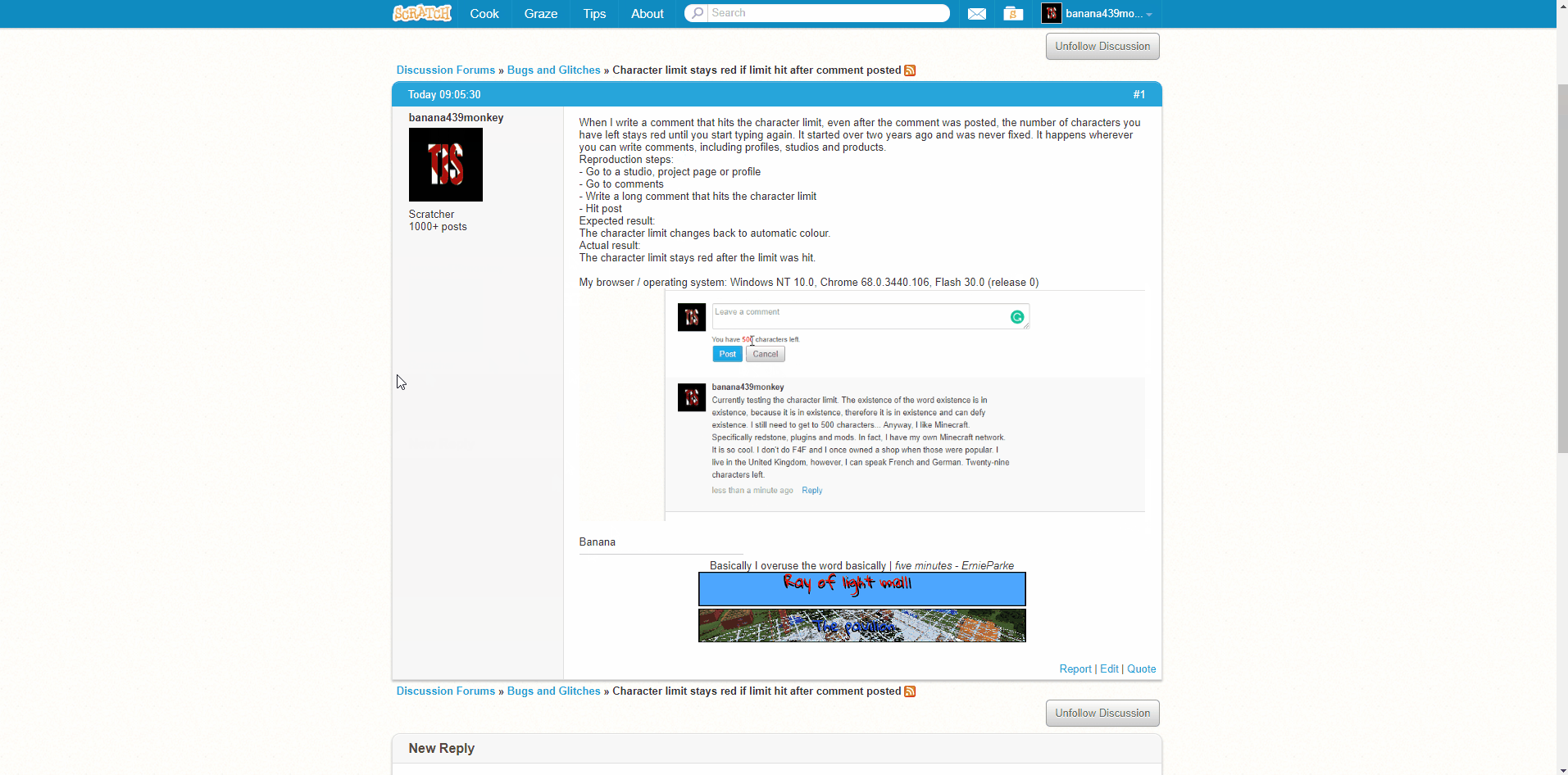 PLEASE READ BEFORE MAKING A TOPIC: A guide to reporting glitches18 janeiro 2025
PLEASE READ BEFORE MAKING A TOPIC: A guide to reporting glitches18 janeiro 2025 -
 My Fruit Battlegrounds Luck in a Nutshell18 janeiro 2025
My Fruit Battlegrounds Luck in a Nutshell18 janeiro 2025 -
 Timeskip in GTA Online : r/gtaonline18 janeiro 2025
Timeskip in GTA Online : r/gtaonline18 janeiro 2025 -
 Kirito, Wikia Liber Proeliis18 janeiro 2025
Kirito, Wikia Liber Proeliis18 janeiro 2025 -
 Jean Dawson - SICK OF IT* // Lyrics, Sub. Español18 janeiro 2025
Jean Dawson - SICK OF IT* // Lyrics, Sub. Español18 janeiro 2025 -
 boruto _ ep 288 - BiliBili18 janeiro 2025
boruto _ ep 288 - BiliBili18 janeiro 2025 -
 Nerf - Roblox MM2 Dartbringer (F3776) : : Brinquedos18 janeiro 2025
Nerf - Roblox MM2 Dartbringer (F3776) : : Brinquedos18 janeiro 2025
