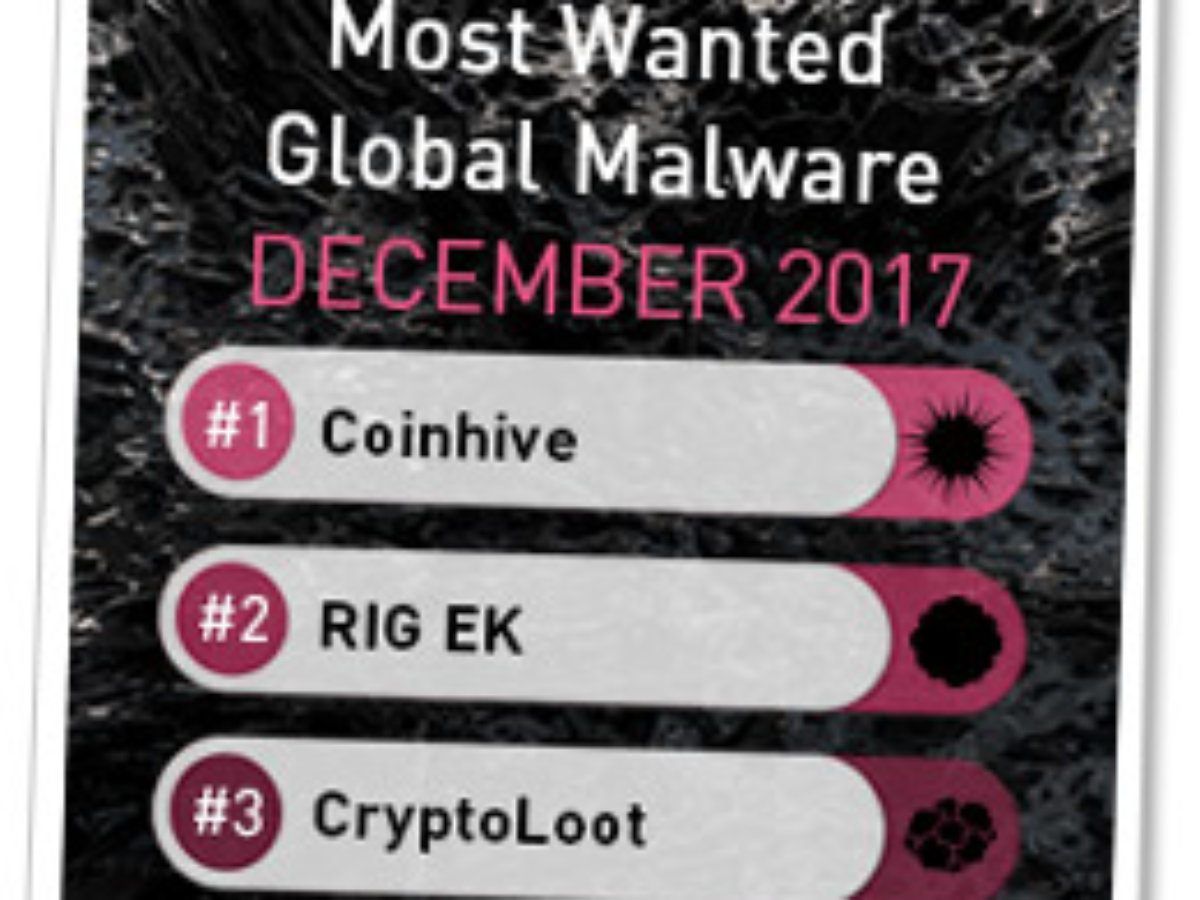
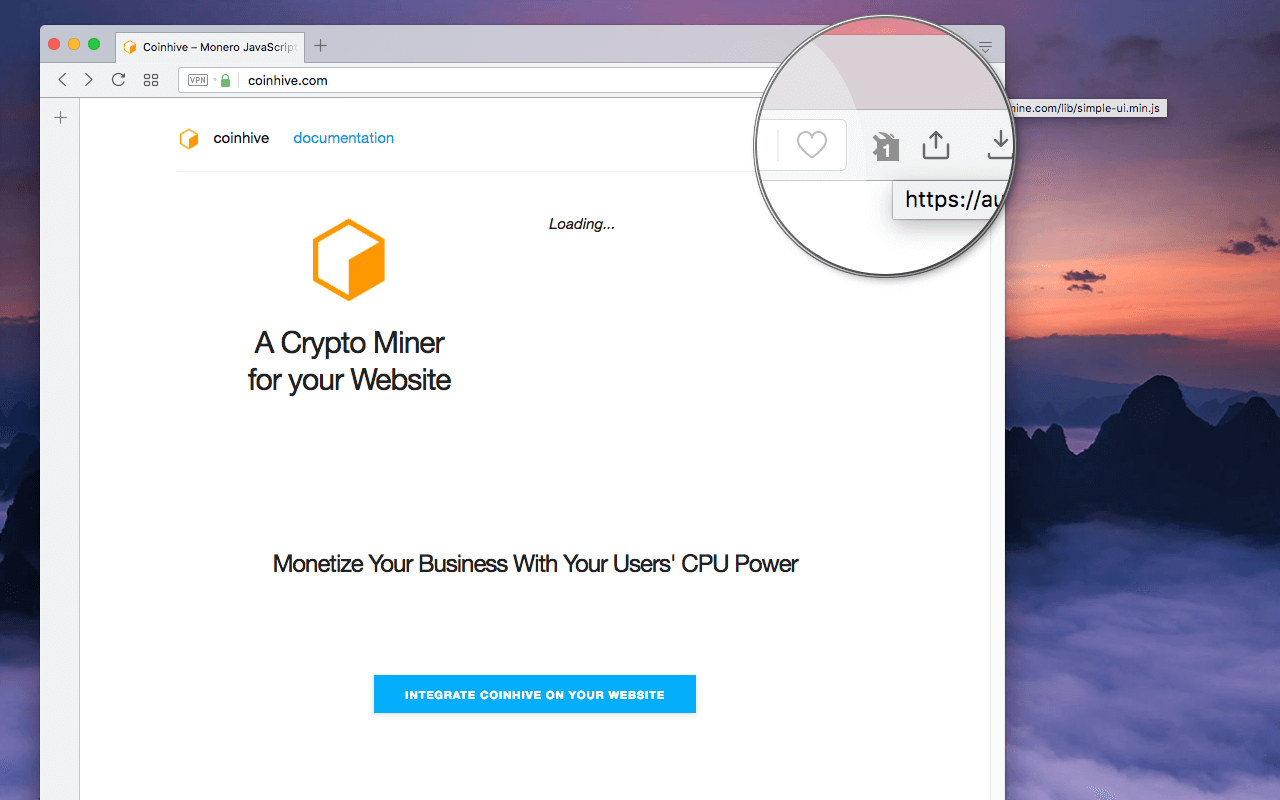
Crypto-Miner Named the Most Wanted Malware for December 2017
Por um escritor misterioso
Last updated 20 fevereiro 2025

