Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 19 janeiro 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.

What are Advance Persistent Threats (APT)?

Try Hack Me Red Team Threat Intel

FireEye Reveals How SolarWinds Hackers Bypassed the Defenses

Big Russian hack used a technique experts had warned about for

Red Team tactics – breaching the lines of defense – Comsec Global

TTPs Within Cyber Threat Intelligence
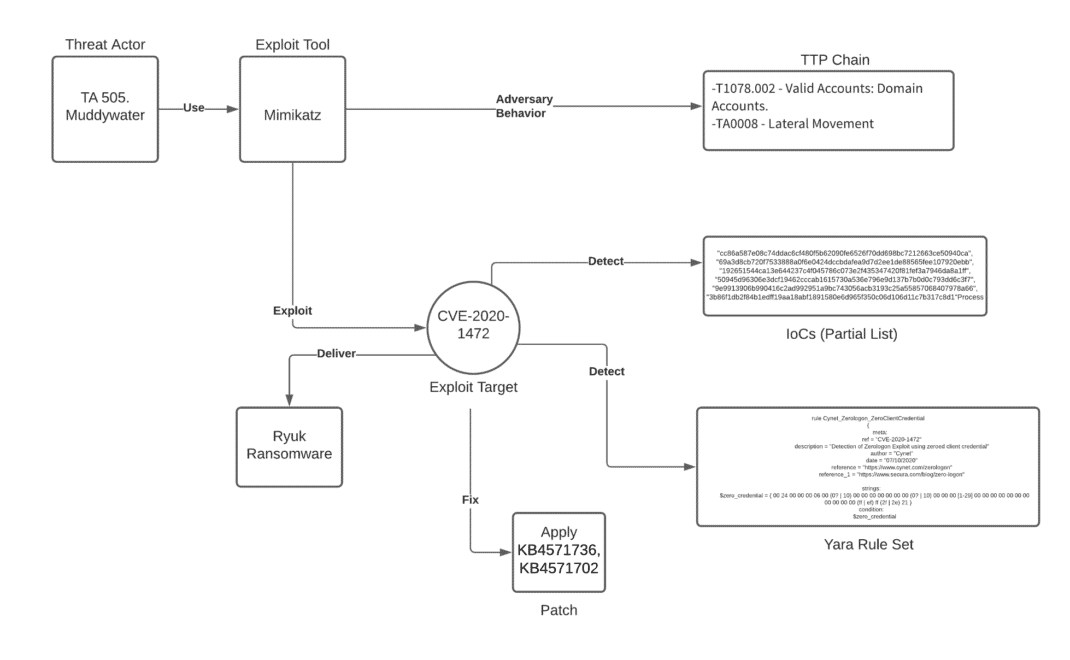
Unpacking the CVEs in the FireEye Breach - Start Here First
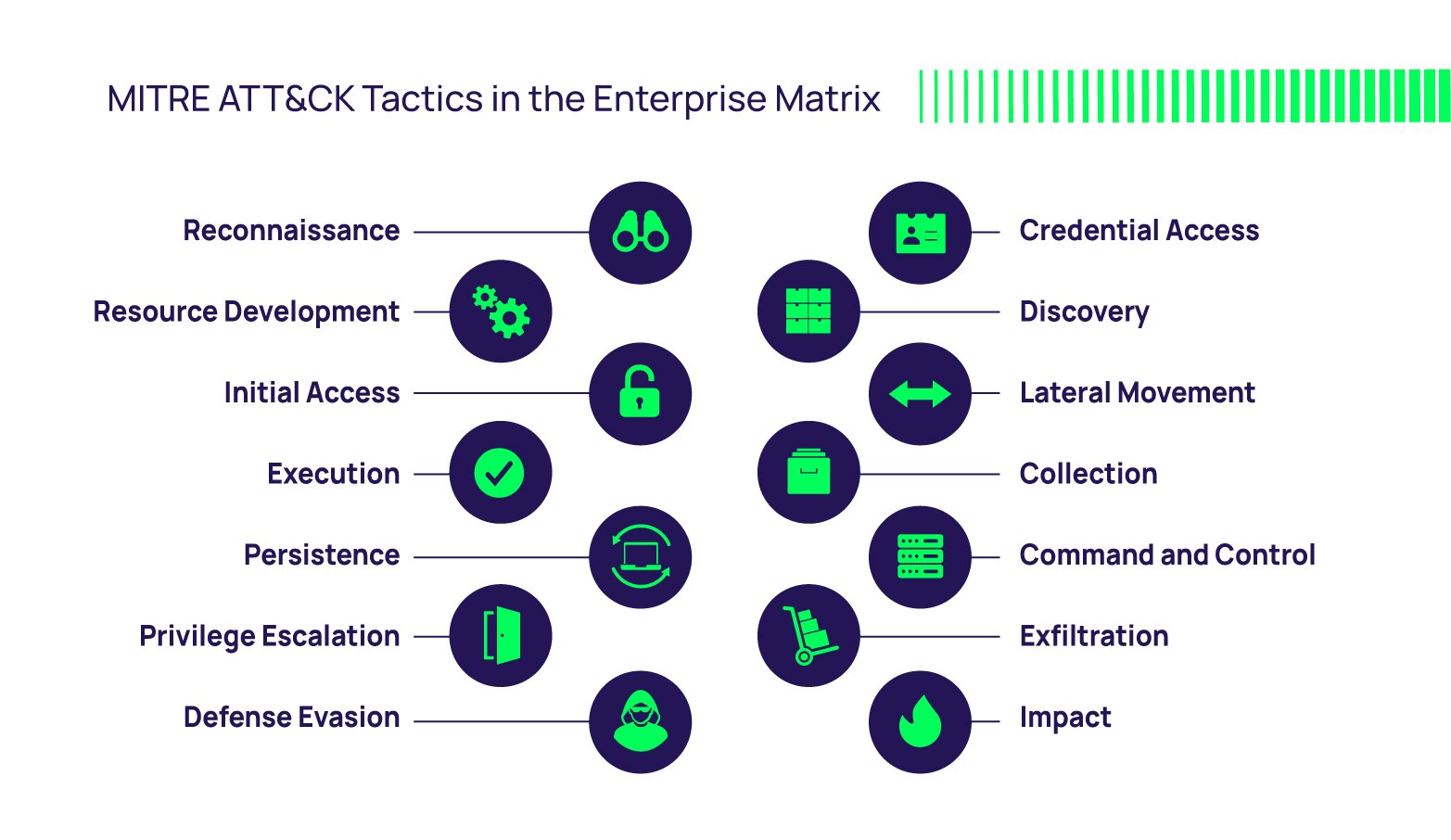
The MITRE ATT&CK Framework

Red Team Tools Detection and Alerting
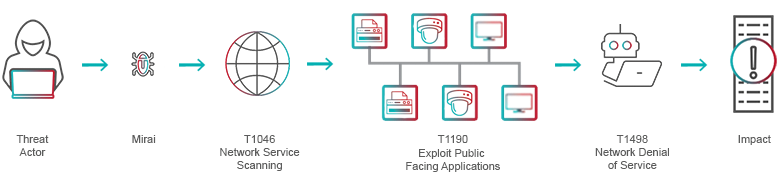
Tactics, Techniques and Procedures
Recomendado para você
-
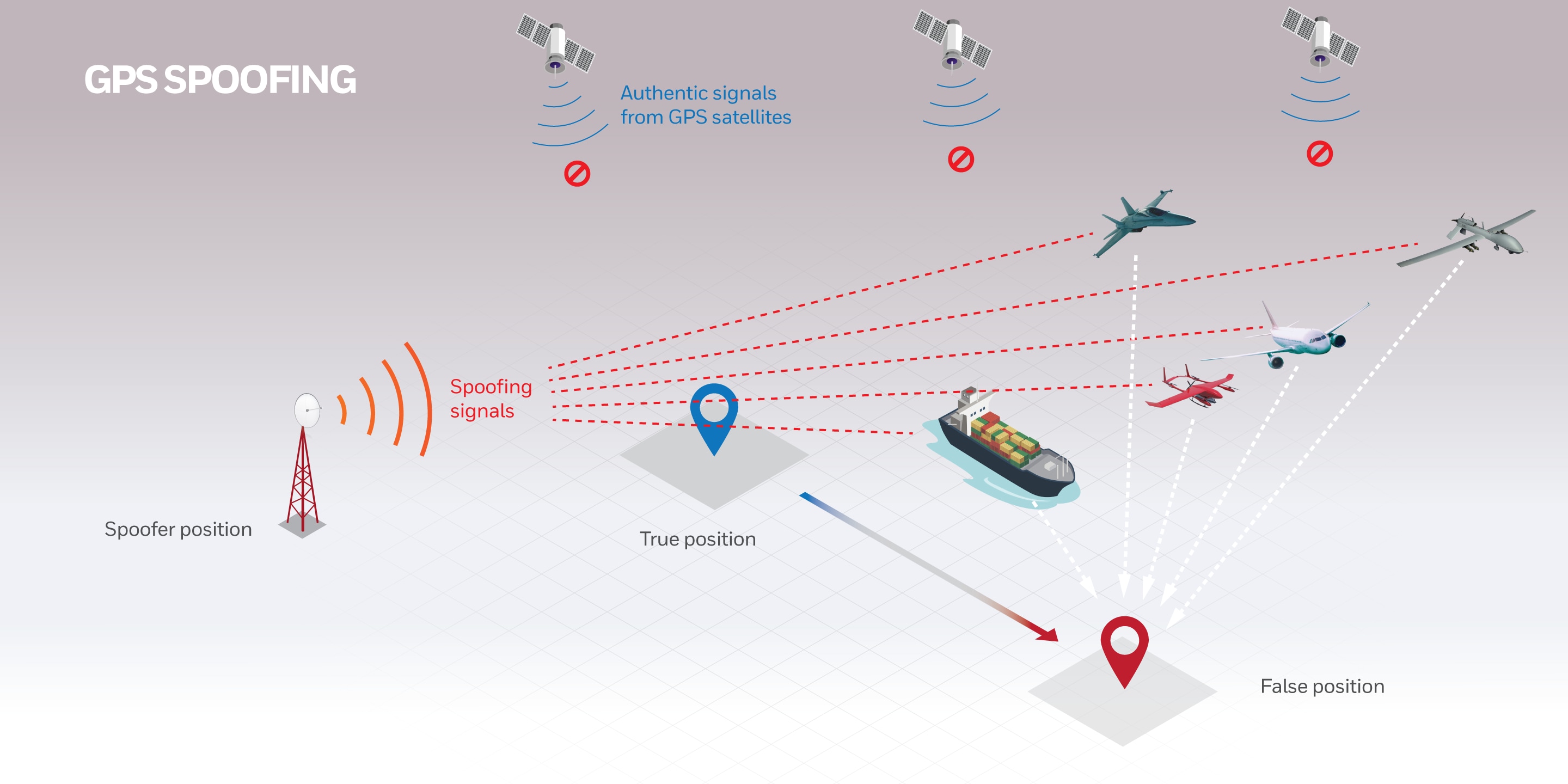 No GPS, No Problem: Honeywell Invents, Demonstrates Military-Grade19 janeiro 2025
No GPS, No Problem: Honeywell Invents, Demonstrates Military-Grade19 janeiro 2025 -
 SimGEN Simulator and PNT Product Improvements - Spirent19 janeiro 2025
SimGEN Simulator and PNT Product Improvements - Spirent19 janeiro 2025 -
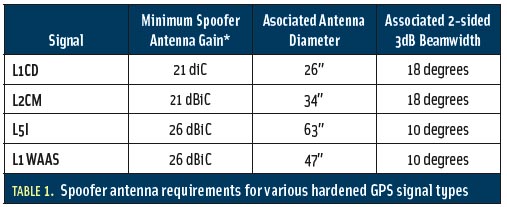 Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation19 janeiro 2025
Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation19 janeiro 2025 -
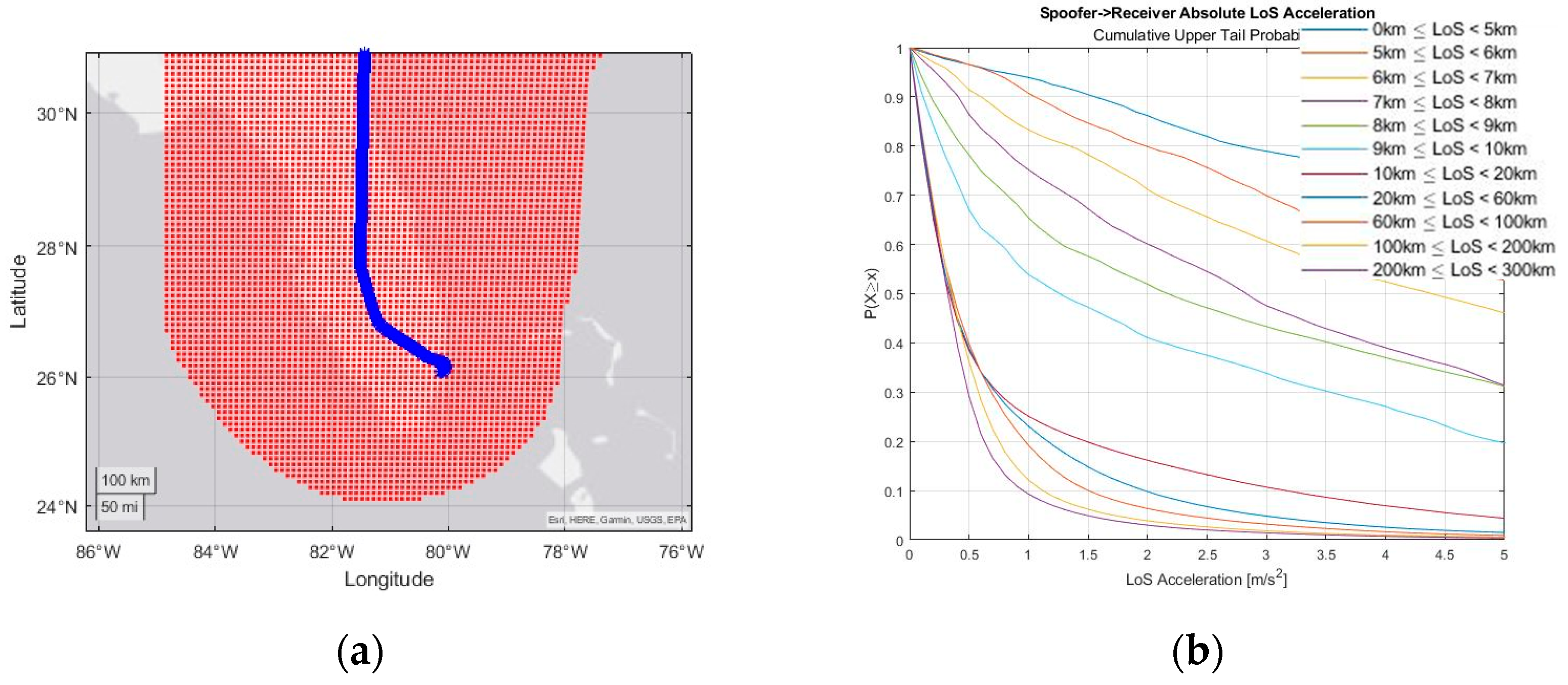 Engineering Proceedings, Free Full-Text19 janeiro 2025
Engineering Proceedings, Free Full-Text19 janeiro 2025 -
best fivem spoofer free|TikTok Search19 janeiro 2025
-
 11 Types of Spoofing Attacks Every Security Professional Should19 janeiro 2025