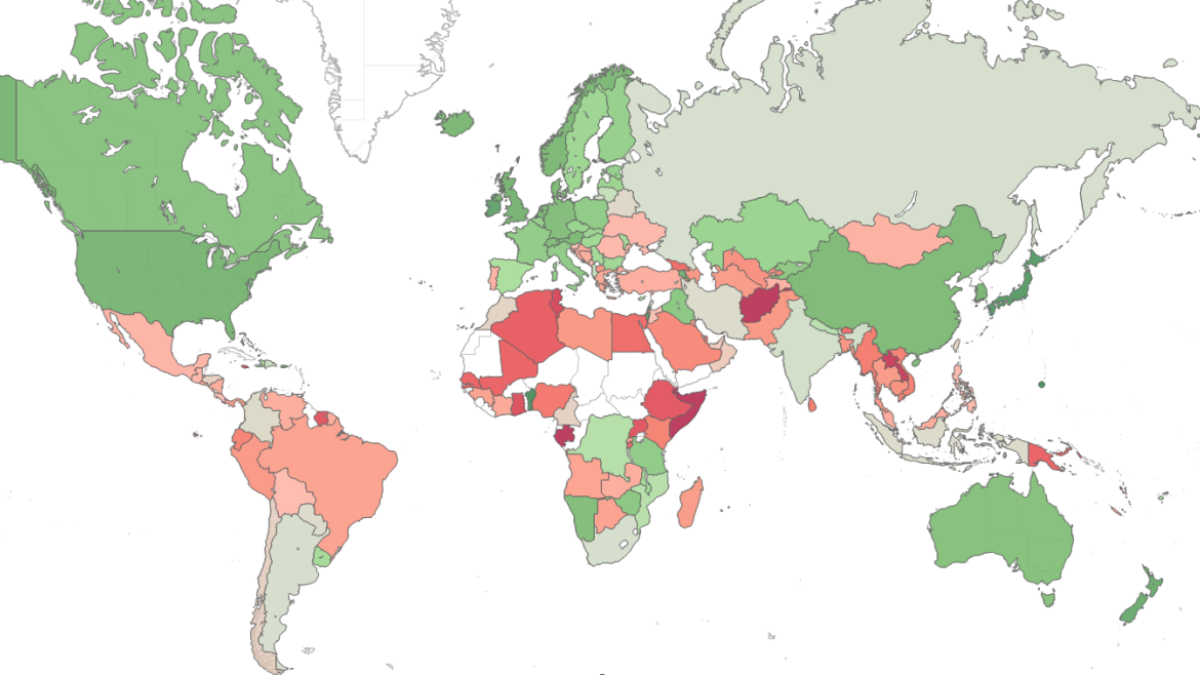
A JavaScript-based cryptocurrency miner earned the top spot in a list of the "most wanted" malware for December 2017.