11 Types of Spoofing Attacks Every Security Professional Should19 janeiro 2025 -
 GitHub - sCANd3ww/RedEngineX: RedENGINE is the Best LUA Executor and Spoofer for FiveM with features Like: Premium Menu, Dumper, Stopper Ressource, Event Logger, Aimbot,ESP.19 janeiro 2025
GitHub - sCANd3ww/RedEngineX: RedENGINE is the Best LUA Executor and Spoofer for FiveM with features Like: Premium Menu, Dumper, Stopper Ressource, Event Logger, Aimbot,ESP.19 janeiro 2025 -
 Protecting GPS From Spoofers Is Critical to the Future of Navigation19 janeiro 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation19 janeiro 2025 -
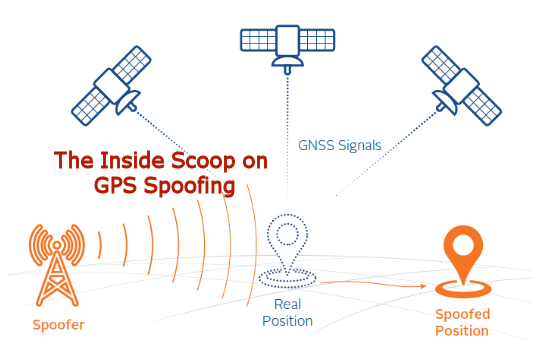 Telnet Networks - Managing Network Performance - Telnet Network19 janeiro 2025
Telnet Networks - Managing Network Performance - Telnet Network19 janeiro 2025 -
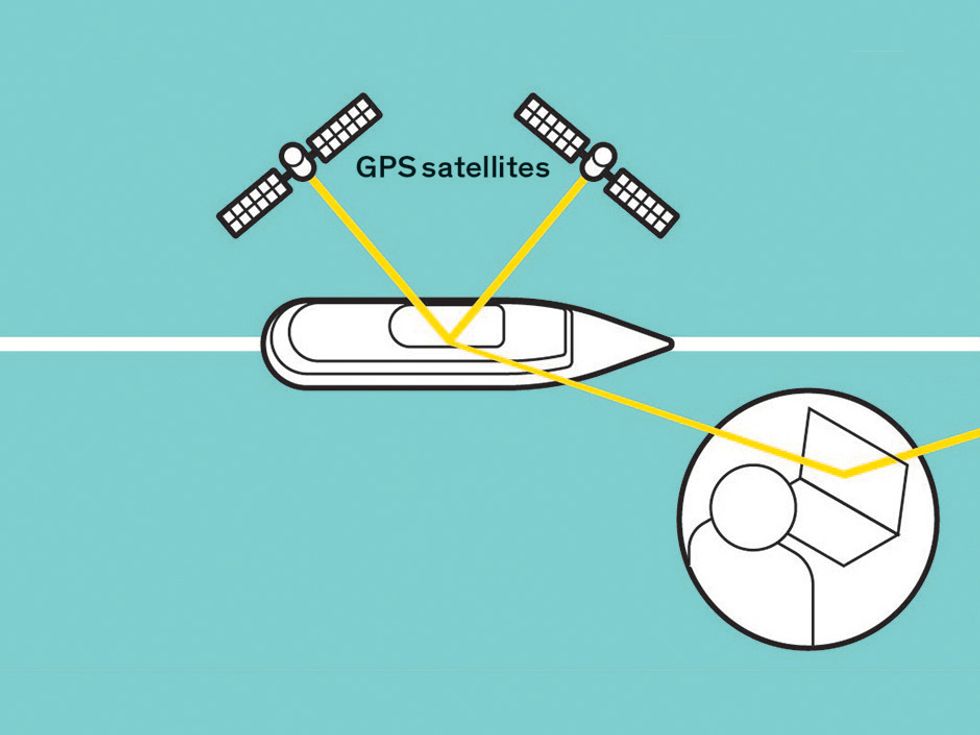 Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum19 janeiro 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum19 janeiro 2025
você pode gostar
-
 Pac-Man Games - Giant Bomb19 janeiro 2025
Pac-Man Games - Giant Bomb19 janeiro 2025 -
 itens gratis do roblox codigos|Pesquisa do TikTok19 janeiro 2025
itens gratis do roblox codigos|Pesquisa do TikTok19 janeiro 2025 -
 17_12_16 - Esportes - Brasil x Argentina - Futebol America…19 janeiro 2025
17_12_16 - Esportes - Brasil x Argentina - Futebol America…19 janeiro 2025 -
Imaging Surrogates of Disease Activity in Neuromyelitis Optica Allow Distinction from Multiple Sclerosis19 janeiro 2025
-
 1366x768 Resolution Valorant Video Game 1366x768 Resolution19 janeiro 2025
1366x768 Resolution Valorant Video Game 1366x768 Resolution19 janeiro 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/l/l/lo9TKzQLOwuTgAz5aDew/2016-08-22-ps-plus-playstation-4-ps3-ps-vita.jpg) Preço da PS Plus no PS4, PS3 e PS Vita aumentará para R$ 12919 janeiro 2025
Preço da PS Plus no PS4, PS3 e PS Vita aumentará para R$ 12919 janeiro 2025 -
Donald E Tico E Teco - Quebrando O Galho (Out On A Limb) (1950) HQ on Vimeo19 janeiro 2025
-
 Assistir Boruto: Naruto Next Generations - Episódio 54 - Meus Animes19 janeiro 2025
Assistir Boruto: Naruto Next Generations - Episódio 54 - Meus Animes19 janeiro 2025 -
 Roblox Face Kids Bath Towel by Vacy Poligree - Pixels19 janeiro 2025
Roblox Face Kids Bath Towel by Vacy Poligree - Pixels19 janeiro 2025 -
meguru bachira number|TikTok Search19 janeiro 2025