Botnet - Wikipedia

U.S. Charges Russia GRU Intelligence Officers for notorious attacks, including NotPetya
March 2019's Most Wanted Malware: Cryptomining Still Dominates Despite Coinhive Closure - Check Point Blog

New Jenkins Campaign Hides Malware, Kills Competing Crypto-Miners

Mining is the new black

Is cryptocurrency mining malware the new adware?

Powerful Malware Disguised as Crypto Miner Infects 1M+ Windows, Linux PCs
December's Most Wanted Malware: Crypto-Miners Affect 55% of Businesses Worldwide - Check Point Blog

The Top Malware Families in Banking, Mobile, Ransomware, and Crypto-Mining of 2017

February 2020's Most Wanted Malware: Increase in Exploits Spreading the Mirai Botnet to IoT Devices - Check Point Blog

Everything you wanted to know about bitcoin but were afraid to ask, Cryptocurrencies

Cybercrime's Cryptocurrency Gold Rush: Going Strong!
Check Point Research detects Crypto Miner malware disguised as Google translate desktop and other legitimate applications - Check Point Research
Recomendado para você
-
 Coin Mining Blocker20 fevereiro 2025
Coin Mining Blocker20 fevereiro 2025 -
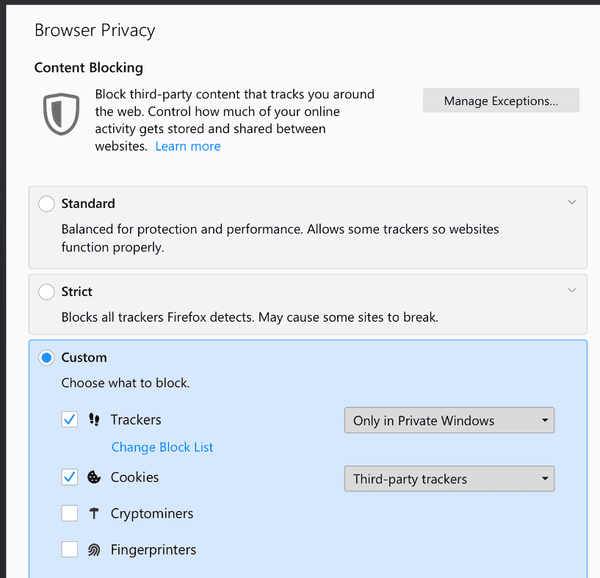 Firefox 67: Cryptocurrency miners and Fingerprinters protection20 fevereiro 2025
Firefox 67: Cryptocurrency miners and Fingerprinters protection20 fevereiro 2025 -
 Game Used Colorado Avalanche Pro Stock Bauer Mach Glove & Blocker Regular Miner20 fevereiro 2025
Game Used Colorado Avalanche Pro Stock Bauer Mach Glove & Blocker Regular Miner20 fevereiro 2025 -
 AdBlock and Authedmine.com cryptocurrency miners – AdBlock20 fevereiro 2025
AdBlock and Authedmine.com cryptocurrency miners – AdBlock20 fevereiro 2025 -
 Cryptojacking - Cryptomining in the browser — ENISA20 fevereiro 2025
Cryptojacking - Cryptomining in the browser — ENISA20 fevereiro 2025 -
Yes! Hackers are using your computer to make money (Crypto Currency).20 fevereiro 2025
-
 Miner's Bane, Planeswalker Symbol Reprints20 fevereiro 2025
Miner's Bane, Planeswalker Symbol Reprints20 fevereiro 2025 -
 Home Mining – CryptoCloaks20 fevereiro 2025
Home Mining – CryptoCloaks20 fevereiro 2025 -
 Bitcoin Miners Building Rigs Must Navigate World of Crypto Power-Hunting - Bloomberg20 fevereiro 2025
Bitcoin Miners Building Rigs Must Navigate World of Crypto Power-Hunting - Bloomberg20 fevereiro 2025 -
 Men's Basketball - UTEP Miners20 fevereiro 2025
Men's Basketball - UTEP Miners20 fevereiro 2025
você pode gostar
-
 SONIC SUPERSTARS, PC Steam Game20 fevereiro 2025
SONIC SUPERSTARS, PC Steam Game20 fevereiro 2025 -
 Sistine Fibel, rokudenashi Majutsu Koushi To Akashic Records20 fevereiro 2025
Sistine Fibel, rokudenashi Majutsu Koushi To Akashic Records20 fevereiro 2025 -
FutParódias Radio - playlist by Spotify20 fevereiro 2025
-
 Check out SkyBlock Lucky Block, a community creation available in the Minecraft marketplace.20 fevereiro 2025
Check out SkyBlock Lucky Block, a community creation available in the Minecraft marketplace.20 fevereiro 2025 -
 Tiara Orelha de gato – Melinda Acessórios20 fevereiro 2025
Tiara Orelha de gato – Melinda Acessórios20 fevereiro 2025 -
 One Piece (anime) Roronoa Zoro wallpaper, 1920x108020 fevereiro 2025
One Piece (anime) Roronoa Zoro wallpaper, 1920x108020 fevereiro 2025 -
 Hello! Exploring the Supercute World of Hello Kitty20 fevereiro 2025
Hello! Exploring the Supercute World of Hello Kitty20 fevereiro 2025 -
 Filmes Perturbadores20 fevereiro 2025
Filmes Perturbadores20 fevereiro 2025 -
 Free STL file Twisted Metal JOHNDOE license plate 👾・3D printable design to download・Cults20 fevereiro 2025
Free STL file Twisted Metal JOHNDOE license plate 👾・3D printable design to download・Cults20 fevereiro 2025 -
 Lembrancinha Aniversário Roblox Rosa Maleta Marshmallow20 fevereiro 2025
Lembrancinha Aniversário Roblox Rosa Maleta Marshmallow20 fevereiro 2025

